挖掘经验:遇到的比较多的就是出现在cookie验证上面,通常是没有使用session来认证,直接将用户信息保存在cookie中
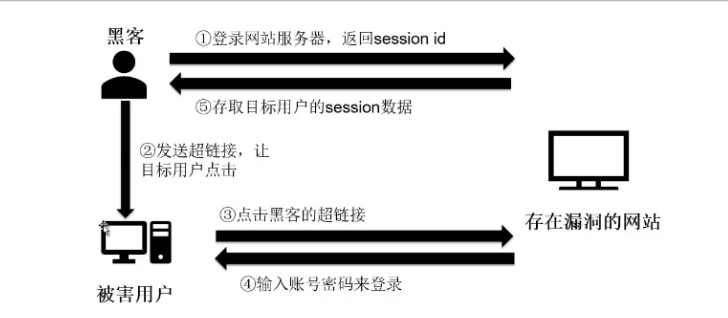
Session固定攻击:
黑客固定住目标用户的session id,所以目标用户使用的session可以由攻击者指定
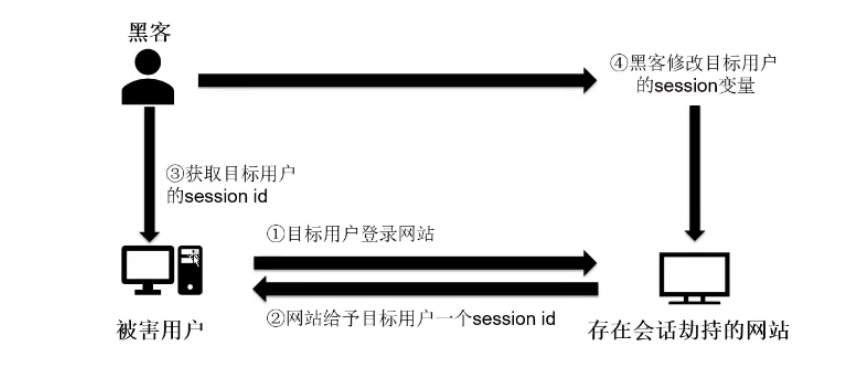
Session劫持攻击:
黑客劫持目标用户的session id俩获取网站服务器上未经许可的存取信息,特别是窃取目标用户的cookie数据,来取得网站的认可
代码:
espcms任意用户登录分析
在文件espcms/upload/memebermain.php的in_center()函数可以看到如下代码:
function in_center() {
if ($this->CON[‘mem_isucenter’]) {
include_once admin_ROOT . ‘public/uc_client/client.php’;
}
parent::start_pagetemplate();
parent::member_purview();
$lng = (admin_LNG == ‘big5’) ? $this->CON[‘is_lancode’] : admin_LNG;
$db_where = “userid=$this->ec_member_username_id AND username=’$this->ec_member_username’ “;
$db_table1 = db_prefix . ‘member AS a’;
$db_table2 = db_prefix . ‘member_value AS b’;
$db_sql = “SELECT a.*,b.mvid,b.value FROM $db_table1 LEFT JOIN $db_table2 ON a.userid = b.userid WHERE a.userid = $this->ec_member_username_id “;
$rsMember = $this->db->fetch_first($db_sql);
$rsMember[‘rankname’] = $this->get_member_purview($rsMember[‘mcid’], ‘rankname’);
$userid = $rsMember[‘userid’];
if (empty($userid)) {
exit(‘user err!’);
}
$db_table = db_prefix . “order”;
$db_where = " WHERE userid=$userid";
$db_where2 = " WHERE userid=$userid and ordertype=1";
$db_where3 = " WHERE userid=$userid and ordertype=3";
$this->pagetemplate->assign('ordernum', $this->db_numrows($db_table, $db_where));
$this->pagetemplate->assign('ordernum2', $this->db_numrows($db_table, $db_where2));
$this->pagetemplate->assign('ordernum3', $this->db_numrows($db_table, $db_where3));
$db_table = db_prefix . "bbs";
$db_where = " WHERE userid=$userid";
在代码中$_userid=$this->ec_member_username_id;这行代码这只当前用户id,随后根据这个$userid变量去直接操作这个id的用户数据。
接下来,根据parent::member_purview()函数跟到espcms/upload/public/class_connector.php文件的member_purview()函数,代码如下:
function member_purview($userrank=false, $url=null, $upurl=false) {
$this->ec_member_username = $this->fun->eccode($this->fun->accept('ecisp_member_username', 'C'), 'DECODE', db_pscode);
$user_info = explode('|', $this->fun->eccode($this->fun->accept('ecisp_member_info', 'C'), 'DECODE', db_pscode));
list($this->ec_member_username_id, $this->ec_member_alias, $this->ec_member_integral, $this->ec_member_mcid, $this->ec_member_email, $this->ec_member_lastip, $this->ec_member_ipadd, $this->ec_member_useragent, $this->ec_member_adminclassurl) = $user_info;
list()函数中使用$user_info数组为$this->ec_member_username_id变量进行赋值,而$user_info数组是从cookie中解密出来的,关于这个算法的加密代码在espcms/upload/public/class_function.php文件的eccode()函数
修复方案:
使用随机而且长度够大的数字或字符串来当做session id
将网页之间传递的数据使用某种形式封装,特别是session id
更改session名称
注销后销毁session的所有数据
友情链接 http://www.cnblogs.com/klionsec
http://www.feiyusafe.cn