Unit2: Transport
学习目标:
- how TCP set up a connection
- what TCP segment looks like
- how can TCP be in high performance
- detect errors
- Finite State Machine, a basic tools and approach to network protocol design
2.1 The TCP service model
-
Transmission Control Protocol(TCP)
- connection:
- two-way communication channel
- A -> B
- B -> A
- at both ends of the connection, TCP keeps a state machine to keep track of how the connection is doing
- connection:
-
Connection setup: 3-way hadnshake
- SYN:
- 方向:A向B
- A request conn with B
- SYN + ACK:
- 方向:B向A
- SYN:B request conn with A
- ACK: B agree to conn with A
- ACK:
- 方向:A向B
- A agree to conn with B
- SYN:
-
Data trasmission
- stream of bytes service
- using TCP segments
- SSH一次segment只有1个byte
-
Connection teardown
- closing the connection and both ends can clean up the state associated with the state machine
- FIN:
- 方向:A向B
- (Data+) ACK:
- 方向:B向A
- FIN:
- 方向:B向A
- ACK:
- 方向:A向B
-
The TCP service model
Property Behavior Stream of bytes Reliable delivery service Reliable delivery:
4 mechanism for reliability1. Acknowledgments indicate correct delivery
2. Checksums detect corrupted data
3. Sequence numbers detect missing data
4. Flow-control prevents overrunning receiverIn-sequence Data delivered to application in sequence transmitted. Congestion Control Controls network congestions -
The TCP Segment Format
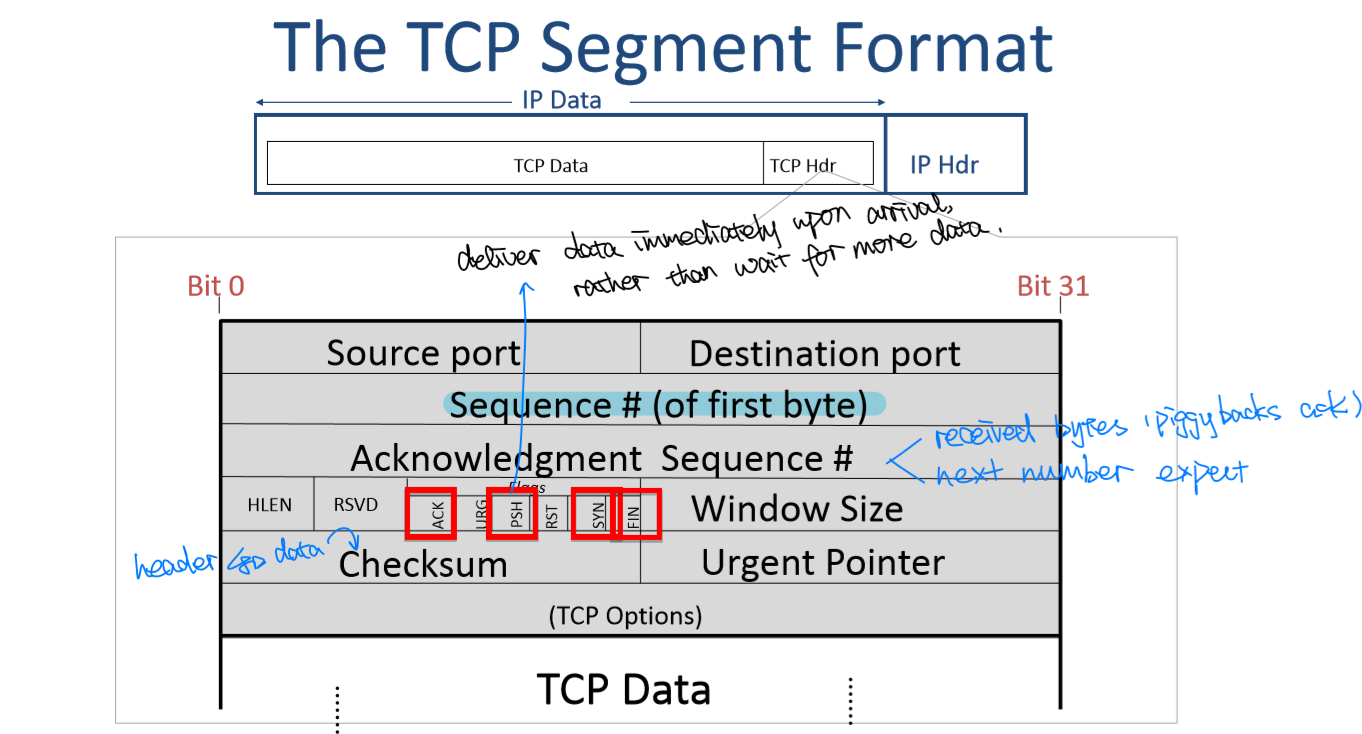
-
The Unique ID of the TCP connection
- 104-bit globally unique ID(Internet wide)
- IP:
- IP Dest Addr
- IP Src Addr
- Protocol ID
- TCP:
- Dest Port
- Src Port
- IP:
- Host A increments source port for every new connection: unique source port number(16bits)
- TCP picks random ISN(Initial Sequence Number) to avoid overlap with previous connection with same ID
- 104-bit globally unique ID(Internet wide)
-
Sequence Numbers
- ISN(initial sequence number): 表明发送的第一个字节的序列号
- Ack sequence number:
- 表明下一个期待的字节的序列号
- 表明已经接受到的字节数
-
Summary
- TCP provides in-order, reliable delivery of a stream of bytes between application processes.
2.2: UDP service model
-
UDP用途
- UDP datagram只是在IP基础上,指明the application that the data should be sent to at the other end
- application handles retransmissions in its own private way
- application doesn't need reliable delivery
- UDP datagram只是在IP基础上,指明the application that the data should be sent to at the other end
-
The UDP Datagram Format
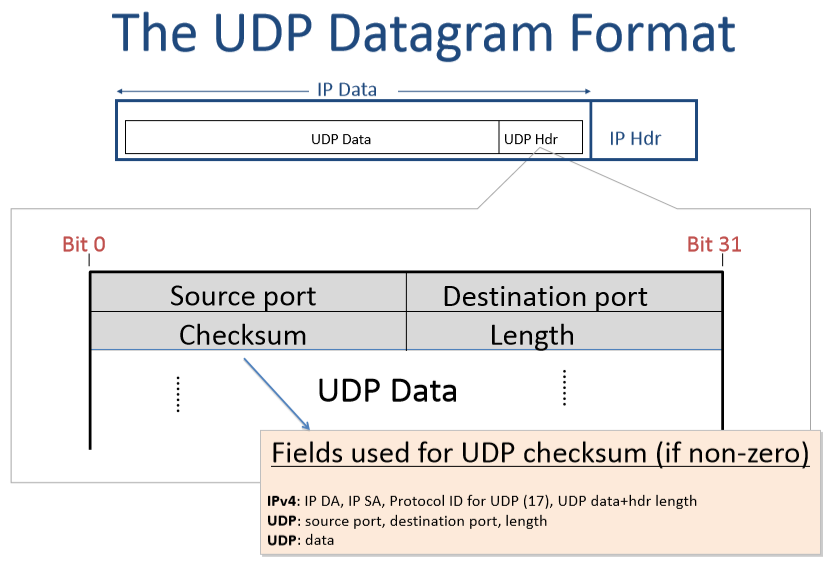
- length:header(8字节) plus data
- checksum可选:
- 不使用:全0
- 使用:calculated over the UDP header + UDP data + IP source addresses + IP destination addresses + protocol ID(值为17,表示data是UDP)
- 破坏了分层,但是允许UDP层检测datagram是否送到错误的位置
-
User Datagram Protocol(UDP)
Property Behavior Connectionless No connection established
Packets may show up in any orderSelf contained datagrams . Unreliable delivery 1. No acknowledgments
2. No mechanism to detect missing or mis-sequenced datagrams
3. No flow control- 使用UDP协议的通常是简单的request-response应用
- 早期版本的NFS:(the Network File System),不想使用TCP的sliding window,因此使用UDP并在程序中自己实现该机制
- DNS(Domain Name System): 使用UDP,因为DNS request是完全contained in one DNS datagram. UDP足够轻量级,并且没有必要建立连接
- DHCP(Dynamic Host Configuration Protocol): helps a new host find out its IP address when it joins a network
- 其它使用UDP协议的应用程序通常需要自己的机制用于retransmission, congestion control, in-sequence delivery
- 使用UDP协议的通常是简单的request-response应用
-
Summary
- UDP provides a simpler, datagram delivery service between application processes.
2.3: The Internet Control Message Protocol(ICMP) service model
-
ICMP 用途
- report errors
- diagnose problems
- IP doesn't provide any guarantees about delivery, ICMP tells about when things going wrong
-
Making the Network Layer work
- The Internet Protocol(IP)
- The creation of IP datagrams
- Hop-by-hop delivery from end to end
- Routing Tables
- Algorithms to populate router forwarding tables
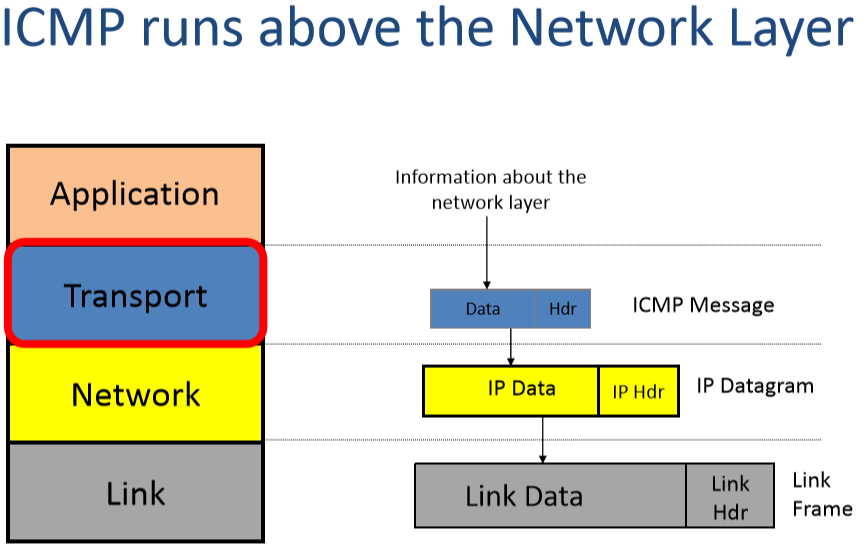
- Internet Control Message Protocol(ICMP)
- Communicates network layer information between end hosts and routers
- Reports error conditions
- Helps us diagnose problems
- The Internet Protocol(IP)
-
ICMP runs above the Network Layer
-
The ICMP Service Model
Property Behavior Reporting Message Self-contained message reporting error Unreliable Simple datagram service -no retries 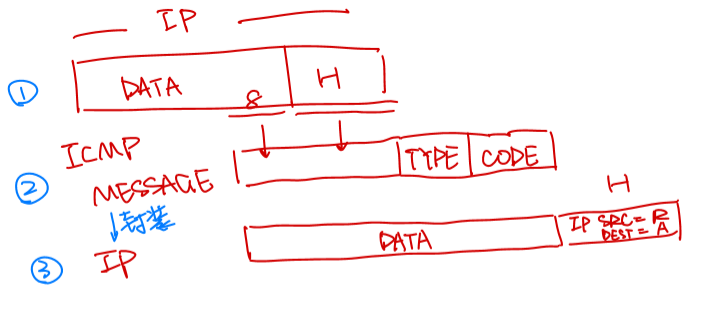
- ICMP Message:
- IP data的前8字节数据
- IP header
- error Type和error Code
- 继续封装在IP packet中,src是路由器/host,dest是IP src地址
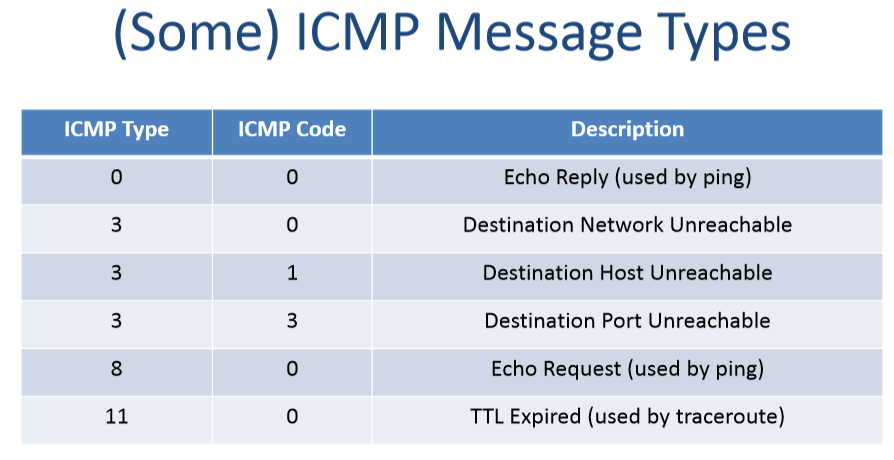
- ICMP Message:
-
How "ping" uses ICMP
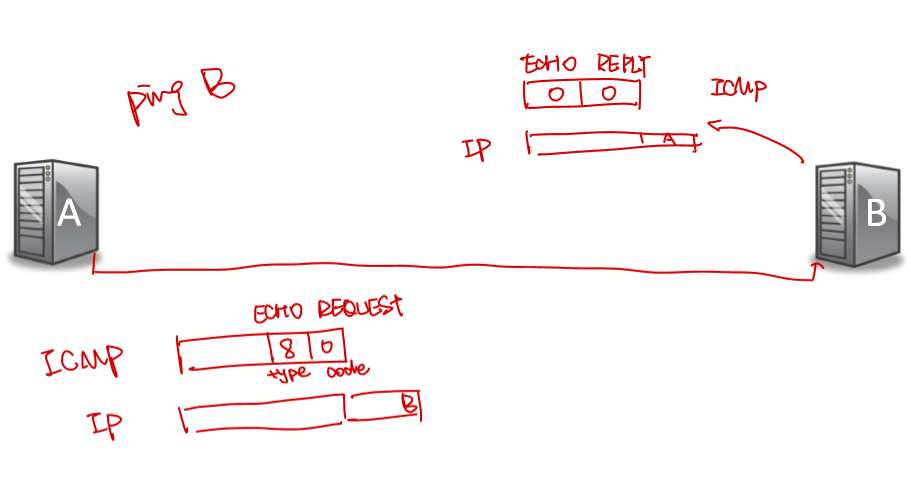
-
How "traceroute" uses ICMP
- traceroute程序两个作用
- 返回routers along the path
- 计算round trip time
- 发送UDP packet,其port端口设置为一个不可达的值,IP的TTL(Time to Live)域从1开始递增,这样当packet达到0时,路径上的router就会返回一个TTL Expired的ICMP message,就能报告router的ip地址和信息。直到最后的host返回"Port Not Reachable"的ICMP message。
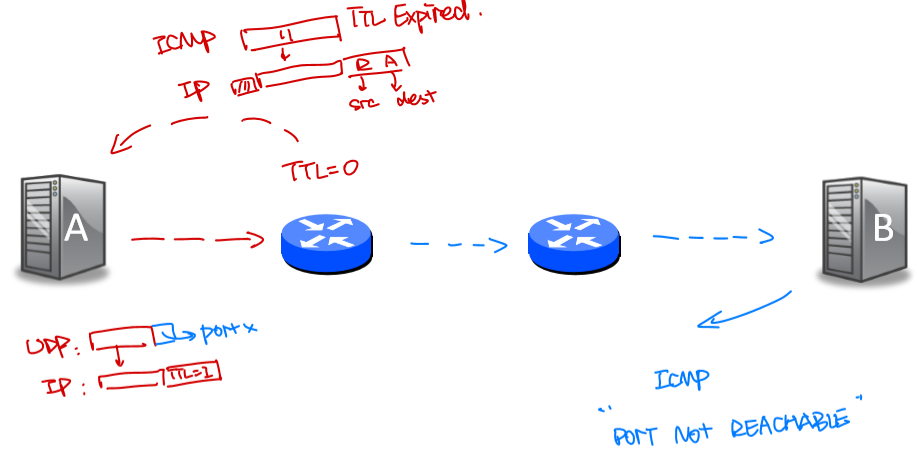
- traceroute程序两个作用
-
Summary
- ICMP provides information about the network layer to end hosts and routers
- It sits above IP and is a transport layer mechanism
- 关于"traceroute"程序
- traceroute can be used to figure out network topology.
- traceroute works by increasing the TTL values in each successive packet it sends.
- traceroute can be used to identify incorrect routing tables.
- ICMP的作用:
- Test if a web server is sending correct responses to requests.
- Know the exact link utilization between two routers to see if it is overloaded with packets.
- 下面哪些ICMP消息总是将router的IP地址作为源地址域
- (-) Echo Reply
- (+) Destination Network Unreachable
- (+) Destination Host Unreachable
- (-) Destination Port Unreachable
- (-) Echo Request
- (+) TTL Expired
2.4: The End-to-End Principle
- 弱端到端原则
- 正确性只有通信的两端能够保证。因此让通信系统自身保证正确性是不可能的。但是通信系统能够提供功能的不完整版本以提高性能。
- network can help:You can do stuff in the middle to help as performance improvements.
- but cannot be responsible for correctness
- 例如:
-
- Tcp: 端到端可靠的协议,即使链路不可靠,但只会使性能下降而不会影响正确性。除非TCP软件栈有bug。
-
- WiFi:通过retransmit提高性能
-
- 正确性只有通信的两端能够保证。因此让通信系统自身保证正确性是不可能的。但是通信系统能够提供功能的不完整版本以提高性能。
- 强端到端原则
- The network's job is to transmit datagrams as efficiently and flexibly as possible. Everything else should be done at the fringes.
2.5: Error detection: 3 schemes
- Error Detection
- append: 校验码至于包尾:
- ethernet CRC
- TLS MAC
- prepend:校验码至于包头:
- IP checksum:校验和域
- append: 校验码至于包尾:
- 3 Error Detection Schemes
- Checksum adds up values in packet(IP,TCP)
- Very fast, cheap to compute even in software
- Not very robust
- Cyclic redundancy code computes remainder of a polynomial(Ethernet)
- More expensive(easy today)
- Message authentication code: crytographic transformation of data(TLS: transport layer security-HTTPs)
- 基于安全性考虑而设计:Robust to malicious modifications
- 对检错不鲁棒
- Checksum adds up values in packet(IP,TCP)
- IP Checksum
- IP, UDP, TCP use one's complement checksum algorithm:
- 生成:设置checksum域为0,计算包中所有16位words的和,0xffff减去该结果设为校验码
- 0x8000+0x8000的进位轮回:=0x0001
- 若求和结果为0xffff,则校验码设为0xffff
- 校验:求和,结果应为0xffff
- 性能:仅保证检测1 bit错误
- 生成:设置checksum域为0,计算包中所有16位words的和,0xffff减去该结果设为校验码
- IP, UDP, TCP use one's complement checksum algorithm:
- Cyclic Redundancy Check(CRC):循环冗余校验码
- 对n位数据计算得到c位校验码。
- Ethernet:32bit CRC
- Bluetooth、USB:16bit CRC
- 生成:Uses polynomial long division
- 用数据M表示一个多项式的系数。使用一个生成多项式G。M除以G,余数是CRC
- 校验:M+CRC除以G,并判断余数是否为0
- 性能(用于检测特定形式的错误,对于一个c位CRC):
- 所有奇数位错误
- 所有2位错误
- Any message with a single burst of errors <= c bits long
- 对n位数据计算得到c位校验码。
- MAC
- Message Authentication Code(消息认证码):
- 用于Transport Layer Security:为了安全性而设计
- 生成:通信双方保存一个密钥$s$(随机生成)。则$c=MAC(M,s),|c|<<|M|$。c被append到数据包尾步。
- 校验:Using M and secret s, can verify c = MAC(M,s)
- 特点:
- 如果不知道s很难生成c
- 即很难构造(虚假)消息M其校验码满足c
- 1bit数据的翻转导致新的校验码c中每一bit变为随机的0或1:
- 本质:M和c不提供关于S的任何信息
- 存在概率新的c不变,即有两个数据具有相同的c。所以能保证error detection
- 能提供很好的安全保证,很难生成虚假消息
- ssh使用了散列消息验证码
- Message Authentication Code(消息认证码):
- recap
- IP、TCP不能依赖底层Ethernet的校验机制,因为有可能底层校验通过之后又引入了错误
- 因此:Each layer has its own error detection: end-to-end principle!
2.6 有限状态机:协议规范
- TCP状态机
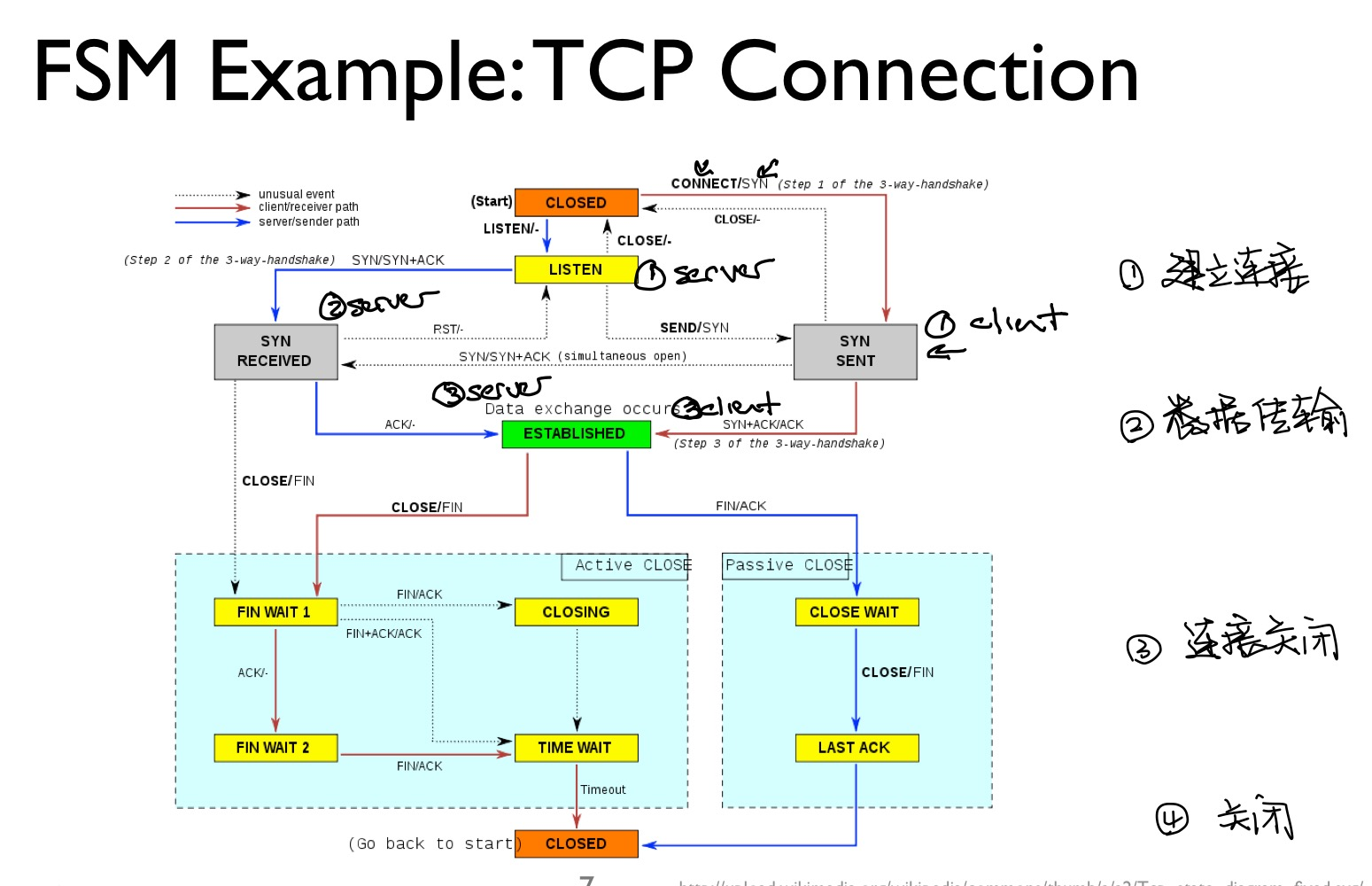
2.7 可靠通信:flow control - Stop and wait protocol
发送端发送速度超过接收端接收速度
- Flow Control
- basic idea: 让发送端发送速度小于接收端可以接收的速度。接收端给予发送端一些反馈信息。
- two basicapproaches:
1.Stop and Wait
2. Sliding window
- Stop and Wait
- Idea: At most one packet in flight at any time.
- 发送者依次发送一个packet,接受者回复一个ack,若timeout,则发送者重传。
- Stop and Wait FSM
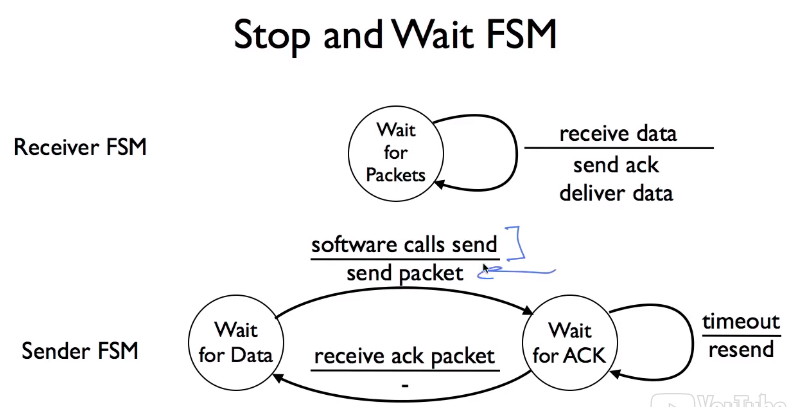
- Example Executions
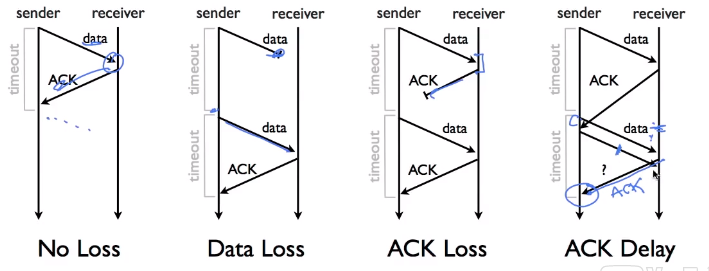
- No Loss
- Data Loss
- Ack Loss
- Ack Delay
- 发送者发送dataA,若Ack到达超过了timeout期限,在timeout时刻,发送者会重传dataA,因此将迟到的Ack视为重传AckA的确认。进而传输新的dataB,假设传输的新的dataB丢失了。接收端只收到重传的旧dataA,回复Ack。发送者并不知道此时的Ack,对应于重传的dataA还是新的dataB。
- 如果视为dataA的则状态机需要追踪data的信息。如果视为dataB的,则需要假设dataB的数据没有到达。
- Duplicates
- Flow control的基本问题:How to detect duplicates? How do you know when ack are from retransmissions or duplicated copies of packets versus new data?
- Stop and Wait:
- 使用1bit计数器:发送数据0,接收ack0;发送数据1,接收数据1.
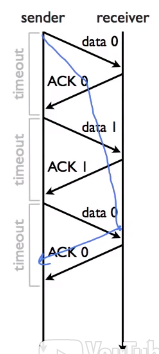
- 需要满足条件:
- Network itself does not duplicate packets
- Pakcets not delayed multiple timeouts.
- 使用1bit计数器:发送数据0,接收ack0;发送数据1,接收数据1.
- quiz
- (-)In a network that does not drop, duplicate, or corrupt any packets, stop-and-wait without an additional parity bit guarantees that the receiver receives all data in order.(只是网络本身不产生重复数据包,ack仍会timeout。)
- (+)In a network that does not drop, duplicate, or corrupt any packets, stop-and-wait without an additional parity bit guarantees that the receiver receives all data, but not necessarily in order.