Author:LEOGG
Misc
misc1 颜文字之谜
http导出对象,有个index-demo.html
查看源码里面有一大段base64
base64隐写得到key:lorrie
snow隐写,注意不要加-C
snow.exe -p lorrie index-demo.html
flag{→_→←_←←_←←_←←_← →_→→_→←_←←_←←_← →_→←_←←_←←_← ←_←←_←←_←→_→→_→ ←_←←_←←_←→_→→_→ ←_← ←_←←_←←_←→_→→_→ →_→→_→→_→→_→←_← →_→←_←←_←←_← ←_←←_←←_←←_←←_← ←_←→_→→_→→_→→_→ →_→→_→→_→→_→→_→ ←_←←_←←_←←_←←_← ←_←←_←→_→←_← →_→←_←←_←←_← ←_←←_←←_←←_←→_→ ←_←→_→ ←_←←_←→_→→_→→_→ →_→→_→→_→→_→←_← ←_←←_←←_←←_←←_← ←_←←_←←_←→_→→_→ ←_←→_→ →_→→_→→_→→_→→_→ →_→←_←→_→←_← ←_← →_→→_→←_←←_←←_← →_→→_→→_→→_→←_← →_→←_←→_→←_← ←_←←_←←_←→_→→_→ ←_←←_←←_←→_→→_→ →_→→_→←_←←_←←_← →_→→_→→_→←_←←_←}
联想到摩斯电码,只有两个符号和空格组成
→_→替换成-
←_←替换成.
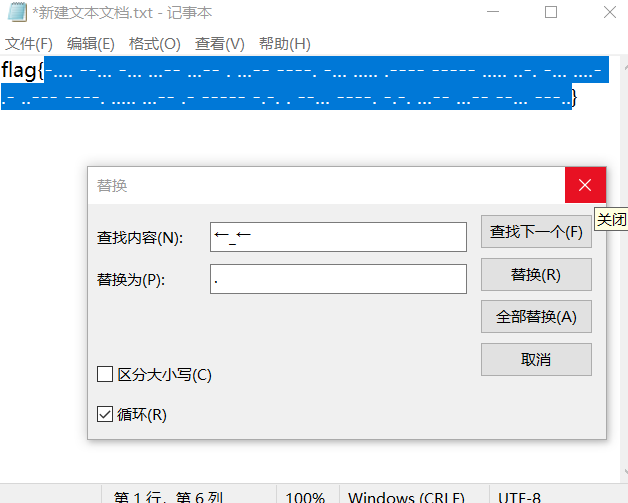
在线网站解一下转小写得到flag
misc2 passwd
hivelist查看注册表
volatility -f 555.raw --profile=Win7SP1x86 hivelist
Volatility Foundation Volatility Framework 2.6
Virtual Physical Name
---------- ---------- ----
0x93fc41e8 0x030cf1e8 SystemRootSystem32ConfigSAM
0x93fe7008 0x1bc6c008 ??C:WindowsServiceProfilesNetworkServiceNTUSER.DAT
0x9494e9c8 0x11c9a9c8 ??C:UsersCTFAppDataLocalMicrosoftWindowsUsrClass.dat
0x992de5d8 0x223cb5d8 SystemRootSystem32ConfigDEFAULT
0x8a00c2b0 0x23e0a2b0 [no name]
0x8a01c008 0x24019008 REGISTRYMACHINESYSTEM
0x8a03d008 0x22dfa008 REGISTRYMACHINEHARDWARE
0x8c6d99c8 0x22b499c8 DeviceHarddiskVolume1BootBCD
0x8e00d9c8 0x189629c8 ??C:UsersCTF
tuser.dat
0x8f97c008 0x22de2008 SystemRootSystem32ConfigSOFTWARE
0x93fb19c8 0x00a759c8 SystemRootSystem32ConfigSECURITY
0x93fb7440 0x03145440 ??C:WindowsServiceProfilesLocalServiceNTUSER.DAT
hashdump取出密码,-y是system的virtual地址,-s是SAM表的virtual地址
volatility -f 555.raw --profile=Win7SP1x86 hashdump -y 0x8a01c008 -s 0x93fc41e8
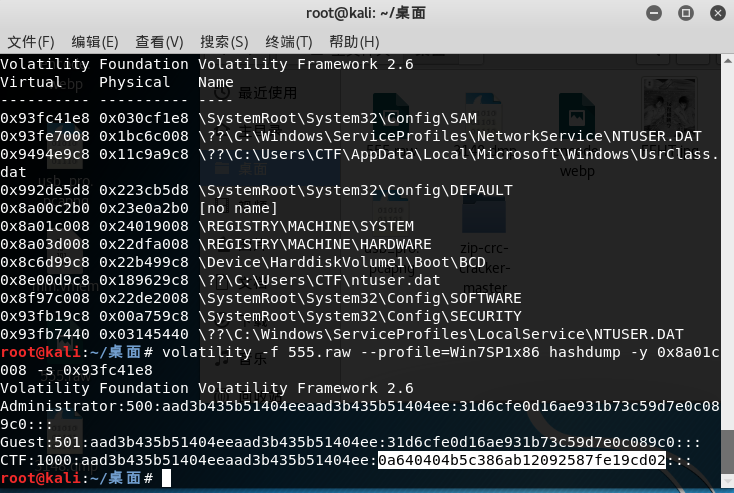
0a640404b5c386ab12092587fe19cd02去md5解密的qwer1234
再sha1()加密
ps:其实一条命令hashdump就够了,人菜就多敲一条=。=
flag:db25f2fc14cd2d2b1e7af307241f548fb03c312a
misc3 虚实之间
伪加密得到文件mingwen.txt
明文攻击得到密码
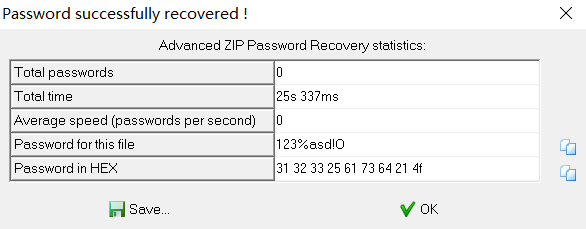
拿到flag.txt
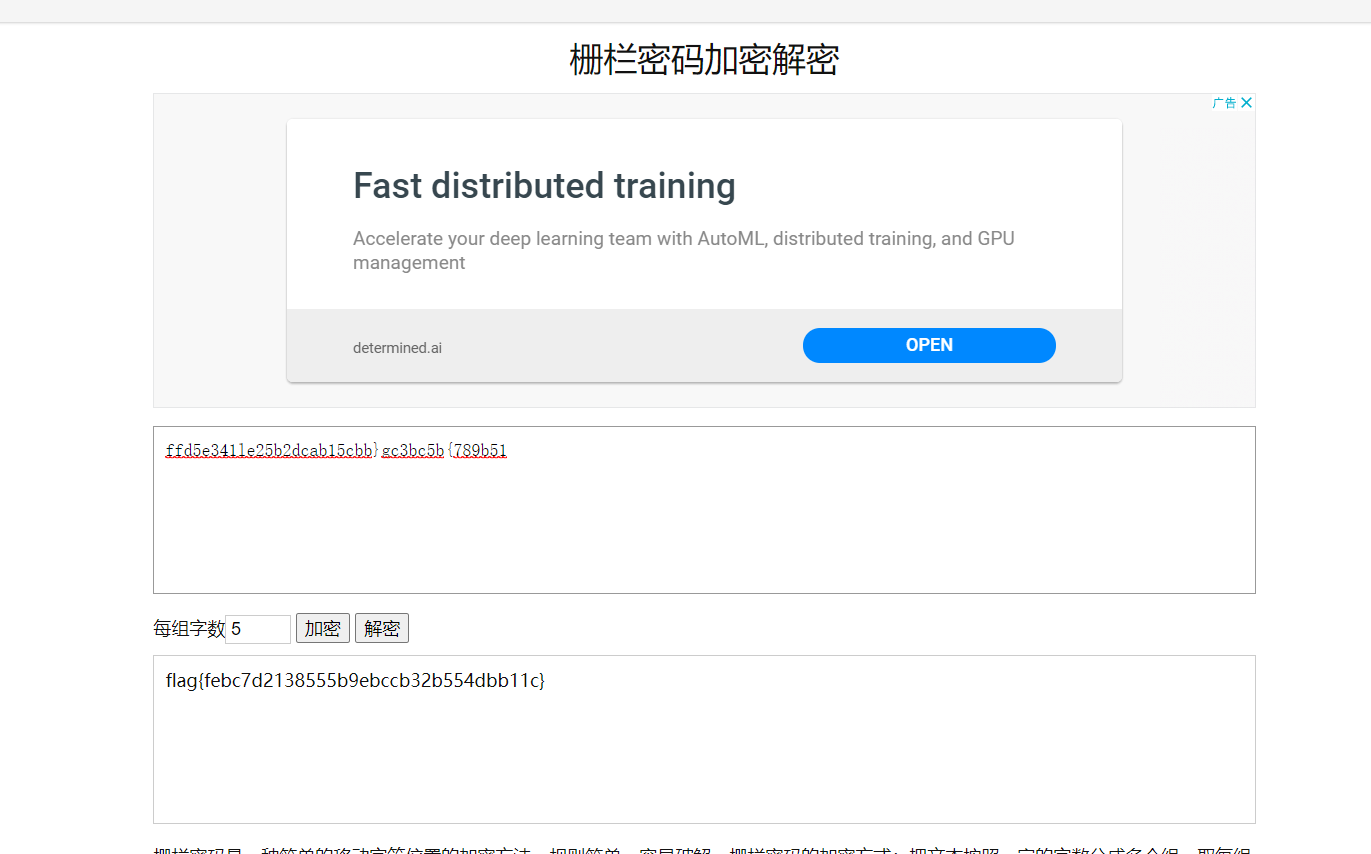
ffd5e341le25b2dcab15cbb}gc3bc5b{789b51
栅栏位数5
解密一下
ps:吐槽一下captEncoder这个小帽子解码软件,栅栏有问题
misc4 隐藏的秘密
先看一下pslist,找到notepad.exe,去grep一下txt文件
volatility -f mm.vmem --profile=Win2003SP1x86 filescan | grep "txt"
Volatility Foundation Volatility Framework 2.6
0x000000000412cde0 1 0 RW-r-- DeviceHarddiskVolume1Documents and SettingsAdministrator桌面file.txt
0x000000000426b890 1 0 R--rw- DeviceHarddiskVolume1Documents and SettingsAll UsersApplication DataVMwareVMware ToolsUnity Filterswin7gadgets.txt
0x000000000426ba90 1 0 R--rw- DeviceHarddiskVolume1Documents and SettingsAll UsersApplication DataVMwareVMware ToolsUnity Filtersvmwarefilters.txt
0x000000000426bc90 1 0 R--rw- DeviceHarddiskVolume1Documents and SettingsAll UsersApplication DataVMwareVMware ToolsUnity Filtersvisualstudio2005.txt
0x000000000426be90 1 0 R--rw- DeviceHarddiskVolume1Documents and SettingsAll UsersApplication DataVMwareVMware ToolsUnity Filtersvistasidebar.txt
0x000000000479d4a8 4 2 -W-rw- DeviceHarddiskVolume1Documents and SettingsAll UsersApplication DataVMwareVMware VGAuthlogfile.txt.0
0x00000000049e1cf0 1 0 R--rw- DeviceHarddiskVolume1Program FilesVMwareVMware Toolsvmacthlp.txt
0x00000000049e6228 1 0 RW-rw- DeviceHarddiskVolume1Documents and SettingsAdministratorRecentfile.txt.lnk
0x0000000004a511a0 1 0 R--rw- DeviceHarddiskVolume1Documents and SettingsAll UsersApplication DataVMwareVMware ToolsUnity Filtersmicrosoftoffice.txt
0x0000000004a513a0 1 0 R--rw- DeviceHarddiskVolume1Documents and SettingsAll UsersApplication DataVMwareVMware ToolsUnity Filtersgoogledesktop.txt
0x0000000004a51770 1 0 R--rw- DeviceHarddiskVolume1Documents and SettingsAll UsersApplication DataVMwareVMware ToolsUnity Filtersadobephotoshopcs3.txt
0x0000000004c05370 1 0 R--rwd DeviceHarddiskVolume1Documents and SettingsAll UsersApplication DataVMwareVMware Toolsmanifest.txt
0x0000000004c70ae8 1 0 RW---- DeviceHarddiskVolume1WINDOWSsystem32CatRoot2dberr.txt
0x0000000004d44028 1 0 R--rw- DeviceHarddiskVolume1Documents and SettingsAll UsersApplication DataVMwareVMware ToolsUnity Filtersadobeflashcs3.txt
找到file.txt,dump下来
volatility -f mm.vmem --profile=Win2003SP1x86 dumpfiles -Q 0x000000000412cde0 -D ./
什么?计算机又被不知名账户登录了?明明在计算机管理中没有这个用户,为什么还会被这个用户登录呢?电脑跟前的你能帮我找到原因吗?flag为该用户的用户名以及密码的md5值。
格式:md5(用户名:密码)
hivelist查看注册表,找到最近登陆的用户,使用WRR(windows registry recovery)查找注册表
volatility -f mm.vmem --profile=Win2003SP1x86 dumpregistry -D ./
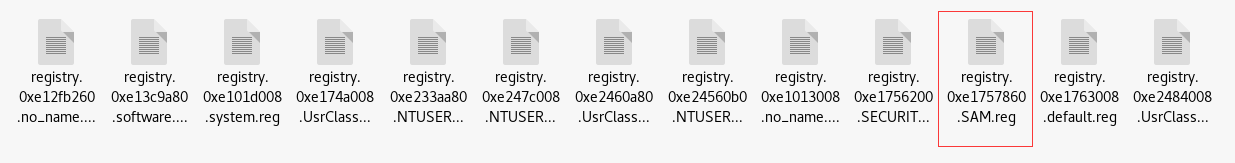
查SAM表
根据最近登陆的用户发现只有Administrator和FHREhpe登陆过
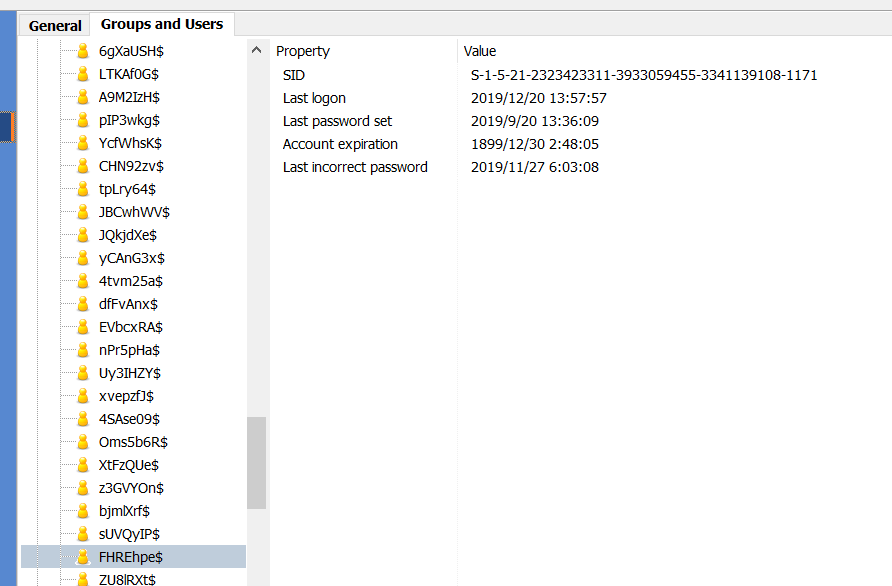
列出用户名和密码
volatility -f mm.vmem --profile=Win2003SP1x86 hashdump -y 0xe101d008 -s 0xe1757860
得到用户名密码,md5解密一下FHREhpe$:NIAIWOMA
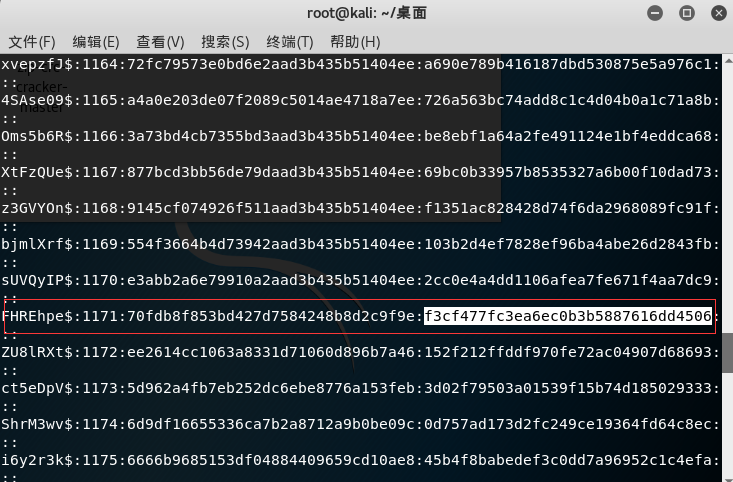
md5加密一下
flag:8cf1d5b00c27cb8284bce9ccecb09fb7