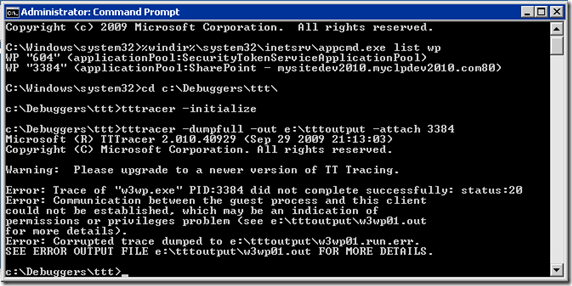
有一次, 我需要在客户的环境上抓取Time Travel Tracing, 简称TTT(dump的一种). 但是就是不能成功抓取. 报错如下:
具体错误信息如下:
c:\Debuggers\ttt>tttracer -dumpfull -out e:\tttoutput -attach 3384
Microsoft (R) TTTracer 2.010.40929 (Sep 29 2009 21:13:03)
Copyright (C) Microsoft Corporation. All rights reserved.
Warning: Please upgrade to a newer version of TT Tracing.
Error: Trace of "w3wp.exe" PID:3384 did not complete successfully: status:20
Error: Communication between the guest process and this client
could not be established, which may be an indication of
permissions or privileges problem (see e:\tttoutput\w3wp01.out
for more details).
Error: Corrupted trace dumped to e:\tttoutput\w3wp01.run.err.
SEE ERROR OUTPUT FILE e:\tttoutput\w3wp01.out FOR MORE DETAILS.
w3wp01.run.err 的内容
------------
Microsoft (R) TTTClient 2.010.40929 (Sep 29 2009 21:12:58)
Microsoft (R) Time Travel Tracing 2.010.40929 (Sep 29 2009 21:12:58)
Copyright (C) Microsoft Corporation. All rights reserved.
Microsoft Confidential - Strictly For Internal Use Only
Initializing Time Travel Tracing for Attach to 3384
Time: 03/02/2012 15:40:36
OS:6.1.7601 EDITION:x64
Group tracing GUID: d2c17755-0428-4e74-8709-b2f3bdfe0fa1
Running "w3wp.exe"
Running "c:\Debuggers\ttt\nirvexec.exe" /duration 1 /ClientName "c:\Debuggers\ttt\TTTraceWriter.dll" /ClientParams "23 e:\tttoutput\w3wp01.run 0 0 0 100000 0 1 0 0 6001" /attach 3384
客户说他们有一些组策略对他们的计算机进行安全限制, 然而当我们打开secpol.msc进行查看的时候, 他们也不记得究竟修改了那些组策略了. -_-||
解决方案
===================
使用系统Command Prompt, 而不是提升了权限的Command Prompt.
如何才能使用System的Command Prompt呢? 答案是使用Sysinternals(已被微软收购)的一个叫做PsExec的命令行工具.
首先运行命令:
PsExec.exe -s -i -d cmd.exe
稍等, 在新弹出的CMD窗口中输入原本被系统拒绝的命令.
关于该工具的更多信息
==================
PsExec, User Account Control and Security Boundaries
http://blogs.technet.com/b/markrussinovich/archive/2007/02/12/638372.aspx
Execute processes on a remote system and redirect output to the local system
http://www.windowsitpro.com/article/remote-computing/psexec
下载地址
==================
PsExec v1.98