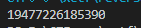
1、base64
Y3liZXJwZWFjZXtXZWxjb21lX3RvX25ld19Xb3JsZCF9
2、Caesar
凯撒加密
oknqdbqmoq{kag_tmhq_xqmdzqp_omqemd_qzodkbfuaz}

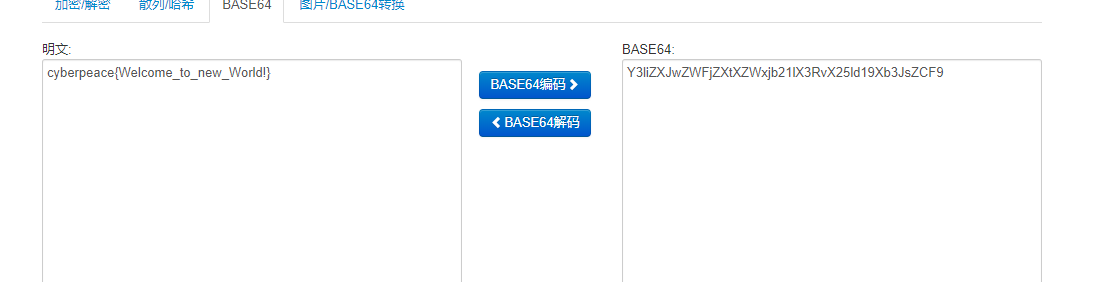
3、Morse
摩斯密码(摩尔斯密码)
11 111 010 000 0 1010 111 100 0 00 000 000 111 00 10 1 0 010 0 000 1 00 10 110
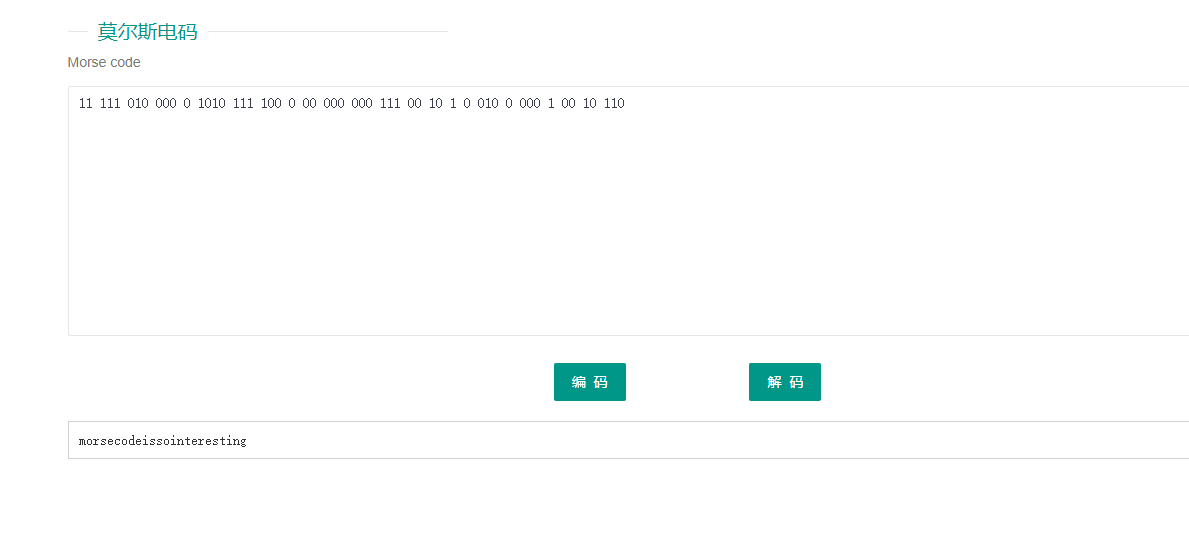
4、幂数加密
8842101220480224404014224202480122
把数字串用 0 分割开后,再将每组密码相加后的和代换为字符
1 a = [23, 5, 12, 12, 4, 15, 14, 5] 2 s = '' 3 for i in range(26): 4 s += chr(i+0x41) 5 flag = '' 6 for i in a: 7 flag += s[i-1] 8 print(flag)
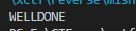
5、Railfence
ccehgyaefnpeoobe{lcirg}epriec_ora_g
栅栏密码 w型
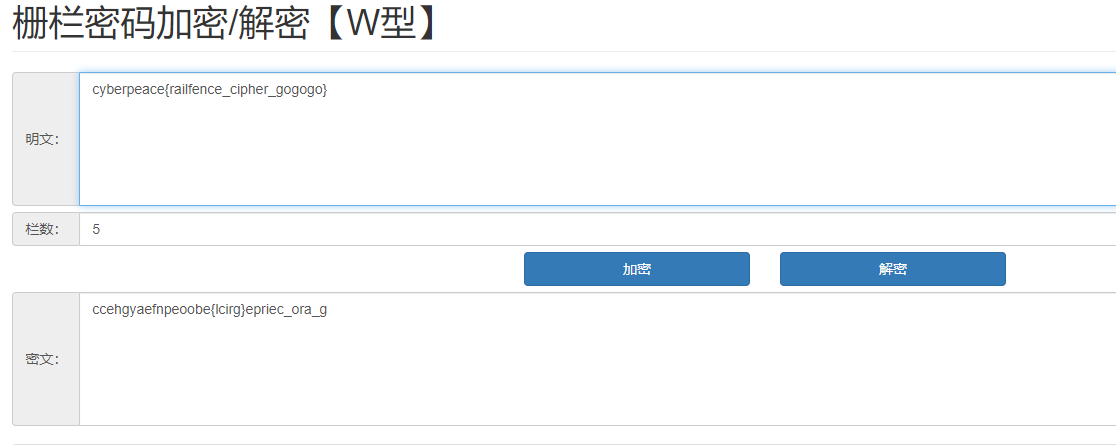
6、不仅仅是Morse
--/.-/-.--/..--.-/-..././..--.-/..../.-/...-/./..--.-/.-/-./---/-/...././.-./..--.-/-.././-.-./---/-.././..../..../..../..../.-/.-/.-/.-/.-/-.../.-/.-/-.../-.../-.../.-/.-/-.../-.../.-/.-/.-/.-/.-/.-/.-/.-/-.../.-/.-/-.../.-/-.../.-/.-/.-/.-/.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../-.../.-/.-/.-/-.../-.../.-/.-/-.../.-/.-/.-/.-/-.../.-/-.../.-/.-/-.../.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/-.../-.../.-/.-/-.../-.../-.../.-/-.../.-/.-/.-/-.../.-/-.../.-/-.../-.../.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/.-/.-/.-/-.../-.../.-/-.../-.../.-/.-/-.../-.../.-/.-/-.../.-/.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/-.../.-/.-/-.../-.../.-/-.../.-/.-/.-/.-/-.../-.../.-/-.../.-/.-/-.../-.../.-
首先将其处理为 01 串
1 a = '--/.-/-.--/..--.-/-..././..--.-/..../.-/...-/./..--.-/.-/-./---/-/...././.-./..--.-/-.././-.-./---/-.././..../..../..../..../.-/.-/.-/.-/.-/-.../.-/.-/-.../-.../-.../.-/.-/-.../-.../.-/.-/.-/.-/.-/.-/.-/.-/-.../.-/.-/-.../.-/-.../.-/.-/.-/.-/.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../-.../.-/.-/.-/-.../-.../.-/.-/-.../.-/.-/.-/.-/-.../.-/-.../.-/.-/-.../.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/-.../-.../.-/.-/-.../-.../-.../.-/-.../.-/.-/.-/-.../.-/-.../.-/-.../-.../.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/.-/.-/.-/-.../-.../.-/-.../-.../.-/.-/-.../-.../.-/.-/-.../.-/.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/-.../.-/.-/-.../-.../.-/-.../.-/.-/.-/.-/-.../-.../.-/-.../.-/.-/-.../-.../.-' 2 v = a.split('/') 3 bin_list = [] 4 for i in v: 5 value = '' 6 for j in i: 7 if j == '-': value += '1' 8 else: value += '0' 9 bin_list.append(value) 10 flag = '' 11 for i in bin_list: 12 flag += i + ' ' 13 print(flag)
莫斯密码在线转换

根据提示,还有另一种加密——培根密码

7、混合编码
JiM3NjsmIzEyMjsmIzY5OyYjMTIwOyYjNzk7JiM4MzsmIzU2OyYjMTIwOyYjNzc7JiM2ODsmIzY5OyYjMTE4OyYjNzc7JiM4NDsmIzY1OyYjNTI7JiM3NjsmIzEyMjsmIzEwNzsmIzUzOyYjNzY7JiMxMjI7JiM2OTsmIzEyMDsmIzc3OyYjODM7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiMxMDc7JiMxMTg7JiM3NzsmIzg0OyYjNjU7JiMxMjA7JiM3NjsmIzEyMjsmIzY5OyYjMTIwOyYjNzg7JiMxMDU7JiM1NjsmIzEyMDsmIzc3OyYjODQ7JiM2OTsmIzExODsmIzc5OyYjODQ7JiM5OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzUwOyYjNzY7JiMxMjI7JiM2OTsmIzEyMDsmIzc4OyYjMTA1OyYjNTY7JiM1MzsmIzc4OyYjMTIxOyYjNTY7JiM1MzsmIzc5OyYjODM7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiM5OTsmIzExODsmIzc5OyYjODQ7JiM5OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzExOTsmIzc2OyYjMTIyOyYjNjk7JiMxMTk7JiM3NzsmIzY3OyYjNTY7JiMxMjA7JiM3NzsmIzY4OyYjNjU7JiMxMTg7JiM3NzsmIzg0OyYjNjU7JiMxMjA7JiM3NjsmIzEyMjsmIzY5OyYjMTE5OyYjNzc7JiMxMDU7JiM1NjsmIzEyMDsmIzc3OyYjNjg7JiM2OTsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzExOTsmIzc2OyYjMTIyOyYjMTA3OyYjNTM7JiM3NjsmIzEyMjsmIzY5OyYjMTE5OyYjNzc7JiM4MzsmIzU2OyYjMTIwOyYjNzc7JiM4NDsmIzEwNzsmIzExODsmIzc3OyYjODQ7JiM2OTsmIzEyMDsmIzc2OyYjMTIyOyYjNjk7JiMxMjA7JiM3ODsmIzY3OyYjNTY7JiMxMjA7JiM3NzsmIzY4OyYjMTAzOyYjMTE4OyYjNzc7JiM4NDsmIzY1OyYjMTE5Ow==
base64 解密

HTML 解密

在进行一次 base64 解密
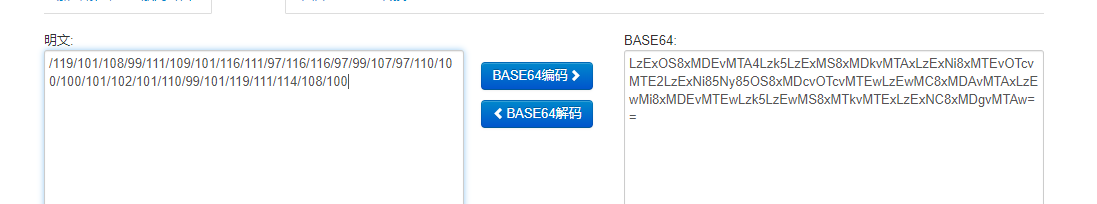
之后对得到的数字串根据 ASCII 码转换为字符串
1 a = '119/101/108/99/111/109/101/116/111/97/116/116/97/99/107/97/110/100/100/101/102/101/110/99/101/119/111/114/108/100' 2 b = a.split('/') 3 flag = '' 4 for i in b: 5 value = int(i) 6 flag += chr(value) 7 print(flag)
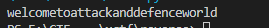
8、easy_RSA
在一次RSA密钥对生成中,假设p=473398607161,q=4511491,e=17
求解出d
由所给的 p, q 我们可以求得 m = (p-1)*(q-1)
之后再由 d * e = 1 mod m 可以知道 d 即是 e 模 m 的逆元,运用扩展欧几里得算法就能得到逆元(我这里直接从网上找到一段扩展欧几里得算法的代码)
1 p = 473398607161 2 q = 4511491 3 e = 17 4 n = p * q 5 m = (p-1) * (q-1) 6 print('m=' + str(m)) 7 8 9 #欧几里得算法求最大公约数 10 def get_gcd(a, b): 11 k = a // b 12 remainder = a % b 13 while remainder != 0: 14 a = b 15 b = remainder 16 k = a // b 17 remainder = a % b 18 return b 19 20 #改进欧几里得算法求线性方程的x与y 21 def get_(a, b): 22 if b == 0: 23 return 1, 0 24 else: 25 k = a // b 26 remainder = a % b 27 x1, y1 = get_(b, remainder) 28 x, y = y1, x1 - k * y1 29 return x, y 30 31 a, b = 17, m 32 33 #将初始b的绝对值进行保存 34 if b < 0: 35 m = abs(b) 36 else: 37 m = b 38 flag = get_gcd(a, b) 39 40 #判断最大公约数是否为1,若不是则没有逆元 41 if flag == 1: 42 x, y = get_(a, b) 43 x0 = x % m #对于Python '%'就是求模运算,因此不需要'+m' 44 print(x0) #x0就是所求的逆元 45 else: 46 print("Do not have!")

9、easychallenge
题目所给的 pyc 文件,先在线反编译为 python 代码
import base64 def encode1(ans): s = '' for i in ans: x = ord(i) ^ 36 x = x + 25 s += chr(x) return s def encode2(ans): s = '' for i in ans: x = ord(i) + 36 x = x ^ 36 s += chr(x) return s def encode3(ans): return base64.b32encode(ans) flag = ' ' print 'Please Input your flag:' flag = raw_input() final = 'UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E===' if encode3(encode2(encode1(flag))) == final: print 'correct' else: print 'wrong'
先后对 flag 进行 encode1, encode2, encode3 进行加密得到 final
那么将顺序反过来解密 final 就能得到 flag
1 import base64 2 3 def main(): 4 decode() 5 6 def decode(): 7 final = 'UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E===' 8 result = base64.b32decode(final) 9 result1 = [] 10 for i in result: 11 result1.append(i) 12 print(result1) 13 14 result2 = [] 15 for i in result1: 16 value = i ^ 36 17 value -= 36 18 result2.append(value) 19 print(result2) 20 21 result3 = [] 22 for i in result2: 23 value = i - 25 24 value ^= 36 25 result3.append(value) 26 print(result3) 27 28 flag = '' 29 for i in result3: 30 flag += chr(i) 31 print(flag) 32 33 main()
10、转轮机加密
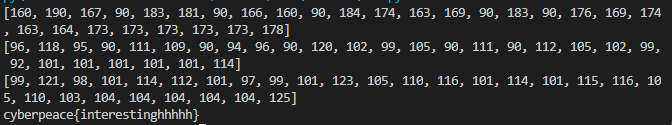
1: < ZWAXJGDLUBVIQHKYPNTCRMOSFE < 2: < KPBELNACZDTRXMJQOYHGVSFUWI < 3: < BDMAIZVRNSJUWFHTEQGYXPLOCK < 4: < RPLNDVHGFCUKTEBSXQYIZMJWAO < 5: < IHFRLABEUOTSGJVDKCPMNZQWXY < 6: < AMKGHIWPNYCJBFZDRUSLOQXVET < 7: < GWTHSPYBXIZULVKMRAFDCEONJQ < 8: < NOZUTWDCVRJLXKISEFAPMYGHBQ < 9: < XPLTDSRFHENYVUBMCQWAOIKZGJ < 10: < UDNAJFBOWTGVRSCZQKELMXYIHP < 11: < MNBVCXZQWERTPOIUYALSKDJFHG < 12: < LVNCMXZPQOWEIURYTASBKJDFHG < 13: < JZQAWSXCDERFVBGTYHNUMKILOP < 密钥为:2,3,7,5,13,12,9,1,8,10,4,11,6 密文为:NFQKSEVOQOFNP
根据密钥重新排序十三组字符串
将密文的十三个字符分别排到每组的起始位置
之后更改横纵方向方便查看,当然仅仅为了是方便查看
1 s = ['ZWAXJGDLUBVIQHKYPNTCRMOSFE ', 2 'KPBELNACZDTRXMJQOYHGVSFUWI ', 3 'BDMAIZVRNSJUWFHTEQGYXPLOCK ', 4 'RPLNDVHGFCUKTEBSXQYIZMJWAO ', 5 'IHFRLABEUOTSGJVDKCPMNZQWXY ', 6 'AMKGHIWPNYCJBFZDRUSLOQXVET ', 7 'GWTHSPYBXIZULVKMRAFDCEONJQ ', 8 'NOZUTWDCVRJLXKISEFAPMYGHBQ ', 9 'XPLTDSRFHENYVUBMCQWAOIKZGJ ', 10 'UDNAJFBOWTGVRSCZQKELMXYIHP ', 11 'MNBVCXZQWERTPOIUYALSKDJFHG ', 12 'LVNCMXZPQOWEIURYTASBKJDFHG ', 13 'JZQAWSXCDERFVBGTYHNUMKILOP '] 14 15 for i in range(len(s)): 16 s[i] = s[i].strip() 17 18 key = [2,3,7,5,13,12,9,1,8,10,4,11,6] 19 v = 'NFQKSEVOQOFNP' 20 21 t = [] 22 #更换字符串的顺序 23 for i in range(13): 24 t.append(s[key[i]-1]) 25 print(t) 26 27 u = [] 28 #改变每个字符串的排列顺序 29 for i in range(13): 30 new_sting = '' 31 index = t[i].index(v[i]) 32 new_sting += t[i][index:] + t[i][0:index] 33 u.append(new_sting) 34 print(u) 35 36 w = [] 37 #改变横纵方向方便查看,并修改为小写 38 for i in range(26): 39 new_sting = '' 40 for j in range(13): 41 new_sting += u[j][i].lower() 42 w.append(new_sting) 43 44 print(w)
之后在得到的结果中找到一个可以看得懂的明文串即是 flag

11、Normal_RSA
下载得到两个文件
需要运用到工具 openssl, rsatool, yafu
1 openssl rsa -pubin -text -modulus -in warmup -in pubkey.pem
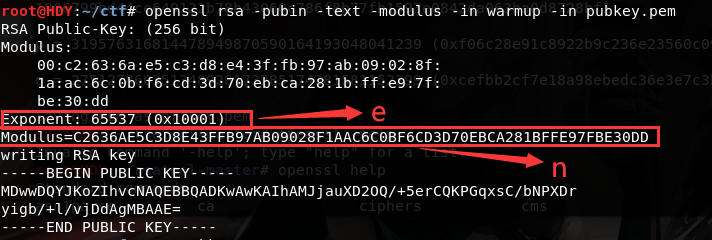
得到 e, n ,之后由 yafu 分解得到 p, q

1 python rsatool.py -o prikey.pem -e 65537 -p 319576316814478949870590164193048041239 -q 275127860351348928173285174381581152299

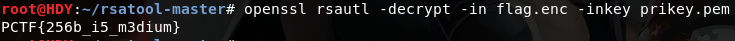
得到 prikey.pem (自己命名的文件)后和 flag.enc 放在同一目录下,解密得到 flag
1 openssl rsautl -decrypt -in flag.enc -inkey prikey.pem
12、easy_ECC
已知椭圆曲线加密Ep(a,b)参数为 p = 15424654874903 a = 16546484 b = 4548674875 G(6478678675,5636379357093) 私钥为 k = 546768 求公钥K(x,y)
借助 ECCTOOL 运算
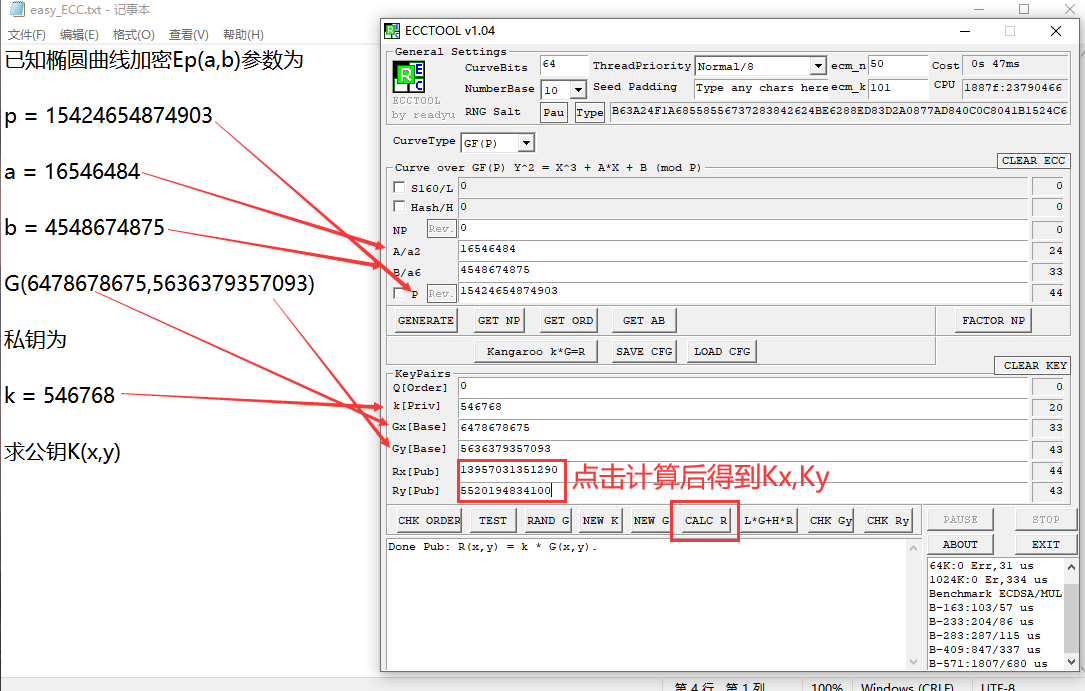
1 print(13957031351290+5520194834100)