此题的关键在于给你的位置的分布, 可以发现是交错的,那么就可以用二分图了。
National Treasures
Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 32768/32768 K (Java/Others)
Total Submission(s): 854 Accepted Submission(s): 281
Problem Description
The great hall of the national museum has been robbed few times recently. Everyone is now worried about the security of the treasures on display. To help secure the hall, the museum contracted with a private security company to provide additional guards to stay in the great hall and keep an eye on the ancient artifacts. The museum would like to hire the minimum number of additional guards so that the great hall is secured.
The great hall is represented as a two dimensional grid of R × C cells. Some cells are already occupied with the museum’s guards. All remaining cells are occupied by artifacts of different types (statues, sculptures, . . . etc.) which can be replaced by new hired guards. For each artifact, few other cells in the hall are identified as critical points of the artifact depending on the artifact value, type of vault it is kept inside, and few other factors. In other words, if this artifact is going to stay in the hall then all of its critical points must have guards standing on them. A guard standing in a critical position of multiple artifacts can keep an eye on them all. A guard, however,
can not stand in a cell which contains an artifact (instead, you may remove the artifact to allow the guard to stay there). Also you can not remove an artifact and leave the space free (you can only replace an artifact with a new hired guard).
Surveying all the artifacts in the great hall you figured out that the critical points of any artifact (marked by a ) are always a subset of the 12 neighboring cells as shown in the grid below.
) are always a subset of the 12 neighboring cells as shown in the grid below.
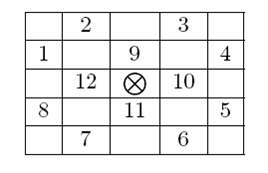
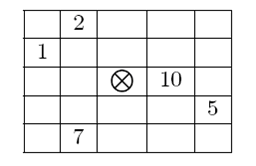
Accordingly, the type of an artifact can be specified as a non-negative integer where the i-th bit is 1 only if critical point number i from the picture above is a critical point of that artifact. For example an artifact of type 595 (in binary 1001010011) can be pictured as shown in the figure below. Note that bits are numbered from right to left (the right-most bit is bit number 1.) If a critical point of an artifact lies outside the hall grid then it is considered secure.
You are given the layout of the great hall and are asked to find the minimum number of additional guards to hire such that all remaining artifacts are secured.
The great hall is represented as a two dimensional grid of R × C cells. Some cells are already occupied with the museum’s guards. All remaining cells are occupied by artifacts of different types (statues, sculptures, . . . etc.) which can be replaced by new hired guards. For each artifact, few other cells in the hall are identified as critical points of the artifact depending on the artifact value, type of vault it is kept inside, and few other factors. In other words, if this artifact is going to stay in the hall then all of its critical points must have guards standing on them. A guard standing in a critical position of multiple artifacts can keep an eye on them all. A guard, however,
can not stand in a cell which contains an artifact (instead, you may remove the artifact to allow the guard to stay there). Also you can not remove an artifact and leave the space free (you can only replace an artifact with a new hired guard).
Surveying all the artifacts in the great hall you figured out that the critical points of any artifact (marked by a
 ) are always a subset of the 12 neighboring cells as shown in the grid below.
) are always a subset of the 12 neighboring cells as shown in the grid below.
Accordingly, the type of an artifact can be specified as a non-negative integer where the i-th bit is 1 only if critical point number i from the picture above is a critical point of that artifact. For example an artifact of type 595 (in binary 1001010011) can be pictured as shown in the figure below. Note that bits are numbered from right to left (the right-most bit is bit number 1.) If a critical point of an artifact lies outside the hall grid then it is considered secure.

You are given the layout of the great hall and are asked to find the minimum number of additional guards to hire such that all remaining artifacts are secured.
Input
Your program will be tested on one or more test cases. Each test case is specified using R+1 lines.
The first line specifies two integers (1<= R,C <= 50) which are the dimensions of the museum hall. The next R lines contain C integers separated by one or more spaces. The j-th integer of the i-th row is -1 if cell (i, j) already contains one of the museum’s guards, otherwise it contains an integer (0 <= T <= 212) representing the type of the artifact in that cell.
The last line of the input file has two zeros.
The first line specifies two integers (1<= R,C <= 50) which are the dimensions of the museum hall. The next R lines contain C integers separated by one or more spaces. The j-th integer of the i-th row is -1 if cell (i, j) already contains one of the museum’s guards, otherwise it contains an integer (0 <= T <= 212) representing the type of the artifact in that cell.
The last line of the input file has two zeros.
Output
For each test case, print the following line:
k. G
Where k is the test case number (starting at one,) and G is the minimum number of additional guards to hire such that all remaining artifacts are secured.
k. G
Where k is the test case number (starting at one,) and G is the minimum number of additional guards to hire such that all remaining artifacts are secured.
Sample Input
1 3
512 -1 2048
2 3
512 2560 2048
512 2560 2048
0 0
Sample Output
1. 0
2. 2
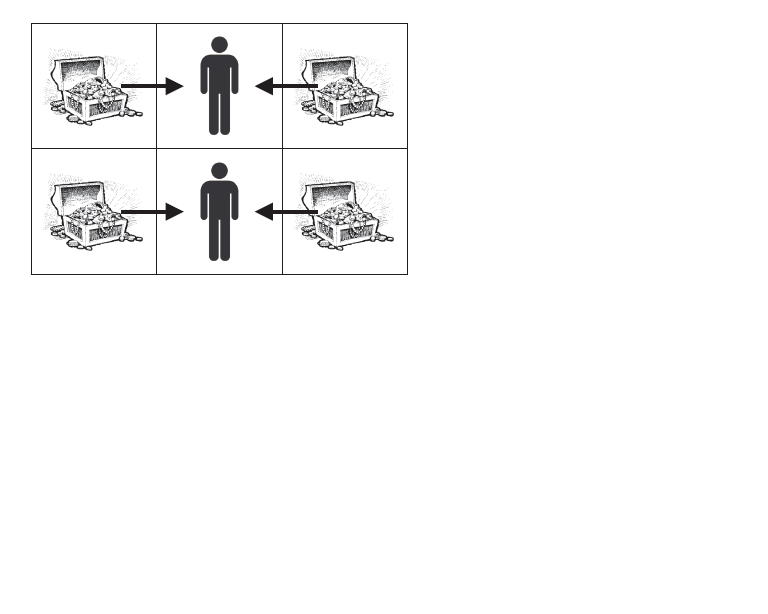
Hint
The picture below shows the solution of the second test case where the two artifacts in the middle are replaced by guards.

Source
Recommend
lcy
#include <stdio.h> #include <string.h> #include <iostream> using namespace std; #define N 2505 #define M 2500*50 struct node { int to,next; }edge[M]; int map[5][5]={ {0,2,0,3,0},{1,0,9,0,4},{0,12,0,10,0},{8,0,11,0,5},{0,7,0,6,0} }; int n,m; int save[55][55]; int g[55][55],g1[55][55]; int cnt,pre[N],frt[N],mark[N]; int ver[N],ver1[N]; int vcnt,vcnt1; void init() { vcnt=0; vcnt1=0; cnt=0; memset(pre,-1,sizeof(pre)); int tmp=0; for(int i=1;i<=m;i++) { save[1][i]=tmp; tmp^=1; } for(int i=2;i<=n;i++) { for(int j=1;j<=m;j++) save[i][j]=save[i-1][j]^1; } } void add_edge(int u,int v) { edge[cnt].to=v; edge[cnt].next=pre[u]; pre[u]=cnt++; } void link(int x,int y,int w) { int tmp,id=0; int tx,ty; int flag; while(w) { tmp = w&1; w = w>>1; id++; if(tmp==0) continue; flag=0; for(int i=0;i<5;i++) { for(int j=0;j<5;j++) { if(map[i][j] == id) { tx=x+i-2; ty=y+j-2; flag=1; break; } if(flag) break; } if(flag) break; } if((tx>=1&&tx<=n)&&(ty>=1&&ty<=m)) { if( g[tx][ty]==-1 ) continue; add_edge(g1[x][y],g1[tx][ty]); add_edge(g1[tx][ty],g1[x][y]); } } } int dfs(int s) { int v; for(int p=pre[s];p!=-1;p=edge[p].next) { v=edge[p].to; if(mark[v]==1) continue; mark[v]=1; if(frt[v]==-1||dfs(frt[v])==1) { frt[v]=s; return 1; } } return 0; } int main() { int tt=1; while(scanf("%d%d",&n,&m)&&(n+m)) { init(); for(int i=1;i<=n;i++) for(int j=1;j<=m;j++) { scanf("%d",&g[i][j]); } int id=0; for(int i=1;i<=n;i++) for(int j=1;j<=m;j++) { if( g[i][j] == -1 ) continue; id++; g1[i][j] = id; if(save[i][j]==0) { ver[++vcnt]=id; } else { ver1[++vcnt1]=id; } } for(int i=1;i<=n;i++) { for(int j=1;j<=m;j++) { if(g[i][j]==-1) continue; link(i,j,g[i][j]); } } int sum=0; memset(frt,-1,sizeof(frt)); for(int i=1;i<=vcnt;i++) { memset(mark,0,sizeof(mark)); sum += dfs(ver[i]); } printf("%d. ",tt++); printf("%d\n",sum); } return 0; }