Finding:
Thread 119:1f7c
Exception Code 0xE06D7363
This exception code will be used for any error that is raised by the Microsoft Visual C++ compiler through a call to "throw
From https://support.microsoft.com/en-us/help/313109/how-to-find-the-problem-exception-stack-when-you-receive-an-unhandlede Step by step
0:119> dd 0x3e43abbc
3e43abbc 3e43acbc 3e43acdc 77051288 00000001
3e43abcc 0008e883 3e43abf4 770471b9 fffffffe
3e43abdc 3e43ffc4 3e43acdc 3e43ac90 3e43b208
3e43abec 770471cd 3e43ffc4 3e43aca4 7704718b
3e43abfc 3e43acbc 3e43ffc4 3e43acdc 3e43ac90
3e43ac0c 7701e0ed 00000000 3e43acbc 3e43ffc4
3e43ac1c 7701f96f 3e43acbc 3e43ffc4 3e43acdc
3e43ac2c 3e43ac90 7701e0ed 3e43b1b8 3e43acbc
0:119> dd 3e43acbc
3e43acbc e06d7363 00000001 00000000 752bd36f
3e43accc 00000003 19930520 3e43b1d4 7c047f0c
3e43acdc 0001007f 00000000 00000000 00000000
3e43acec 00000000 00000000 00000000 0000027f
3e43acfc 00000129 0000ffff 1020961b 00000000
3e43ad0c 3e43b1f0 00000000 00000000 00000000
3e43ad1c 0000ffff 00000000 ffff0000 00000000
3e43ad2c c0000000 0000ffff 00000000 ffffc000
0:119> u 752bd36f
Loading symbols for 752b0000 KERNELBASE.dll -> KERNELBASE.dll
*** ERROR: Symbol file could not be found. Defaulted to export symbols for KERNELBASE.dll -
KERNELBASE!RaiseException+0x54:
752bd36f c9 leave
752bd370 c21000 ret 10h
752bd373 8945c0 mov dword ptr [ebp-40h],eax
752bd376 ebed jmp KERNELBASE!RaiseException+0x4a (752bd365)
752bd378 90 nop
752bd379 90 nop
752bd37a 90 nop
752bd37b 90 nop
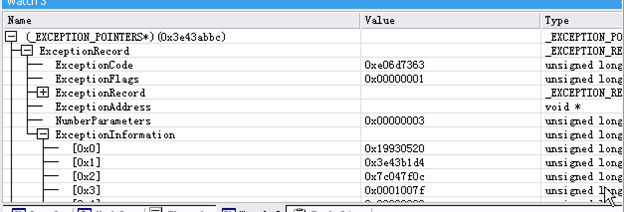
0:119> .exr 3e43acbc
ExceptionAddress: 752bd36f (KERNELBASE!RaiseException+0x00000054)
ExceptionCode: e06d7363 (C++ EH exception)
ExceptionFlags: 00000001
NumberParameters: 3
Parameter[0]: 19930520
Parameter[1]: 3e43b1d4
Parameter[2]: 7c047f0c
pExceptionObject: 3e43b1d4
_s_ThrowInfo : 7c047f0c
Type : class __non_rtti_object
Type : class bad_typeid
Type : class exception
0:119> .cxr 3e43acdc
eax=3e43b128 ebx=3e43b208 ecx=00000003 edx=00000000 esi=7c03fdb4 edi=3e43b1b8
eip=752bd36f esp=3e43b128 ebp=3e43b178 iopl=0 nv up ei pl nz ac pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000216
KERNELBASE!RaiseException+0x54:
752bd36f c9 leave
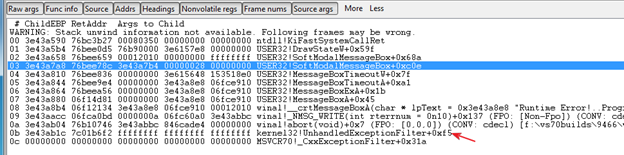
0:119> kpn*** Stack trace for last set context - .thread/.cxr resets it
# ChildEBP RetAddr
WARNING: Stack unwind information not available. Following frames may be wrong.
00 3e43b178 7c01ba05 KERNELBASE!RaiseException+0x54
01 3e43b1b8 7c01c20e MSVCR70!CxxThrowException+0x34
02 3e43b218 052ab837 MSVCR70!_RTDynamicCast+0xdf
03 3e43b230 04f18340 xxx!xxxshort wChID = 26679, unsigned long * pulStationID = 0x0f004c38, unsigned long * pulModuleID = 0x00000000)+0x27 [xxxi.c @ 76]----