Power Network
Time Limit:2000MS Memory Limit:32768KB 64bit IO Format:%I64d & %I64uDescription
A power network consists of nodes (power stations, consumers and dispatchers) connected by power transport lines. A node u may be supplied with an amount s(u) >= 0 of power, may produce an amount 0 <= p(u) <= p max(u) of power, may consume an amount 0 <= c(u) <= min(s(u),c max(u)) of power, and may deliver an amount d(u)=s(u)+p(u)-c(u) of power. The following restrictions apply: c(u)=0 for any power station, p(u)=0 for any consumer, and p(u)=c(u)=0 for any dispatcher. There is at most one power transport line (u,v) from a node u to a node v in the net; it transports an amount 0 <= l(u,v) <= lmax(u,v) of power delivered by u to v. Let Con=Σ uc(u) be the power consumed in the net. The problem is to compute the maximum value of Con.
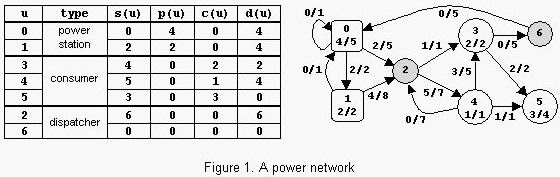
An example is in figure 1. The label x/y of power station u shows that p(u)=x and p max(u)=y. The label x/y of consumer u shows that c(u)=x and cmax(u)=y. The label x/y of power transport line (u,v) shows that l(u,v)=x and l max(u,v)=y. The power consumed is Con=6. Notice that there are other possible states of the network but the value of Con cannot exceed 6.

An example is in figure 1. The label x/y of power station u shows that p(u)=x and p max(u)=y. The label x/y of consumer u shows that c(u)=x and cmax(u)=y. The label x/y of power transport line (u,v) shows that l(u,v)=x and l max(u,v)=y. The power consumed is Con=6. Notice that there are other possible states of the network but the value of Con cannot exceed 6.
Input
There are several data sets in the input. Each data set encodes a power network. It starts with four integers: 0 <= n <= 100 (nodes), 0 <= np <= n (power stations), 0 <= nc <= n (consumers), and 0 <= m <= n^2 (power transport lines). Follow m data triplets (u,v)z, where u and v are node identifiers (starting from 0) and 0 <= z <= 1000 is the value of l max(u,v). Follow np doublets (u)z, where u is the identifier of a power station and 0 <= z <= 10000 is the value of p max(u). The data set ends with nc doublets (u)z, where u is the identifier of a consumer and 0 <= z <= 10000 is the value of c max(u). All input numbers are integers. Except the (u,v)z triplets and the (u)z doublets, which do not contain white spaces, white spaces can occur freely in input. Input data terminate with an end of file and are correct.
Output
For each data set from the input, the program prints on the standard output the maximum amount of power that can be consumed in the corresponding network. Each result has an integral value and is printed from the beginning of a separate line.
Sample Input
2 1 1 2 (0,1)20 (1,0)10 (0)15 (1)20
7 2 3 13 (0,0)1 (0,1)2 (0,2)5 (1,0)1 (1,2)8 (2,3)1 (2,4)7
(3,5)2 (3,6)5 (4,2)7 (4,3)5 (4,5)1 (6,0)5
(0)5 (1)2 (3)2 (4)1 (5)4
Sample Output
15 6
Hint
The sample input contains two data sets. The first data set encodes a network with 2 nodes, power station 0 with pmax(0)=15 and consumer 1 with cmax(1)=20, and 2 power transport lines with lmax(0,1)=20 and lmax(1,0)=10. The maximum value of Con is 15. The second data set encodes the network from figure 1.
典型的多源多汇最大流问题,只要再找一个源点,一个汇点即可。

#include<stdio.h> #include<queue> #include<string.h> #define MAXN 1000 #define INF 1<<28 int cap[MAXN][MAXN], vis[MAXN], pre[MAXN], maxflow[MAXN]; using namespace std; int n, npow, ncon, m; void bfs() { queue<int>q; int i, Maxflow, u, v; Maxflow = 0; while(1) { memset(vis, 0, sizeof(vis)); memset(pre, 0, sizeof(pre)); memset(maxflow, 0, sizeof(maxflow)); maxflow[n] = INF; q.push(n); vis[n] = 1; while(!q.empty()) { u = q.front(); q.pop(); for(v=0; v<=n+1; v++){ if(!vis[v] && cap[u][v]>0){ vis[v] = 1; pre[v] = u; q.push(v); maxflow[v] = maxflow[u]<cap[u][v]?maxflow[u]:cap[u][v]; } } } if(!maxflow[n+1]) break; for(i=n+1; i!=n; i=pre[i]) { cap[pre[i]][i] -= maxflow[n+1]; cap[i][pre[i]] += maxflow[n+1]; } Maxflow += maxflow[n+1]; } printf("%d ", Maxflow); } int main() { int i, u, v, c; while(~scanf("%d %d %d %d", &n, &npow, &ncon, &m)) { memset(cap, 0, sizeof(cap)); for(i=0; i<m; i++){ scanf(" (%d,%d)", &u, &v); scanf("%d", &c); cap[u][v] += c; } for(i=0; i<npow; i++){ scanf(" (%d)", &u); scanf("%d", &c); cap[n][u] += c; } for(i=0; i<ncon; i++){ scanf(" (%d)", &v); scanf("%d", &c); cap[v][n+1] += c; } bfs(); } return 0; }
