[root@bogon ~]# cd /etc/xinetd.d/ [root@bogon xinetd.d]# ls chargen-dgram daytime-dgram discard-dgram echo-dgram tcpmux-server time-dgram chargen-stream daytime-stream discard-stream echo-stream tftp time-stream [root@bogon xinetd.d]# cat tftp # default: off # description: The tftp server serves files using the trivial file transfer # protocol. The tftp protocol is often used to boot diskless # workstations, download configuration files to network-aware printers, # and to start the installation process for some operating systems. service tftp { socket_type = dgram protocol = udp wait = yes user = root server = /usr/sbin/in.tftpd #server_args = -s /var/lib/tftpboot server_args = -v -v -v -v -v --map-file /tftpboot/map-file /tftpboot disable = no per_source = 11 cps = 100 2 flags = IPv4 }
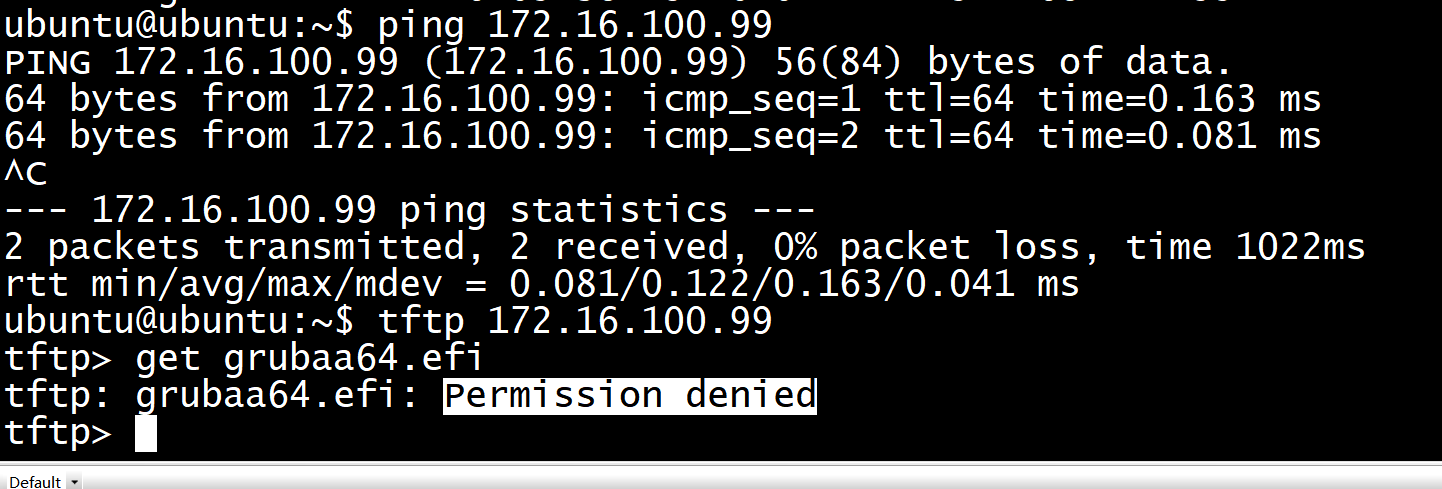
如果回显信息显示”Permission denied”,表示TFTP服务目录“tftpboot”的访问权限未打开。 执行vi /etc/sysconfig/selinux命令。 在回显信息中编辑修改如下。 SELINUX=permissive 按“ESC”。 按“Shift”+“:”,输入wq,按“Enter”保存并退出编辑。 执行sudo setenforce 0,打开访问权限。
[root@bogon ~]# service firewalld status Redirecting to /bin/systemctl status firewalld.service ● firewalld.service - firewalld - dynamic firewall daemon Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled) Active: active (running) since Thu 2020-07-16 04:25:51 CST; 5h 21min ago Docs: man:firewalld(1) Main PID: 1788 (firewalld) Tasks: 2 CGroup: /system.slice/firewalld.service └─1788 /usr/bin/python -Es /usr/sbin/firewalld --nofork --nopid Jul 16 04:25:49 localhost.localdomain systemd[1]: Starting firewalld - dynamic firewall daemon... Jul 16 04:25:51 localhost.localdomain systemd[1]: Started firewalld - dynamic firewall daemon. [root@bogon ~]#
[root@bogon ~]# service firewalld status
service xinetd restart
[root@bogon data2]# tcpdump -i enahisic2i3.900 -T tftp -env tcpdump: listening on enahisic2i3.900, link-type EN10MB (Ethernet), capture size 262144 bytes
910, offset 0, flags [none], proto UDP (17), length 544) 172.16.100.99.50487 > 172.16.100.82.51334: 516 DATA block 1284 10:11:02.059619 48:57:02:64:e7:ae > 48:57:02:64:ea:1e, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 45169, offset 0, flags [DF], proto UDP (17), length 32) 172.16.100.82.51334 > 172.16.100.99.50487: 4 ACK block 1284 10:11:02.059634 48:57:02:64:ea:1e > 48:57:02:64:e7:ae, ethertype IPv4 (0x0800), length 558: (tos 0x0, ttl 64, id 2911, offset 0, flags [none], proto UDP (17), length 544) 172.16.100.99.50487 > 172.16.100.82.51334: 516 DATA block 1285 10:11:02.059672 48:57:02:64:e7:ae > 48:57:02:64:ea:1e, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 45170, offset 0, flags [DF], proto UDP (17), length 32) 172.16.100.82.51334 > 172.16.100.99.50487: 4 ACK block 1285 10:11:02.059686 48:57:02:64:ea:1e > 48:57:02:64:e7:ae, ethertype IPv4 (0x0800), length 558: (tos 0x0, ttl 64, id 2912, offset 0, flags [none], proto UDP (17), length 544) 172.16.100.99.50487 > 172.16.100.82.51334: 516 DATA block 1286 10:11:02.059725 48:57:02:64:e7:ae > 48:57:02:64:ea:1e, ethertype IPv4 (0x0800), length 56: (tos 0x0, ttl 64, id 45171, offset 0, flags [DF], proto UDP (17), length 32) 172.16.100.82.51334 > 172.16.100.99.50487: 4 ACK block 1286 10:11:02.059739 48:57:02:64:ea:1e > 48:57:02:64:e7:ae, ethertype IPv4 (0x0800), length 558: (tos 0x0, ttl 64, id 2913, offset 0, flags [none], proto UDP (17), length 544)