OpenLDAP安装与配置
初始化安装环境
sed -i '/SELINUX/s/enforcing/disabled/' /etc/selinux/config
setenforce 0
systemctl disable firewalld.service
systemctl stop firewalld.service
为了避免单点故障,通常都会采用双机环境。使用OpenLDAP复制同步功能,保持Master与Slave的数据一致性
Ldap Master : 提供所有的更新、修改
Ldap Slave : 提供给各种应用(jira, zabbix, svn ...)调用
安装OpenLDAP
yum -y install openldap compat-openldap openldap-clients openldap-servers openldap-servers-sql openldap-devel migrationtools
# 查看Ldap版本
slapd -VV
启动OpenLDAP
systemctl enable slapd
systemctl start slapd
systemctl status slapd
配置OpenLDAP
设置OpenLDAP的管理员密码
slappasswd -s LDAP@2018
加密后的字段保存下,等在配置文件中会使用到
导入chrootpw.ldif文件
cd /etc/openldap/
vim chrootpw.ldif
# specify the password generated above for "olcRootPW" section
dn: olcDatabase={0}config,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}HS5Bu2oNnnGe+G7OaWCtfnPBJUz7G2k2
ldapadd -Y EXTERNAL -H ldapi:/// -f chrootpw.ldif
导入基本Schema
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
设置Domain Name
首先要生成经处理后的目录管理者明文密码
slappasswd -s LDAP@2018
导入chdomain.ldif文件,使用域名test.com,一定注意修改olcRootPW参数
cd /etc/openldap
vim chdomain.ldif
# replace to your own domain name for "dc=***,dc=***" section
# specify the password generated above for "olcRootPW" section
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth"
read by dn.base="cn=Manager,dc=test,dc=com" read by * none
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=test,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=Manager,dc=test,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}eTMA99w62m1Oslr8FjNXwmFplJyZK+ei
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcAccess
olcAccess: {0}to attrs=userPassword,shadowLastChange by
dn="cn=Manager,dc=test,dc=com" write by anonymous auth by self write by * none
olcAccess: {1}to dn.base="" by * read
olcAccess: {2}to * by dn="cn=Manager,dc=test,dc=com" write by * read
ldapmodify -Y EXTERNAL -H ldapi:/// -f chdomain.ldif
导入basedomain.ldif文件
cd /etc/openldap
vim basedomain.ldif
# replace to your own domain name for "dc=***,dc=***" section
dn: dc=test,dc=com
objectClass: top
objectClass: dcObject
objectclass: organization
o: Server Com
dc: test
dn: cn=Manager,dc=test,dc=com
objectClass: organizationalRole
cn: Manager
description: Directory Manager
dn: ou=People,dc=test,dc=com
objectClass: organizationalUnit
ou: People
dn: ou=Group,dc=test,dc=com
objectClass: organizationalUnit
ou: Group
ldapadd -x -D cn=Manager,dc=test,dc=com -W -f basedomain.ldif
向OpenLDAP Server中添加用户
首先要生成经处理后的明文密码
slappasswd -s LDAP@2018
vim ldapuser.ldif
# create new user jerryhuang
# replace to your own domain name for "dc=***,dc=***" section
dn: uid=jerryhuang,ou=People,dc=test,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
cn: jerryhuang
sn: Linux
userPassword: {SSHA}SFmmNnCFHAyNZ4jFXUmDDsRXams3VABh
loginShell: /bin/bash
uidNumber: 1000
gidNumber: 1000
homeDirectory: /home/jerryhuang
dn: cn=jerryhuang,ou=Group,dc=test,dc=com
objectClass: posixGroup
cn: jerryhuang
gidNumber: 1000
memberUid: jerryhuang
ldapadd -x -D cn=Manager,dc=test,dc=com -W -f ldapuser.ldif
添加本机的系统用户和群组到ldap目录
脚本SUFFIX变量替换为自己的域名
vim ldapuser.sh
# extract local users and groups who have 1000-9999 digit UID
# replace "SUFFIX=***" to your own domain name
# this is an example
#!/bin/bash
SUFFIX='dc=test,dc=com'
LDIF='ldapuser.ldif'
echo -n > $LDIF
GROUP_IDS=()
grep "x:[1-9][0-9][0-9][0-9]:" /etc/passwd | (while read TARGET_USER
do
USER_ID="$(echo "$TARGET_USER" | cut -d':' -f1)"
USER_NAME="$(echo "$TARGET_USER" | cut -d':' -f5 | cut -d' ' -f1,2)"
[ ! "$USER_NAME" ] && USER_NAME="$USER_ID"
LDAP_SN="$(echo "$USER_NAME" | cut -d' ' -f2)"
[ ! "$LDAP_SN" ] && LDAP_SN="$USER_NAME"
LASTCHANGE_FLAG="$(grep "${USER_ID}:" /etc/shadow | cut -d':' -f3)"
[ ! "$LASTCHANGE_FLAG" ] && LASTCHANGE_FLAG="0"
SHADOW_FLAG="$(grep "${USER_ID}:" /etc/shadow | cut -d':' -f9)"
[ ! "$SHADOW_FLAG" ] && SHADOW_FLAG="0"
GROUP_ID="$(echo "$TARGET_USER" | cut -d':' -f4)"
[ ! "$(echo "${GROUP_IDS[@]}" | grep "$GROUP_ID")" ] && GROUP_IDS=("${GROUP_IDS[@]}" "$GROUP_ID")
echo "dn: uid=$USER_ID,ou=People,$SUFFIX" >> $LDIF
echo "objectClass: inetOrgPerson" >> $LDIF
echo "objectClass: posixAccount" >> $LDIF
echo "objectClass: shadowAccount" >> $LDIF
echo "sn: $LDAP_SN" >> $LDIF
echo "givenName: $(echo "$USER_NAME" | awk '{print $1}')" >> $LDIF
echo "cn: $USER_NAME" >> $LDIF
echo "displayName: $USER_NAME" >> $LDIF
echo "uidNumber: $(echo "$TARGET_USER" | cut -d':' -f3)" >> $LDIF
echo "gidNumber: $(echo "$TARGET_USER" | cut -d':' -f4)" >> $LDIF
echo "userPassword: {crypt}$(grep "${USER_ID}:" /etc/shadow | cut -d':' -f2)" >> $LDIF
echo "gecos: $USER_NAME" >> $LDIF
echo "loginShell: $(echo "$TARGET_USER" | cut -d':' -f7)" >> $LDIF
echo "homeDirectory: $(echo "$TARGET_USER" | cut -d':' -f6)" >> $LDIF
echo "shadowExpire: $(passwd -S "$USER_ID" | awk '{print $7}')" >> $LDIF
echo "shadowFlag: $SHADOW_FLAG" >> $LDIF
echo "shadowWarning: $(passwd -S "$USER_ID" | awk '{print $6}')" >> $LDIF
echo "shadowMin: $(passwd -S "$USER_ID" | awk '{print $4}')" >> $LDIF
echo "shadowMax: $(passwd -S "$USER_ID" | awk '{print $5}')" >> $LDIF
echo "shadowLastChange: $LASTCHANGE_FLAG" >> $LDIF
echo >> $LDIF
done
for TARGET_GROUP_ID in "${GROUP_IDS[@]}"
do
LDAP_CN="$(grep ":${TARGET_GROUP_ID}:" /etc/group | cut -d':' -f1)"
echo "dn: cn=$LDAP_CN,ou=Group,$SUFFIX" >> $LDIF
echo "objectClass: posixGroup" >> $LDIF
echo "cn: $LDAP_CN" >> $LDIF
echo "gidNumber: $TARGET_GROUP_ID" >> $LDIF
for MEMBER_UID in $(grep ":${TARGET_GROUP_ID}:" /etc/passwd | cut -d':' -f1,3)
do
UID_NUM=$(echo "$MEMBER_UID" | cut -d':' -f2)
[ $UID_NUM -ge 1000 -a $UID_NUM -le 9999 ] && echo "memberUid: $(echo "$MEMBER_UID" | cut -d':' -f1)" >> $LDIF
done
echo >> $LDIF
done
)
执行该脚本,会生成 ldapuser.ldif 文件
导入该文件
ldapadd -x -D cn=Manager,dc=test,dc=com -W -f ldapuser.ldif
删除LDAP用户或组
删除用户:
ldapdelete -x -W -D 'cn=Manager,dc=test,dc=com' "uid=ldapuser,ou=People,dc=test,dc=com"
删除组:
ldapdelete -x -W -D 'cn=Manager,dc=test,dc=com' "cn=ldapgroup,ou=Group,dc=test,dc=com"
查询OpenLDAP的相关信息
用户和用户组全部导入完毕后,我们就可以查询OpenLDAP的相关信息
查询OpenLDAP全部信息,使用如下命令:
ldapsearch -x -b "dc=test,dc=com" -H ldap://127.0.0.1
查询添加的OpenLDAP用户信息,使用如下命令:
ldapsearch -LLL -x -D 'cn=Manager,dc=test,dc=com' -w "LDAP@2018" -b 'dc=test,dc=com' 'uid=jerryhuang'
把OpenLDAP用户加入到用户组
现在我们要把ldapuser用户加入到ldapgroup用户组,需要新建添加用户到用户组的ldif文件
cat > add_user_to_groups.ldif << "EOF"
dn: cn=ldapgroup,ou=Group,dc=test,dc=com
changetype: modify
add: memberuid
memberuid: ldapuser
EOF
执行如下命令:
ldapadd -x -w "LDAP@2018" -D "cn=Manager,dc=test,dc=com" -f add_user_to_groups.ldif
开启OpenLADP日志访问功能
默认情况下OpenLDAP是没有启用日志记录功能,但是在实际使用过程中,为了定位问题需要使用OpenLDAP日志
cat > loglevel.ldif << "EOF"
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: stats
EOF
导入到OpenLDAP中,并重启OpenLDAP服务
ldapmodify -Y EXTERNAL -H ldapi:/// -f loglevel.ldif
修改rsyslog配置文件,并重启rsyslog服务
cat >> /etc/rsyslog.conf << "EOF"
local4.* /var/log/slapd.log
EOF
systemctl restart rsyslog
systemctl restart slapd
查看日志
tail -f /var/log/slapd.log
修改OpenLDAP默认监听端口
例如我们现在把OpenLDAP监听的端口修改为4567
vim /etc/sysconfig/slapd
SLAPD_URLS="ldapi://0.0.0.0:4567/ ldap://0.0.0.0:4567/"
# 重启OpenLDAP服务
systemctl restart slapd.service
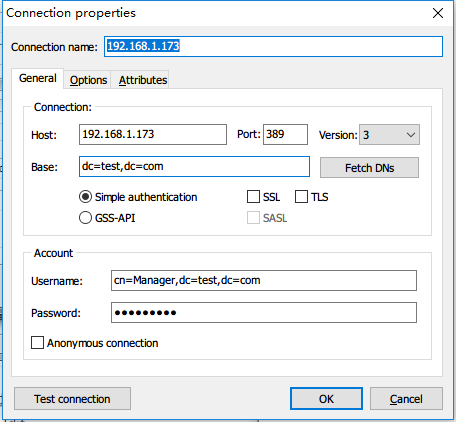
配置 LDAP 客户端 (服务器端ip:192.168.1.173)
yum install -y openldap-clients nss-pam-ldapd authconfig authconfig-gtk
执行命令
authconfig --enableldap
--enableldapauth
--ldapserver=192.168.1.173
--ldapbasedn="dc=test,dc=com"
--enablemkhomedir
--update
使用LDAP Admin管理OpenLDAP