测试文件:https://adworld.xctf.org.cn/media/task/attachments/fac4d1290e604fdfacbbe06fd1a5ca39.exe
1.准备

获取信息:
- 32位文件
2.IDA打开
打开main函数
1 int __cdecl main(int argc, const char **argv, const char **envp) 2 { 3 void *v3; // eax 4 int v4; // edx 5 void *v5; // eax 6 int result; // eax 7 void *v7; // eax 8 void *v8; // eax 9 void *v9; // eax 10 size_t i; // [esp+4Ch] [ebp-8Ch] 11 char v11[4]; // [esp+50h] [ebp-88h] 12 char v12[28]; // [esp+58h] [ebp-80h] 13 char v13; // [esp+74h] [ebp-64h] 14 15 v3 = (void *)sub_402B30(&unk_446360, "Give me your flag:");// 这两段代码直接理解成printf即可。下面的代码同样如此 16 sub_4013F0(v3, (int (__cdecl *)(void *))sub_403670); 17 sub_401440((int)&dword_4463F0, v4, (int)v12, 127); 18 if ( strlen(v12) < 30 && strlen(v12) > 4 ) 19 { 20 strcpy(v11, "EIS{"); 21 for ( i = 0; i < strlen(v11); ++i ) 22 { 23 if ( v12[i] != v11[i] ) // flag前四位为"ESI{" 24 { 25 v7 = (void *)sub_402B30(&unk_446360, "Sorry, keep trying! "); 26 sub_4013F0(v7, (int (__cdecl *)(void *))sub_403670); 27 return 0; 28 } 29 } 30 if ( v13 == 125 ) 31 { 32 if ( sub_4011C0(v12) ) 33 v9 = (void *)sub_402B30(&unk_446360, "Congratulations! "); 34 else 35 v9 = (void *)sub_402B30(&unk_446360, "Sorry, keep trying! "); 36 sub_4013F0(v9, (int (__cdecl *)(void *))sub_403670); 37 result = 0; 38 } 39 else 40 { 41 v8 = (void *)sub_402B30(&unk_446360, "Sorry, keep trying! "); 42 sub_4013F0(v8, (int (__cdecl *)(void *))sub_403670); 43 result = 0; 44 } 45 } 46 else 47 { 48 v5 = (void *)sub_402B30(&unk_446360, "Sorry, keep trying!"); 49 sub_4013F0(v5, (int (__cdecl *)(void *))sub_403670); 50 result = 0; 51 } 52 return result; 53 }
3.代码分析
看到第32行代码
if ( sub_4011C0(v12) ) v9 = (void *)sub_402B30(&unk_446360, "Congratulations! ");
这里通过sub_4011C0(v12)传入输入的flag来判断真假,打开函数
1 bool __cdecl sub_4011C0(char *a1) 2 { 3 size_t v2; // eax 4 signed int v3; // [esp+50h] [ebp-B0h] 5 char v4[32]; // [esp+54h] [ebp-ACh] 6 int v5; // [esp+74h] [ebp-8Ch] 7 int v6; // [esp+78h] [ebp-88h] 8 size_t i; // [esp+7Ch] [ebp-84h] 9 char v8[128]; // [esp+80h] [ebp-80h] 10 11 if ( strlen(a1) <= 4 ) 12 return 0; 13 i = 4; 14 v6 = 0; 15 while ( i < strlen(a1) - 1 ) 16 v8[v6++] = a1[i++]; 17 v8[v6] = 0; 18 v5 = 0; 19 v3 = 0; 20 memset(v4, 0, 0x20u); 21 for ( i = 0; ; ++i ) 22 { 23 v2 = strlen(v8); 24 if ( i >= v2 ) 25 break; 26 if ( v8[i] >= 97 && v8[i] <= 122 ) 27 { 28 v8[i] -= 32; 29 v3 = 1; 30 } 31 if ( !v3 && v8[i] >= 65 && v8[i] <= 90 ) 32 v8[i] += 32; 33 v4[i] = byte_4420B0[i] ^ sub_4013C0(v8[i]); 34 v3 = 0; 35 } 36 return strcmp("GONDPHyGjPEKruv{{pj]X@rF", v4) == 0; 37 }
这里i是从4开始即flag的第四位开始,对flag的操作分为了两部分:
- 第26行代码~第32行代码,将flag中的大写字母转小写,小写字母转大写。
- 第33行代码对每位字符进行异或操作。
第一步不必多说,第二步byte_4420B0数组从文件中提取出来
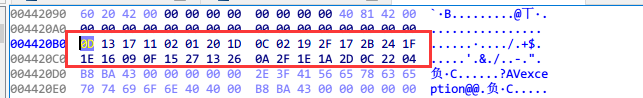
0D 13 17 11 02 01 20 1D 0C 02 19 2F 17 2B 24 1F 1E 16 09 0F 15 27 13 26 0A 2F 1E 1A 2D 0C 22 04
sub_4013C0(v8[i])函数为
int __cdecl sub_4013C0(int a1) { return (a1 ^ 0x55) + 72; }
最后得到的字符串V4为
GONDPHyGjPEKruv{{pj]X@rF
因此我们只需要逆向操作还原flag即可
4.脚本获取
n = 28 val1 = [0x0D,0x13,0x17,0x11,0x02,0x01,0x20,0x1D,0x0C,0x02,0x19,0x2F,0x17,0x2B, 0x24,0x1F,0x1E,0x16,0x09,0x0F,0x15,0x27,0x13,0x26,0x0A,0x2F,0x1E,0x1A, 0x2D,0x0C,0x22,0x04] v4 = "GONDPHyGjPEKruv{{pj]X@rF" v8 = "" flag = "" for i in range(len(v4)): v8 += chr(((ord(v4[i]) ^ val1[i]) - 72) ^ 0x55) for i in range(len(v8)): if ord(v8[i]) >= 97 and ord(v8[i]) <= 122: flag += chr(ord(v8[i]) - 32) elif ord(v8[i]) >= 65 and ord(v8[i]) <= 90: flag += chr(ord(v8[i]) + 32) else: flag += v8[i] print('EIS{'+flag+'}')
5.get flag!
EIS{wadx_tdgk_aihc_ihkn_pjlm}