拓扑如下
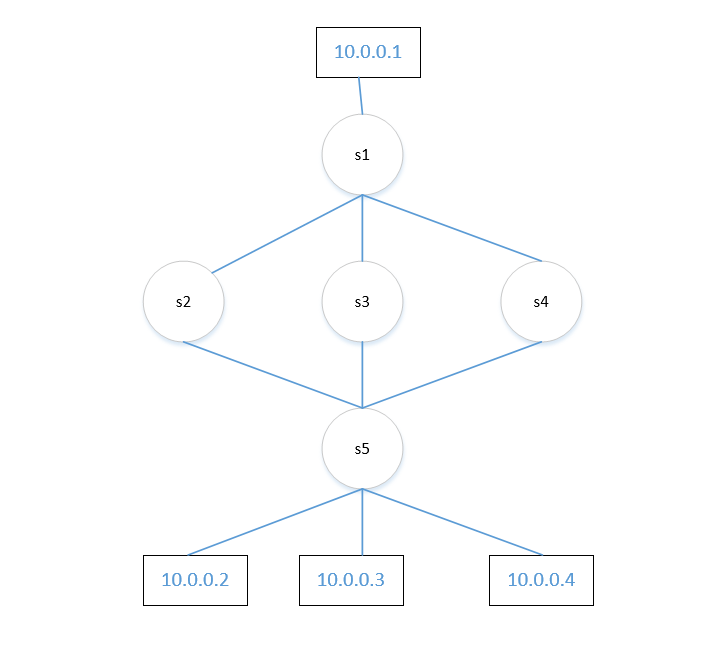
from mininet.topo import Topo class MininetTopo(Topo): def __init__(self,**opts): Topo.__init__(self, **opts) host1 = self.addHost('h1') host2 = self.addHost('h2') host3 = self.addHost('h3') host4 = self.addHost('h4') self.switch = {} for s in range(1,6): self.switch[s-1] = self.addSwitch('s%s' %(s)) self.addLink(self.switch[0], self.switch[1]) self.addLink(self.switch[0], self.switch[2]) self.addLink(self.switch[0], self.switch[3]) self.addLink(self.switch[4], self.switch[1]) self.addLink(self.switch[4], self.switch[2]) self.addLink(self.switch[4], self.switch[3]) #Adding host self.addLink(self.switch[0], host1) self.addLink(self.switch[4], host2) self.addLink(self.switch[4], host3) self.addLink(self.switch[4], host4) topos = {'group':(lambda:MininetTopo())}
mininet> net h1 h1-eth0:s1-eth4 h2 h2-eth0:s5-eth4 h3 h3-eth0:s5-eth5 h4 h4-eth0:s5-eth6 s1 lo: s1-eth1:s2-eth1 s1-eth2:s3-eth1 s1-eth3:s4-eth1 s1-eth4:h1-eth0 s2 lo: s2-eth1:s1-eth1 s2-eth2:s5-eth1 s3 lo: s3-eth1:s1-eth2 s3-eth2:s5-eth2 s4 lo: s4-eth1:s1-eth3 s4-eth2:s5-eth3 s5 lo: s5-eth1:s2-eth2 s5-eth2:s3-eth2 s5-eth3:s4-eth2 s5-eth4:h2-eth0 s5-eth5:h3-eth0 s5-eth6:h4-eth0 c0
arp代理
from ryu.base import app_manager from ryu.controller import ofp_event from ryu.controller.handler import CONFIG_DISPATCHER, MAIN_DISPATCHER from ryu.controller.handler import set_ev_cls from ryu.ofproto import ofproto_v1_3 from ryu.lib.packet import packet from ryu.lib.packet import ethernet from ryu.lib.packet import arp from ryu.lib.packet import ipv6 from ryu.lib import mac class SimpleARPProxy13(app_manager.RyuApp): OFP_VERSIONS = [ofproto_v1_3.OFP_VERSION] def __init__(self, *args, **kwargs): super(SimpleARPProxy13, self).__init__(*args, **kwargs) self.mac_to_port = {} self.arp_table = {} self.sw = {} @set_ev_cls(ofp_event.EventOFPSwitchFeatures, CONFIG_DISPATCHER) def switch_features_handler(self, ev): datapath = ev.msg.datapath ofproto = datapath.ofproto parser = datapath.ofproto_parser # install table-miss flow entry # # We specify NO BUFFER to max_len of the output action due to # OVS bug. At this moment, if we specify a lesser number, e.g., # 128, OVS will send Packet-In with invalid buffer_id and # truncated packet data. In that case, we cannot output packets # correctly. match = parser.OFPMatch() actions = [parser.OFPActionOutput(ofproto.OFPP_CONTROLLER, ofproto.OFPCML_NO_BUFFER)] self.add_flow(datapath, 0, match, actions) self.logger.info("switch:%s connected", datapath.id) # switch s1 ''' if datapath.id == 1: # add group tables self.send_group_mod(datapath) actions = [parser.OFPActionGroup(group_id=50)] match = parser.OFPMatch(in_port=4) self.add_flow(datapath, 10, match, actions) ''' def add_flow(self, datapath, priority, match, actions, buffer_id=None): ofproto = datapath.ofproto parser = datapath.ofproto_parser inst = [parser.OFPInstructionActions(ofproto.OFPIT_APPLY_ACTIONS, actions)] if buffer_id: mod = parser.OFPFlowMod(datapath=datapath, buffer_id=buffer_id, priority=priority, match=match, instructions=inst) else: mod = parser.OFPFlowMod(datapath=datapath, priority=priority, match=match, instructions=inst) datapath.send_msg(mod) @set_ev_cls(ofp_event.EventOFPPacketIn, MAIN_DISPATCHER) def _packet_in_handler(self, ev): msg = ev.msg datapath = msg.datapath ofproto = datapath.ofproto parser = datapath.ofproto_parser in_port = msg.match['in_port'] pkt = packet.Packet(msg.data) eth = pkt.get_protocols(ethernet.ethernet)[0] dst = eth.dst src = eth.src dpid = datapath.id self.logger.info("packet in %s %s %s %s", dpid, src, dst, in_port) if pkt.get_protocol(ipv6.ipv6): # Drop the IPV6 Packets. match = parser.OFPMatch(eth_type=eth.ethertype) actions = [] self.add_flow(datapath, 1, match, actions) return None arp_pkt = pkt.get_protocol(arp.arp) if arp_pkt: self.arp_table[arp_pkt.src_ip] = src # ARP learning self.logger.info(" ARP: %s -> %s", arp_pkt.src_ip, arp_pkt.dst_ip) if self.arp_handler(msg): # answer or drop return None self.mac_to_port.setdefault(dpid, {}) self.logger.info("packet in %s %s %s %s", dpid, src, dst, in_port) # Learn a mac address to avoid FLOOD next time. if src not in self.mac_to_port[dpid]: self.mac_to_port[dpid][src] = in_port #print self.mac_to_port if dst in self.mac_to_port[dpid]: out_port = self.mac_to_port[dpid][dst] #else: #if self.arp_handler(msg): # 1:reply or drop; 0: flood # return None else: print(self.mac_to_port[dpid]) out_port = ofproto.OFPP_FLOOD print("Flood") actions = [parser.OFPActionOutput(out_port)] # Install a flow to avoid packet_in next time if out_port != ofproto.OFPP_FLOOD: self.logger.info(" install flow_mod:%s -> %s ", in_port, out_port) match = parser.OFPMatch(in_port=in_port, eth_dst=dst) self.add_flow(datapath, 1, match, actions) data = None if msg.buffer_id == ofproto.OFP_NO_BUFFER: data = msg.data out = parser.OFPPacketOut(datapath=datapath, buffer_id=msg.buffer_id, in_port=in_port, actions=actions, data=data) datapath.send_msg(out) def arp_handler(self, msg): datapath = msg.datapath ofproto = datapath.ofproto parser = datapath.ofproto_parser in_port = msg.match['in_port'] pkt = packet.Packet(msg.data) eth = pkt.get_protocols(ethernet.ethernet)[0] arp_pkt = pkt.get_protocol(arp.arp) if eth: eth_dst = eth.dst eth_src = eth.src #arp learn只学习arp reques中的src ip 和in port,没有学习arp reply中的src ip 和in port # Break the loop for avoiding ARP broadcast storm if eth_dst == mac.BROADCAST_STR: # and arp_pkt: arp_dst_ip = arp_pkt.dst_ip arp_src_ip = arp_pkt.src_ip if (datapath.id, arp_src_ip, arp_dst_ip) in self.sw: # packet come back at different port. if self.sw[(datapath.id, arp_src_ip, arp_dst_ip)] != in_port: #drop datapath.send_packet_out(in_port=in_port, actions=[]) return True else: # self.sw.setdefault((datapath.id, eth_src, arp_dst_ip), None) self.sw[(datapath.id, arp_src_ip, arp_dst_ip)] = in_port print(self.sw) self.mac_to_port.setdefault(datapath.id, {}) self.mac_to_port[datapath.id][eth_src] = in_port # Try to reply arp request if arp_pkt: if arp_pkt.opcode == arp.ARP_REQUEST: hwtype = arp_pkt.hwtype proto = arp_pkt.proto hlen = arp_pkt.hlen plen = arp_pkt.plen arp_src_ip = arp_pkt.src_ip arp_dst_ip = arp_pkt.dst_ip if arp_dst_ip in self.arp_table: actions = [parser.OFPActionOutput(in_port)] ARP_Reply = packet.Packet() ARP_Reply.add_protocol(ethernet.ethernet( ethertype=eth.ethertype, dst=eth_src, src=self.arp_table[arp_dst_ip])) ARP_Reply.add_protocol(arp.arp( opcode=arp.ARP_REPLY, src_mac=self.arp_table[arp_dst_ip], src_ip=arp_dst_ip, dst_mac=eth_src, dst_ip=arp_src_ip)) ARP_Reply.serialize() out = parser.OFPPacketOut( datapath=datapath, buffer_id=ofproto.OFP_NO_BUFFER, in_port=ofproto.OFPP_CONTROLLER, actions=actions, data=ARP_Reply.data) datapath.send_msg(out) print("ARP_Reply") return True return False def send_group_mod(self, datapath): ofproto = datapath.ofproto parser = datapath.ofproto_parser # Hardcoding the stuff, as we already know the topology diagram. # Group table1 # Receiver port4, forward it to port1 and port2、 Port3 actions1 = [parser.OFPActionOutput(1)] actions2 = [parser.OFPActionOutput(2)] actions3 = [parser.OFPActionOutput(3)] buckets = [parser.OFPBucket(actions=actions1), parser.OFPBucket(actions=actions2), parser.OFPBucket(actions=actions3)] req = parser.OFPGroupMod(datapath, ofproto.OFPGC_ADD, ofproto.OFPGT_ALL, 50, buckets) datapath.send_msg(req)
同时开三个终端 tcpdump -i s1-eth1 icmp -nv ; tcpdump -i s1-eth2 icmp -nv;tcpdump -i s1-eth3 icmp -nv
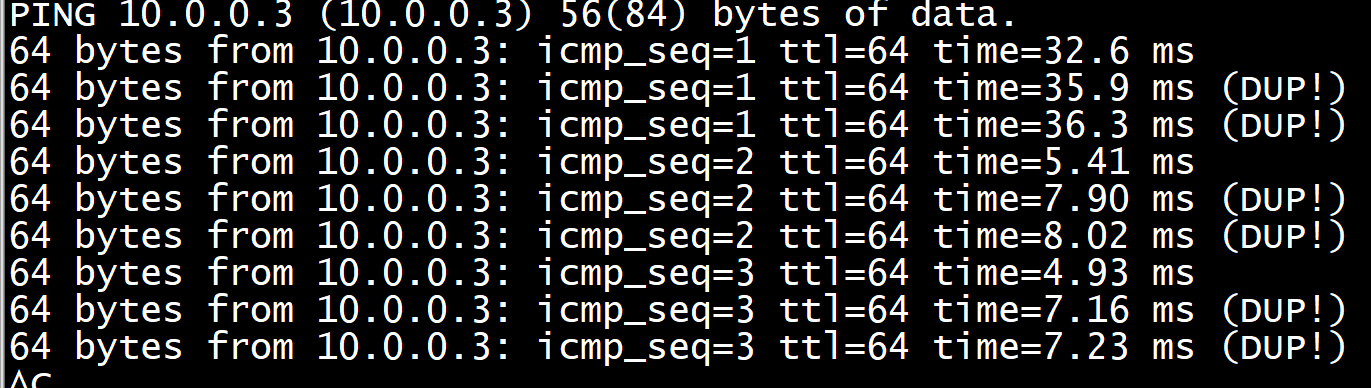
mininet> h1 ping -i 3 h2 PING 10.0.0.2 (10.0.0.2) 56(84) bytes of data. 64 bytes from 10.0.0.2: icmp_seq=1 ttl=64 time=5.24 ms 64 bytes from 10.0.0.2: icmp_seq=1 ttl=64 time=6.49 ms (DUP!) 64 bytes from 10.0.0.2: icmp_seq=1 ttl=64 time=6.67 ms (DUP!) 64 bytes from 10.0.0.2: icmp_seq=2 ttl=64 time=4.64 ms 64 bytes from 10.0.0.2: icmp_seq=2 ttl=64 time=5.87 ms (DUP!) 64 bytes from 10.0.0.2: icmp_seq=2 ttl=64 time=5.97 ms (DUP!) 64 bytes from 10.0.0.2: icmp_seq=3 ttl=64 time=4.13 ms 64 bytes from 10.0.0.2: icmp_seq=3 ttl=64 time=5.59 ms (DUP!) 64 bytes from 10.0.0.2: icmp_seq=3 ttl=64 time=5.68 ms (DUP!) ^C --- 10.0.0.2 ping statistics --- 3 packets transmitted, 3 received, +6 duplicates, 0% packet loss, time 6007ms rtt min/avg/max/mdev = 4.136/5.591/6.674/0.772 ms
出现dupliacte报文

[root@kunpeng82 devuser]# tcpdump -i s1-eth1 icmp -nv tcpdump: listening on s1-eth1, link-type EN10MB (Ethernet), capture size 262144 bytes 08:34:11.640951 IP (tos 0x0, ttl 64, id 20196, offset 0, flags [DF], proto ICMP (1), length 84) 10.0.0.1 > 10.0.0.2: ICMP echo request, id 18347, seq 1, length 64 08:34:14.643905 IP (tos 0x0, ttl 64, id 20302, offset 0, flags [DF], proto ICMP (1), length 84) 10.0.0.1 > 10.0.0.2: ICMP echo request, id 18347, seq 2, length 64 08:34:17.647875 IP (tos 0x0, ttl 64, id 20418, offset 0, flags [DF], proto ICMP (1), length 84) 10.0.0.1 > 10.0.0.2: ICMP echo request, id 18347, seq 3, length 64
[root@kunpeng82 devuser]# tcpdump -i s1-eth2 icmp -nv tcpdump: listening on s1-eth2, link-type EN10MB (Ethernet), capture size 262144 bytes 08:34:11.640963 IP (tos 0x0, ttl 64, id 20196, offset 0, flags [DF], proto ICMP (1), length 84) 10.0.0.1 > 10.0.0.2: ICMP echo request, id 18347, seq 1, length 64 08:34:11.643867 IP (tos 0x0, ttl 64, id 25361, offset 0, flags [none], proto ICMP (1), length 84) 10.0.0.2 > 10.0.0.1: ICMP echo reply, id 18347, seq 1, length 64 08:34:11.645171 IP (tos 0x0, ttl 64, id 25362, offset 0, flags [none], proto ICMP (1), length 84) 10.0.0.2 > 10.0.0.1: ICMP echo reply, id 18347, seq 1, length 64 08:34:11.645354 IP (tos 0x0, ttl 64, id 25363, offset 0, flags [none], proto ICMP (1), length 84) 10.0.0.2 > 10.0.0.1: ICMP echo reply, id 18347, seq 1, length 64 08:34:14.643914 IP (tos 0x0, ttl 64, id 20302, offset 0, flags [DF], proto ICMP (1), length 84) 10.0.0.1 > 10.0.0.2: ICMP echo request, id 18347, seq 2, length 64 08:34:14.647024 IP (tos 0x0, ttl 64, id 25439, offset 0, flags [none], proto ICMP (1), length 84) 10.0.0.2 > 10.0.0.1: ICMP echo reply, id 18347, seq 2, length 64 08:34:14.648252 IP (tos 0x0, ttl 64, id 25440, offset 0, flags [none], proto ICMP (1), length 84) 10.0.0.2 > 10.0.0.1: ICMP echo reply, id 18347, seq 2, length 64 08:34:14.648350 IP (tos 0x0, ttl 64, id 25441, offset 0, flags [none], proto ICMP (1), length 84) 10.0.0.2 > 10.0.0.1: ICMP echo reply, id 18347, seq 2, length 64 08:34:17.647883 IP (tos 0x0, ttl 64, id 20418, offset 0, flags [DF], proto ICMP (1), length 84) 10.0.0.1 > 10.0.0.2: ICMP echo request, id 18347, seq 3, length 64 08:34:17.650512 IP (tos 0x0, ttl 64, id 25464, offset 0, flags [none], proto ICMP (1), length 84) 10.0.0.2 > 10.0.0.1: ICMP echo reply, id 18347, seq 3, length 64 08:34:17.651973 IP (tos 0x0, ttl 64, id 25465, offset 0, flags [none], proto ICMP (1), length 84) 10.0.0.2 > 10.0.0.1: ICMP echo reply, id 18347, seq 3, length 64 08:34:17.652065 IP (tos 0x0, ttl 64, id 25466, offset 0, flags [none], proto ICMP (1), length 84) 10.0.0.2 > 10.0.0.1: ICMP echo reply, id 18347, seq 3, length 64
[root@kunpeng82 devuser]# tcpdump -i s1-eth3 icmp -nv tcpdump: listening on s1-eth3, link-type EN10MB (Ethernet), capture size 262144 bytes 08:34:11.640971 IP (tos 0x0, ttl 64, id 20196, offset 0, flags [DF], proto ICMP (1), length 84) 10.0.0.1 > 10.0.0.2: ICMP echo request, id 18347, seq 1, length 64 08:34:14.643919 IP (tos 0x0, ttl 64, id 20302, offset 0, flags [DF], proto ICMP (1), length 84) 10.0.0.1 > 10.0.0.2: ICMP echo request, id 18347, seq 2, length 64 08:34:17.647888 IP (tos 0x0, ttl 64, id 20418, offset 0, flags [DF], proto ICMP (1), length 84) 10.0.0.1 > 10.0.0.2: ICMP echo request, id 18347, seq 3, length 64
三个端口都能抓到
mininet> h1 ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: h1-eth0@if381: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether 1e:86:6e:61:30:84 brd ff:ff:ff:ff:ff:ff link-netnsid 0 inet 10.0.0.1/8 brd 10.255.255.255 scope global h1-eth0 valid_lft forever preferred_lft forever inet6 fe80::1c86:6eff:fe61:3084/64 scope link valid_lft forever preferred_lft forever mininet> h2 ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: h2-eth0@if388: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether 9a:43:17:a6:6a:b5 brd ff:ff:ff:ff:ff:ff link-netnsid 0 inet 10.0.0.2/8 brd 10.255.255.255 scope global h2-eth0 valid_lft forever preferred_lft forever inet6 fe80::9843:17ff:fea6:6ab5/64 scope link valid_lft forever preferred_lft forever
[root@kunpeng82 app]# ovs-ofctl dump-flows s1 cookie=0x0, duration=803.112s, table=0, n_packets=11, n_bytes=1022, priority=1,in_port="s1-eth4",dl_dst=96:6a:f6:25:8c:95 actions=output:"s1-eth2" cookie=0x0, duration=803.100s, table=0, n_packets=51, n_bytes=4662, priority=1,in_port="s1-eth2",dl_dst=1e:86:6e:61:30:84 actions=output:"s1-eth4" cookie=0x0, duration=801.318s, table=0, n_packets=9, n_bytes=630, priority=1,ipv6 actions=drop cookie=0x0, duration=840.963s, table=0, n_packets=24, n_bytes=1764, priority=0 actions=CONTROLLER:65535 [root@kunpeng82 app]# ovs-ofctl dump-flows s2 cookie=0x0, duration=832.486s, table=0, n_packets=5, n_bytes=350, priority=1,ipv6 actions=drop cookie=0x0, duration=846.527s, table=0, n_packets=22, n_bytes=1624, priority=0 actions=CONTROLLER:65535 [root@kunpeng82 app]# ovs-ofctl dump-flows s3 cookie=0x0, duration=843.846s, table=0, n_packets=5, n_bytes=350, priority=1,ipv6 actions=drop cookie=0x0, duration=830.277s, table=0, n_packets=11, n_bytes=1022, priority=1,in_port="s3-eth1",dl_dst=96:6a:f6:25:8c:95 actions=output:"s3-eth2" cookie=0x0, duration=830.270s, table=0, n_packets=51, n_bytes=4662, priority=1,in_port="s3-eth2",dl_dst=1e:86:6e:61:30:84 actions=output:"s3-eth1" cookie=0x0, duration=868.126s, table=0, n_packets=21, n_bytes=1638, priority=0 actions=CONTROLLER:65535 [root@kunpeng82 app]# ovs-ofctl dump-flows s4 cookie=0x0, duration=849.782s, table=0, n_packets=4, n_bytes=280, priority=1,ipv6 actions=drop cookie=0x0, duration=894.542s, table=0, n_packets=22, n_bytes=1624, priority=0 actions=CONTROLLER:65535 [root@kunpeng82 app]# ovs-ofctl dump-flows s5 cookie=0x0, duration=893.198s, table=0, n_packets=16, n_bytes=1120, priority=1,ipv6 actions=drop cookie=0x0, duration=859.148s, table=0, n_packets=11, n_bytes=1022, priority=1,in_port="s5-eth2",dl_dst=96:6a:f6:25:8c:95 actions=output:"s5-eth6" cookie=0x0, duration=859.145s, table=0, n_packets=10, n_bytes=924, priority=1,in_port="s5-eth6",dl_dst=1e:86:6e:61:30:84 actions=output:"s5-eth2" cookie=0x0, duration=840.901s, table=0, n_packets=13, n_bytes=1218, priority=1,in_port="s5-eth5",dl_dst=1e:86:6e:61:30:84 actions=output:"s5-eth2" cookie=0x0, duration=840.892s, table=0, n_packets=4, n_bytes=336, priority=1,in_port="s5-eth2",dl_dst=02:29:e7:1e:64:47 actions=output:"s5-eth5" cookie=0x0, duration=840.890s, table=0, n_packets=4, n_bytes=336, priority=1,in_port="s5-eth1",dl_dst=02:29:e7:1e:64:47 actions=output:"s5-eth5" cookie=0x0, duration=840.889s, table=0, n_packets=4, n_bytes=336, priority=1,in_port="s5-eth3",dl_dst=02:29:e7:1e:64:47 actions=output:"s5-eth5" cookie=0x0, duration=834.086s, table=0, n_packets=26, n_bytes=2436, priority=1,in_port="s5-eth4",dl_dst=1e:86:6e:61:30:84 actions=output:"s5-eth2" cookie=0x0, duration=834.077s, table=0, n_packets=9, n_bytes=770, priority=1,in_port="s5-eth2",dl_dst=9a:43:17:a6:6a:b5 actions=output:"s5-eth4" cookie=0x0, duration=834.074s, table=0, n_packets=9, n_bytes=770, priority=1,in_port="s5-eth1",dl_dst=9a:43:17:a6:6a:b5 actions=output:"s5-eth4" cookie=0x0, duration=834.074s, table=0, n_packets=9, n_bytes=770, priority=1,in_port="s5-eth3",dl_dst=9a:43:17:a6:6a:b5 actions=output:"s5-eth4" cookie=0x0, duration=896.999s, table=0, n_packets=18, n_bytes=1176, priority=0 actions=CONTROLLER:65535 [root@kunpeng82 app]#
mininet> h1 ip n 10.0.0.2 dev h1-eth0 lladdr 9a:43:17:a6:6a:b5 STALE 10.0.0.4 dev h1-eth0 lladdr 96:6a:f6:25:8c:95 STALE 10.0.0.3 dev h1-eth0 lladdr 02:29:e7:1e:64:47 STALE
EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 1 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 4 packet in 1 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 4 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 4} Flood EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 3 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 packet in 3 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 2 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 packet in 2 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood packet in 4 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 packet in 4 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 1 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 4 packet in 1 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 4 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 4} Flood EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 3 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 packet in 3 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 4 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 packet in 4 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood packet in 2 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 packet in 2 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 1 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 4 ARP: 10.0.0.1 -> 10.0.0.2 ARP_Reply packet in 1 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 4 ARP: 10.0.0.1 -> 10.0.0.2 packet in 1 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 4 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 4} Flood EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 3 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 ARP: 10.0.0.1 -> 10.0.0.2 packet in 3 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood ----------------------------- arp learn只学习arp reques中的src ip 和in port,没有学习arp reply中的src ip 和in port,所以dst mac从哪里发出仍然不知道 EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 2 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 ARP: 10.0.0.1 -> 10.0.0.2 packet in 2 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood packet in 4 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 ARP: 10.0.0.1 -> 10.0.0.2 packet in 4 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 1 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 4 packet in 1 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 4 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 4} Flood EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 3 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 packet in 3 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn EVENT ofp_event->SimpleARPProxy13 EventOFPPacketIn packet in 2 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 packet in 2 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood packet in 4 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 packet in 4 1e:86:6e:61:30:84 9a:43:17:a6:6a:b5 1 {'96:6a:f6:25:8c:95': 2, '1e:86:6e:61:30:84': 1} Flood
加上以下流规则,给s1加上
[root@kunpeng82 app]# ovs-ofctl -O OpenFlow13 add-group s1 group_id=5566,type=select,bucket=output:1,bucket=output:2,bucket=output:3 [root@kunpeng82 app]# ovs-ofctl -O OpenFlow13 add-flow s1 in_port=4,actions=group:5566
所有访问10.0.0.1的报文(包括h2、h3、h4)的恢复报文都是从1号端口转发(这么设置),这样会使arp reply都从output:1发出, arp proxy learn学到的到h2、h3、h4的转发端口都是同一个port,不这么设置,h2/h3/h4反问h1会出现flood
[root@kunpeng82 app]# ovs-ofctl -O OpenFlow13 add-flow s5 eth_type=0x0800,ip_dst=10.0.0.1,actions=output:1 [root@kunpeng82 app]# ovs-ofctl -O OpenFlow13 add-flow s5 eth_type=0x0806,ip_dst=10.0.0.1,actions=output:1 [root@kunpeng82 app]#
h1 ping h2只能 s1-eth1 上抓到报文

arp learn只学习arp reques中的src ip 和in port,没有学习arp reply中的src ip 和in port