minemeld在微软sentinel上的使用(一个订阅情报示例):

What is MineMeld?
An extensible Threat Intelligence processing framework brought to you by Palo Alto Networks.
What is MineMeld for?
MineMeld is a community supported tool to manipulate list of indicators and transform/aggregate them for consumption by third party enforcement infrastructure. MineMeld has many use-cases and can easily be extended to fulfill many more. Here are a few examples:
- Connect to the Spamhaus DROP feed and transform it for enforcement by Palo Alto Networks EDL (External Dynamic List) objects
- Mine Office 365 IP addresses provided by Microsoft and dynamically create an EDL list for usage in a Palo Alto Networks security policy to further restrict trafic
- Aggregate CERTs and ISACs Threat Intelligence feeds, removing duplicates, expiring entries and consolidating attack directions and confidence levels then make this list available for enforcement by third party tools
- Extract indicators from syslog messages and aggregate them with indicators coming from 3rd party sources
Check this page for a brief list of currently supported nodes/feeds.
MineMeld Threat Intelligence Sharing

In order to prevent successful cyberattacks, many organizations collect indicators of compromise (IOCs) from various threat intelligence providers with the intent of creating new controls for their security devices. Unfortunately, legacy approaches to aggregation and enforcement are highly manual in nature, often creating complex workflows and extending the time needed to identify and validate which IOCs should be blocked.
Now security organizations can leverage MineMeld, an open-source application that streamlines the aggregation, enforcement and sharing of threat intelligence. MineMeld is available for all users directly on GitHub, as well as pre-built virtual machines (VMs) for easy deployment. With an extensible modular architecture, anyone can add to the MineMeld functionality by contributing code to the open-source repository.
MineMeld use cases
MineMeld supports a variety of use cases, with more being added each day by the community, including:
- Aggregation and correlation of threat intelligence feeds
- Enforcement of new prevention controls, including IP blacklists.
- Evaluate the value of a specific threat intelligence feed for your environment.
- Extract indicators from Palo Alto Networks device logs and share them with other security tools.
- Share indicators with trusted peers.
- Identify incoming sessions from Tor exit nodes for blocking or strict inspection.
- Track Office365 URLs and IPs
Aggregate and correlate threat intelligence feeds
MineMeld allows you to aggregate threat intelligence across public, private and commercial intelligence sources, including between government and commercial organizations.
MineMeld simplifies the collection and correlation of intelligence across:
- Commercial threat intelligence feeds
- Open-source intelligence (OSINT) providers
- Threat intelligence platforms
- ISACs
- CERTs
- Other MineMeld users
Once indicators are collected, MineMeld can filter, unduplicate and consolidate metadata across all sources, allowing security teams to analyze a more actionable set of data, enriched from multiple sources, for easier enforcement.
Automated enforcement of prevention-based controls
MineMeld natively integrates with Palo Alto Networks security platforms to automatically create new prevention-based controls for URLs, IPs and domain intelligence derived from all sources feeding into the tool. Now, organizations can simplify their workflows for blocking IOCs with External Dynamic Lists and Dynamic Address Groups, without spending additional resources to manage block lists, including the automated timeout of expired indicators. MineMeld further integrates with the Palo Alto Networks AutoFocus™ contextual threat intelligence service, allowing you to identify high-value, targeted indicators – in AutoFocus – and block them on your next-generation firewall with export lists and MineMeld.
Threat-intelligence-sharing ecosystem
Palo Alto Networks has partnered with other leading organizations to create a threat-intelligence-sharing ecosystem with native MineMeld support built in from the start. Additionally, the open-source availability inherent in MineMeld allows other providers to easily add integration with their offerings by building a new Miner.
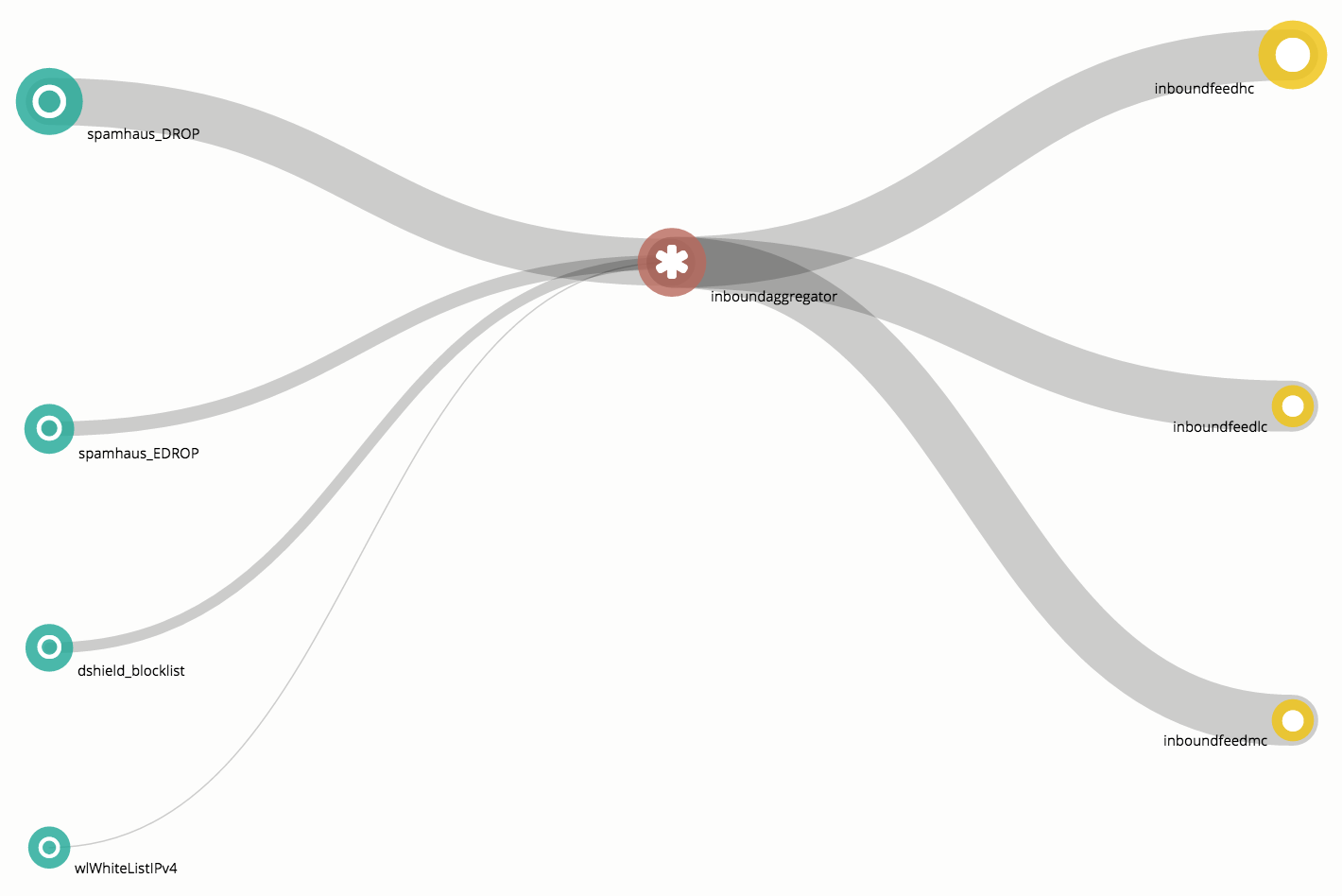
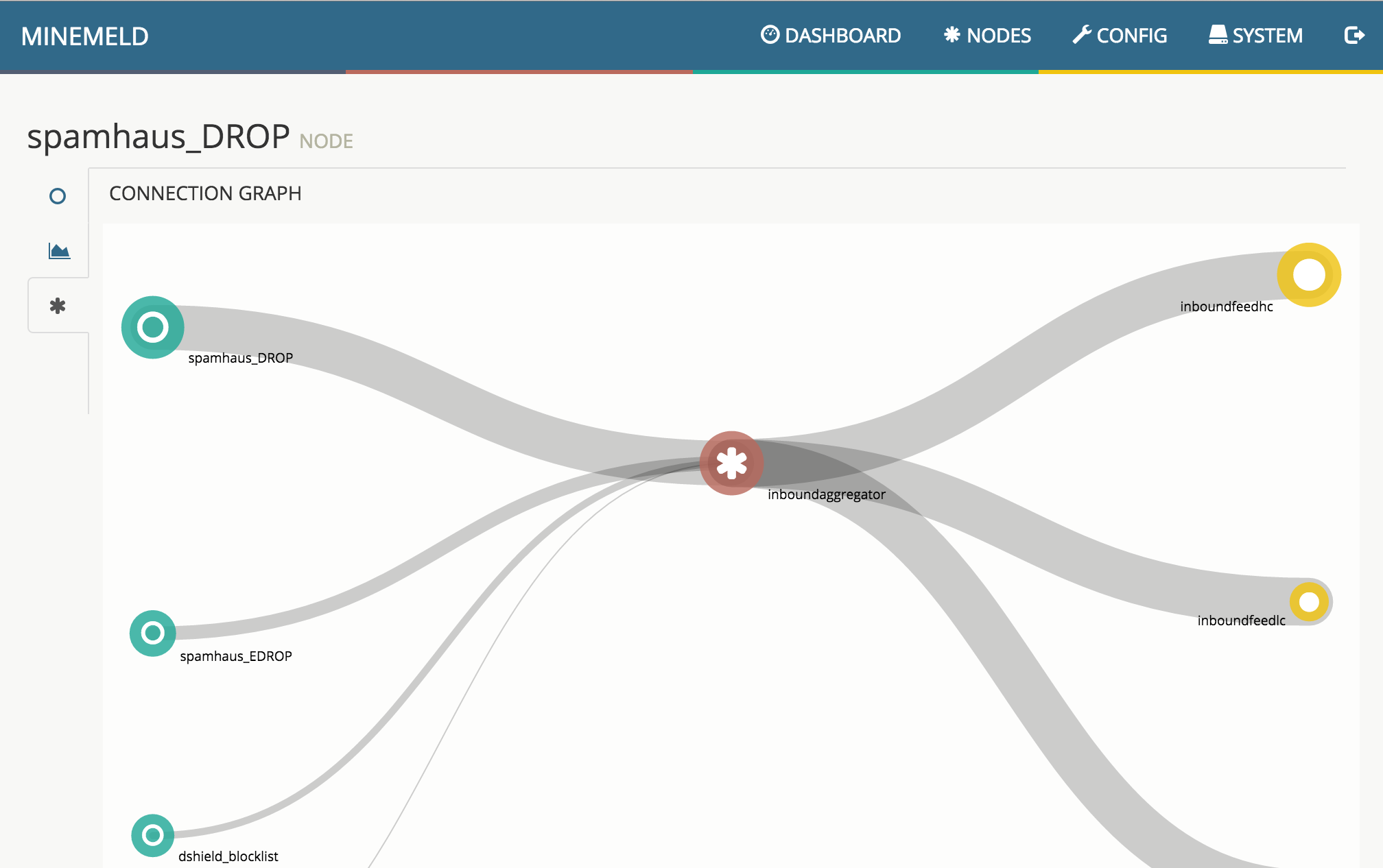
The default config installed by the MineMeld loader is really simple, and can be seen in the following graph.
The 3 green nodes on the left are called Miners and are responsible for periodically retrieving indicators from 3 different feeds and push them downstream to the connected nodes using update messages. Miners are also responsible for aging out indicators: when indicators disappear from the original feed or when an indicator is considered dead, the corresponding Miner instructs the downstream nodes of removing the indicator via a withdraw message.
The central red node is a Processor node. In this specific configuration, the processor node is an IPv4 aggregator node and aggregates IPv4 indicators received from the 3 Miners and sends downstream the aggregated indicators.
The 3 yellow nodes on the right are Output nodes. These nodes receive indicators from the processor nodes and transform them into a format that could be directly consumed by external entities. In the default config the 3 output nodes translates the indicators received from the aggregator node into a format that can be consumed using the PAN-OS Dynamic Block List feature. All 3 output nodes in this graph receive the same set of indicators from the aggregator node, but each of them stores a different subset of these indicators based on the configured input filters. inboundfeedhc accepts only indicators with confidence level > 75, inboundfeedmc only indicators with confidence level < 75 and > 50, inboundfeedlc indicators with confidence level < 50. These subset of indicators are stored into 3 different DBLs that can be used in different ways inside the PAN-OS configuration.
1. Login
Default credentials are admin / minemeld
2. Dashboard
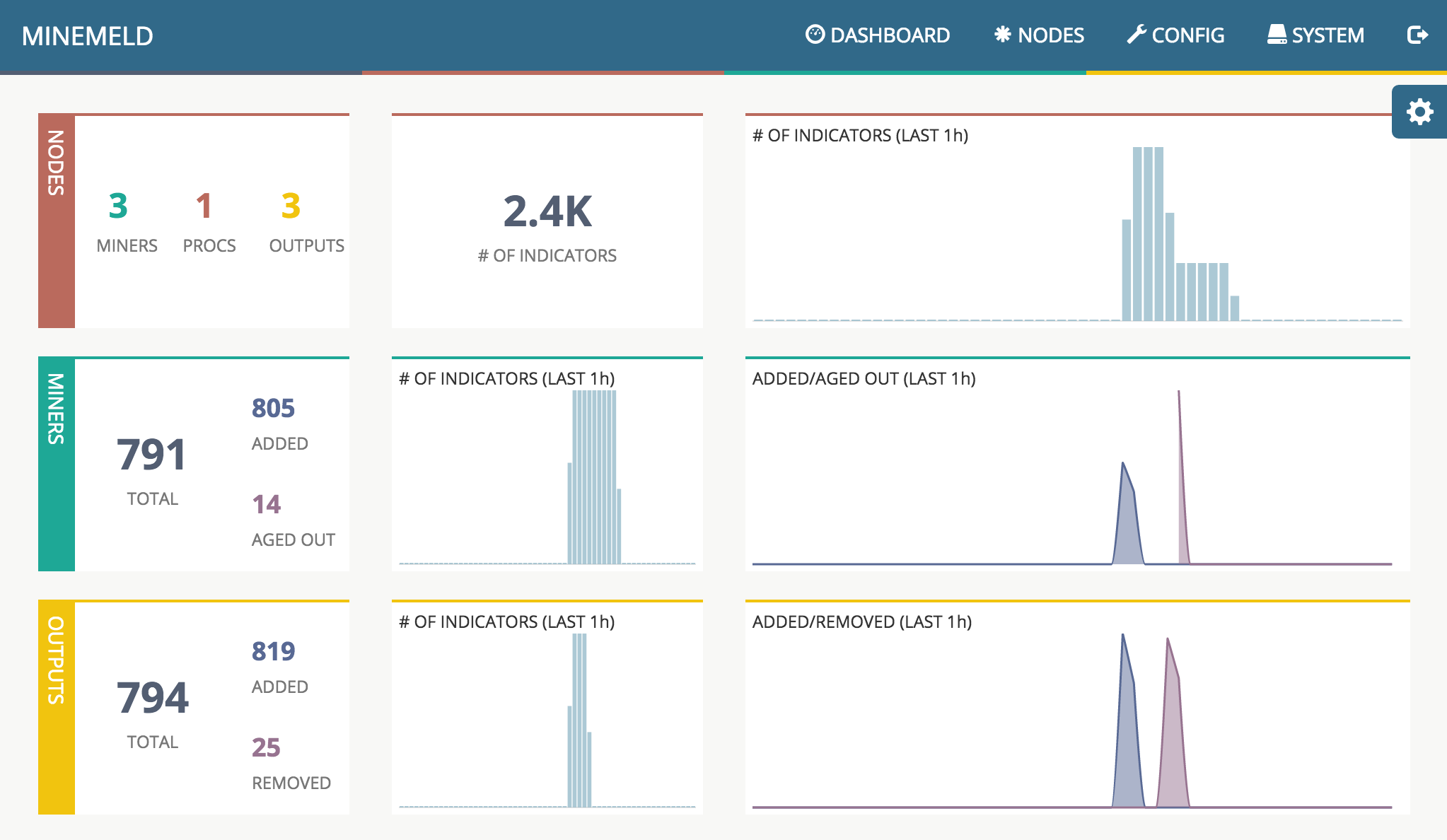
The dashboard page can be used to check the overall status of the MineMeld processing engine.
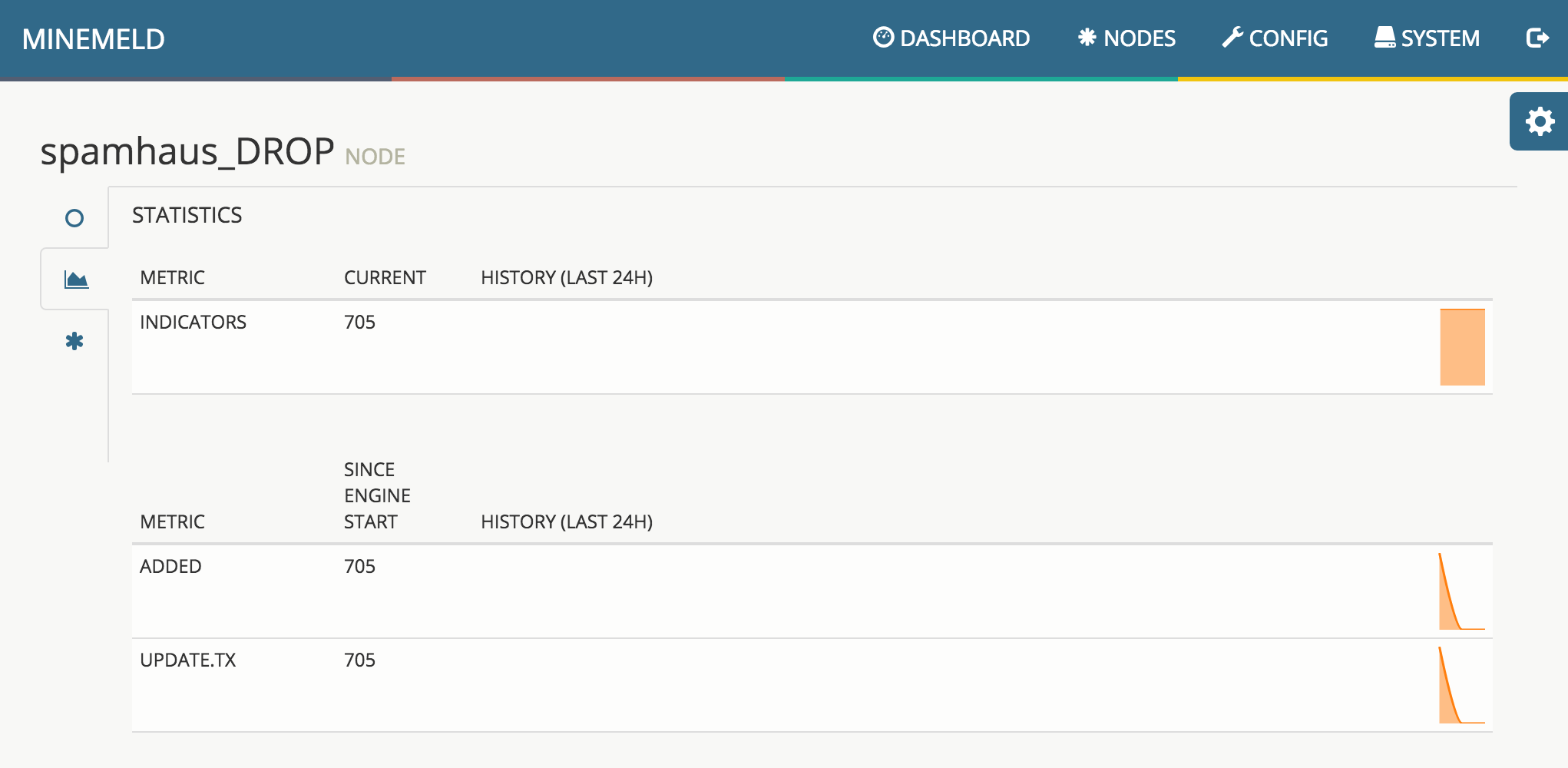
In the first row you can find the number of active nodes per type, the current total number of indicators stored inside the graph and an historical chart of the total number of indicators. The second row is dedicated to Miners, the first panel reports the total number of indicators stored in the miner nodes, and the number of indicators that have been added and aged out since engine start. The historical chart on the right represents the number of indicators added and aged out by the miner nodes in the last period of time. The third row reports the same statistics of the second row but related to Outputs.
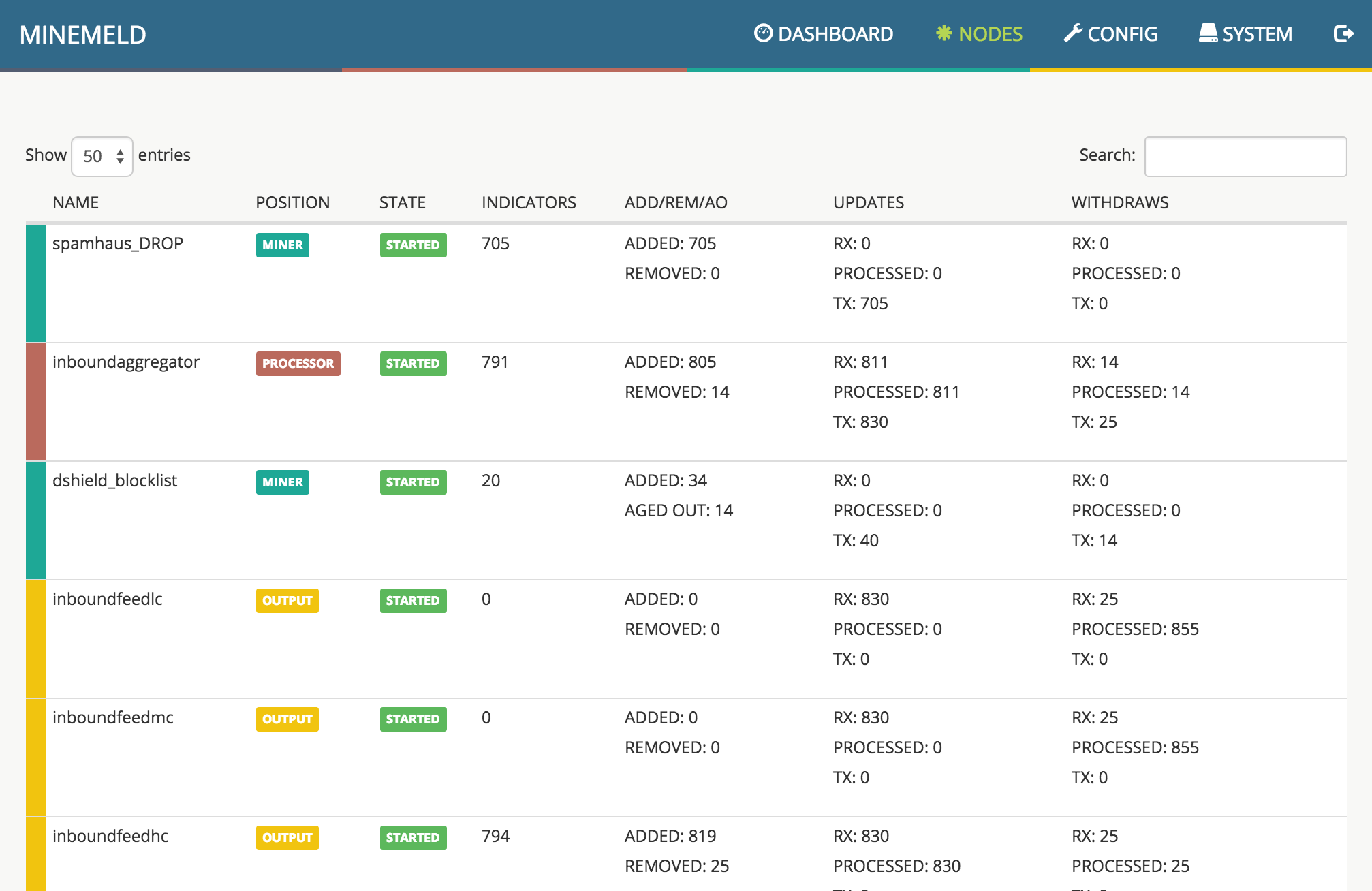
3. Nodes
The nodes view reports the status of every single active node of the graph.
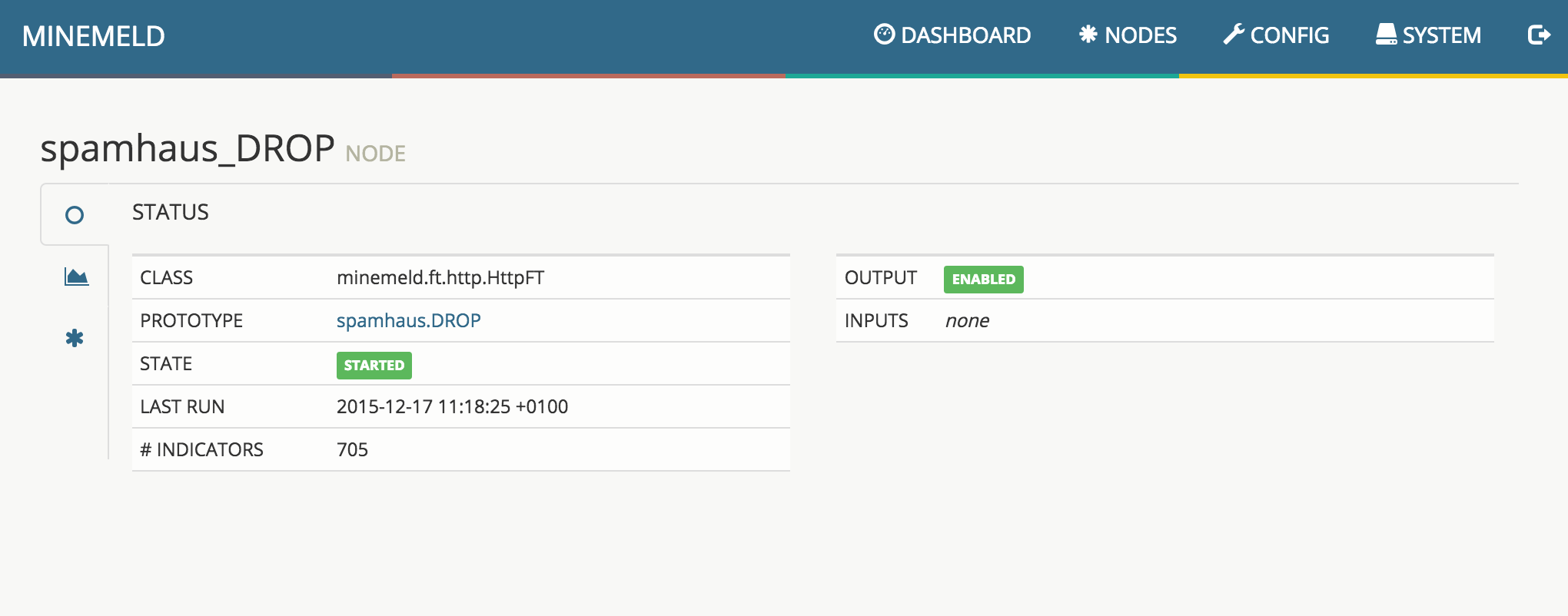
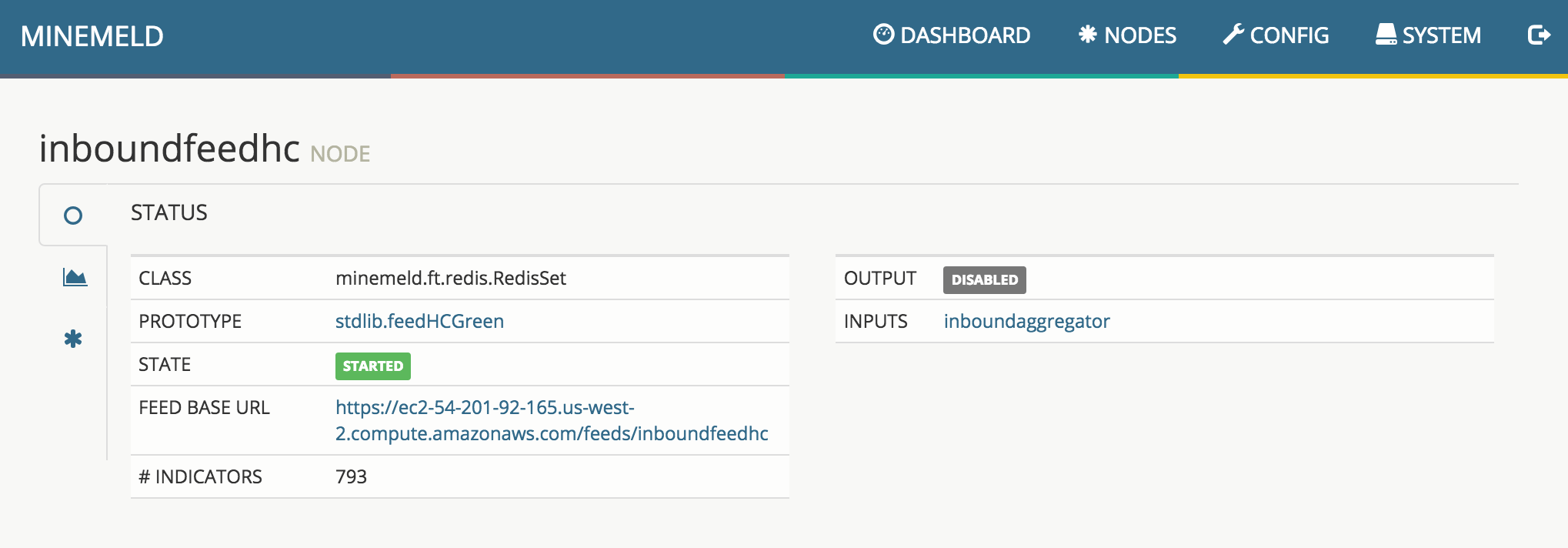
4. Node status
Clicking on a node in the Nodes view shows the details of the configuration of the node
the historical charts of the metrics of the node
and the connected graph where the node lives
5. Nodes and prototypes
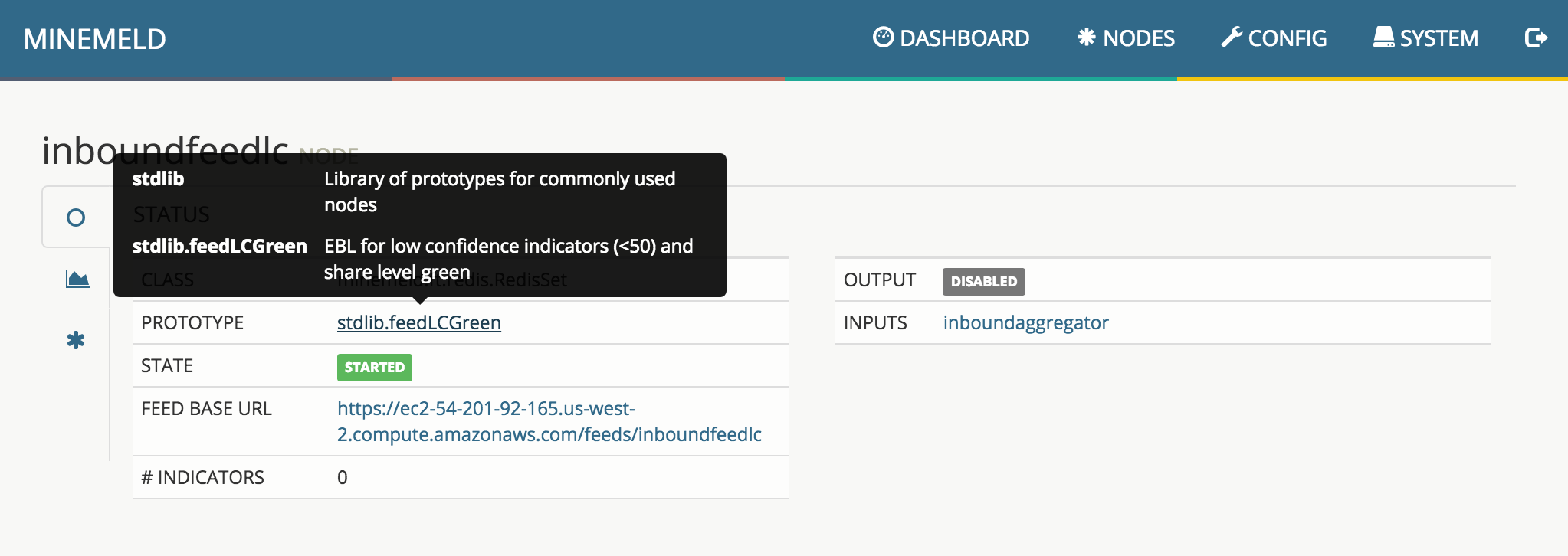
Nodes are created using libraries of prototypes. Each prototype defines the type of node and its configuration.
To check the details of a prototype, just click on a node in the Nodes view and move the pointer over the prototype field
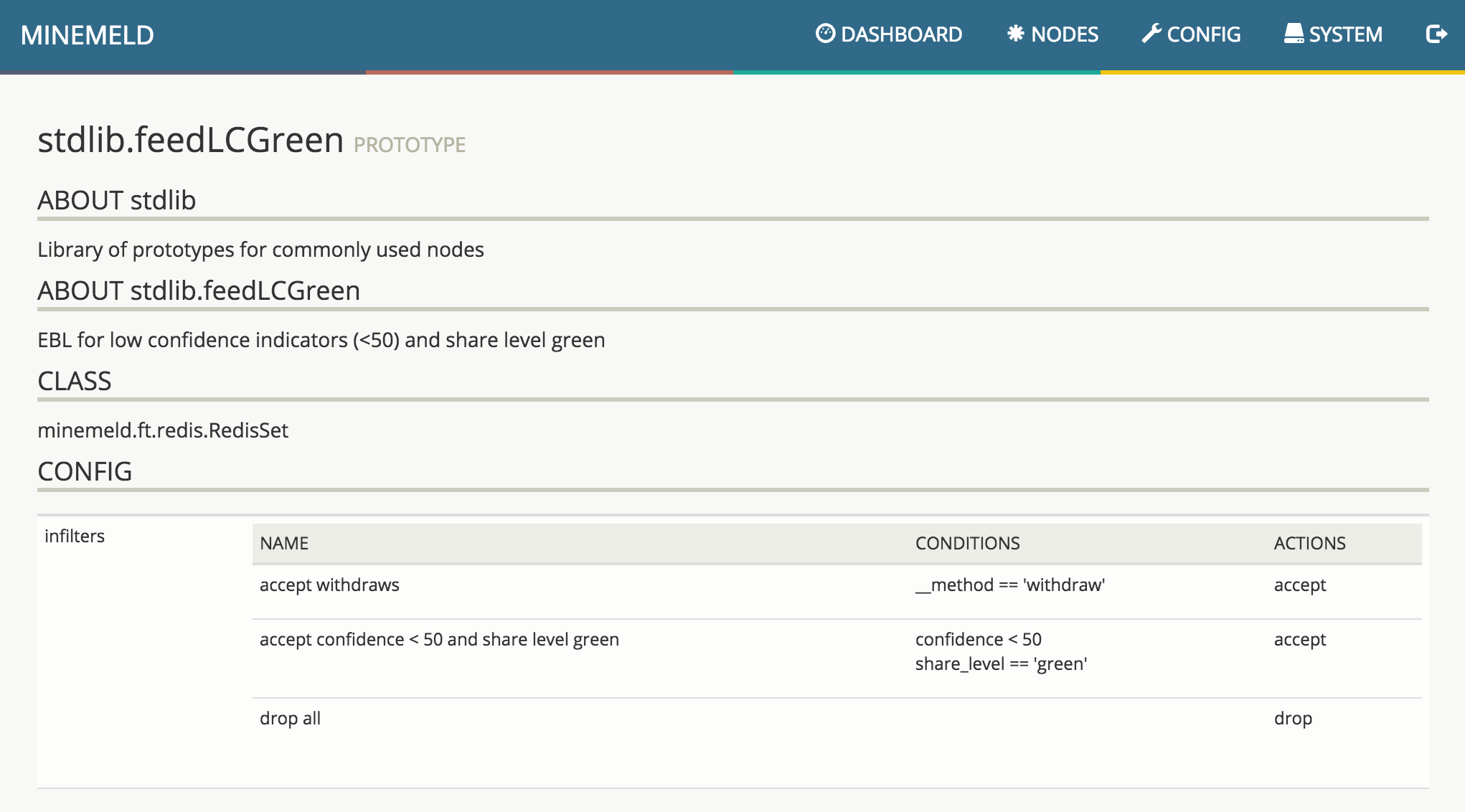
Clicking on the prototype name shows all the details about that prototype
6. PAN-OS External Dynamic Lists
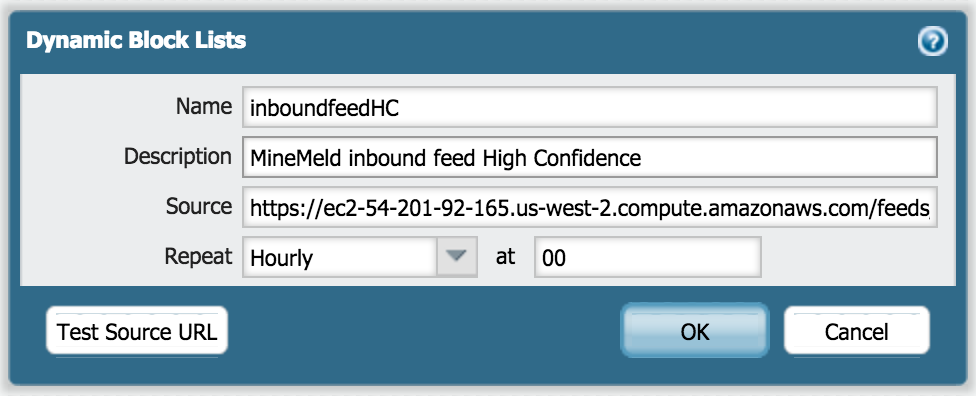
To use MineMeld feeds with PAN-OS External Dynamic Lists (named Dynamic Block Lists before PAN-OS 7.1), select the output node responsible for the feed in the Nodes view and copy the FEED BASE URL
In PAN-OS, under Object > External Dyanmic Lists (or Object > Dynamic Block Lists in PAN-OS before 7.1) define a new list using the output node URL
7. Whitelist indicators
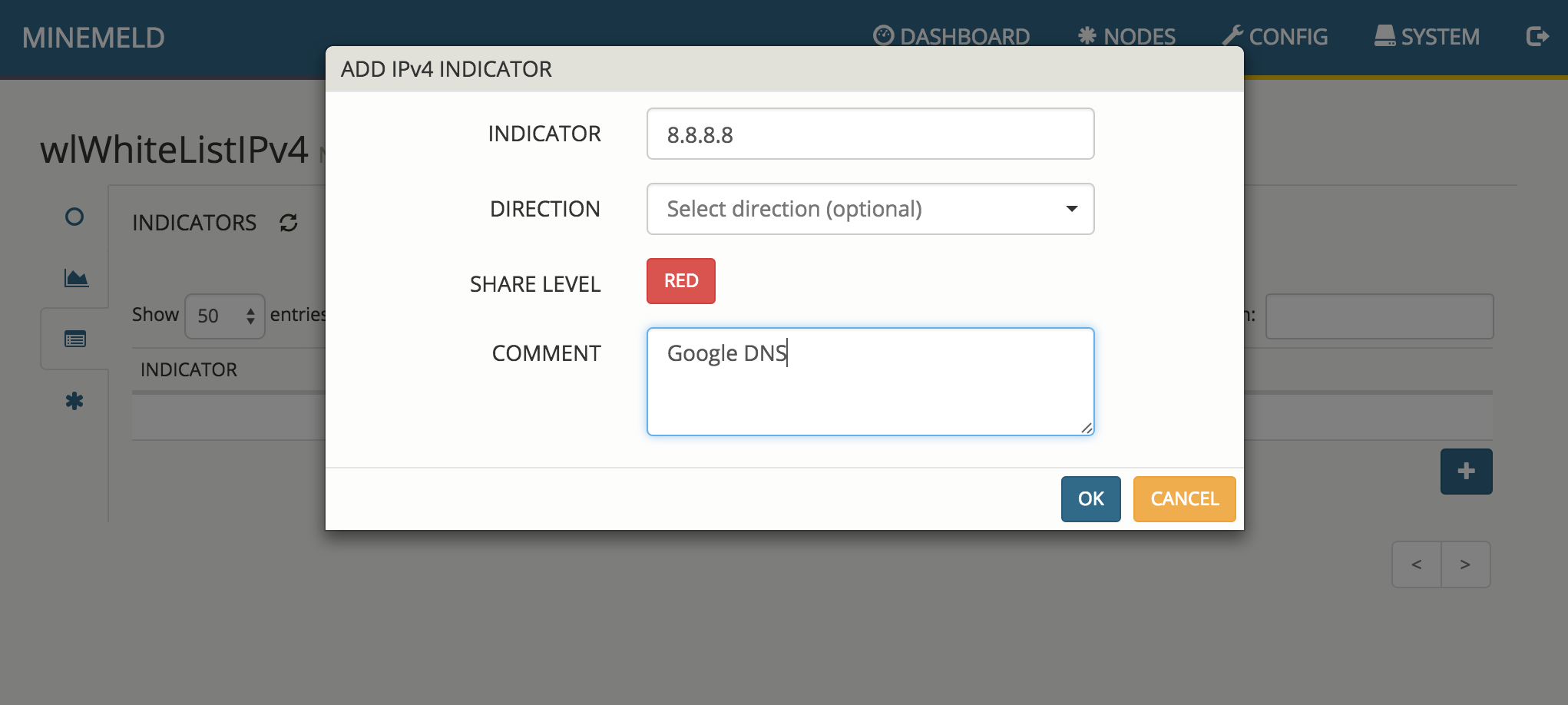
To whitelist a network, range or a single IPv4 address, click on wlWhiteListIPv4 under Nodes and select the INDICATORS option on the left. This list of indicators is treated as a whitelist by the aggregator.
To add a new indicator click on + and specify the IPv4 indicator. Changes will be automatically saved by pressing OK.