You can configure SSL for SCM-Manager so that the communication of your repositories are encrypted.
Recommend doing the certificate things on a non-Server-OS PC
- Get JDK, the installation help can be found here
- Create a public/private key pair in a keystore
keytool -genkey -keyalg RSA -alias scm -keystore keystore.jks- Then you will be asked to provide the password to protect the keystore, and info about your organization, at last, type
yesto confirm the creation.
- Request a trusted certificate
keytool -certreq -alias scm -keystore keystore.jks -file scm.csr- Open
scm.csrwith Notepad and copy its the content - Login to your CA server, for example: https://CA/certsrv/
- Click Request a certificate
- Click advanced certificate request
- Click Submit a certificate request by using a base-64-encoded ..
- Paste the content into Base-64-encoded certificate request
- Choose Web Server for Certificate Template
- Click the Submit button
- The default DER encode is fine, download the certificate file, name it
scm.cer - Also, download the CA certificate, name it
rootCA.cer
- Import both CA and the requested certificate into keystore
keytool -import -alias root -file rootCA.cer -keystore keystore.jkskeytool -import -alias scm -file scm.cer -keystore keystore.jks
Now you can copy the keystore.jks file to the server under D:scm-serverconf, and start configuring Jetty
- Edit the
server-config.xmlfile- Uncomment the
SSL-Connectorsection - Specify passwords to the
keystore.jksfile, they can be in clear text, obfuscated, checksummed or encrypted
- Uncomment the
- Restart the
scm-serverservice
Configuring TortoiseHg
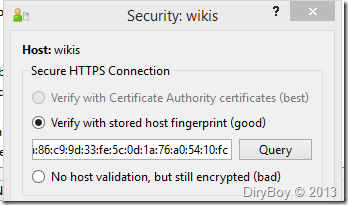
When saving the path, choose Verify with stored host fingerprint in the Security window, and click the Query button.
References:
https://support.quest.com/SolutionDetail.aspx?id=SOL86932
https://bitbucket.org/sdorra/scm-manager/wiki/scm-server-ssl
http://mercurial.selenic.com/wiki/CACertificates
https://bitbucket.org/tortoisehg/thg/issue/63/cannot-pull-push-to-https-server-with-self