
在用Fiddler抓包的时候,遇到这种包类型.里面的数据是乱码的.这样改怎么查看原文呢.
Content-Disposition: form-data; name=xDeviceInfo
Content-Type: application/octet-stream
Content-Length: 241
Raw的数据是
POST http://hsa.m.800best.com/hsaapi/v1/RealNameService/SubmitRealNameCustomerReceiveInfo HTTP/1.1
X-Auth-Site: 327232
X-Auth-User: 327232.002
X-Auth-Token: ed56d35f-0e63-482e-852e-42ab68070290
X-ClientVersion: 670
X-ClientTime: 2020-06-05T14:11:36.409+08:00
X-SerializationType: json
X-Sequence: f704f9dc-0b68-44b6-8ef5-247d62354038
X-SystemType: android
X-PackageName: com.best.android.hsandroid
X-SystemVersion: 24
X-AppVersion: 670
X-CompressType: gzip
Content-Type: multipart/form-data; boundary=c94e71d4-0cbd-47d9-8e68-8f1c07465123
Content-Length: 1669
Host: hsa.m.800best.com
Connection: Keep-Alive
Accept-Encoding: gzip
User-Agent: okhttp/3.10.0
--c94e71d4-0cbd-47d9-8e68-8f1c07465123
Content-Disposition: form-data; name=xDeviceInfo
Content-Type: application/octet-stream
Content-Length: 241
m n D g ` U{j/ nT EU H9 ff 5
=w h R } w~ y y;F79 K = |N a kps ? PH Z Oa 3i
8
; a - _ *
P 9 $ fh =z^+ B TOq' " A*5y Ȃ n K 8n ]> ZB 6 ^? p 3<l Y
--c94e71d4-0cbd-47d9-8e68-8f1c07465123
Content-Disposition: form-data; name=xLocation
Content-Type: application/octet-stream
Content-Length: 74
VJLN.-JL T 2 3 Q I, ,)MI q ґ E e ) EJVJI ) %@^- [ ˲H
--c94e71d4-0cbd-47d9-8e68-8f1c07465123
Content-Disposition: form-data; name=userName
Content-Type: application/octet-stream
Content-Length: 31
Sz qճ}O ە
--c94e71d4-0cbd-47d9-8e68-8f1c07465123
Content-Disposition: form-data; name=siteCode
Content-Type: application/octet-stream
Content-Length: 28
S262726R ˹VY
--c94e71d4-0cbd-47d9-8e68-8f1c07465123
Content-Disposition: form-data; name=clientTime
Content-Type: application/octet-stream
Content-Length: 51
S2202 50 50
14 24 26 3 6 20P D
--c94e71d4-0cbd-47d9-8e68-8f1c07465123
Content-Disposition: form-data; name=scanDataList
Content-Type: application/octet-stream
Content-Length: 284
n 0
E k
.
y+ B D , 2# ͐
D f` Vl y u
J Ab
{ I z sl ]R
F ܛJ P Z"Gp R? j e ~ ʲ͛R<a# 5:
%Y˲ 5 U) h " A6l <2 C P
G Y` TM[e +V|ܧ u4 q ;F t 4c Ma
" p> w /e 3
G K` M @ _ / o lwi4 s O
--c94e71d4-0cbd-47d9-8e68-8f1c07465123--
从请求头里可以看到是Accept-Encoding: gzip
这样的话需要在HexView里复制相应的16进制源数据,然后进行Gzip解压
找到相对应的数据,根据经验可得
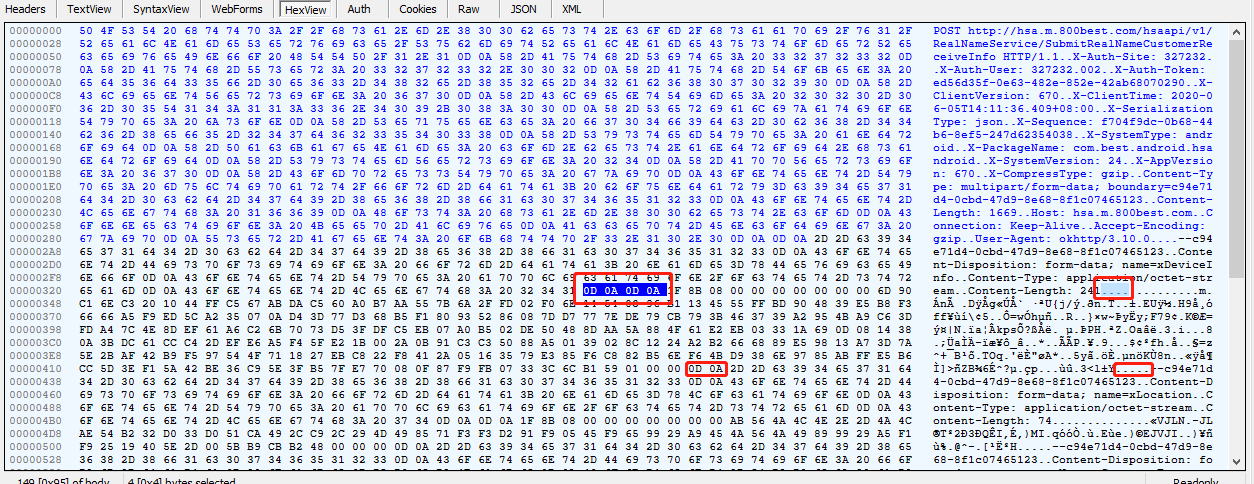
16进制的0D 0A 对应的字符串其实是 ,那么就从0D0A开始,一直到下个0D0A结束,这个就是压缩过的数据,然后复制这串数据
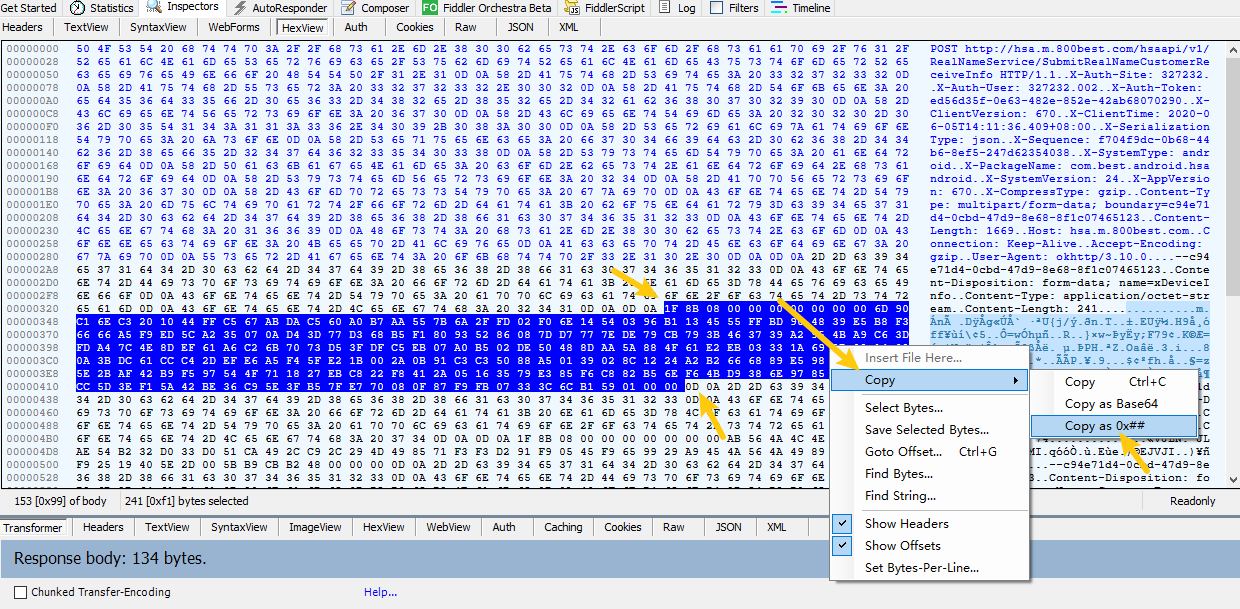
把这串数据放到下面的代码里,然后用python执行即可
复制出来是这样的一串代码
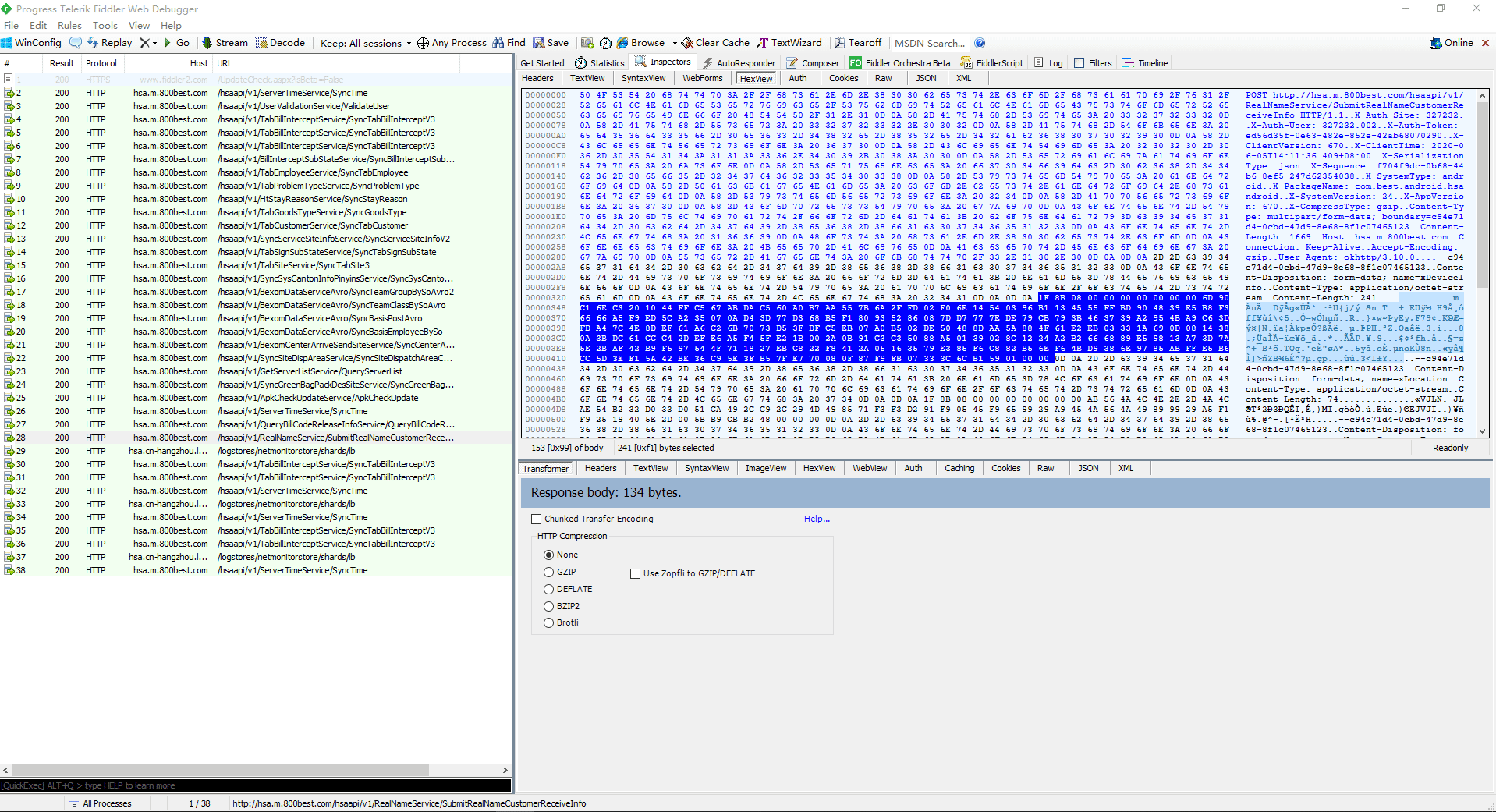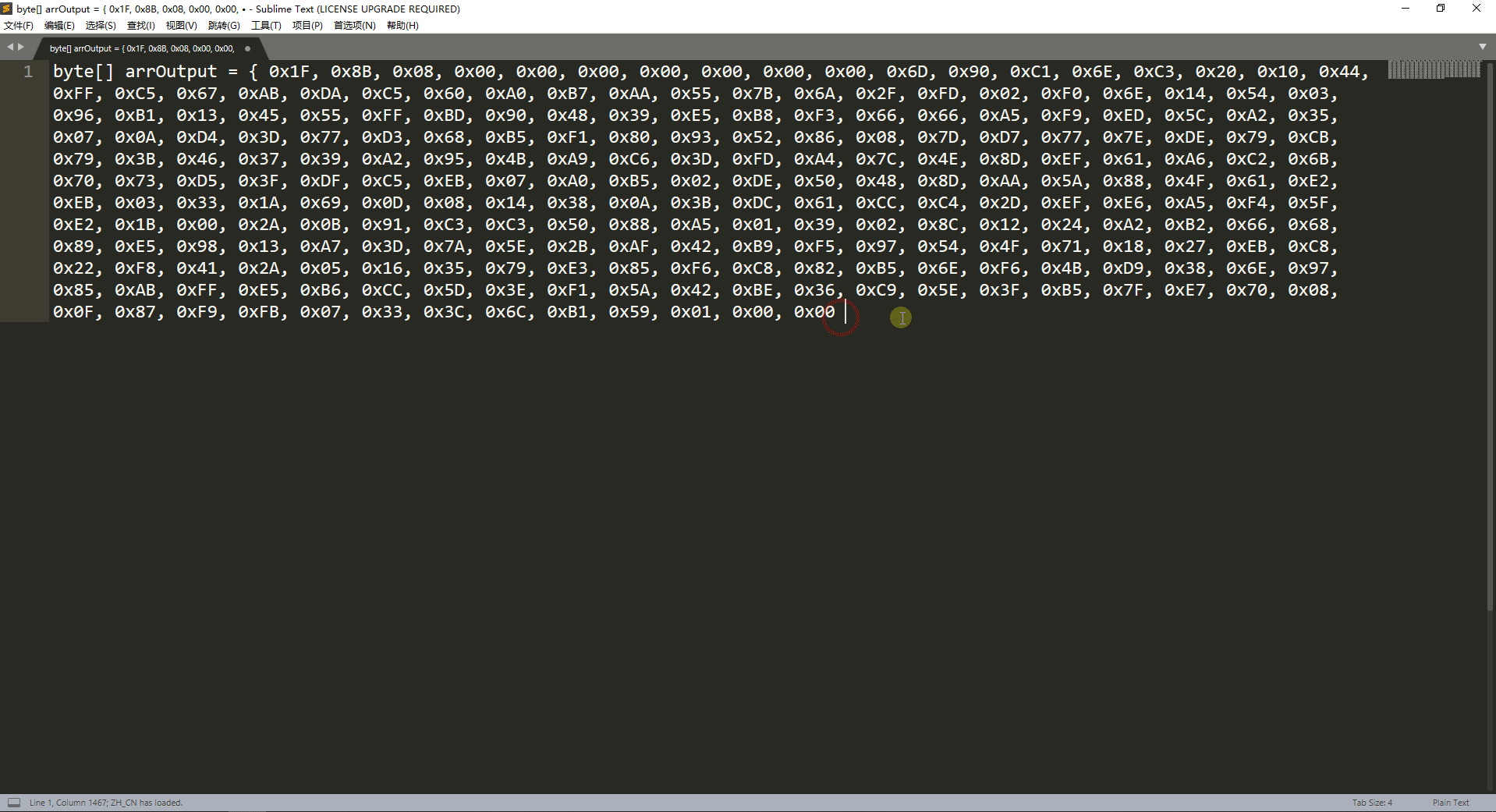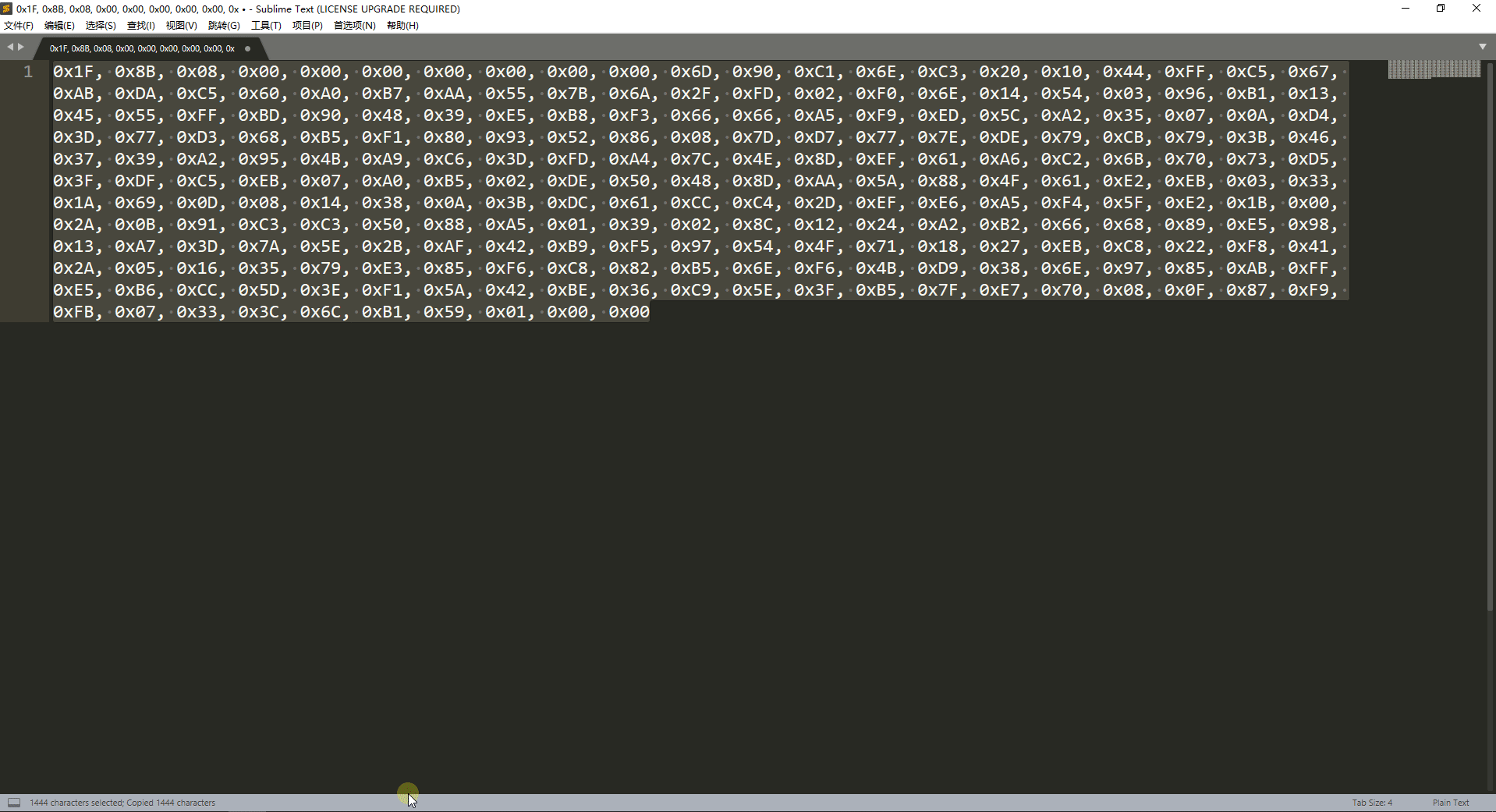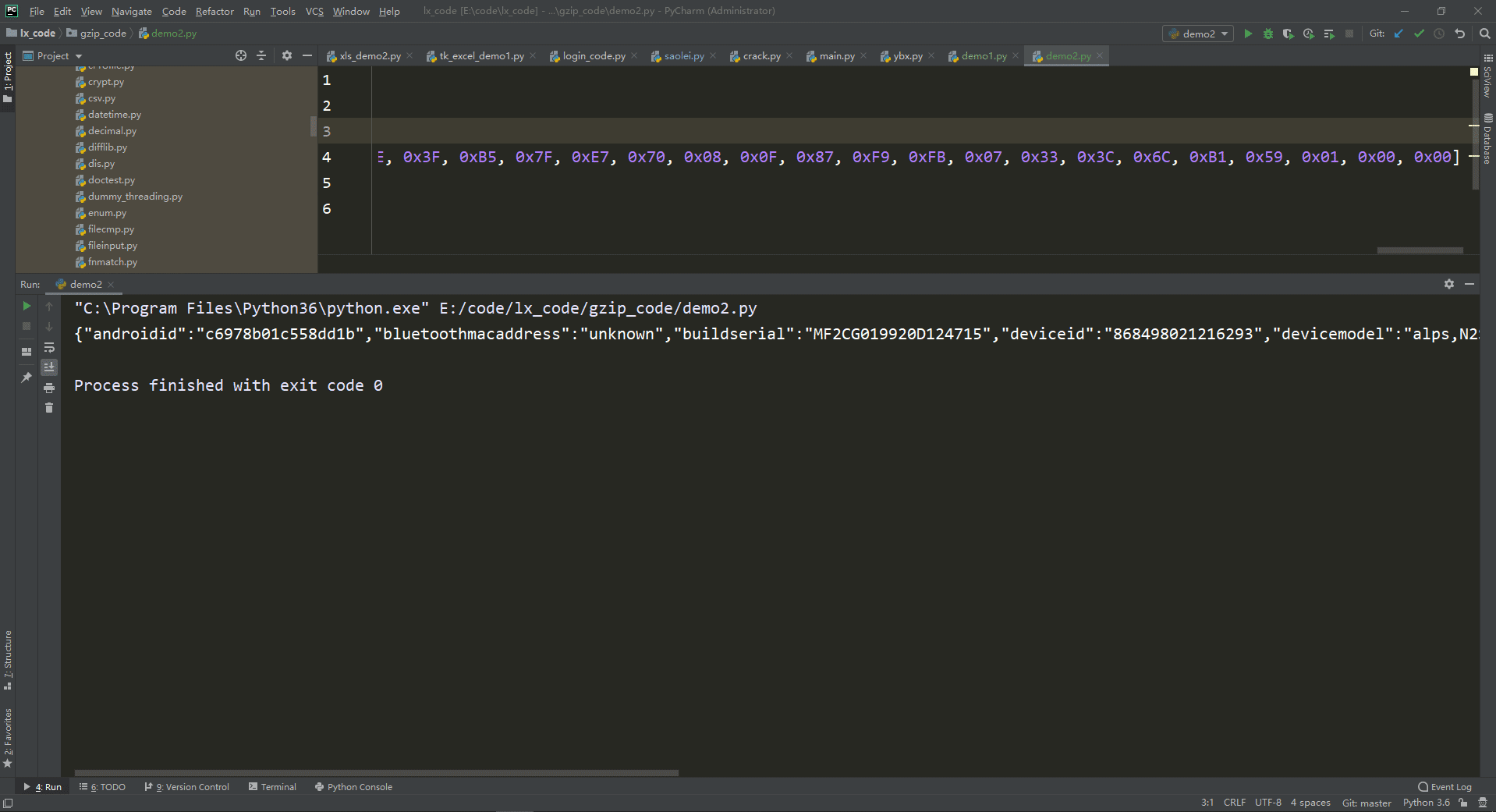
byte[] arrOutput = { 0x1F, 0x8B, 0x08, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x6D, 0x90, 0xC1, 0x6E, 0xC3, 0x20, 0x10, 0x44, 0xFF, 0xC5, 0x67, 0xAB, 0xDA, 0xC5, 0x60, 0xA0, 0xB7, 0xAA, 0x55, 0x7B, 0x6A, 0x2F, 0xFD, 0x02, 0xF0, 0x6E, 0x14, 0x54, 0x03, 0x96, 0xB1, 0x13, 0x45, 0x55, 0xFF, 0xBD, 0x90, 0x48, 0x39, 0xE5, 0xB8, 0xF3, 0x66, 0x66, 0xA5, 0xF9, 0xED, 0x5C, 0xA2, 0x35, 0x07, 0x0A, 0xD4, 0x3D, 0x77, 0xD3, 0x68, 0xB5, 0xF1, 0x80, 0x93, 0x52, 0x86, 0x08, 0x7D, 0xD7, 0x77, 0x7E, 0xDE, 0x79, 0xCB, 0x79, 0x3B, 0x46, 0x37, 0x39, 0xA2, 0x95, 0x4B, 0xA9, 0xC6, 0x3D, 0xFD, 0xA4, 0x7C, 0x4E, 0x8D, 0xEF, 0x61, 0xA6, 0xC2, 0x6B, 0x70, 0x73, 0xD5, 0x3F, 0xDF, 0xC5, 0xEB, 0x07, 0xA0, 0xB5, 0x02, 0xDE, 0x50, 0x48, 0x8D, 0xAA, 0x5A, 0x88, 0x4F, 0x61, 0xE2, 0xEB, 0x03, 0x33, 0x1A, 0x69, 0x0D, 0x08, 0x14, 0x38, 0x0A, 0x3B, 0xDC, 0x61, 0xCC, 0xC4, 0x2D, 0xEF, 0xE6, 0xA5, 0xF4, 0x5F, 0xE2, 0x1B, 0x00, 0x2A, 0x0B, 0x91, 0xC3, 0xC3, 0x50, 0x88, 0xA5, 0x01, 0x39, 0x02, 0x8C, 0x12, 0x24, 0xA2, 0xB2, 0x66, 0x68, 0x89, 0xE5, 0x98, 0x13, 0xA7, 0x3D, 0x7A, 0x5E, 0x2B, 0xAF, 0x42, 0xB9, 0xF5, 0x97, 0x54, 0x4F, 0x71, 0x18, 0x27, 0xEB, 0xC8, 0x22, 0xF8, 0x41, 0x2A, 0x05, 0x16, 0x35, 0x79, 0xE3, 0x85, 0xF6, 0xC8, 0x82, 0xB5, 0x6E, 0xF6, 0x4B, 0xD9, 0x38, 0x6E, 0x97, 0x85, 0xAB, 0xFF, 0xE5, 0xB6, 0xCC, 0x5D, 0x3E, 0xF1, 0x5A, 0x42, 0xBE, 0x36, 0xC9, 0x5E, 0x3F, 0xB5, 0x7F, 0xE7, 0x70, 0x08, 0x0F, 0x87, 0xF9, 0xFB, 0x07, 0x33, 0x3C, 0x6C, 0xB1, 0x59, 0x01, 0x00, 0x00 };
我们把{}前后的代码去掉,然后把这串字符串复制到下面的代码里,运行即可
代码
import gzip hex_list = [0x1F, 0x8B, 0x08, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x6D, 0x90, 0xC1, 0x6E, 0xC3, 0x20, 0x10, 0x44, 0xFF, 0xC5, 0x67, 0xAB, 0xDA, 0xC5, 0x60, 0xA0, 0xB7, 0xAA, 0x55, 0x7B, 0x6A, 0x2F, 0xFD, 0x02, 0xF0, 0x6E, 0x14, 0x54, 0x03, 0x96, 0xB1, 0x13, 0x45, 0x55, 0xFF, 0xBD, 0x90, 0x48, 0x39, 0xE5, 0xB8, 0xF3, 0x66, 0x66, 0xA5, 0xF9, 0xED, 0x5C, 0xA2, 0x35, 0x07, 0x0A, 0xD4, 0x3D, 0x77, 0xD3, 0x68, 0xB5, 0xF1, 0x80, 0x93, 0x52, 0x86, 0x08, 0x7D, 0xD7, 0x77, 0x7E, 0xDE, 0x79, 0xCB, 0x79, 0x3B, 0x46, 0x37, 0x39, 0xA2, 0x95, 0x4B, 0xA9, 0xC6, 0x3D, 0xFD, 0xA4, 0x7C, 0x4E, 0x8D, 0xEF, 0x61, 0xA6, 0xC2, 0x6B, 0x70, 0x73, 0xD5, 0x3F, 0xDF, 0xC5, 0xEB, 0x07, 0xA0, 0xB5, 0x02, 0xDE, 0x50, 0x48, 0x8D, 0xAA, 0x5A, 0x88, 0x4F, 0x61, 0xE2, 0xEB, 0x03, 0x33, 0x1A, 0x69, 0x0D, 0x08, 0x14, 0x38, 0x0A, 0x3B, 0xDC, 0x61, 0xCC, 0xC4, 0x2D, 0xEF, 0xE6, 0xA5, 0xF4, 0x5F, 0xE2, 0x1B, 0x00, 0x2A, 0x0B, 0x91, 0xC3, 0xC3, 0x50, 0x88, 0xA5, 0x01, 0x39, 0x02, 0x8C, 0x12, 0x24, 0xA2, 0xB2, 0x66, 0x68, 0x89, 0xE5, 0x98, 0x13, 0xA7, 0x3D, 0x7A, 0x5E, 0x2B, 0xAF, 0x42, 0xB9, 0xF5, 0x97, 0x54, 0x4F, 0x71, 0x18, 0x27, 0xEB, 0xC8, 0x22, 0xF8, 0x41, 0x2A, 0x05, 0x16, 0x35, 0x79, 0xE3, 0x85, 0xF6, 0xC8, 0x82, 0xB5, 0x6E, 0xF6, 0x4B, 0xD9, 0x38, 0x6E, 0x97, 0x85, 0xAB, 0xFF, 0xE5, 0xB6, 0xCC, 0x5D, 0x3E, 0xF1, 0x5A, 0x42, 0xBE, 0x36, 0xC9, 0x5E, 0x3F, 0xB5, 0x7F, 0xE7, 0x70, 0x08, 0x0F, 0x87, 0xF9, 0xFB, 0x07, 0x33, 0x3C, 0x6C, 0xB1, 0x59, 0x01, 0x00, 0x00] b_bytes = bytes(hex_list) print(gzip.decompress(b_bytes).decode())