[反汇编练习] 160个CrackMe之022.
本系列文章的目的是从一个没有任何经验的新手的角度(其实就是我自己),一步步尝试将160个CrackMe全部破解,如果可以,通过任何方式写出一个类似于注册机的东西。
其中,文章中按照如下逻辑编排(解决如下问题):
1、使用什么环境和工具
2、程序分析
3、思路分析和破解流程
4、注册机的探索
----------------------------------
提醒各位看客: 如果文章中的逻辑看不明白,那你一定是没有亲手操刀!OD中的跳转提示很强大,只要你跟踪了,不用怎么看代码就理解了!
----------------------------------
1、工具和环境:
WinXP SP3 + 52Pojie六周年纪念版OD + PEID + 汇编金手指。
160个CrackMe的打包文件。
下载地址: http://pan.baidu.com/s/1xUWOY 密码: jbnq
注:
1、Win7系统对于模块和程序开启了随机初始地址的功能,会给分析带来很大的负担,所以不建议使用Win7进行分析。
2、以上工具都是在52PoJie论坛下的原版程序,NOD32不报毒,个人承诺绝对不会进行任何和木马病毒相关内容。
2、程序分析:
想要破解一个程序,必须先了解这个程序。所以,在破解过程中,对最初程序的分析很重要,他可以帮助我们理解作者的目的和意图,特别是对于注册码的处理细节,从而方便我们反向跟踪和推导。
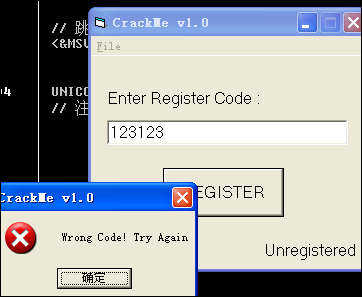
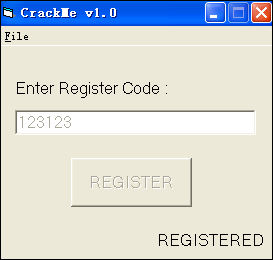
和上一节一样,打开CHM,选择第22个CarLitoZ.1.EXE,保存下来。运行程序,程序界面如下:
又有信息框了,我很高兴啊!
PEID: Microsoft Visual Basic 5.0 / 6.0
3、思路分析和破解流程
步骤:
1、打开OD,将exe拖到OD窗口中,等程序暂停后,直接点击运行按钮(F9),不用理会。
2、在exe中输入Key:123123。点击OK按钮,弹出错误信息框,不要关闭。
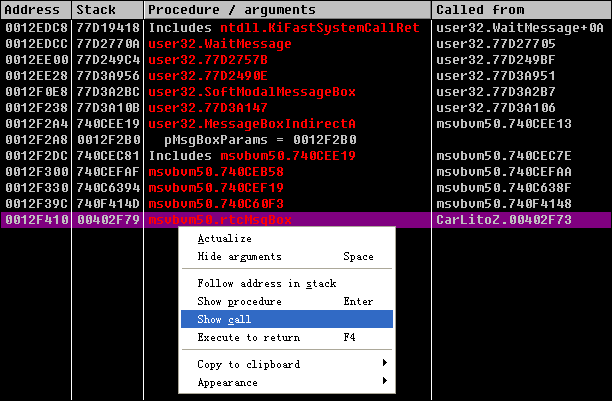
3、在OD中点击暂停按钮(Ctrl+F12),再点击堆栈K按钮(Ctrl+K),可以看到当前堆栈情况。
4、选中最后的rtcMsgBox,右键->Show call,返回到反汇编界面:
00402D86 . /7D 12 jge short 00402D9A 00402D88 . |68 F8060000 push 0x6F8 00402D8D . |68 0C224000 push 0040220C 00402D92 . |56 push esi 00402D93 . |50 push eax 00402D94 . |FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 00402D9A > 8D4E 34 lea ecx,dword ptr ds:[esi+0x34] 00402D9D . 8D55 94 lea edx,dword ptr ss:[ebp-0x6C] 00402DA0 . 51 push ecx 00402DA1 . 52 push edx 00402DA2 . C745 9C 01000>mov dword ptr ss:[ebp-0x64],0x1 00402DA9 . C745 94 02800>mov dword ptr ss:[ebp-0x6C],0x8002 00402DB0 . FF15 6C614000 call dword ptr ds:[<&MSVBVM50.__vbaVarTs>; msvbvm50.__vbaVarTstEq 00402DB6 . 8B3D C4614000 mov edi,dword ptr ds:[<&MSVBVM50.__vbaVa>; msvbvm50.__vbaVarDup 00402DBC . B9 04000280 mov ecx,0x80020004 00402DC1 . 66:85C0 test ax,ax 00402DC4 . B8 0A000000 mov eax,0xA 00402DC9 . 894D AC mov dword ptr ss:[ebp-0x54],ecx 00402DCC . 894D BC mov dword ptr ss:[ebp-0x44],ecx 00402DCF . 8945 A4 mov dword ptr ss:[ebp-0x5C],eax 00402DD2 . 8945 B4 mov dword ptr ss:[ebp-0x4C],eax 00402DD5 . C745 8C 08234>mov dword ptr ss:[ebp-0x74],00402308 ; UNICODE "CrackMe v1.0" 00402DDC . C745 84 08000>mov dword ptr ss:[ebp-0x7C],0x8 00402DE3 . 8D55 84 lea edx,dword ptr ss:[ebp-0x7C] 00402DE6 . 8D4D C4 lea ecx,dword ptr ss:[ebp-0x3C] 00402DE9 0F84 5A010000 je 00402F49 ; // 跳到失败 00402DEF . FFD7 call edi ; <&MSVBVM50.__vbaVarDup> 00402DF1 . 8D55 94 lea edx,dword ptr ss:[ebp-0x6C] 00402DF4 . 8D4D D4 lea ecx,dword ptr ss:[ebp-0x2C] 00402DF7 . C745 9C D4224>mov dword ptr ss:[ebp-0x64],004022D4 ; UNICODE "Registration Successful" 00402DFE . C745 94 08000>mov dword ptr ss:[ebp-0x6C],0x8 ; // 注册成功 00402E05 . FFD7 call edi 00402E07 . 8D45 A4 lea eax,dword ptr ss:[ebp-0x5C] 00402E0A . 8D4D B4 lea ecx,dword ptr ss:[ebp-0x4C] 00402E0D . 50 push eax 00402E0E . 8D55 C4 lea edx,dword ptr ss:[ebp-0x3C] 00402E11 . 51 push ecx 00402E12 . 52 push edx 00402E13 . 8D45 D4 lea eax,dword ptr ss:[ebp-0x2C] 00402E16 . 6A 30 push 0x30 00402E18 . 50 push eax 00402E19 . FF15 40614000 call dword ptr ds:[<&MSVBVM50.#595>] ; msvbvm50.rtcMsgBox 00402E1F . 8D4D A4 lea ecx,dword ptr ss:[ebp-0x5C] 00402E22 . 8D55 B4 lea edx,dword ptr ss:[ebp-0x4C] 00402E25 . 51 push ecx 00402E26 . 8D45 C4 lea eax,dword ptr ss:[ebp-0x3C] 00402E29 . 52 push edx 00402E2A . 8D4D D4 lea ecx,dword ptr ss:[ebp-0x2C] 00402E2D . 50 push eax 00402E2E . 51 push ecx 00402E2F . 6A 04 push 0x4 00402E31 . FF15 1C614000 call dword ptr ds:[<&MSVBVM50.__vbaFreeV>; msvbvm50.__vbaFreeVarList 00402E37 . 83C4 14 add esp,0x14 00402E3A . 8D7E 44 lea edi,dword ptr ds:[esi+0x44] 00402E3D . 68 40224000 push 00402240 ; UNICODE "c:windowsMTR.dat" 00402E42 . 57 push edi 00402E43 . FF15 90614000 call dword ptr ds:[<&MSVBVM50.__vbaI2Var>; msvbvm50.__vbaI2Var 00402E49 . 50 push eax 00402E4A . 6A FF push -0x1 00402E4C . 6A 20 push 0x20 00402E4E . FF15 98614000 call dword ptr ds:[<&MSVBVM50.__vbaFileO>; msvbvm50.__vbaFileOpen 00402E54 . BA 6C224000 mov edx,0040226C ; UNICODE "trv2156j0e" 00402E59 . 8D4D E8 lea ecx,dword ptr ss:[ebp-0x18] 00402E5C . FF15 AC614000 call dword ptr ds:[<&MSVBVM50.__vbaStrCo>; msvbvm50.__vbaStrCopy 00402E62 . 57 push edi 00402E63 . FF15 90614000 call dword ptr ds:[<&MSVBVM50.__vbaI2Var>; msvbvm50.__vbaI2Var 00402E69 . 50 push eax 00402E6A . 8D55 E8 lea edx,dword ptr ss:[ebp-0x18] 00402E6D . 6A 2D push 0x2D 00402E6F . 52 push edx 00402E70 . 6A 00 push 0x0 00402E72 . FF15 24614000 call dword ptr ds:[<&MSVBVM50.__vbaPut4>>; msvbvm50.__vbaPut4 00402E78 . 8D4D E8 lea ecx,dword ptr ss:[ebp-0x18] 00402E7B . FF15 DC614000 call dword ptr ds:[<&MSVBVM50.__vbaFreeS>; msvbvm50.__vbaFreeStr 00402E81 . 57 push edi 00402E82 . FF15 90614000 call dword ptr ds:[<&MSVBVM50.__vbaI2Var>; msvbvm50.__vbaI2Var 00402E88 . 50 push eax 00402E89 . FF15 60614000 call dword ptr ds:[<&MSVBVM50.__vbaFileC>; msvbvm50.__vbaFileClose 00402E8F . 56 push esi 00402E90 . FF93 0C030000 call dword ptr ds:[ebx+0x30C] 00402E96 . 50 push eax 00402E97 . 8D45 E4 lea eax,dword ptr ss:[ebp-0x1C] 00402E9A . 50 push eax 00402E9B . FF15 3C614000 call dword ptr ds:[<&MSVBVM50.__vbaObjSe>; msvbvm50.__vbaObjSet 00402EA1 . 8BF8 mov edi,eax 00402EA3 . 68 88224000 push 00402288 ; UNICODE "REGISTERED" 00402EA8 . 57 push edi ; // ↑的文本说明验证成功了 00402EA9 . 8B0F mov ecx,dword ptr ds:[edi] 00402EAB . FF51 54 call dword ptr ds:[ecx+0x54] 00402EAE . 85C0 test eax,eax 00402EB0 . 7D 0F jge short 00402EC1 00402EB2 . 6A 54 push 0x54 00402EB4 . 68 A0224000 push 004022A0 00402EB9 . 57 push edi 00402EBA . 50 push eax 00402EBB . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 00402EC1 > 8D4D E4 lea ecx,dword ptr ss:[ebp-0x1C] 00402EC4 . FF15 E0614000 call dword ptr ds:[<&MSVBVM50.__vbaFreeO>; msvbvm50.__vbaFreeObj 00402ECA . 56 push esi 00402ECB . FF93 04030000 call dword ptr ds:[ebx+0x304] 00402ED1 . 8D55 E4 lea edx,dword ptr ss:[ebp-0x1C] 00402ED4 . 50 push eax 00402ED5 . 52 push edx 00402ED6 . FF15 3C614000 call dword ptr ds:[<&MSVBVM50.__vbaObjSe>; msvbvm50.__vbaObjSet 00402EDC . 8BF8 mov edi,eax 00402EDE . 6A 00 push 0x0 00402EE0 . 57 push edi 00402EE1 . 8B07 mov eax,dword ptr ds:[edi] 00402EE3 . FF90 8C000000 call dword ptr ds:[eax+0x8C] 00402EE9 . 85C0 test eax,eax 00402EEB . 7D 12 jge short 00402EFF 00402EED . 68 8C000000 push 0x8C 00402EF2 . 68 B0224000 push 004022B0 00402EF7 . 57 push edi 00402EF8 . 50 push eax 00402EF9 . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 00402EFF > 8B3D E0614000 mov edi,dword ptr ds:[<&MSVBVM50.__vbaFr>; msvbvm50.__vbaFreeObj 00402F05 . 8D4D E4 lea ecx,dword ptr ss:[ebp-0x1C] 00402F08 . FFD7 call edi ; <&MSVBVM50.__vbaFreeObj> 00402F0A . 56 push esi 00402F0B . FF93 08030000 call dword ptr ds:[ebx+0x308] 00402F11 . 8D4D E4 lea ecx,dword ptr ss:[ebp-0x1C] 00402F14 . 50 push eax 00402F15 . 51 push ecx 00402F16 . FF15 3C614000 call dword ptr ds:[<&MSVBVM50.__vbaObjSe>; msvbvm50.__vbaObjSet 00402F1C . 8BF0 mov esi,eax 00402F1E . 6A 00 push 0x0 00402F20 . 56 push esi 00402F21 . 8B16 mov edx,dword ptr ds:[esi] 00402F23 . FF92 8C000000 call dword ptr ds:[edx+0x8C] 00402F29 . 85C0 test eax,eax 00402F2B . 7D 12 jge short 00402F3F 00402F2D . 68 8C000000 push 0x8C 00402F32 . 68 C0224000 push 004022C0 00402F37 . 56 push esi 00402F38 . 50 push eax 00402F39 . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 00402F3F > 8D4D E4 lea ecx,dword ptr ss:[ebp-0x1C] 00402F42 . FFD7 call edi 00402F44 . E9 8C000000 jmp 00402FD5 00402F49 > FFD7 call edi 00402F4B . 8D55 94 lea edx,dword ptr ss:[ebp-0x6C] 00402F4E . 8D4D D4 lea ecx,dword ptr ss:[ebp-0x2C] 00402F51 . C745 9C 28234>mov dword ptr ss:[ebp-0x64],00402328 ; UNICODE " Wrong Code! Try Again" 00402F58 . C745 94 08000>mov dword ptr ss:[ebp-0x6C],0x8 00402F5F . FFD7 call edi 00402F61 . 8D45 A4 lea eax,dword ptr ss:[ebp-0x5C] 00402F64 . 8D4D B4 lea ecx,dword ptr ss:[ebp-0x4C] 00402F67 . 50 push eax 00402F68 . 8D55 C4 lea edx,dword ptr ss:[ebp-0x3C] 00402F6B . 51 push ecx 00402F6C . 52 push edx 00402F6D . 8D45 D4 lea eax,dword ptr ss:[ebp-0x2C] 00402F70 . 6A 10 push 0x10 00402F72 . 50 push eax 00402F73 . FF15 40614000 call dword ptr ds:[<&MSVBVM50.#595>] ; msvbvm50.rtcMsgBox
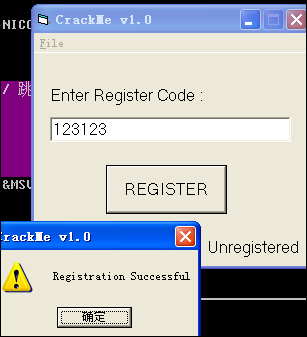
从当前位置向上查找,很容易地发现了好几处提示注册成功的文本,最后在头部发现了__vbaVarTstEq,并且他下面接着 je 00402F49 跳转,接着就是提示成功的文本。我们再去中间还发现了一个特殊的文件路径:c:windowsMTR.dat,留心一下。
分析到这里,爆破很简单了,直接将关键跳转使用NOP填充就可以了。选中je 00402F49 ,右键->Binary->Fill with NOPs。试一试,哈哈,成功了!
考虑到刚才的那个文件路径,我们重启文件一下,看看是否可行:
4、注册机的探索
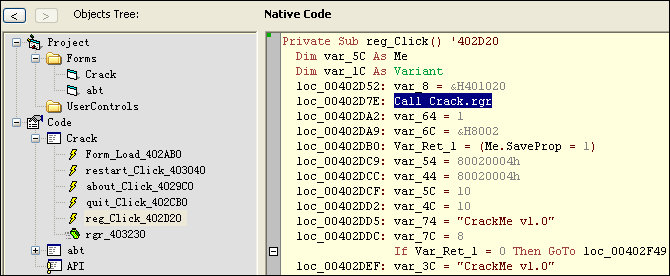
直接上VB Decompiler Pro, 分析了一下:
Private Sub reg_Click() '402D20
Dim var_5C As Me
Dim var_1C As Variant
loc_00402D52: var_8 = &H401020
loc_00402D7E: Call Crack.rgr
loc_00402DA2: var_64 = 1
loc_00402DA9: var_6C = &H8002
loc_00402DB0: Var_Ret_1 = (Me.SaveProp = 1)
loc_00402DC9: var_54 = 80020004h
loc_00402DCC: var_44 = 80020004h
loc_00402DCF: var_5C = 10
loc_00402DD2: var_4C = 10
loc_00402DD5: var_74 = "CrackMe v1.0"
loc_00402DDC: var_7C = 8
If Var_Ret_1 = 0 Then GoTo loc_00402F49
loc_00402DEF: var_3C = "CrackMe v1.0"
loc_00402DF7: var_64 = "Registration Successful"
loc_00402DFE: var_6C = 8
loc_00402E05: var_2C = "Registration Successful"
loc_00402E19: MsgBox var_2C, 48, var_3C
loc_00402E43: Me = %x1 = CInt("c:windowsMTR.dat")
loc_00402E4E: Open Me For Random As #var_3C
loc_00402E5C: var_18 = "trv2156j0e"
loc_00402E63: Me = %x1 = CInt(4203020)
loc_00402E72: Put #var_18, 45, var_18
loc_00402E82: Me = %x1 = CInt(1784)
loc_00402E89: Close #Put #var_18, 45, var_18
loc_00402E9B: Set var_1C = Close #Put #var_18, 45, var_18
loc_00402EAB: Unknown_VTable_Call[ecx+54h]
loc_00402ED6: Set var_1C = Unknown_VTable_Call[ecx+54h]
loc_00402EE3: reg.Enabled = False
loc_00402F23: Text.Enabled = False
loc_00402F51: var_64 = "Wrong Code! Try Again"
loc_00402F58: var_6C = 8
loc_00402F73: MsgBox var_2C, 16, var_3C
loc_00402FB0: Text.Text = 4203356
loc_00402FE1: GoTo loc_00403011
loc_00403010: Exit Sub
loc_00403011: Exit Sub
End Sub发现按钮点击事件调用了Call Crack.rgr进行验证,而他自身只进行判断:
ublic Sub rgr() '403230
Dim var_3C As TextBox
loc_0040325C: var_8 = &H401040
loc_0040339E: Set var_40 = 404024h
loc_004033A9: Unknown_VTable_Call[eax+50h]
loc_004033D2: CreateObject(4200340, 4210724)
loc_004033DD:
loc_004033EB: Set var_44 = 404024h
loc_004033F6: Unknown_VTable_Call[ecx+50h]
loc_0040341F: CreateObject(4200340, 4210724)
loc_0040342A:
loc_00403438: Set var_48 = 404024h
loc_00403443: Unknown_VTable_Call[eax+50h]
loc_0040346C: CreateObject(4200340, 4210724)
loc_00403477:
loc_00403485: Set var_4C = 404024h
loc_00403490: Unknown_VTable_Call[ecx+50h]
loc_004034B9: CreateObject(4200340, 4210724)
loc_004034C4:
loc_004034D2: Set var_50 = 404024h
loc_004034DD: Unknown_VTable_Call[eax+50h]
loc_00403506: CreateObject(4200340, 4210724)
loc_00403511:
loc_0040351F: Set var_54 = 404024h
loc_0040352A: Unknown_VTable_Call[ecx+50h]
loc_00403553: CreateObject(4200340, 4210724)
loc_0040355E:
loc_0040356C: Set var_58 = 404024h
loc_00403577: Unknown_VTable_Call[eax+50h]
loc_004035A0: CreateObject(4200340, 4210724)
loc_004035AB:
loc_004035B9: Set var_5C = 404024h
loc_004035C4: Unknown_VTable_Call[ecx+50h]
loc_004035EF: Set var_3C = Me
loc_004035FA: var_18 = Text.Text
loc_0040361F: var_254 = var_18
loc_0040362B: var_64 = var_1C
loc_00403644: var_25C = &H8008
loc_0040364E: var_74 = 1
loc_00403655: var_7C = 2
loc_0040365B: var_6C = 8
loc_0040366D: var_94 = var_20
loc_00403684: var_A4 = 1
loc_0040368E: var_AC = 2
loc_00403697: var_9C = 8
loc_004036AC: var_D4 = var_24
loc_004036C6: var_E4 = 1
loc_004036D0: var_EC = 2
loc_004036D9: var_DC = 8
loc_004036EE: var_114 = var_28
loc_00403705: var_124 = 1
loc_0040370F: var_12C = 2
loc_00403718: var_11C = 8
loc_0040372D: var_154 = var_2C
loc_00403747: var_164 = 1
loc_00403751: var_16C = 2
loc_0040375A: var_15C = 8
loc_00403769: var_1A4 = 1
loc_00403773: var_1AC = 2
loc_0040377C: var_194 = var_30
loc_0040379C: var_19C = 8
loc_004037B1: var_1D4 = var_34
loc_004037CB: var_1E4 = 1
loc_004037D5: var_1EC = 2
loc_004037DE: var_1DC = 8
loc_004037F3: var_214 = var_38
loc_0040380D: var_224 = 1
loc_00403817: var_22C = 2
loc_00403820: var_21C = 8
loc_0040384E: Var_Ret_1 = Mid$(var_1C, 6, 1) + Mid$(var_20, 9, 1)
loc_0040385F: Var_Ret_2 = Var_Ret_1 + Mid$(var_24, 143, 1)
loc_00403870: Var_Ret_3 = Var_Ret_2 + Mid$(var_28, 16, 1)
loc_00403881: Var_Ret_4 = Var_Ret_3 + Mid$(var_2C, 161, 1)
loc_00403892: Var_Ret_5 = Var_Ret_4 + Mid$(var_30, 171, 1)
loc_004038A3: Var_Ret_6 = Var_Ret_5 + Mid$(var_34, 166, 1)
loc_004038B4: Var_Ret_7 = Var_Ret_6 + Mid$(var_38, 168, 1)
loc_004038B7: Var_Ret_8 = (var_18 = Var_Ret_7)
If Var_Ret_8 = 0 Then GoTo loc_004039FD
loc_004039E4: var_274 = 1
loc_004039EE: var_27C = 2
loc_004039F7: ecx = 1
loc_004039FD:
loc_00403A02: GoTo loc_00403B55
loc_00403B54: Exit Sub
loc_00403B55: Exit Sub
End Sub我们在OD中,Ctrl+G,输入 ublic Sub rgr() 的开头地址:403230,在OD中参照上述代码进行具体分析:
00403230 > 55 push ebp ; // 验证注册码的函数 00403231 . 8BEC mov ebp,esp 00403233 . 83EC 0C sub esp,0xC 00403236 . 68 66104000 push <jmp.&MSVBVM50.__vbaExceptHandler> ; SE handler installation 0040323B . 64:A1 0000000>mov eax,dword ptr fs:[0] 00403241 . 50 push eax 00403242 . 64:8925 00000>mov dword ptr fs:[0],esp 00403249 . 81EC 54030000 sub esp,0x354 0040324F . 8B45 08 mov eax,dword ptr ss:[ebp+0x8] 00403252 . 53 push ebx 00403253 . 56 push esi 00403254 . 57 push edi 00403255 . 8B08 mov ecx,dword ptr ds:[eax] 00403257 . 8965 F4 mov dword ptr ss:[ebp-0xC],esp 0040325A . 33F6 xor esi,esi 0040325C . C745 F8 40104>mov dword ptr ss:[ebp-0x8],00401040 00403263 . 50 push eax 00403264 . 8975 FC mov dword ptr ss:[ebp-0x4],esi 00403267 . 898D 98FCFFFF mov dword ptr ss:[ebp-0x368],ecx 0040326D . FF51 04 call dword ptr ds:[ecx+0x4] 00403270 . A1 24404000 mov eax,dword ptr ds:[0x404024] 00403275 . 8975 E8 mov dword ptr ss:[ebp-0x18],esi 00403278 . 3BC6 cmp eax,esi 0040327A . 8975 E4 mov dword ptr ss:[ebp-0x1C],esi 0040327D . 8975 E0 mov dword ptr ss:[ebp-0x20],esi 00403280 . 8975 DC mov dword ptr ss:[ebp-0x24],esi 00403283 . 8975 D8 mov dword ptr ss:[ebp-0x28],esi 00403286 . 8975 D4 mov dword ptr ss:[ebp-0x2C],esi 00403289 . 8975 D0 mov dword ptr ss:[ebp-0x30],esi 0040328C . 8975 CC mov dword ptr ss:[ebp-0x34],esi 0040328F . 8975 C8 mov dword ptr ss:[ebp-0x38],esi 00403292 . 8975 C4 mov dword ptr ss:[ebp-0x3C],esi 00403295 . 8975 C0 mov dword ptr ss:[ebp-0x40],esi 00403298 . 8975 BC mov dword ptr ss:[ebp-0x44],esi 0040329B . 8975 B8 mov dword ptr ss:[ebp-0x48],esi 0040329E . 8975 B4 mov dword ptr ss:[ebp-0x4C],esi 004032A1 . 8975 B0 mov dword ptr ss:[ebp-0x50],esi 004032A4 . 8975 AC mov dword ptr ss:[ebp-0x54],esi 004032A7 . 8975 A8 mov dword ptr ss:[ebp-0x58],esi 004032AA . 8975 A4 mov dword ptr ss:[ebp-0x5C],esi 004032AD . 8975 94 mov dword ptr ss:[ebp-0x6C],esi 004032B0 . 8975 84 mov dword ptr ss:[ebp-0x7C],esi 004032B3 . 89B5 74FFFFFF mov dword ptr ss:[ebp-0x8C],esi 004032B9 . 89B5 64FFFFFF mov dword ptr ss:[ebp-0x9C],esi 004032BF . 89B5 54FFFFFF mov dword ptr ss:[ebp-0xAC],esi 004032C5 . 89B5 44FFFFFF mov dword ptr ss:[ebp-0xBC],esi 004032CB . 89B5 34FFFFFF mov dword ptr ss:[ebp-0xCC],esi 004032D1 . 89B5 24FFFFFF mov dword ptr ss:[ebp-0xDC],esi 004032D7 . 89B5 14FFFFFF mov dword ptr ss:[ebp-0xEC],esi 004032DD . 89B5 04FFFFFF mov dword ptr ss:[ebp-0xFC],esi 004032E3 . 89B5 F4FEFFFF mov dword ptr ss:[ebp-0x10C],esi 004032E9 . 89B5 E4FEFFFF mov dword ptr ss:[ebp-0x11C],esi 004032EF . 89B5 D4FEFFFF mov dword ptr ss:[ebp-0x12C],esi 004032F5 . 89B5 C4FEFFFF mov dword ptr ss:[ebp-0x13C],esi 004032FB . 89B5 B4FEFFFF mov dword ptr ss:[ebp-0x14C],esi 00403301 . 89B5 A4FEFFFF mov dword ptr ss:[ebp-0x15C],esi 00403307 . 89B5 94FEFFFF mov dword ptr ss:[ebp-0x16C],esi 0040330D . 89B5 84FEFFFF mov dword ptr ss:[ebp-0x17C],esi 00403313 . 89B5 74FEFFFF mov dword ptr ss:[ebp-0x18C],esi 00403319 . 89B5 64FEFFFF mov dword ptr ss:[ebp-0x19C],esi 0040331F . 89B5 54FEFFFF mov dword ptr ss:[ebp-0x1AC],esi 00403325 . 89B5 44FEFFFF mov dword ptr ss:[ebp-0x1BC],esi 0040332B . 89B5 34FEFFFF mov dword ptr ss:[ebp-0x1CC],esi 00403331 . 89B5 24FEFFFF mov dword ptr ss:[ebp-0x1DC],esi 00403337 . 89B5 14FEFFFF mov dword ptr ss:[ebp-0x1EC],esi 0040333D . 89B5 04FEFFFF mov dword ptr ss:[ebp-0x1FC],esi 00403343 . 89B5 F4FDFFFF mov dword ptr ss:[ebp-0x20C],esi 00403349 . 89B5 E4FDFFFF mov dword ptr ss:[ebp-0x21C],esi 0040334F . 89B5 D4FDFFFF mov dword ptr ss:[ebp-0x22C],esi 00403355 . 89B5 C4FDFFFF mov dword ptr ss:[ebp-0x23C],esi 0040335B . 89B5 B4FDFFFF mov dword ptr ss:[ebp-0x24C],esi 00403361 . 89B5 A4FDFFFF mov dword ptr ss:[ebp-0x25C],esi 00403367 . 89B5 94FDFFFF mov dword ptr ss:[ebp-0x26C],esi 0040336D . 89B5 84FDFFFF mov dword ptr ss:[ebp-0x27C],esi 00403373 . 75 15 jnz short 0040338A 00403375 . 68 24404000 push 00404024 0040337A . 68 94174000 push 00401794 0040337F . FF15 9C614000 call dword ptr ds:[<&MSVBVM50.__vbaNew2>>; msvbvm50.__vbaNew2 00403385 . A1 24404000 mov eax,dword ptr ds:[0x404024] 0040338A > 8B08 mov ecx,dword ptr ds:[eax] 0040338C . 50 push eax 0040338D . FF91 00030000 call dword ptr ds:[ecx+0x300] 00403393 . 8B1D 3C614000 mov ebx,dword ptr ds:[<&MSVBVM50.__vbaOb>; msvbvm50.__vbaObjSet 00403399 . 8D55 C0 lea edx,dword ptr ss:[ebp-0x40] 0040339C . 50 push eax 0040339D . 52 push edx 0040339E . FFD3 call ebx ; <&MSVBVM50.__vbaObjSet> 004033A0 . 8BF8 mov edi,eax 004033A2 . 8D4D E4 lea ecx,dword ptr ss:[ebp-0x1C] 004033A5 . 51 push ecx 004033A6 . 57 push edi 004033A7 . 8B07 mov eax,dword ptr ds:[edi] 004033A9 . FF50 50 call dword ptr ds:[eax+0x50] 004033AC . 3BC6 cmp eax,esi 004033AE . 7D 0F jge short 004033BF 004033B0 . 6A 50 push 0x50 004033B2 . 68 A0224000 push 004022A0 004033B7 . 57 push edi 004033B8 . 50 push eax 004033B9 . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 004033BF > A1 24404000 mov eax,dword ptr ds:[0x404024] 004033C4 . 3BC6 cmp eax,esi 004033C6 . 75 15 jnz short 004033DD 004033C8 . 68 24404000 push 00404024 004033CD . 68 94174000 push 00401794 004033D2 . FF15 9C614000 call dword ptr ds:[<&MSVBVM50.__vbaNew2>>; msvbvm50.__vbaNew2 004033D8 . A1 24404000 mov eax,dword ptr ds:[0x404024] 004033DD > 8B10 mov edx,dword ptr ds:[eax] 004033DF . 50 push eax 004033E0 . FF92 00030000 call dword ptr ds:[edx+0x300] 004033E6 . 50 push eax 004033E7 . 8D45 BC lea eax,dword ptr ss:[ebp-0x44] 004033EA . 50 push eax 004033EB . FFD3 call ebx 004033ED . 8BF8 mov edi,eax 004033EF . 8D55 E0 lea edx,dword ptr ss:[ebp-0x20] 004033F2 . 52 push edx 004033F3 . 57 push edi 004033F4 . 8B0F mov ecx,dword ptr ds:[edi] 004033F6 . FF51 50 call dword ptr ds:[ecx+0x50] 004033F9 . 3BC6 cmp eax,esi 004033FB . 7D 0F jge short 0040340C 004033FD . 6A 50 push 0x50 004033FF . 68 A0224000 push 004022A0 00403404 . 57 push edi 00403405 . 50 push eax 00403406 . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 0040340C > A1 24404000 mov eax,dword ptr ds:[0x404024] 00403411 . 3BC6 cmp eax,esi 00403413 . 75 15 jnz short 0040342A 00403415 . 68 24404000 push 00404024 0040341A . 68 94174000 push 00401794 0040341F . FF15 9C614000 call dword ptr ds:[<&MSVBVM50.__vbaNew2>>; msvbvm50.__vbaNew2 00403425 . A1 24404000 mov eax,dword ptr ds:[0x404024] 0040342A > 8B08 mov ecx,dword ptr ds:[eax] 0040342C . 50 push eax 0040342D . FF91 00030000 call dword ptr ds:[ecx+0x300] 00403433 . 8D55 B8 lea edx,dword ptr ss:[ebp-0x48] 00403436 . 50 push eax 00403437 . 52 push edx 00403438 . FFD3 call ebx 0040343A . 8BF8 mov edi,eax 0040343C . 8D4D DC lea ecx,dword ptr ss:[ebp-0x24] 0040343F . 51 push ecx 00403440 . 57 push edi 00403441 . 8B07 mov eax,dword ptr ds:[edi] 00403443 . FF50 50 call dword ptr ds:[eax+0x50] 00403446 . 3BC6 cmp eax,esi 00403448 . 7D 0F jge short 00403459 0040344A . 6A 50 push 0x50 0040344C . 68 A0224000 push 004022A0 00403451 . 57 push edi 00403452 . 50 push eax 00403453 . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 00403459 > A1 24404000 mov eax,dword ptr ds:[0x404024] 0040345E . 3BC6 cmp eax,esi 00403460 . 75 15 jnz short 00403477 00403462 . 68 24404000 push 00404024 00403467 . 68 94174000 push 00401794 0040346C . FF15 9C614000 call dword ptr ds:[<&MSVBVM50.__vbaNew2>>; msvbvm50.__vbaNew2 00403472 . A1 24404000 mov eax,dword ptr ds:[0x404024] 00403477 > 8B10 mov edx,dword ptr ds:[eax] 00403479 . 50 push eax 0040347A . FF92 00030000 call dword ptr ds:[edx+0x300] 00403480 . 50 push eax 00403481 . 8D45 B4 lea eax,dword ptr ss:[ebp-0x4C] 00403484 . 50 push eax 00403485 . FFD3 call ebx 00403487 . 8BF8 mov edi,eax 00403489 . 8D55 D8 lea edx,dword ptr ss:[ebp-0x28] 0040348C . 52 push edx 0040348D . 57 push edi 0040348E . 8B0F mov ecx,dword ptr ds:[edi] 00403490 . FF51 50 call dword ptr ds:[ecx+0x50] 00403493 . 3BC6 cmp eax,esi 00403495 . 7D 0F jge short 004034A6 00403497 . 6A 50 push 0x50 00403499 . 68 A0224000 push 004022A0 0040349E . 57 push edi 0040349F . 50 push eax 004034A0 . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 004034A6 > A1 24404000 mov eax,dword ptr ds:[0x404024] 004034AB . 3BC6 cmp eax,esi 004034AD . 75 15 jnz short 004034C4 004034AF . 68 24404000 push 00404024 004034B4 . 68 94174000 push 00401794 004034B9 . FF15 9C614000 call dword ptr ds:[<&MSVBVM50.__vbaNew2>>; msvbvm50.__vbaNew2 004034BF . A1 24404000 mov eax,dword ptr ds:[0x404024] 004034C4 > 8B08 mov ecx,dword ptr ds:[eax] 004034C6 . 50 push eax 004034C7 . FF91 00030000 call dword ptr ds:[ecx+0x300] 004034CD . 8D55 B0 lea edx,dword ptr ss:[ebp-0x50] 004034D0 . 50 push eax 004034D1 . 52 push edx 004034D2 . FFD3 call ebx 004034D4 . 8BF8 mov edi,eax 004034D6 . 8D4D D4 lea ecx,dword ptr ss:[ebp-0x2C] 004034D9 . 51 push ecx 004034DA . 57 push edi 004034DB . 8B07 mov eax,dword ptr ds:[edi] 004034DD . FF50 50 call dword ptr ds:[eax+0x50] 004034E0 . 3BC6 cmp eax,esi 004034E2 . 7D 0F jge short 004034F3 004034E4 . 6A 50 push 0x50 004034E6 . 68 A0224000 push 004022A0 004034EB . 57 push edi 004034EC . 50 push eax 004034ED . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 004034F3 > A1 24404000 mov eax,dword ptr ds:[0x404024] 004034F8 . 3BC6 cmp eax,esi 004034FA . 75 15 jnz short 00403511 004034FC . 68 24404000 push 00404024 00403501 . 68 94174000 push 00401794 00403506 . FF15 9C614000 call dword ptr ds:[<&MSVBVM50.__vbaNew2>>; msvbvm50.__vbaNew2 0040350C . A1 24404000 mov eax,dword ptr ds:[0x404024] 00403511 > 8B10 mov edx,dword ptr ds:[eax] 00403513 . 50 push eax 00403514 . FF92 00030000 call dword ptr ds:[edx+0x300] 0040351A . 50 push eax 0040351B . 8D45 AC lea eax,dword ptr ss:[ebp-0x54] 0040351E . 50 push eax 0040351F . FFD3 call ebx 00403521 . 8BF8 mov edi,eax 00403523 . 8D55 D0 lea edx,dword ptr ss:[ebp-0x30] 00403526 . 52 push edx 00403527 . 57 push edi 00403528 . 8B0F mov ecx,dword ptr ds:[edi] 0040352A . FF51 50 call dword ptr ds:[ecx+0x50] 0040352D . 3BC6 cmp eax,esi 0040352F . 7D 0F jge short 00403540 00403531 . 6A 50 push 0x50 00403533 . 68 A0224000 push 004022A0 00403538 . 57 push edi 00403539 . 50 push eax 0040353A . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 00403540 > A1 24404000 mov eax,dword ptr ds:[0x404024] 00403545 . 3BC6 cmp eax,esi 00403547 . 75 15 jnz short 0040355E 00403549 . 68 24404000 push 00404024 0040354E . 68 94174000 push 00401794 00403553 . FF15 9C614000 call dword ptr ds:[<&MSVBVM50.__vbaNew2>>; msvbvm50.__vbaNew2 00403559 . A1 24404000 mov eax,dword ptr ds:[0x404024] 0040355E > 8B08 mov ecx,dword ptr ds:[eax] 00403560 . 50 push eax 00403561 . FF91 00030000 call dword ptr ds:[ecx+0x300] 00403567 . 8D55 A8 lea edx,dword ptr ss:[ebp-0x58] 0040356A . 50 push eax 0040356B . 52 push edx 0040356C . FFD3 call ebx 0040356E . 8BF8 mov edi,eax 00403570 . 8D4D CC lea ecx,dword ptr ss:[ebp-0x34] 00403573 . 51 push ecx 00403574 . 57 push edi 00403575 . 8B07 mov eax,dword ptr ds:[edi] 00403577 . FF50 50 call dword ptr ds:[eax+0x50] 0040357A . 3BC6 cmp eax,esi 0040357C . 7D 0F jge short 0040358D 0040357E . 6A 50 push 0x50 00403580 . 68 A0224000 push 004022A0 00403585 . 57 push edi 00403586 . 50 push eax 00403587 . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 0040358D > A1 24404000 mov eax,dword ptr ds:[0x404024] 00403592 . 3BC6 cmp eax,esi 00403594 . 75 15 jnz short 004035AB 00403596 . 68 24404000 push 00404024 0040359B . 68 94174000 push 00401794 004035A0 . FF15 9C614000 call dword ptr ds:[<&MSVBVM50.__vbaNew2>>; msvbvm50.__vbaNew2 004035A6 . A1 24404000 mov eax,dword ptr ds:[0x404024] 004035AB > 8B10 mov edx,dword ptr ds:[eax] 004035AD . 50 push eax 004035AE . FF92 00030000 call dword ptr ds:[edx+0x300] 004035B4 . 50 push eax 004035B5 . 8D45 A4 lea eax,dword ptr ss:[ebp-0x5C] 004035B8 . 50 push eax 004035B9 . FFD3 call ebx 004035BB . 8BF8 mov edi,eax 004035BD . 8D55 C8 lea edx,dword ptr ss:[ebp-0x38] 004035C0 . 52 push edx 004035C1 . 57 push edi 004035C2 . 8B0F mov ecx,dword ptr ds:[edi] 004035C4 . FF51 50 call dword ptr ds:[ecx+0x50] 004035C7 . 3BC6 cmp eax,esi 004035C9 . 7D 0F jge short 004035DA 004035CB . 6A 50 push 0x50 004035CD . 68 A0224000 push 004022A0 004035D2 . 57 push edi 004035D3 . 50 push eax 004035D4 . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 004035DA > 8B45 08 mov eax,dword ptr ss:[ebp+0x8] 004035DD . 8B8D 98FCFFFF mov ecx,dword ptr ss:[ebp-0x368] 004035E3 . 50 push eax 004035E4 . FF91 08030000 call dword ptr ds:[ecx+0x308] 004035EA . 8D55 C4 lea edx,dword ptr ss:[ebp-0x3C] 004035ED . 50 push eax 004035EE . 52 push edx 004035EF . FFD3 call ebx 004035F1 . 8BF8 mov edi,eax 004035F3 . 8D4D E8 lea ecx,dword ptr ss:[ebp-0x18] 004035F6 . 51 push ecx 004035F7 . 57 push edi 004035F8 . 8B07 mov eax,dword ptr ds:[edi] 004035FA . FF90 A0000000 call dword ptr ds:[eax+0xA0] 00403600 . 3BC6 cmp eax,esi 00403602 . 7D 12 jge short 00403616 00403604 . 68 A0000000 push 0xA0 00403609 . 68 C0224000 push 004022C0 0040360E . 57 push edi 0040360F . 50 push eax 00403610 . FF15 34614000 call dword ptr ds:[<&MSVBVM50.__vbaHresu>; msvbvm50.__vbaHresultCheckObj 00403616 > 8B45 E8 mov eax,dword ptr ss:[ebp-0x18] 00403619 . 8B3D 58614000 mov edi,dword ptr ds:[<&MSVBVM50.#632>] ; msvbvm50.rtcMidCharVar 0040361F . 8985 ACFDFFFF mov dword ptr ss:[ebp-0x254],eax 00403625 . 8B45 E4 mov eax,dword ptr ss:[ebp-0x1C] 00403628 . 8D55 84 lea edx,dword ptr ss:[ebp-0x7C] 0040362B . 8945 9C mov dword ptr ss:[ebp-0x64],eax 0040362E . 52 push edx 0040362F . 8D45 94 lea eax,dword ptr ss:[ebp-0x6C] 00403632 . 6A 06 push 0x6 00403634 . 8D8D 74FFFFFF lea ecx,dword ptr ss:[ebp-0x8C] 0040363A . BB 02000000 mov ebx,0x2 0040363F . 50 push eax ; UNICODE "bPe CrackMe v1.0 " 00403640 . 51 push ecx 00403641 . 8975 E8 mov dword ptr ss:[ebp-0x18],esi 00403644 . C785 A4FDFFFF>mov dword ptr ss:[ebp-0x25C],0x8008 0040364E . C745 8C 01000>mov dword ptr ss:[ebp-0x74],0x1 00403655 . 895D 84 mov dword ptr ss:[ebp-0x7C],ebx 00403658 . 8975 E4 mov dword ptr ss:[ebp-0x1C],esi 0040365B . C745 94 08000>mov dword ptr ss:[ebp-0x6C],0x8 00403662 . FFD7 call edi ; msvbvm50.rtcMidCharVar; <&MSVBVM50.#632> 00403664 . 8B45 E0 mov eax,dword ptr ss:[ebp-0x20] 00403667 . 8D95 54FFFFFF lea edx,dword ptr ss:[ebp-0xAC] 0040366D . 8985 6CFFFFFF mov dword ptr ss:[ebp-0x94],eax 00403673 . 52 push edx 00403674 . 8D85 64FFFFFF lea eax,dword ptr ss:[ebp-0x9C] 0040367A . 6A 09 push 0x9 0040367C . 8D8D 44FFFFFF lea ecx,dword ptr ss:[ebp-0xBC] 00403682 . 50 push eax ; UNICODE "bPe CrackMe v1.0 " 00403683 . 51 push ecx 00403684 . C785 5CFFFFFF>mov dword ptr ss:[ebp-0xA4],0x1 0040368E . 899D 54FFFFFF mov dword ptr ss:[ebp-0xAC],ebx 00403694 . 8975 E0 mov dword ptr ss:[ebp-0x20],esi 00403697 . C785 64FFFFFF>mov dword ptr ss:[ebp-0x9C],0x8 004036A1 . FFD7 call edi ; msvbvm50.rtcMidCharVar 004036A3 . 8B45 DC mov eax,dword ptr ss:[ebp-0x24] 004036A6 . 8D95 14FFFFFF lea edx,dword ptr ss:[ebp-0xEC] 004036AC . 8985 2CFFFFFF mov dword ptr ss:[ebp-0xD4],eax 004036B2 . 52 push edx 004036B3 . 8D85 24FFFFFF lea eax,dword ptr ss:[ebp-0xDC] 004036B9 . 68 8F000000 push 0x8F 004036BE . 8D8D 04FFFFFF lea ecx,dword ptr ss:[ebp-0xFC] 004036C4 . 50 push eax ; UNICODE "bPe CrackMe v1.0 " 004036C5 . 51 push ecx 004036C6 . C785 1CFFFFFF>mov dword ptr ss:[ebp-0xE4],0x1 004036D0 . 899D 14FFFFFF mov dword ptr ss:[ebp-0xEC],ebx 004036D6 . 8975 DC mov dword ptr ss:[ebp-0x24],esi 004036D9 . C785 24FFFFFF>mov dword ptr ss:[ebp-0xDC],0x8 004036E3 . FFD7 call edi ; msvbvm50.rtcMidCharVar 004036E5 . 8B45 D8 mov eax,dword ptr ss:[ebp-0x28] 004036E8 . 8D95 D4FEFFFF lea edx,dword ptr ss:[ebp-0x12C] 004036EE . 8985 ECFEFFFF mov dword ptr ss:[ebp-0x114],eax 004036F4 . 52 push edx 004036F5 . 8D85 E4FEFFFF lea eax,dword ptr ss:[ebp-0x11C] 004036FB . 6A 10 push 0x10 004036FD . 8D8D C4FEFFFF lea ecx,dword ptr ss:[ebp-0x13C] 00403703 . 50 push eax 00403704 . 51 push ecx 00403705 . C785 DCFEFFFF>mov dword ptr ss:[ebp-0x124],0x1 0040370F . 899D D4FEFFFF mov dword ptr ss:[ebp-0x12C],ebx 00403715 . 8975 D8 mov dword ptr ss:[ebp-0x28],esi 00403718 . C785 E4FEFFFF>mov dword ptr ss:[ebp-0x11C],0x8 00403722 . FFD7 call edi ; msvbvm50.rtcMidCharVar 00403724 . 8B45 D4 mov eax,dword ptr ss:[ebp-0x2C] 00403727 . 8D95 94FEFFFF lea edx,dword ptr ss:[ebp-0x16C] 0040372D . 8985 ACFEFFFF mov dword ptr ss:[ebp-0x154],eax 00403733 . 52 push edx 00403734 . 8D85 A4FEFFFF lea eax,dword ptr ss:[ebp-0x15C] 0040373A . 68 A1000000 push 0xA1 0040373F . 8D8D 84FEFFFF lea ecx,dword ptr ss:[ebp-0x17C] 00403745 . 50 push eax 00403746 . 51 push ecx 00403747 . C785 9CFEFFFF>mov dword ptr ss:[ebp-0x164],0x1 00403751 . 899D 94FEFFFF mov dword ptr ss:[ebp-0x16C],ebx 00403757 . 8975 D4 mov dword ptr ss:[ebp-0x2C],esi 0040375A . C785 A4FEFFFF>mov dword ptr ss:[ebp-0x15C],0x8 00403764 . FFD7 call edi ; msvbvm50.rtcMidCharVar 00403766 . 8B45 D0 mov eax,dword ptr ss:[ebp-0x30] 00403769 . C785 5CFEFFFF>mov dword ptr ss:[ebp-0x1A4],0x1 00403773 . 899D 54FEFFFF mov dword ptr ss:[ebp-0x1AC],ebx 00403779 . 8975 D0 mov dword ptr ss:[ebp-0x30],esi 0040377C . 8985 6CFEFFFF mov dword ptr ss:[ebp-0x194],eax 00403782 . 8D95 54FEFFFF lea edx,dword ptr ss:[ebp-0x1AC] 00403788 . 8D85 64FEFFFF lea eax,dword ptr ss:[ebp-0x19C] 0040378E . 52 push edx 0040378F . 68 AB000000 push 0xAB 00403794 . 8D8D 44FEFFFF lea ecx,dword ptr ss:[ebp-0x1BC] 0040379A . 50 push eax 0040379B . 51 push ecx 0040379C . C785 64FEFFFF>mov dword ptr ss:[ebp-0x19C],0x8 004037A6 . FFD7 call edi ; msvbvm50.rtcMidCharVar 004037A8 . 8B45 CC mov eax,dword ptr ss:[ebp-0x34] 004037AB . 8D95 14FEFFFF lea edx,dword ptr ss:[ebp-0x1EC] 004037B1 . 8985 2CFEFFFF mov dword ptr ss:[ebp-0x1D4],eax 004037B7 . 52 push edx 004037B8 . 8D85 24FEFFFF lea eax,dword ptr ss:[ebp-0x1DC] 004037BE . 68 A6000000 push 0xA6 004037C3 . 8D8D 04FEFFFF lea ecx,dword ptr ss:[ebp-0x1FC] 004037C9 . 50 push eax 004037CA . 51 push ecx 004037CB . C785 1CFEFFFF>mov dword ptr ss:[ebp-0x1E4],0x1 004037D5 . 899D 14FEFFFF mov dword ptr ss:[ebp-0x1EC],ebx 004037DB . 8975 CC mov dword ptr ss:[ebp-0x34],esi 004037DE . C785 24FEFFFF>mov dword ptr ss:[ebp-0x1DC],0x8 004037E8 . FFD7 call edi ; msvbvm50.rtcMidCharVar 004037EA . 8B45 C8 mov eax,dword ptr ss:[ebp-0x38] 004037ED . 8D95 D4FDFFFF lea edx,dword ptr ss:[ebp-0x22C] 004037F3 . 8985 ECFDFFFF mov dword ptr ss:[ebp-0x214],eax 004037F9 . 52 push edx 004037FA . 8D85 E4FDFFFF lea eax,dword ptr ss:[ebp-0x21C] 00403800 . 68 A8000000 push 0xA8 00403805 . 8D8D C4FDFFFF lea ecx,dword ptr ss:[ebp-0x23C] 0040380B . 50 push eax 0040380C . 51 push ecx 0040380D . C785 DCFDFFFF>mov dword ptr ss:[ebp-0x224],0x1 00403817 . 899D D4FDFFFF mov dword ptr ss:[ebp-0x22C],ebx 0040381D . 8975 C8 mov dword ptr ss:[ebp-0x38],esi 00403820 . C785 E4FDFFFF>mov dword ptr ss:[ebp-0x21C],0x8 0040382A . FFD7 call edi ; msvbvm50.rtcMidCharVar 0040382C . 8B3D C0614000 mov edi,dword ptr ds:[<&MSVBVM50.__vbaVa>; msvbvm50.__vbaVarAdd 00403832 . 8D95 A4FDFFFF lea edx,dword ptr ss:[ebp-0x25C] 00403838 . 8D85 74FFFFFF lea eax,dword ptr ss:[ebp-0x8C] 0040383E . 52 push edx ; // "123123" 0040383F . 8D8D 44FFFFFF lea ecx,dword ptr ss:[ebp-0xBC] 00403845 . 50 push eax ; // eax ="r" 00403846 . 8D95 34FFFFFF lea edx,dword ptr ss:[ebp-0xCC] 0040384C . 51 push ecx ; // ecx ="k" 0040384D . 52 push edx 0040384E . FFD7 call edi ; msvbvm50.__vbaVarAdd; <&MSVBVM50.__vbaVarAdd> 00403850 . 50 push eax ; // eax = "rk" 00403851 . 8D85 04FFFFFF lea eax,dword ptr ss:[ebp-0xFC] 00403857 . 8D8D F4FEFFFF lea ecx,dword ptr ss:[ebp-0x10C] 0040385D . 50 push eax ; // rax ="h" 0040385E . 51 push ecx 0040385F . FFD7 call edi ; msvbvm50.__vbaVarAdd 00403861 . 50 push eax ; // eax = "rkh" 00403862 . 8D95 C4FEFFFF lea edx,dword ptr ss:[ebp-0x13C] 00403868 . 8D85 B4FEFFFF lea eax,dword ptr ss:[ebp-0x14C] 0040386E . 52 push edx ; // edx = "1" 0040386F . 50 push eax 00403870 . FFD7 call edi ; msvbvm50.__vbaVarAdd 00403872 . 8D8D 84FEFFFF lea ecx,dword ptr ss:[ebp-0x17C] ; // eax = "rkh1" 00403878 . 50 push eax 00403879 . 8D95 74FEFFFF lea edx,dword ptr ss:[ebp-0x18C] 0040387F . 51 push ecx ; // ecx ="o" 00403880 . 52 push edx 00403881 . FFD7 call edi ; msvbvm50.__vbaVarAdd 00403883 . 50 push eax 00403884 . 8D85 44FEFFFF lea eax,dword ptr ss:[ebp-0x1BC] 0040388A . 8D8D 34FEFFFF lea ecx,dword ptr ss:[ebp-0x1CC] 00403890 . 50 push eax ; // "y" 00403891 . 51 push ecx 00403892 . FFD7 call edi ; msvbvm50.__vbaVarAdd 00403894 . 50 push eax ; // eax = "rkh1oy" 00403895 . 8D95 04FEFFFF lea edx,dword ptr ss:[ebp-0x1FC] 0040389B . 8D85 F4FDFFFF lea eax,dword ptr ss:[ebp-0x20C] 004038A1 . 52 push edx ; // "i" 004038A2 . 50 push eax 004038A3 . FFD7 call edi ; msvbvm50.__vbaVarAdd 004038A5 . 8D8D C4FDFFFF lea ecx,dword ptr ss:[ebp-0x23C] 004038AB . 50 push eax 004038AC . 51 push ecx ; // "e" 004038AD . 8D95 B4FDFFFF lea edx,dword ptr ss:[ebp-0x24C] 004038B3 . 52 push edx 004038B4 . FFD7 call edi ; msvbvm50.__vbaVarAdd 004038B6 . 50 push eax ; // Arg1 = eax ="rkh1oyie", Arg2="123123" 004038B7 . FF15 6C614000 call dword ptr ds:[<&MSVBVM50.__vbaVarTs>; msvbvm50.__vbaVarTstEq 004038BD . 8BF8 mov edi,eax ; // eax = 结果 004038BF . 8D45 A4 lea eax,dword ptr ss:[ebp-0x5C] 004038C2 . 8D4D A8 lea ecx,dword ptr ss:[ebp-0x58] 004038C5 . 50 push eax 004038C6 . 8D55 AC lea edx,dword ptr ss:[ebp-0x54] 004038C9 . 51 push ecx 004038CA . 8D45 B0 lea eax,dword ptr ss:[ebp-0x50] 004038CD . 52 push edx 004038CE . 8D4D B4 lea ecx,dword ptr ss:[ebp-0x4C] 004038D1 . 50 push eax 004038D2 . 8D55 B8 lea edx,dword ptr ss:[ebp-0x48] 004038D5 . 51 push ecx 004038D6 . 8D45 BC lea eax,dword ptr ss:[ebp-0x44] 004038D9 . 52 push edx 004038DA . 8D4D C0 lea ecx,dword ptr ss:[ebp-0x40] 004038DD . 50 push eax 004038DE . 8D55 C4 lea edx,dword ptr ss:[ebp-0x3C] 004038E1 . 51 push ecx 004038E2 . 52 push edx 004038E3 . 6A 09 push 0x9 004038E5 . FF15 28614000 call dword ptr ds:[<&MSVBVM50.__vbaFreeO>; msvbvm50.__vbaFreeObjList 004038EB . 83C4 28 add esp,0x28 004038EE . 8D85 C4FDFFFF lea eax,dword ptr ss:[ebp-0x23C] 004038F4 . 8D8D F4FDFFFF lea ecx,dword ptr ss:[ebp-0x20C] 004038FA . 8D95 D4FDFFFF lea edx,dword ptr ss:[ebp-0x22C] 00403900 . 50 push eax 00403901 . 51 push ecx 00403902 . 8D85 E4FDFFFF lea eax,dword ptr ss:[ebp-0x21C] 00403908 . 52 push edx 00403909 . 8D8D 04FEFFFF lea ecx,dword ptr ss:[ebp-0x1FC] 0040390F . 50 push eax 00403910 . 8D95 34FEFFFF lea edx,dword ptr ss:[ebp-0x1CC] 00403916 . 51 push ecx 00403917 . 8D85 14FEFFFF lea eax,dword ptr ss:[ebp-0x1EC] 0040391D . 52 push edx 0040391E . 8D8D 24FEFFFF lea ecx,dword ptr ss:[ebp-0x1DC] 00403924 . 50 push eax 00403925 . 8D95 44FEFFFF lea edx,dword ptr ss:[ebp-0x1BC] 0040392B . 51 push ecx 0040392C . 8D85 74FEFFFF lea eax,dword ptr ss:[ebp-0x18C] 00403932 . 52 push edx 00403933 . 8D8D 54FEFFFF lea ecx,dword ptr ss:[ebp-0x1AC] 00403939 . 50 push eax 0040393A . 8D95 64FEFFFF lea edx,dword ptr ss:[ebp-0x19C] 00403940 . 51 push ecx 00403941 . 8D85 84FEFFFF lea eax,dword ptr ss:[ebp-0x17C] 00403947 . 52 push edx 00403948 . 8D8D B4FEFFFF lea ecx,dword ptr ss:[ebp-0x14C] 0040394E . 50 push eax 0040394F . 8D95 94FEFFFF lea edx,dword ptr ss:[ebp-0x16C] 00403955 . 51 push ecx 00403956 . 8D85 A4FEFFFF lea eax,dword ptr ss:[ebp-0x15C] 0040395C . 52 push edx 0040395D . 8D8D C4FEFFFF lea ecx,dword ptr ss:[ebp-0x13C] 00403963 . 50 push eax 00403964 . 8D95 F4FEFFFF lea edx,dword ptr ss:[ebp-0x10C] 0040396A . 51 push ecx 0040396B . 8D85 D4FEFFFF lea eax,dword ptr ss:[ebp-0x12C] 00403971 . 52 push edx 00403972 . 8D8D E4FEFFFF lea ecx,dword ptr ss:[ebp-0x11C] 00403978 . 50 push eax 00403979 . 8D95 04FFFFFF lea edx,dword ptr ss:[ebp-0xFC] 0040397F . 51 push ecx 00403980 . 8D85 34FFFFFF lea eax,dword ptr ss:[ebp-0xCC] 00403986 . 52 push edx 00403987 . 8D8D 14FFFFFF lea ecx,dword ptr ss:[ebp-0xEC] 0040398D . 50 push eax 0040398E . 8D95 24FFFFFF lea edx,dword ptr ss:[ebp-0xDC] 00403994 . 51 push ecx 00403995 . 8D85 44FFFFFF lea eax,dword ptr ss:[ebp-0xBC] 0040399B . 52 push edx 0040399C . 8D8D 74FFFFFF lea ecx,dword ptr ss:[ebp-0x8C] 004039A2 . 50 push eax 004039A3 . 8D95 54FFFFFF lea edx,dword ptr ss:[ebp-0xAC] 004039A9 . 51 push ecx 004039AA . 52 push edx 004039AB . 8D85 64FFFFFF lea eax,dword ptr ss:[ebp-0x9C] 004039B1 . 8D4D 84 lea ecx,dword ptr ss:[ebp-0x7C] 004039B4 . 50 push eax 004039B5 . 8D55 94 lea edx,dword ptr ss:[ebp-0x6C] 004039B8 . 51 push ecx 004039B9 . 8D85 B4FDFFFF lea eax,dword ptr ss:[ebp-0x24C] 004039BF . 52 push edx 004039C0 . 8D8D A4FDFFFF lea ecx,dword ptr ss:[ebp-0x25C] 004039C6 . 50 push eax 004039C7 . 51 push ecx 004039C8 . 6A 20 push 0x20 004039CA . FF15 1C614000 call dword ptr ds:[<&MSVBVM50.__vbaFreeV>; msvbvm50.__vbaFreeVarList 004039D0 . 81C4 84000000 add esp,0x84 004039D6 . 66:3BFE cmp di,si 004039D9 74 22 je short 004039FD ; // 如果正确,将结果给另一个变量赋值 004039DB . 8B45 08 mov eax,dword ptr ss:[ebp+0x8] 004039DE . 8D95 84FDFFFF lea edx,dword ptr ss:[ebp-0x27C] 004039E4 . C785 8CFDFFFF>mov dword ptr ss:[ebp-0x274],0x1 004039EE . 899D 84FDFFFF mov dword ptr ss:[ebp-0x27C],ebx 004039F4 . 8D48 34 lea ecx,dword ptr ds:[eax+0x34] 004039F7 . FF15 10614000 call dword ptr ds:[<&MSVBVM50.__vbaVarMo>; msvbvm50.__vbaVarMove 004039FD > 68 563B4000 push 00403B56 00403A02 . E9 4E010000 jmp 00403B55
上半部分 msvbvm50.rtcMidCharVar 都是对 UNICODE "bPe CrackMe v1.0 " 进行处理,并且结果未发现进行了什么处理,似乎都没什么用处。只有最后的部分才是真正的处理比较。
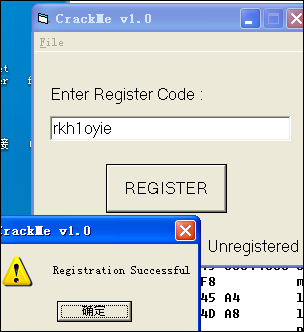
虽然具体内容分析了出来,但是还是不是很明白为什么有这么多的加法和比较,最后得到的文本还是一个固定的:rkh1oyie。
BY 笨笨D幸福