升级版本
3.0.2 版本升级到 redis-3.2.0 版本远程无法访问,比较配置文件有些变化,比如默认只能本地的机器才能访问
3.0.2 版本
# By default Redis listens for connections from all the network interfaces
# available on the server. It is possible to listen to just one or multiple
# interfaces using the "bind" configuration directive, followed by one or
# more IP addresses.
#
# Examples:
#
# bind 192.168.1.100 10.0.0.1
# bind 127.0.0.1
redis-3.2.0版本
# By default, if no "bind" configuration directive is specified, Redis listens
# for connections from all the network interfaces available on the server.
# It is possible to listen to just one or multiple selected interfaces using
# the "bind" configuration directive, followed by one or more IP addresses.
#
# Examples:
#
# bind 192.168.1.100 10.0.0.1
# bind 127.0.0.1 ::1
#
# ~~~ WARNING ~~~ If the computer running Redis is directly exposed to the
# internet, binding to all the interfaces is dangerous and will expose the
# instance to everybody on the internet. So by default we uncomment the
# following bind directive, that will force Redis to listen only into
# the IPv4 lookback interface address (this means Redis will be able to
# accept connections only from clients running into the same computer it
# is running).
#
# IF YOU ARE SURE YOU WANT YOUR INSTANCE TO LISTEN TO ALL THE INTERFACES
# JUST COMMENT THE FOLLOWING LINE.
# ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
# bind 127.0.0.1
# Protected mode is a layer of security protection, in order to avoid that
# Redis instances left open on the internet are accessed and exploited.
#
# When protected mode is on and if:
#
# 1) The server is not binding explicitly to a set of addresses using the
# "bind" directive.
# 2) No password is configured.
#
# The server only accepts connections from clients connecting from the
# IPv4 and IPv6 loopback addresses 127.0.0.1 and ::1, and from Unix domain
# sockets.
#
# By default protected mode is enabled. You should disable it only if
# you are sure you want clients from other hosts to connect to Redis
# even if no authentication is configured, nor a specific set of interfaces
# are explicitly listed using the "bind" directive.
protected-mode yes
安全
##Redis 配置
http://redis.io/download
http://redis.io/documentation
######编译包
yum update
yum -y install gcc gcc-c++ autoconf automake make
######下载编译
wget http://download.redis.io/releases/redis-3.2.0.tar.gz
tar xzf redis-3.2.0.tar.gz
cd redis-3.2.0
make
######编译测试
yum install tcl
make test
######注释bind
# bind 127.0.0.1
######守护进程启动
daemonize yes
#保护模式[无密码模式设置为no]
protected-mode no
#设置密码
requirepass test
######数据文件路径
dir /opt/data/
######日志文件路径
logfile "/opt/data/redis.log"
######缓存数据名称
dbfilename dump.rdb
#查看防火墙关闭状态
service iptables status
######关闭命令
service iptables stop
######永久关闭防火墙
chkconfig iptables off
######主从
配置一个从服务器非常简单,只要在配置文件中增加以下的这一行就可以了:
slaveof 192.168.210.31 6379
SLAVEOF 192.168.210.31 6379
######启动
src/redis-server /opt/redis-3.2.0/redis.conf
######测试
$ src/redis-cli
redis> set foo bar
OK
redis> get foo
"bar"
######查看进程
ps -ef | grep redis
######杀死进程
kill -9 25946
监控
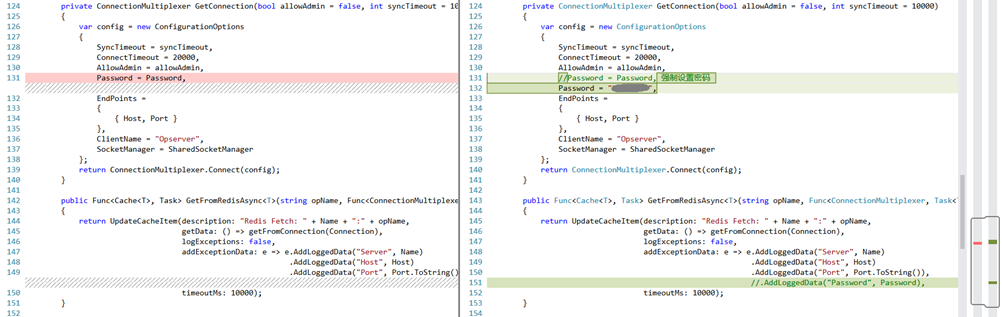
监控是使用的Opserver,启用了密码后,官方也没有相关配置的文档,调试了代码,强制设置了默认的密码。
REFER:
请务必注意 Redis 安全配置,否则将导致轻松被入侵
https://ruby-china.org/topics/28094
记一次Redis被攻击的事件
http://www.cnblogs.com/yangecnu/p/An-Production-Accidents-Caused-by-Redis-Attacked.html
Redis 未授权访问缺陷可轻易导致系统被黑
http://www.oschina.net/news/67975/redis-defect
Redis3.0与3.2文件对比
https://carlosfu.iteye.com/blog/2303254