Frida:
1.拦截器 frida-trace oc方法hook:
frida-trace -U -m "类方法+/实例方法-[类名 方法名:]" 应用名 -m hook某方法 -M 排除某方法
执行后找到相应的js文件函数块添加相应代码打印内容
var objcData = new ObjC.Object(args[2]) //转oc对象然后打印
.readUtf8String()
.UTF8String()
2.hook c函数:
Interceptor.attach(Module.findExportByName(null, "方法"), {
onEnter: function(args) {
console.log("方法");
},
onLeave: function(retval) {
console.log("after之后操作");
},
})
3.hook oc方法//采用API查找器和拦截器组合使用
var resolver = new ApiResolver('objc');
//objc为要过滤的类
resolver.enumerateMatches('*[objc *]', {
onMatch: function(match) {
var method = match['name'];
var implementation = match['address'];
// 过滤需要拦截的方法objc_method
if ((method.indexOf("objc_method") != -1)) {
console.log(match['name'] + ":" + match['address']);
try {
Interceptor.attach(implementation, {
onEnter: function(args) {
//参数打印
var className = ObjC.Object(args[0]);
var methodName = args[1];
var arg_info = ObjC.Object(args[2]);
console.log("className: " + className.toString());
console.log("methodName: " + methodName.readUtf8String());
console.log("arg_info: " + arg_info.toString());
},
onLeave: function(retval) {
}
});
} catch (err) {
console.log("[!] Exception: " + err.message);
}
}
},
onComplete: function() {
}
});
4.hook oc 方法2:implementation
//hook +[NSURL URLWithString:]
var method = ObjC.classes.NSURL['+ URLWithString:'];
var origImp = method.implementation;
method.implementation = ObjC.implement(method, function (self, sel, url){
console.log("+ [NSURL URLWithString:]");
var urlString = ObjC.Object(url);
console.log("url: " + urlString.toString());
return origImp(self, sel, url); //调用原方法,如果不调用则原方法得不到执行
//替换参数,将 URL 替换成 http://www.ioshacker.net
//var newUrl = ObjC.classes.NSString.stringWithString_("http://www.ioshacker.net");
//return origImp(self, sel, newUrl);
});
MonkeyDev:
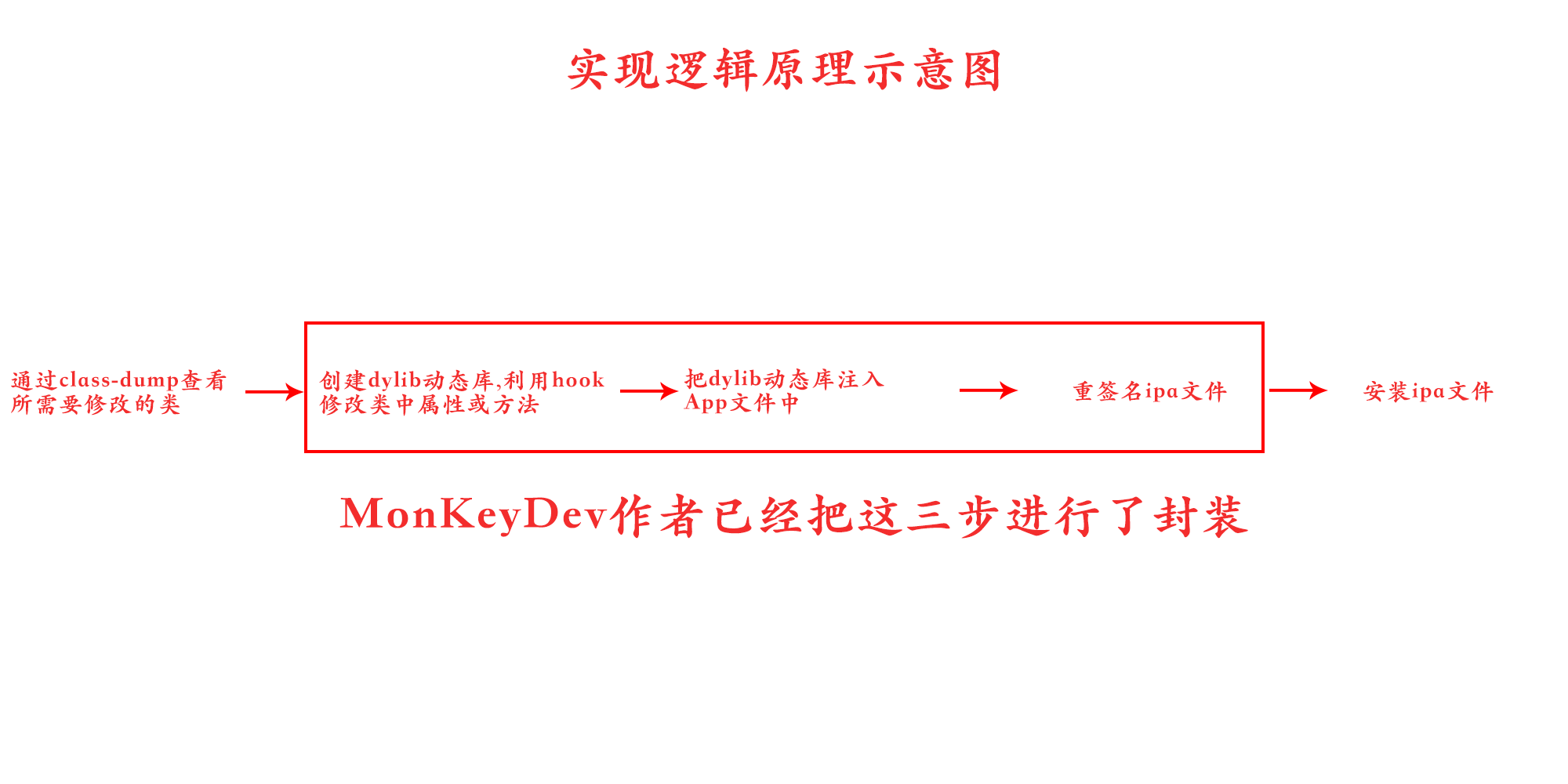
1.CaptainHook:使用CaptainHook提供的头文件进行OC 函数的Hook以及属性的获取。
CHDeclareClass(objC);
CHClassMethod2(id, objC, objc_method, id, arg1, andKeys, id, arg2){
NSLog(@"参数1:%@",arg1);
NSLog(@"参数2:%@",arg2);
id result = CHSuper2(objC, objc_method, arg1, andKeys, arg2);
NSLog(@"jieguo:%@",result);
return result;
}
CHConstructor{
CHLoadLateClass(objC);
CHClassHook2(objC, objc_method, andKeys);
}
类主动调用
SEL sel = @selector(obj_c:andKeys:); return ((id (*)(Class _Nullable, SEL _Nonnull, id, id))(void *)objc_msgSend)(objc, sel, arg1, arg2);
2.Logos hook:官网文档
%hook SBApplicationController
-(void)uninstallApplication:(SBApplication *)application {
NSLog(@"Hey, we're hooking uninstallApplication:!");
%orig; // Call the original implementation of this method
return;
}
%end
3.Method Swizzing hook
#import "UIDevice Swizzing.h"
#import <Foundation/Foundation.h>
#import <UIKit/UIKit.h>
#import <objc-runtime.h>
@implementation UIDevice (swizzling)
+ (void)load{
static dispatch_once_t onceToken;
dispatch_once(&onceToken,^{
Class class = [self class];
SEL originalSelector = @selector(systemVersion);
SEL swizzledSelector = @selector(NewsystemVersion);
Method originalMethod = class_getInstanceMethod(class, originalSelector);
Method swizzledMethod = class_getInstanceMethod(class, swizzledSelector);
method_exchangeImplementations(originalMethod, swizzledMethod);
});
}
-(NSString*) NewsystemVersion {
NSLog(@"systemVersion method swizzing..........");
NSString *strVer = @"0.0.1";
// NssTring *strVer = [self NewsystemVersion];
return strVer;
}
@end
4.finshhook
+ (void)load{
struct rebinding ptracebd;
// 要hook的方法名
ptracebd.name = "ptrace";
// 保存原来方法的地址
ptracebd.replaced = (void *)&ptrace_p;
// 新方法
ptracebd.replacement = myPtrace;
struct rebinding bds[] = {ptracebd};
rebind_symbols(bds, 1);
}
// 函数指针
int (*ptrace_p)(int _request, pid_t _pid, caddr_t _addr, int _data);
// 新函数
int myPtrace(int _request, pid_t _pid, caddr_t _addr, int _data){
if(_request == PT_DENY_ATTACH){
return 0;
}
return ptrace_p(_request, _pid, _addr, _data);
}
参考:https://bbs.pediy.com/thread-259910.htm