[反汇编练习] 160个CrackMe之031.
本系列文章的目的是从一个没有任何经验的新手的角度(其实就是我自己),一步步尝试将160个CrackMe全部破解,如果可以,通过任何方式写出一个类似于注册机的东西。
其中,文章中按照如下逻辑编排(解决如下问题):
1、使用什么环境和工具
2、程序分析
3、思路分析和破解流程
4、注册机的探索
----------------------------------
提醒各位看客: 如果文章中的逻辑看不明白,那你一定是没有亲手操刀!OD中的跳转提示很强大,只要你跟踪了,不用怎么看代码就理解了!
----------------------------------
1、工具和环境:
WinXP SP3 + 52Pojie六周年纪念版OD + PEID + 汇编金手指。
160个CrackMe的打包文件。
下载地址: http://pan.baidu.com/s/1xUWOY 密码: jbnq
注:
1、Win7系统对于模块和程序开启了随机初始地址的功能,会给分析带来很大的负担,所以不建议使用Win7进行分析。
2、以上工具都是在52PoJie论坛下的原版程序,NOD32不报毒,个人承诺绝对不会进行任何和木马病毒相关内容。
2、程序分析:
想要破解一个程序,必须先了解这个程序。所以,在破解过程中,对最初程序的分析很重要,他可以帮助我们理解作者的目的和意图,特别是对于注册码的处理细节,从而方便我们反向跟踪和推导。
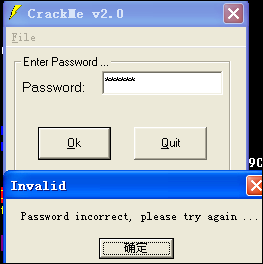
和上一节一样,打开CHM,选择第31个cracking4all.2.exe,保存下来。运行程序,程序界面如下:
点击上面的OK按钮,弹出了信息框,很好。
注意的是,点击确定按钮后,程序直接退出了。
PEID:Microsoft Visual Basic 5.0 / 6.0
哎,又是一个郁闷的征程!
3、思路分析和破解流程
1、打开OD,将exe拖到OD窗口中,等程序暂停后,直接点击运行按钮(F9),不用理会。
2、随意输入伪码:21312321。点击OK按钮,弹出信息框,不要关闭,回到OD。
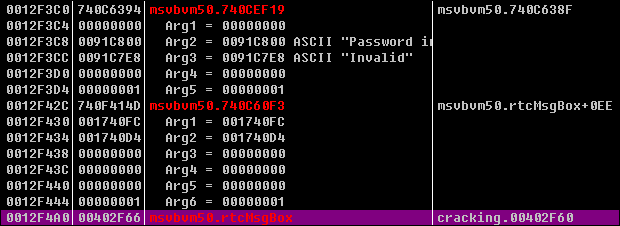
3、Ctrl+K查看堆栈信息:
选中rtcMsgBox,右键->Binary->Fill with NOPs。
4、向上浏览代码:
00402EBA > 8D45 B4 lea eax,dword ptr ss:[ebp-0x4C] 00402EBD . 8D8D 28FFFFFF lea ecx,dword ptr ss:[ebp-0xD8] 00402EC3 . 50 push eax 00402EC4 . 51 push ecx 00402EC5 . C785 30FFFFFF>mov dword ptr ss:[ebp-0xD0],0040259C ; UNICODE "VeiajeEjbavwij" 00402ECF . C785 28FFFFFF>mov dword ptr ss:[ebp-0xD8],0x8008 00402ED9 . FF15 A4614000 call dword ptr ds:[<&MSVBVM50.__vbaVarTs>; msvbvm50.__vbaVarTstNe 00402EDF . 66:85C0 test ax,ax 00402EE2 . /0F84 A1000000 je 00402F89 ; // 关键跳转 00402EE8 . |8B35 A8614000 mov esi,dword ptr ds:[<&MSVBVM50.__vbaVa>; msvbvm50.__vbaVarDup 00402EEE . |B8 04000280 mov eax,0x80020004 00402EF3 . |BB 0A000000 mov ebx,0xA 00402EF8 . |BF 08000000 mov edi,0x8 00402EFD . |8D95 18FFFFFF lea edx,dword ptr ss:[ebp-0xE8] 00402F03 . |8D4D 88 lea ecx,dword ptr ss:[ebp-0x78] 00402F06 . |8985 70FFFFFF mov dword ptr ss:[ebp-0x90],eax 00402F0C . |899D 68FFFFFF mov dword ptr ss:[ebp-0x98],ebx 00402F12 . |8945 80 mov dword ptr ss:[ebp-0x80],eax 00402F15 . |899D 78FFFFFF mov dword ptr ss:[ebp-0x88],ebx 00402F1B . |C785 20FFFFFF>mov dword ptr ss:[ebp-0xE0],00402618 ; UNICODE "Invalid" 00402F25 . |89BD 18FFFFFF mov dword ptr ss:[ebp-0xE8],edi 00402F2B . |FFD6 call esi ; <&MSVBVM50.__vbaVarDup> 00402F2D . |8D95 28FFFFFF lea edx,dword ptr ss:[ebp-0xD8] 00402F33 . |8D4D 98 lea ecx,dword ptr ss:[ebp-0x68] 00402F36 . |C785 30FFFFFF>mov dword ptr ss:[ebp-0xD0],004025C0 ; UNICODE "Password incorrect, please try again ..." 00402F40 . |89BD 28FFFFFF mov dword ptr ss:[ebp-0xD8],edi 00402F46 . |FFD6 call esi 00402F48 . |8D95 68FFFFFF lea edx,dword ptr ss:[ebp-0x98] 00402F4E . |8D85 78FFFFFF lea eax,dword ptr ss:[ebp-0x88] 00402F54 . |52 push edx 00402F55 . |8D4D 88 lea ecx,dword ptr ss:[ebp-0x78] 00402F58 . |50 push eax 00402F59 . |51 push ecx 00402F5A . |8D55 98 lea edx,dword ptr ss:[ebp-0x68] 00402F5D . |6A 00 push 0x0 00402F5F . |52 push edx 00402F60 . |FF15 2C614000 call dword ptr ds:[<&MSVBVM50.#595>] ; msvbvm50.rtcMsgBox 00402F66 . |8D85 68FFFFFF lea eax,dword ptr ss:[ebp-0x98] 00402F6C . |8D8D 78FFFFFF lea ecx,dword ptr ss:[ebp-0x88] 00402F72 . |50 push eax 00402F73 . |8D55 88 lea edx,dword ptr ss:[ebp-0x78] 00402F76 . |51 push ecx 00402F77 . |8D45 98 lea eax,dword ptr ss:[ebp-0x68] 00402F7A . |52 push edx 00402F7B . |50 push eax 00402F7C . |6A 04 push 0x4 00402F7E . |FF15 08614000 call dword ptr ds:[<&MSVBVM50.__vbaFreeV>; msvbvm50.__vbaFreeVarList 00402F84 . |83C4 14 add esp,0x14 00402F87 . |EB 10 jmp short 00402F99 00402F89 > 8B35 A8614000 mov esi,dword ptr ds:[<&MSVBVM50.__vbaVa>; msvbvm50.__vbaVarDup 00402F8F . BB 0A000000 mov ebx,0xA 00402F94 . BF 08000000 mov edi,0x8 00402F99 > 8D4D B4 lea ecx,dword ptr ss:[ebp-0x4C] 00402F9C . 8D95 28FFFFFF lea edx,dword ptr ss:[ebp-0xD8] 00402FA2 . 51 push ecx ; /Arg2 00402FA3 . 52 push edx ; |Arg1 00402FA4 . C785 30FFFFFF>mov dword ptr ss:[ebp-0xD0],0040259C ; |UNICODE "VeiajeEjbavwij" 00402FAE . C785 28FFFFFF>mov dword ptr ss:[ebp-0xD8],0x8008 ; | 00402FB8 . FF15 4C614000 call dword ptr ds:[<&MSVBVM50.__vbaVarTs>; \__vbaVarTstEq 00402FBE . 66:85C0 test ax,ax 00402FC1 . 0F84 8F000000 je 00403056 00402FC7 . B8 04000280 mov eax,0x80020004 00402FCC . 8D95 18FFFFFF lea edx,dword ptr ss:[ebp-0xE8] 00402FD2 . 8D4D 88 lea ecx,dword ptr ss:[ebp-0x78] 00402FD5 . 8985 70FFFFFF mov dword ptr ss:[ebp-0x90],eax 00402FDB . 899D 68FFFFFF mov dword ptr ss:[ebp-0x98],ebx 00402FE1 . 8945 80 mov dword ptr ss:[ebp-0x80],eax 00402FE4 . 899D 78FFFFFF mov dword ptr ss:[ebp-0x88],ebx 00402FEA . C785 20FFFFFF>mov dword ptr ss:[ebp-0xE0],00402668 ; UNICODE "Valid" 00402FF4 . 89BD 18FFFFFF mov dword ptr ss:[ebp-0xE8],edi 00402FFA . FFD6 call esi 00402FFC . 8D95 28FFFFFF lea edx,dword ptr ss:[ebp-0xD8] 00403002 . 8D4D 98 lea ecx,dword ptr ss:[ebp-0x68] 00403005 . C785 30FFFFFF>mov dword ptr ss:[ebp-0xD0],0040262C ; UNICODE "Password correct, hehe, :-)" 0040300F . 89BD 28FFFFFF mov dword ptr ss:[ebp-0xD8],edi 00403015 . FFD6 call esi 00403017 . 8D85 68FFFFFF lea eax,dword ptr ss:[ebp-0x98] 0040301D . 8D8D 78FFFFFF lea ecx,dword ptr ss:[ebp-0x88] 00403023 . 50 push eax 00403024 . 8D55 88 lea edx,dword ptr ss:[ebp-0x78] 00403027 . 51 push ecx 00403028 . 52 push edx 00403029 . 8D45 98 lea eax,dword ptr ss:[ebp-0x68] 0040302C . 6A 00 push 0x0 0040302E . 50 push eax 0040302F . FF15 2C614000 call dword ptr ds:[<&MSVBVM50.#595>] ; msvbvm50.rtcMsgBox
这里使用msvbvm50.__vbaVarTstNe 进行文本比较,下面的00402EE2 地址处 je 00402F89就是关键跳转。
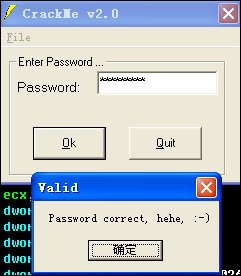
爆破,修改 je 00402F89 为jmp 00402F89,但是发现地址00402F89又进行了一次判断,所以还需要把这个判断屏蔽掉,修改je 00403056,使用NOPs填充!
OK!
4、注册机的探索
直接向上到段头,开始分析:
00402BF8 . FF15 1C614000 call dword ptr ds:[<&MSVBVM50.__vbaHresultCheckObj>; msvbvm50.__vbaHresultCheckObj 00402BFE > 8B45 B0 mov eax,dword ptr ss:[ebp-0x50] 00402C01 . 8D55 98 lea edx,dword ptr ss:[ebp-0x68] 00402C04 . 8D4D D8 lea ecx,dword ptr ss:[ebp-0x28] 00402C07 . 8975 B0 mov dword ptr ss:[ebp-0x50],esi 00402C0A . 8945 A0 mov dword ptr ss:[ebp-0x60],eax 00402C0D . C745 98 08000>mov dword ptr ss:[ebp-0x68],0x8 00402C14 . FF15 00614000 call dword ptr ds:[<&MSVBVM50.__vbaVarMove>] ; msvbvm50.__vbaVarMove 00402C1A . 8D4D A8 lea ecx,dword ptr ss:[ebp-0x58] 00402C1D . FF15 C0614000 call dword ptr ds:[<&MSVBVM50.__vbaFreeObj>] ; msvbvm50.__vbaFreeObj 00402C23 . 8D4D D8 lea ecx,dword ptr ss:[ebp-0x28] 00402C26 . 8D55 98 lea edx,dword ptr ss:[ebp-0x68] 00402C29 . 51 push ecx ; /Arg2 00402C2A . 52 push edx ; |Arg1 00402C2B . FF15 20614000 call dword ptr ds:[<&MSVBVM50.__vbaLenVar>] ; \__vbaLenVar 00402C31 . 50 push eax ; // eax = 9 00402C32 . FF15 7C614000 call dword ptr ds:[<&MSVBVM50.__vbaI2Var>] ; msvbvm50.__vbaI2Var 00402C38 . 8B35 14614000 mov esi,dword ptr ds:[<&MSVBVM50.#516>] ; msvbvm50.rtcAnsiValueBstr 00402C3E . 8B3D 74614000 mov edi,dword ptr ds:[<&MSVBVM50.__vbaStrVarVal>] ; msvbvm50.__vbaStrVarVal 00402C44 . 8985 E8FEFFFF mov dword ptr ss:[ebp-0x118],eax 00402C4A . B8 01000000 mov eax,0x1 ; // eax = 1 00402C4F . 8945 C4 mov dword ptr ss:[ebp-0x3C],eax 00402C52 > 66:3B85 E8FEF>cmp ax,word ptr ss:[ebp-0x118] ; // 循环开始头,ax++ 00402C59 . 8B1D 40614000 mov ebx,dword ptr ds:[<&MSVBVM50.#632>] ; msvbvm50.rtcMidCharVar 00402C5F . 0F8F EF000000 jg 00402D54 00402C65 . 0FBFD0 movsx edx,ax 00402C68 . 8D4D 98 lea ecx,dword ptr ss:[ebp-0x68] 00402C6B . 8D45 D8 lea eax,dword ptr ss:[ebp-0x28] 00402C6E . 51 push ecx ; // ecx = 9 1 00402C6F . 52 push edx ; // edx = ax = 1,2,... 00402C70 . 8D4D 88 lea ecx,dword ptr ss:[ebp-0x78] 00402C73 . 50 push eax ; // eax ="123123123" 00402C74 . 51 push ecx 00402C75 . C745 A0 01000>mov dword ptr ss:[ebp-0x60],0x1 00402C7C . C745 98 02000>mov dword ptr ss:[ebp-0x68],0x2 00402C83 . FFD3 call ebx ; msvbvm50.rtcMidCharVar; <&MSVBVM50.#632> 00402C85 . 8D95 78FFFFFF lea edx,dword ptr ss:[ebp-0x88] 00402C8B . 6A 01 push 0x1 ; /Arg3 = 00000001 00402C8D . 8D85 68FFFFFF lea eax,dword ptr ss:[ebp-0x98] ; | 00402C93 . 52 push edx ; |Arg2=4 00402C94 . 50 push eax ; |Arg1 00402C95 . C745 80 04000>mov dword ptr ss:[ebp-0x80],0x4 ; | 00402C9C . C785 78FFFFFF>mov dword ptr ss:[ebp-0x88],0x2 ; | 00402CA6 . FF15 AC614000 call dword ptr ds:[<&MSVBVM50.#617>] ; tcLeftCharVar 00402CAC . 8D8D 68FFFFFF lea ecx,dword ptr ss:[ebp-0x98] ; // eax = "4" 00402CB2 . 8D55 AC lea edx,dword ptr ss:[ebp-0x54] 00402CB5 . 51 push ecx 00402CB6 . 52 push edx 00402CB7 . FFD7 call edi ; msvbvm50.__vbaStrVarVal 00402CB9 . 50 push eax ; // eax = "4" 00402CBA . FFD6 call esi ; msvbvm50.rtcAnsiValueBstr 00402CBC . 0FBFD8 movsx ebx,ax 00402CBF . 8D45 88 lea eax,dword ptr ss:[ebp-0x78] 00402CC2 . 8D4D B0 lea ecx,dword ptr ss:[ebp-0x50] 00402CC5 . 50 push eax ; "1" 00402CC6 . 51 push ecx 00402CC7 . FFD7 call edi ; msvbvm50.__vbaStrVarVal 00402CC9 . 50 push eax 00402CCA . FFD6 call esi ; msvbvm50.rtcAnsiValueBstr 00402CCC . 0FBFD0 movsx edx,ax 00402CCF . 33DA xor ebx,edx ; // 将两个数异或 00402CD1 . 8D85 58FFFFFF lea eax,dword ptr ss:[ebp-0xA8] 00402CD7 . 53 push ebx ; /Arg2 00402CD8 . 50 push eax ; |Arg1 00402CD9 . FF15 6C614000 call dword ptr ds:[<&MSVBVM50.#608>] ; tcVarBstrFromAnsi 00402CDF . 8D4D C8 lea ecx,dword ptr ss:[ebp-0x38] 00402CE2 . 8D95 58FFFFFF lea edx,dword ptr ss:[ebp-0xA8] 00402CE8 . 51 push ecx ; /Arg3 = [] = 4 00402CE9 . 8D85 48FFFFFF lea eax,dword ptr ss:[ebp-0xB8] ; | 00402CEF . 52 push edx ; |Arg2 00402CF0 . 50 push eax ; |Arg1 00402CF1 . FF15 78614000 call dword ptr ds:[<&MSVBVM50.__vbaVarCat>] ; \__vbaVarCat 00402CF7 . 8BD0 mov edx,eax 00402CF9 . 8D4D C8 lea ecx,dword ptr ss:[ebp-0x38] 00402CFC . FF15 00614000 call dword ptr ds:[<&MSVBVM50.__vbaVarMove>] ; msvbvm50.__vbaVarMove 00402D02 . 8D4D AC lea ecx,dword ptr ss:[ebp-0x54] 00402D05 . 8D55 B0 lea edx,dword ptr ss:[ebp-0x50] 00402D08 . 51 push ecx 00402D09 . 52 push edx 00402D0A . 6A 02 push 0x2 00402D0C . FF15 94614000 call dword ptr ds:[<&MSVBVM50.__vbaFreeStrList>] ; msvbvm50.__vbaFreeStrList 00402D12 . 83C4 0C add esp,0xC 00402D15 . 8D85 58FFFFFF lea eax,dword ptr ss:[ebp-0xA8] 00402D1B . 8D8D 68FFFFFF lea ecx,dword ptr ss:[ebp-0x98] 00402D21 . 8D95 78FFFFFF lea edx,dword ptr ss:[ebp-0x88] 00402D27 . 50 push eax 00402D28 . 51 push ecx 00402D29 . 8D45 88 lea eax,dword ptr ss:[ebp-0x78] 00402D2C . 52 push edx 00402D2D . 8D4D 98 lea ecx,dword ptr ss:[ebp-0x68] 00402D30 . 50 push eax 00402D31 . 51 push ecx 00402D32 . 6A 05 push 0x5 00402D34 . FF15 08614000 call dword ptr ds:[<&MSVBVM50.__vbaFreeVarList>] ; msvbvm50.__vbaFreeVarList 00402D3A . B8 01000000 mov eax,0x1 00402D3F . 83C4 18 add esp,0x18 00402D42 . 66:0345 C4 add ax,word ptr ss:[ebp-0x3C] 00402D46 . 0F80 A0030000 jo 004030EC 00402D4C . 8945 C4 mov dword ptr ss:[ebp-0x3C],eax 00402D4F .^ E9 FEFEFFFF jmp 00402C52 00402D54 > 8D55 C8 lea edx,dword ptr ss:[ebp-0x38] ; // 0016E474 00402D57 . 8D45 98 lea eax,dword ptr ss:[ebp-0x68] 00402D5A . 52 push edx ; /Arg2 00402D5B . 50 push eax ; |Arg1 00402D5C . C745 E8 01000>mov dword ptr ss:[ebp-0x18],0x1 ; | 00402D63 . FF15 20614000 call dword ptr ds:[<&MSVBVM50.__vbaLenVar>] ; \__vbaLenVar 00402D69 . 50 push eax 00402D6A . FF15 7C614000 call dword ptr ds:[<&MSVBVM50.__vbaI2Var>] ; msvbvm50.__vbaI2Var 00402D70 . B9 01000000 mov ecx,0x1 00402D75 . 8985 E0FEFFFF mov dword ptr ss:[ebp-0x120],eax 00402D7B . 8BC1 mov eax,ecx 00402D7D . 8945 C4 mov dword ptr ss:[ebp-0x3C],eax 00402D80 > 66:3B85 E0FEF>cmp ax,word ptr ss:[ebp-0x120] 00402D87 . 0F8F 2D010000 jg 00402EBA 00402D8D . 66:837D E8 04 cmp word ptr ss:[ebp-0x18],0x4 00402D92 . 7E 03 jle short 00402D97 00402D94 . 894D E8 mov dword ptr ss:[ebp-0x18],ecx 00402D97 > 894D A0 mov dword ptr ss:[ebp-0x60],ecx 00402D9A . 8D4D 98 lea ecx,dword ptr ss:[ebp-0x68] 00402D9D . 0FBFD0 movsx edx,ax 00402DA0 . 51 push ecx 00402DA1 . 8D45 C8 lea eax,dword ptr ss:[ebp-0x38] 00402DA4 . 52 push edx ; // edx = 1 00402DA5 . 8D4D 88 lea ecx,dword ptr ss:[ebp-0x78] 00402DA8 . 50 push eax ; // eax = 上一个的返回值 00402DA9 . 51 push ecx 00402DAA . C745 98 02000>mov dword ptr ss:[ebp-0x68],0x2 00402DB1 . FFD3 call ebx ; msvbvm50.rtcMidCharVar 00402DB3 . B8 02000000 mov eax,0x2 00402DB8 . 8D95 68FFFFFF lea edx,dword ptr ss:[ebp-0x98] 00402DBE . 8985 68FFFFFF mov dword ptr ss:[ebp-0x98],eax 00402DC4 . 8985 78FFFFFF mov dword ptr ss:[ebp-0x88],eax 00402DCA . 0FBF45 E8 movsx eax,word ptr ss:[ebp-0x18] 00402DCE . 52 push edx ; "4" 00402DCF . 8D8D 78FFFFFF lea ecx,dword ptr ss:[ebp-0x88] 00402DD5 . 50 push eax ; 1 00402DD6 . 8D95 58FFFFFF lea edx,dword ptr ss:[ebp-0xA8] 00402DDC . 51 push ecx ; 4 00402DDD . 52 push edx 00402DDE . C785 70FFFFFF>mov dword ptr ss:[ebp-0x90],0x1 00402DE8 . C745 80 D0070>mov dword ptr ss:[ebp-0x80],0x7D0 00402DEF . FFD3 call ebx ; msvbvm50.rtcMidCharVar 00402DF1 . 8D85 58FFFFFF lea eax,dword ptr ss:[ebp-0xA8] 00402DF7 . 8D4D AC lea ecx,dword ptr ss:[ebp-0x54] 00402DFA . 50 push eax 00402DFB . 51 push ecx 00402DFC . FFD7 call edi ; msvbvm50.__vbaStrVarVal 00402DFE . 50 push eax ; "2" 00402DFF . FFD6 call esi 00402E01 . 0FBFD8 movsx ebx,ax 00402E04 . 8D55 88 lea edx,dword ptr ss:[ebp-0x78] 00402E07 . 8D45 B0 lea eax,dword ptr ss:[ebp-0x50] 00402E0A . 52 push edx 00402E0B . 50 push eax 00402E0C . FFD7 call edi 00402E0E . 50 push eax 00402E0F . FFD6 call esi ; msvbvm50.rtcAnsiValueBstr 00402E11 . 0FBFC8 movsx ecx,ax ; // ecx = ax=5 00402E14 . 33D9 xor ebx,ecx ; // 异或 00402E16 . 8D95 48FFFFFF lea edx,dword ptr ss:[ebp-0xB8] 00402E1C . 53 push ebx ; /Arg2 00402E1D . 52 push edx ; |Arg1 00402E1E . FF15 6C614000 call dword ptr ds:[<&MSVBVM50.#608>] ; tcVarBstrFromAnsi 00402E24 . 8D45 B4 lea eax,dword ptr ss:[ebp-0x4C] 00402E27 . 8D8D 48FFFFFF lea ecx,dword ptr ss:[ebp-0xB8] 00402E2D . 50 push eax ; /Arg3 00402E2E . 8D95 38FFFFFF lea edx,dword ptr ss:[ebp-0xC8] ; | 00402E34 . 51 push ecx ; |Arg2 00402E35 . 52 push edx ; |Arg1 00402E36 . FF15 78614000 call dword ptr ds:[<&MSVBVM50.__vbaVarCat>] ; \__vbaVarCat 00402E3C . 8BD0 mov edx,eax 00402E3E . 8D4D B4 lea ecx,dword ptr ss:[ebp-0x4C] 00402E41 . FF15 00614000 call dword ptr ds:[<&MSVBVM50.__vbaVarMove>] ; msvbvm50.__vbaVarMove 00402E47 . 8D45 AC lea eax,dword ptr ss:[ebp-0x54] 00402E4A . 8D4D B0 lea ecx,dword ptr ss:[ebp-0x50] 00402E4D . 50 push eax 00402E4E . 51 push ecx 00402E4F . 6A 02 push 0x2 00402E51 . FF15 94614000 call dword ptr ds:[<&MSVBVM50.__vbaFreeStrList>] ; msvbvm50.__vbaFreeStrList 00402E57 . 83C4 0C add esp,0xC 00402E5A . 8D95 48FFFFFF lea edx,dword ptr ss:[ebp-0xB8] 00402E60 . 8D85 58FFFFFF lea eax,dword ptr ss:[ebp-0xA8] 00402E66 . 8D8D 68FFFFFF lea ecx,dword ptr ss:[ebp-0x98] 00402E6C . 52 push edx 00402E6D . 50 push eax 00402E6E . 8D95 78FFFFFF lea edx,dword ptr ss:[ebp-0x88] 00402E74 . 51 push ecx 00402E75 . 8D45 88 lea eax,dword ptr ss:[ebp-0x78] 00402E78 . 52 push edx 00402E79 . 8D4D 98 lea ecx,dword ptr ss:[ebp-0x68] 00402E7C . 50 push eax 00402E7D . 51 push ecx 00402E7E . 6A 06 push 0x6 00402E80 . FF15 08614000 call dword ptr ds:[<&MSVBVM50.__vbaFreeVarList>] ; msvbvm50.__vbaFreeVarList 00402E86 . 66:8B55 E8 mov dx,word ptr ss:[ebp-0x18] 00402E8A . 83C4 1C add esp,0x1C 00402E8D . 66:42 inc dx 00402E8F . 0F80 57020000 jo 004030EC 00402E95 . 8B1D 40614000 mov ebx,dword ptr ds:[<&MSVBVM50.#632>] ; msvbvm50.rtcMidCharVar 00402E9B . B8 01000000 mov eax,0x1 00402EA0 . 66:0345 C4 add ax,word ptr ss:[ebp-0x3C] 00402EA4 . 8955 E8 mov dword ptr ss:[ebp-0x18],edx 00402EA7 . B9 01000000 mov ecx,0x1 00402EAC . 0F80 3A020000 jo 004030EC 00402EB2 . 8945 C4 mov dword ptr ss:[ebp-0x3C],eax 00402EB5 .^ E9 C6FEFFFF jmp 00402D80 00402EBA > 8D45 B4 lea eax,dword ptr ss:[ebp-0x4C] 00402EBD . 8D8D 28FFFFFF lea ecx,dword ptr ss:[ebp-0xD8] 00402EC3 . 50 push eax ; //"767547565" 00402EC4 . 51 push ecx ; //"VeiajeEjbavwij" 00402EC5 . C785 30FFFFFF>mov dword ptr ss:[ebp-0xD0],0040259C ; UNICODE "VeiajeEjbavwij" 00402ECF . C785 28FFFFFF>mov dword ptr ss:[ebp-0xD8],0x8008 00402ED9 . FF15 A4614000 call dword ptr ds:[<&MSVBVM50.__vbaVarTstNe>] ; msvbvm50.__vbaVarTstNe 00402EDF . 66:85C0 test ax,ax 00402EE2 0F84 A1000000 je 00402F89 ; // 关键跳转
核心流程和上一个一样,都是取一个字符,然后与另外一个异或,另外的那个字符也很难理清楚是什么,使用其他手段看看吧!
VB反编译:
Private Sub Command1_Click() '402B40
Dim var_58 As TextBox
loc_00402B72: var_8 = &H401000
loc_00402BD3: Set var_58 = Me
loc_00402BE2: var_50 = Text1.Text
loc_00402C0A: var_60 = var_50
loc_00402C0D: var_68 = 8
loc_00402C14: var_28 = var_50
loc_00402C2B: var_68 = Len(var_28)
loc_00402C44: var_118 = CInt(var_50)
loc_00402C4F: var_3C = 1
If 00000001h > 0 Then GoTo loc_00402D54
loc_00402C75: var_60 = 1
loc_00402C7C: var_68 = 2
loc_00402C83: var_78 = Mid$(var_28, 1, 1)
loc_00402C95: var_80 = 4
loc_00402C9C: var_88 = 2
loc_00402CA6: var_98 = Left(4, 1)
loc_00402CB7: var_54 = CStr(var_98)
loc_00402CC7: var_50 = CStr(var_78)
loc_00402CD9: var_A8 = Chr(Asc(var_54) xor edx)
loc_00402CFC: var_38 = var_38 & 4
loc_00402D42: 00000001h = 00000001h + 1
loc_00402D4C: var_3C = 1
loc_00402D4F: GoTo loc_00402C52
loc_00402D54:
loc_00402D5C: var_18 = 1
loc_00402D63: var_68 = Len(var_38)
loc_00402D75: var_120 = CInt(var_58)
loc_00402D7D: var_3C = 1
If 00000001h > 0 Then GoTo loc_00402EBA
If 1 <= 0 Then GoTo loc_00402D97
loc_00402D94: var_18 = 1
loc_00402D97: var_60 = 1
loc_00402DB1: call Asc(var_54) xor edx(var_78, var_38, 00000001h, 2, 00402588h, 000000A0h, var_98, var_A8, var_58)
loc_00402DDE: var_90 = 1
loc_00402DE8: var_80 = &H7D0
loc_00402DEF: call Asc(var_54) xor edx(var_A8, 2, 1, 2)
loc_00402E0C: var_50 = CStr(var_78)
loc_00402E1E: var_B8 = Chr(Asc(CStr(var_A8)) xor ecx)
loc_00402E41: var_4C = var_4C & 1
loc_00402E8D: dx = 1 + 1
loc_00402EA0: 00000001h = 00000001h + 1
loc_00402EB2: var_3C = 1
loc_00402EB5: GoTo loc_00402D80
loc_00402EBA:
loc_00402EC5: var_D0 = "VeiajeEjbavwij"
loc_00402ECF: var_D8 = &H8008
loc_00402ED9: Var_Ret_1 = (var_4C <> "VeiajeEjbavwij")
If Var_Ret_1 = 0 Then GoTo loc_00402F89
loc_00402F06: var_90 = 80020004h
loc_00402F0C: var_98 = 10
loc_00402F12: var_80 = 80020004h
loc_00402F15: var_88 = 10
loc_00402F1B: var_E0 = "Invalid"
loc_00402F25: var_E8 = 8
loc_00402F36: var_D0 = "Password incorrect, please try again ..."
loc_00402F40: var_D8 = 8
loc_00402F60: MsgBox "Password incorrect, please try again ...", 0, "Invalid"
loc_00402FA4: var_D0 = "VeiajeEjbavwij"
loc_00402FAE: var_D8 = &H8008
loc_00402FB8: Var_Ret_2 = (var_4C = "VeiajeEjbavwij")
If Var_Ret_2 = 0 Then GoTo loc_00403056
loc_00402FD5: var_90 = 80020004h
loc_00402FDB: var_98 = 10
loc_00402FE1: var_80 = 80020004h
loc_00402FE4: var_88 = 10
loc_00402FEA: var_E0 = "Valid"
loc_00402FF4: var_E8 = 8
loc_00403005: var_D0 = "Password correct, hehe, :-)"
loc_0040300F: var_D8 = 8
loc_0040302F: MsgBox "Password correct, hehe, :-)", 0, "Valid"
loc_00403056: var_4 = 0
loc_00403062: GoTo loc_004030B7
loc_004030B6: Exit Sub
loc_004030B7:
loc_004030CA: GoTo loc_00esi
loc_004030CC: Exit Sub
End Sub
晕啊,中间的那个异或也太复杂了!
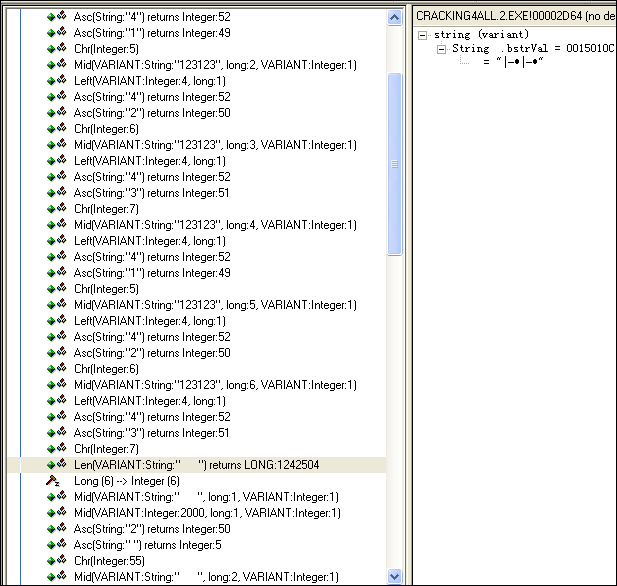
SmartCheck:
看完这个,对那个无法显示出来的字符疑惑了,它是从哪里来的呢?继续跟踪OD分析,发现,他就是第一部分异或得到的字符串,然后继续与2000的每个字符进行异或处理,大概是这样的:
pKey[i]=pName[i]^'4';
pKey[i]=pKey[i]^"2000"[i%4];
pKey == "VeiajeEjbavwij";
所以,pName长度必须是14。我们反过来算原码:
// CrackMeDemo.cpp : 定义控制台应用程序的入口点。
//
#include "stdafx.h"
#include <iostream>
/*
pKey[i]=pName[i]^'4';
pKey[i]=pKey[i]^"2000"[i%4];
pKey == "VeiajeEjbavwij";
*/
int _tmain(int argc, _TCHAR* argv[])
{
char pkey[] = "VeiajeEjbavwij";
char pName[15] = {0};
int nLen = strlen(pkey);
for (int i=0;i<nLen;i++)
{
pName[i] = pkey[i] ^ "2000"[i%4];
pName[i] = pName[i] ^ '4';
}
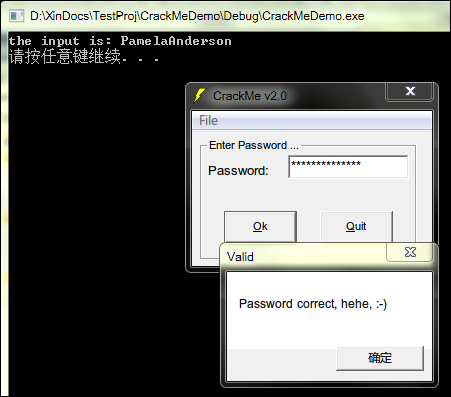
printf("the input is: %s
",pName);
system("pause");
return 0;
}BY 笨笨D幸福