A file upload is a great opportunity to XSS an application. User restricted area with an uploaded profile picture is everywhere, providing more chances to find a developer’s mistake. If it happens to be a self XSS, just take a look at the previous post.
Basically we have the following entry points for an attack.
1) Filename
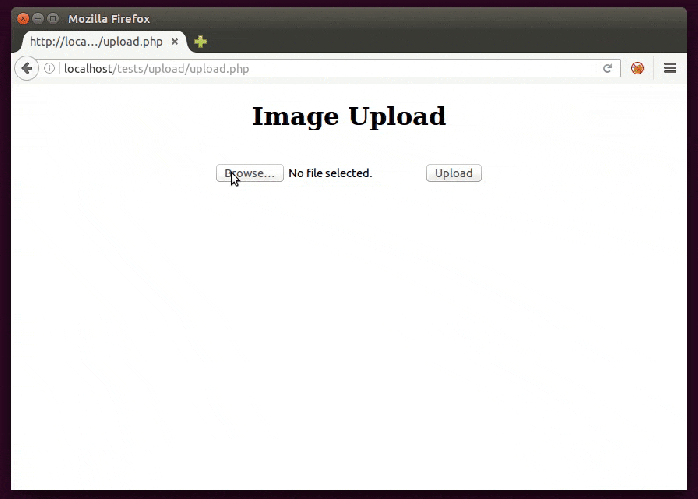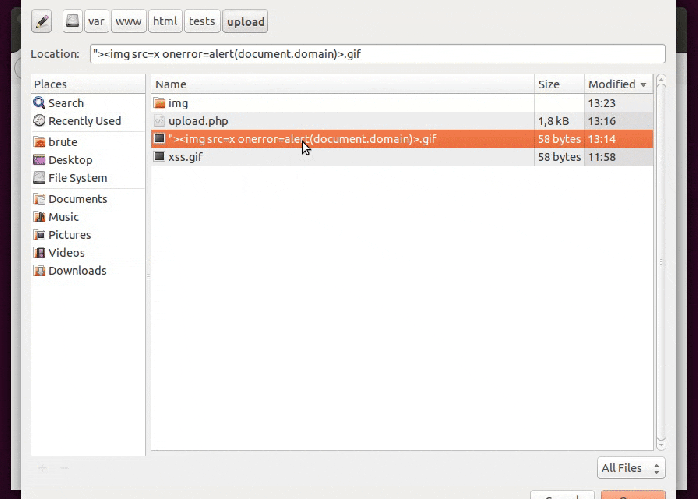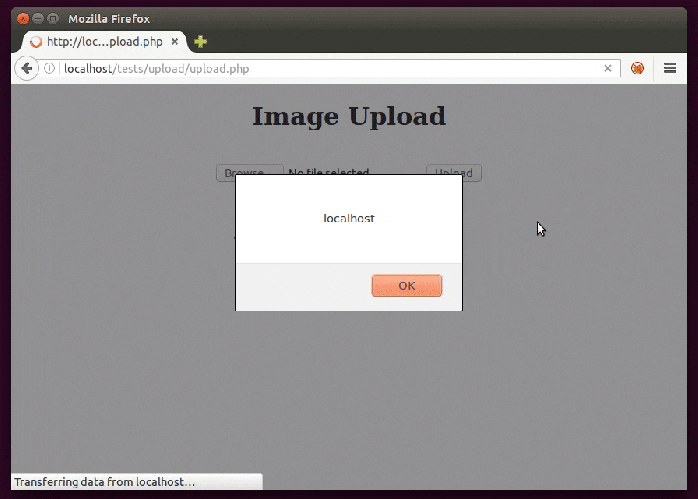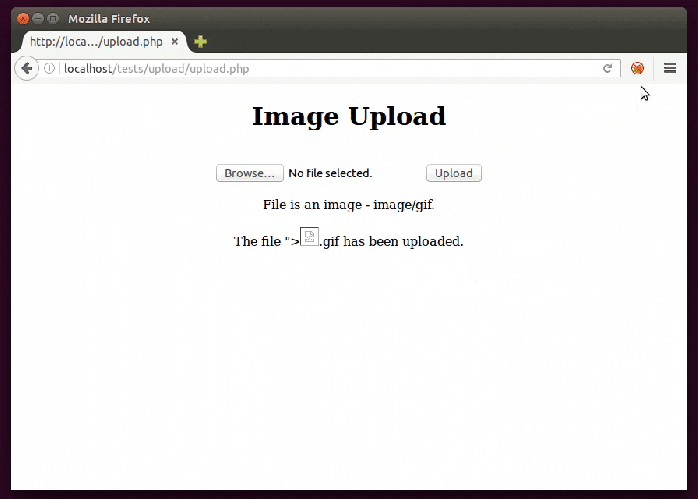
The filename itself may be being reflected in the page so it’s just a matter of naming the file with a XSS.
Although not intended, it’s possible to practice this XSS live at W3Schools.
2) Metadata
Using the exiftool it’s possible to alter EXIF metadata which may lead to a reflection somewhere:
$ exiftool -FIELD=XSS FILE
Example:
$ exiftool -Artist=’ “><img src=1 οnerrοr=alert(document.domain)>’ brute.jpeg

3) Content
If the application allows the upload of a SVG file extension (which is also an image type), a file with the following content can be used to trigger a XSS:
<svg xmlns="http://www.w3.org/2000/svg" onload="alert(document.domain)"/>
A PoC (Proof of Concept) is available live at brutelogic.com.br/poc.svg.
4) Source
It’s easy to build a GIF image to carry a javascript payload for use as a source of a script. This is useful to bypass the CSP (Content Security Policy) protection “script-src ‘self’ ” (which doesn’t allow <script>alert(1)</script>, for example) if we are able to successfully inject in the same domain, as shown below.
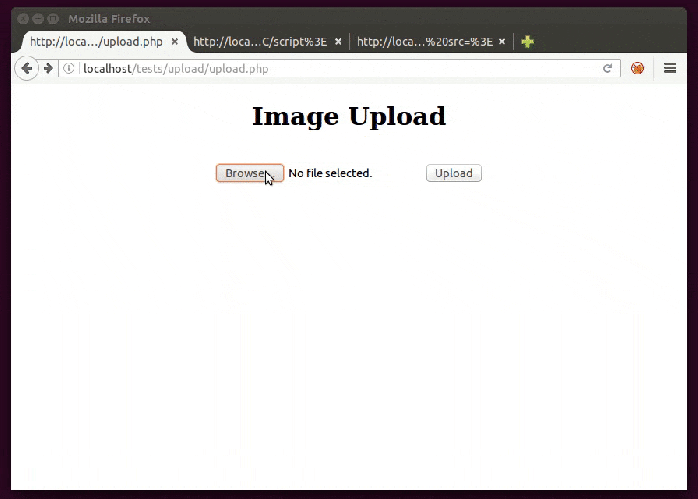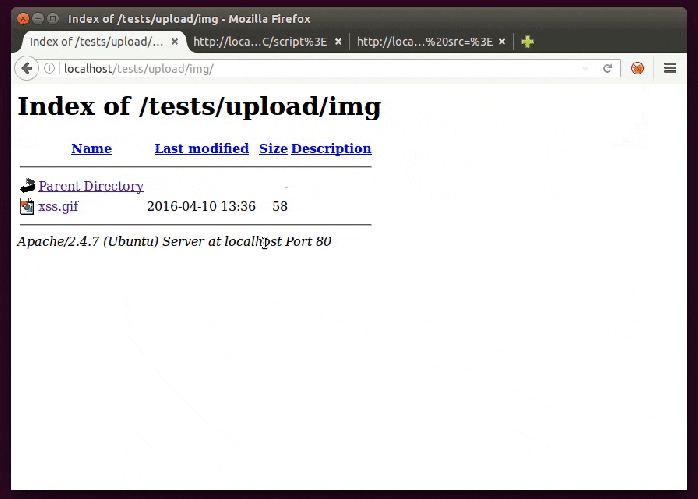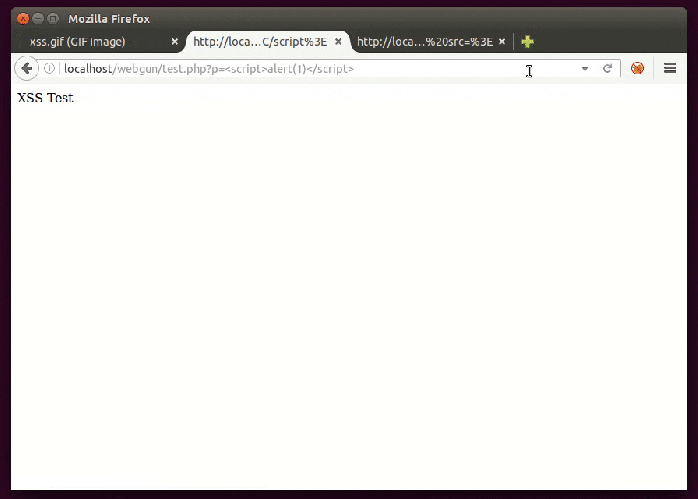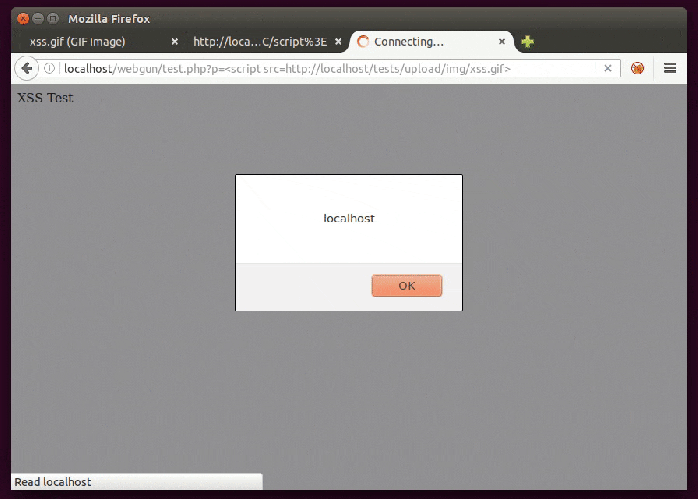
To create such an image just use this as content and name it with .gif extension:
GIF89a/*<svg/οnlοad=alert(1)>*/=alert(document.domain)//;
The signature of a GIF file, GIF89a, is used as a javascript variable assigned to the alert function. Between them however, there’s a commented XSS vector just in case the image can be retrieved as the text/HTML MIME type, thus allowing payload execution by just requesting the file.
As we can also see below, the file UNIX-like command along with the PHP functions exif_imagetype() and getimagesize() recognize it as a GIF file. So if an application is using just these to validate the image, the file will be uploaded (but may be sanitized later).

For more file types that can have its signature as ASCII characters used for a javascript variable assignment, check this.
There are more elaborated examples of XSS using image files, usually bypassing filters like the GD library ones. A good example of that is here.
#hack2learn