Last login: Sun Sep 20 23:51:55 2020 from 192.168.117.59 [root@localhost ~]# cat /var/log/messages|grep conn [root@localhost ~]# dmesg | grep conntrack [ 18.842689] nf_conntrack version 0.5.0 (65536 buckets, 262144 max) [2936843.523511] nf_conntrack version 0.5.0 (65536 buckets, 262144 max) [root@localhost ~]# cat /proc/net/nf_conntrack | wc -l 7 [root@localhost ~]# cat /proc/net/nf_conntrack ipv4 2 icmp 1 29 src=192.168.25.238 dst=192.168.60.15 type=8 code=0 id=1 src=192.168.60.15 dst=192.168.25.238 type=0 code=0 id=1 mark=0 secctx=system_u:object_r:unlabeled_t:s0 zone=0 use=2 ipv4 2 tcp 6 96753 ESTABLISHED src=210.22.22.134 dst=210.22.22.154 sport=31817 dport=22 src=210.22.22.154 dst=210.22.22.134 sport=22 dport=31817 [ASSURED] mark=0 secctx=system_u:object_r:unlabeled_t:s0 zone=0 use=2 ipv4 2 udp 17 25 src=192.168.8.18 dst=255.255.255.255 sport=67 dport=68 [UNREPLIED] src=255.255.255.255 dst=192.168.8.18 sport=68 dport=67 mark=0 secctx=system_u:object_r:unlabeled_t:s0 zone=0 use=2 ipv4 2 udp 17 25 src=0.0.0.0 dst=255.255.255.255 sport=68 dport=67 [UNREPLIED] src=255.255.255.255 dst=0.0.0.0 sport=67 dport=68 mark=0 secctx=system_u:object_r:unlabeled_t:s0 zone=0 use=2 ipv4 2 tcp 6 96738 ESTABLISHED src=210.22.22.134 dst=210.22.22.154 sport=31816 dport=22 src=210.22.22.154 dst=210.22.22.134 sport=22 dport=31816 [ASSURED] mark=0 secctx=system_u:object_r:unlabeled_t:s0 zone=0 use=2 ipv4 2 udp 17 16 src=192.168.117.38 dst=192.168.117.255 sport=137 dport=137 [UNREPLIED] src=192.168.117.255 dst=192.168.117.38 sport=137 dport=137 mark=0 secctx=system_u:object_r:unlabeled_t:s0 zone=0 use=2 ipv4 2 udp 17 14 src=192.168.117.23 dst=255.255.255.255 sport=64756 dport=22313 [UNREPLIED] src=255.255.255.255 dst=192.168.117.23 sport=22313 dport=64756 mark=0 secctx=system_u:object_r:unlabeled_t:s0 zone=0 use=2 ipv4 2 tcp 6 300 ESTABLISHED src=192.168.117.59 dst=192.168.117.240 sport=64629 dport=60000 src=192.168.117.240 dst=192.168.117.59 sport=60000 dport=64629 [ASSURED] mark=0 secctx=system_u:object_r:unlabeled_t:s0 zone=0 use=2 ipv4 2 udp 17 18 src=192.168.117.28 dst=192.168.117.255 sport=138 dport=138 [UNREPLIED] src=192.168.117.255 dst=192.168.117.28 sport=138 dport=138 mark=0 secctx=system_u:object_r:unlabeled_t:s0 zone=0 use=2 [root@localhost ~]#
1. CentOS 6系列
由于iptables的调试日志输出依赖于内核模块,这些内核模块并不是开机就加载的,因此我们需要手动加载,在CentOS 6系列上iptables日志输出依赖于ipt_LOG(LOG是大写的)模块,所以手动加载该模块,
modprobe ipt_LOG
1
加载完后,我们可以通过以下命令确认下是否成功,
[root@CentOS-6-5 localhost]# sysctl net.netfilter.nf_log.2
net.netfilter.nf_log.2 = ipt_LOG
如果为NULL,那么就失败了。
2. CentOS 7系列
对于CentOS 7系列,和6系列不同,依赖的iptables日志模块不再是ipt_LOG,而是nf_log_ipv4,因此需要手动加载该模块,
[root@CentOS-7-3 localhost]# modprobe nf_log_ipv4
[root@CentOS-7-3 localhost]# sysctl net.netfilter.nf_log.2
net.netfilter.nf_log.2 = nf_log_ipv4[root@localhost ~]# lsmod | grep ipt_LOG [root@localhost ~]# modprobe ipt_LOG [root@localhost ~]# lsmod | grep ipt_LOG [root@localhost ~]# sysctl net.netfilter.nf_log.2 net.netfilter.nf_log.2 = nf_log_ipv4 [root@localhost ~]# modprobe nf_log_ipv4 [root@localhost ~]# lsmod | greplog_ipv4 -bash: greplog_ipv4: command not found [root@localhost ~]# lsmod | grep log_ipv4 nf_log_ipv4 262144 1 nf_log_common 262144 1 nf_log_ipv4 [root@localhost ~]#
[root@localhost ~]# lsmod | grep nf_conntrack nf_conntrack_ipv4 262144 4 nf_defrag_ipv4 262144 1 nf_conntrack_ipv4 nf_conntrack 327680 6 xt_nat,nf_conntrack_ipv4,ipt_MASQUERADE,nf_nat_masquerade_ipv4,nf_nat_ipv4,nf_nat libcrc32c 262144 3 nf_conntrack,xfs,nf_nat [root@localhost ~]#
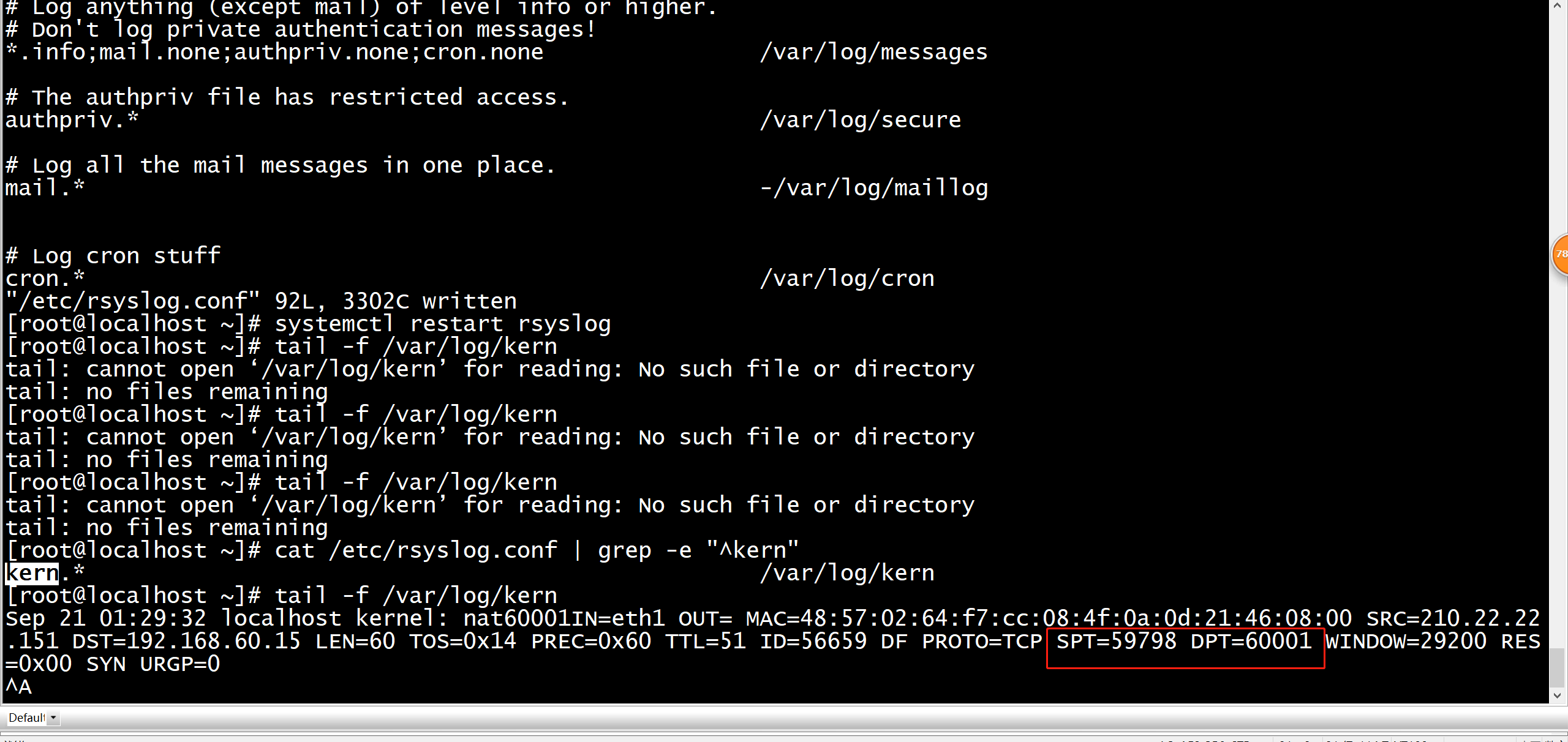
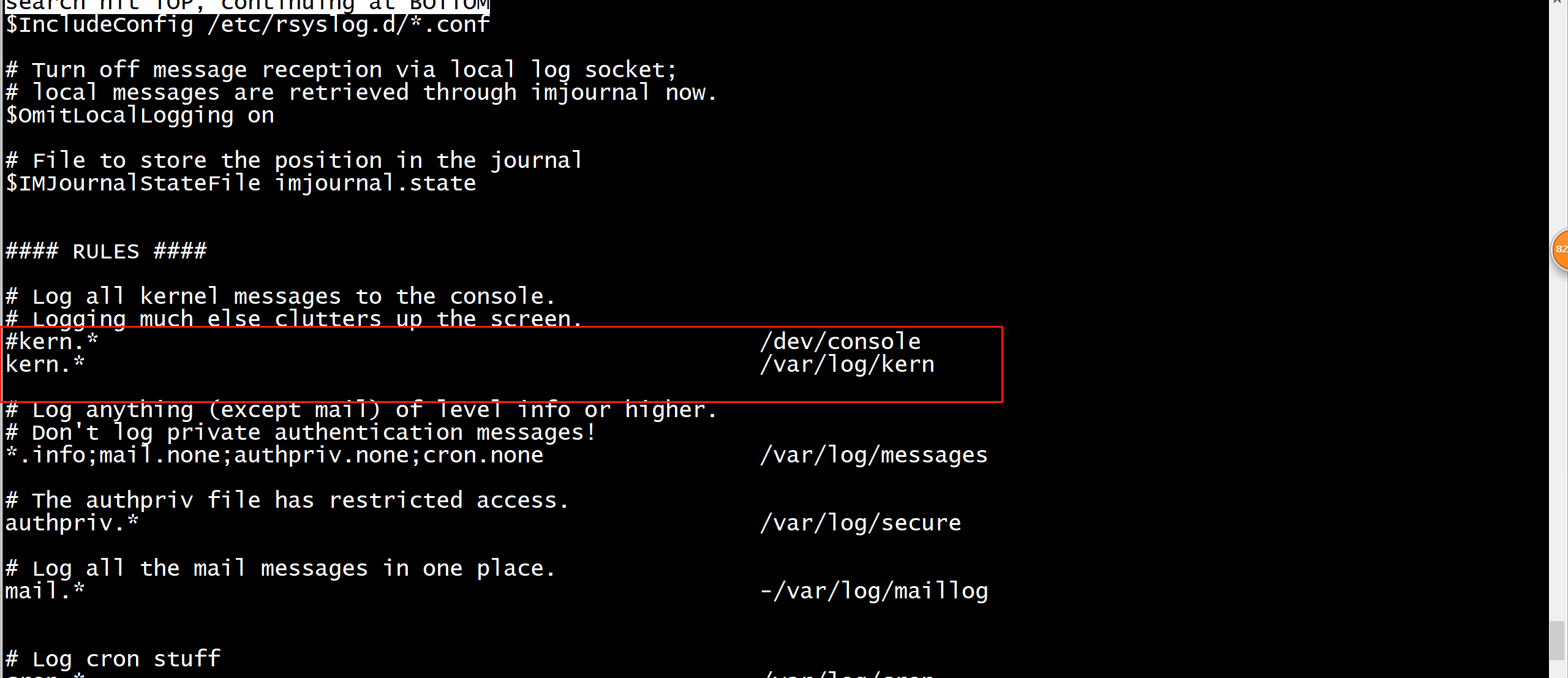
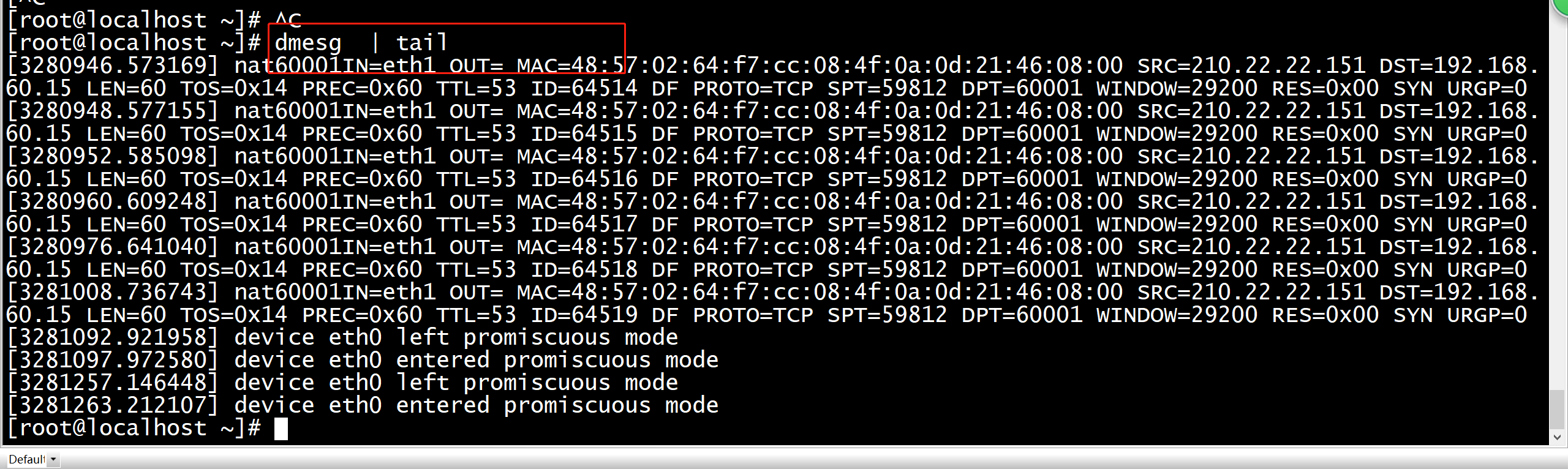
如何查看(debug) iptables/netfilter的详细日志 Load the (IPv4) netfilter log kernel module: modprobe nf_log_ipv4 Enable logging for the IPv4 (AF Family 2): sysctl net.netfilter.nf_log.2=nf_log_ipv4 reconfigure rsyslogd to log kernel messages (kern.*) to /var/log/kern: vi /etc/rsyslog.conf #去掉 #kern.* 前面的#号,且指定日志输出的路径。 > cat /etc/rsyslog.conf | grep -e "^kern" kern.* /var/log/kern restart rsyslogd: systemctl restart rsyslog


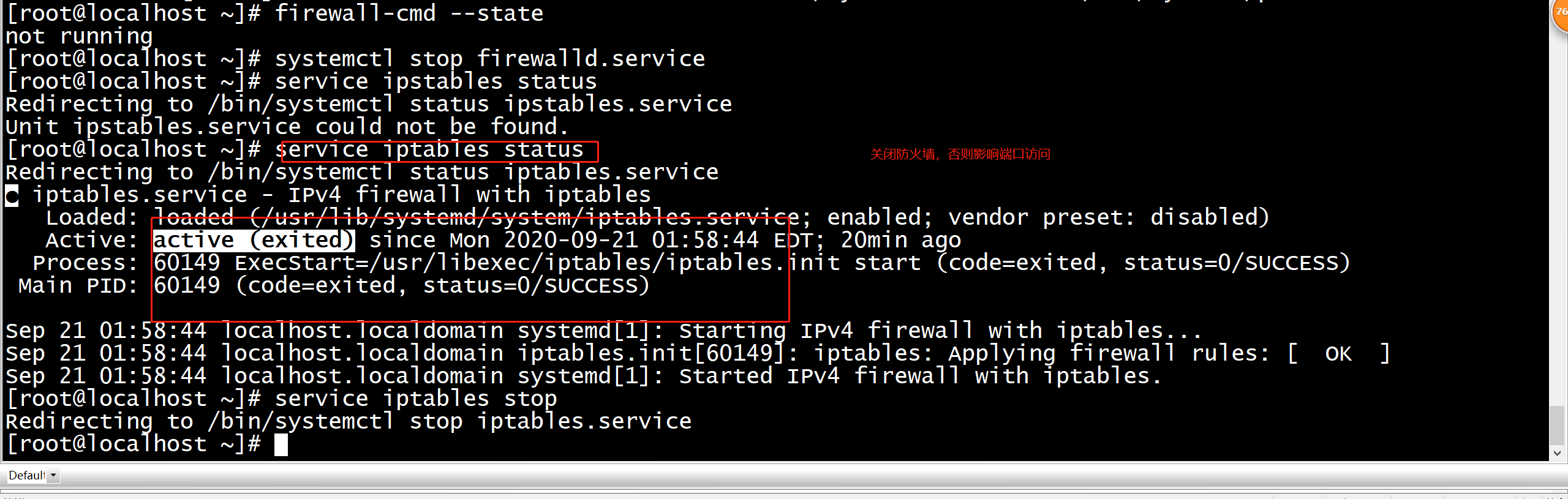
[root@localhost ~]# service iptables status Redirecting to /bin/systemctl status iptables.service Unit iptables.service could not be found. [root@localhost ~]# yum install iptables-services Loaded plugins: fastestmirror Loading mirror speeds from cached hostfile * epel: hkg.mirror.rackspace.com Resolving Dependencies --> Running transaction check ---> Package iptables-services.aarch64 0:1.4.21-34.el7 will be installed --> Finished Dependency Resolution
[root@localhost ~]# systemctl enable iptables Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to /usr/lib/systemd/system/iptables.service. [root@localhost ~]# systemctl start iptables [root@localhost ~]# systemctl status iptables ● iptables.service - IPv4 firewall with iptables Loaded: loaded (/usr/lib/systemd/system/iptables.service; enabled; vendor preset: disabled) Active: active (exited) since Mon 2020-09-21 01:58:44 EDT; 5s ago Process: 60149 ExecStart=/usr/libexec/iptables/iptables.init start (code=exited, status=0/SUCCESS) Main PID: 60149 (code=exited, status=0/SUCCESS) Sep 21 01:58:44 localhost.localdomain systemd[1]: Starting IPv4 firewall with iptables... Sep 21 01:58:44 localhost.localdomain iptables.init[60149]: iptables: Applying firewall rules: [ OK ] Sep 21 01:58:44 localhost.localdomain systemd[1]: Started IPv4 firewall with iptables. [root@localhost ~]#
service ipstables status