root@ubuntu:/opt/gopath/src/github.com/kata-containers/runtime# docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES d36cbb25f4ff debian "/bin/bash" About a minute ago Up About a minute sad_wilson fa2d3b3aec76 busybox "sh" 2 days ago Up 2 days cranky_mendeleev a9ab3ca9fa95 busybox "sh" 3 weeks ago Up 3 weeks stoic_mcclintock root@ubuntu:/opt/gopath/src/github.com/kata-containers/runtime# docker inspect d36cbb25f4ff --format '{{ .State.Pid }}' 12048 root@ubuntu:/opt/gopath/src/github.com/kata-containers/runtime# nsenter --target 12048 --mount --uts --ipc --net --pid root@ubuntu:/# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever 2: tap0_kata: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UNKNOWN group default qlen 1000 link/ether 9e:6a:1f:1c:1e:f1 brd ff:ff:ff:ff:ff:ff 459: eth0@if460: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether 02:42:ac:11:00:04 brd ff:ff:ff:ff:ff:ff link-netnsid 0 inet 172.17.0.4/16 brd 172.17.255.255 scope global eth0 valid_lft forever preferred_lft forever root@ubuntu:/# ip a | grep 02:44:61:7d:bd:3f root@ubuntu:/#
root@ubuntu:/home/ubuntu# ip monitor 458: veth4d73cef@if457: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 master docker0 state LOWERLAYERDOWN link/ether 22:e7:68:f2:d7:6c Deleted dev veth4d73cef lladdr 02:42:ac:11:00:04 REACHABLE Deleted ff02::2 dev veth4d73cef lladdr 33:33:00:00:00:02 NOARP Deleted ff02::16 dev veth4d73cef lladdr 33:33:00:00:00:16 NOARP Deleted ff02::1:fff2:d76c dev veth4d73cef lladdr 33:33:ff:f2:d7:6c NOARP 458: veth4d73cef@if457: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue master docker0 state LOWERLAYERDOWN group default link/ether 22:e7:68:f2:d7:6c brd ff:ff:ff:ff:ff:ff link-netnsid 12 ipv4 dev vethd6c94e3 forwarding on rp_filter strict mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off ipv6 dev vethd6c94e3 forwarding off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off 457: vethd6c94e3@veth4d73cef: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default link/ether 02:42:ac:11:00:04 brd ff:ff:ff:ff:ff:ff 458: veth4d73cef@NONE: <BROADCAST,MULTICAST> mtu 1500 qdisc noqueue master docker0 state DOWN group default link/ether 22:e7:68:f2:d7:6c brd ff:ff:ff:ff:ff:ff Deleted fe80::/64 dev veth4d73cef proto kernel metric 256 linkdown pref medium Deleted local fe80::20e7:68ff:fef2:d76c dev veth4d73cef table local proto kernel metric 0 pref medium Deleted ff00::/8 dev veth4d73cef table local metric 256 linkdown pref medium Deleted 458: veth4d73cef inet6 fe80::20e7:68ff:fef2:d76c/64 scope link valid_lft forever preferred_lft forever 458: veth4d73cef@NONE: <BROADCAST,MULTICAST> mtu 1500 master docker0 state DOWN link/ether 22:e7:68:f2:d7:6c Unknown message: type=0x00000051(81) flags=0x00000000(0)len=0x0000001c(28) Unknown message: type=0x00000051(81) flags=0x00000000(0)len=0x0000001c(28) Deleted 457: vethd6c94e3@NONE: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default link/ether 02:42:ac:11:00:04 brd ff:ff:ff:ff:ff:ff Unknown message: type=0x00000051(81) flags=0x00000000(0)len=0x0000001c(28) Unknown message: type=0x00000051(81) flags=0x00000000(0)len=0x0000001c(28) 458: veth4d73cef@NONE: <BROADCAST,MULTICAST> mtu 1500 master docker0 state DOWN link/ether 22:e7:68:f2:d7:6c Deleted 458: veth4d73cef@NONE: <BROADCAST,MULTICAST> mtu 1500 master docker0 state DOWN link/ether 22:e7:68:f2:d7:6c Deleted dev if458 lladdr 22:e7:68:f2:d7:6c PERMANENT Deleted dev if458 lladdr 22:e7:68:f2:d7:6c PERMANENT Deleted 458: veth4d73cef@NONE: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default link/ether 22:e7:68:f2:d7:6c brd ff:ff:ff:ff:ff:ff Deleted nsid 12 (iproute2 netns name: cnitest-09c30c1b-181d-0f74-8798-2a11ba01c014) ipv4 dev vethfab7edb forwarding on rp_filter strict mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off ipv6 dev vethfab7edb forwarding off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off 459: vethfab7edb@NONE: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default link/ether ca:0d:1a:c6:d2:f5 brd ff:ff:ff:ff:ff:ff ipv4 dev veth51ec210 forwarding on rp_filter strict mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off ipv6 dev veth51ec210 forwarding off mc_forwarding off proxy_neigh off ignore_routes_with_linkdown off 460: veth51ec210@vethfab7edb: <BROADCAST,MULTICAST,M-DOWN> mtu 1500 qdisc noop state DOWN group default link/ether 02:44:61:7d:bd:3f brd ff:ff:ff:ff:ff:ff 460: veth51ec210@vethfab7edb: <BROADCAST,MULTICAST,M-DOWN> mtu 1500 qdisc noop master docker0 state DOWN group default link/ether 02:44:61:7d:bd:3f brd ff:ff:ff:ff:ff:ff 460: veth51ec210@vethfab7edb: <BROADCAST,MULTICAST,M-DOWN> mtu 1500 qdisc noop master docker0 state DOWN group default link/ether 02:44:61:7d:bd:3f brd ff:ff:ff:ff:ff:ff dev veth51ec210 lladdr 02:44:61:7d:bd:3f PERMANENT dev veth51ec210 lladdr 02:44:61:7d:bd:3f PERMANENT 460: veth51ec210@vethfab7edb: <BROADCAST,MULTICAST,M-DOWN> mtu 1500 master docker0 state DOWN link/ether 02:44:61:7d:bd:3f 460: veth51ec210@vethfab7edb: <NO-CARRIER,BROADCAST,MULTICAST,UP,M-DOWN> mtu 1500 qdisc noqueue master docker0 state LOWERLAYERDOWN group default link/ether 02:44:61:7d:bd:3f brd ff:ff:ff:ff:ff:ff 460: veth51ec210@vethfab7edb: <NO-CARRIER,BROADCAST,MULTICAST,UP,M-DOWN> mtu 1500 master docker0 state LOWERLAYERDOWN link/ether 02:44:61:7d:bd:3f Unknown message: type=0x00000051(81) flags=0x00000000(0)len=0x0000001c(28) Unknown message: type=0x00000051(81) flags=0x00000000(0)len=0x0000001c(28) nsid 12 (iproute2 netns name: cnitest-66749d86-4baa-dc15-d273-a4feefc88a8c) Deleted 459: vethfab7edb@veth51ec210: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default link/ether ca:0d:1a:c6:d2:f5 brd ff:ff:ff:ff:ff:ff ff00::/8 dev veth51ec210 table local metric 256 pref medium fe80::/64 dev veth51ec210 proto kernel metric 256 pref medium 460: veth51ec210@if459: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master docker0 state UP link/ether 02:44:61:7d:bd:3f 460: veth51ec210@if459: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master docker0 state UP link/ether 02:44:61:7d:bd:3f 460: veth51ec210@if459: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master docker0 state UP group default link/ether 02:44:61:7d:bd:3f brd ff:ff:ff:ff:ff:ff link-netnsid 12 460: veth51ec210 inet6 fe80::44:61ff:fe7d:bd3f/64 scope link valid_lft forever preferred_lft forever local fe80::44:61ff:fe7d:bd3f dev veth51ec210 table local proto kernel metric 0 pref medium dev veth51ec210 lladdr 02:42:ac:11:00:04 REACHABLE 460: veth51ec210@if459: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 master docker0 state UP link/ether 02:44:61:7d:bd:3f
root@ubuntu:/home/ubuntu# docker run -it --runtime=kata-runtime --rm debian /bin/bash root@d36cbb25f4ff:/# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000 link/ether 02:42:ac:11:00:04 brd ff:ff:ff:ff:ff:ff inet 172.17.0.4/16 brd 172.17.255.255 scope global eth0 valid_lft forever preferred_lft forever inet6 fe80::42:acff:fe11:4/64 scope link valid_lft forever preferred_lft forever root@d36cbb25f4ff:/#
root@ubuntu:/home/ubuntu# docker run -it --runtime=kata-runtime --rm debian /bin/bash root@d36cbb25f4ff:/# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000 link/ether 02:42:ac:11:00:04 brd ff:ff:ff:ff:ff:ff inet 172.17.0.4/16 brd 172.17.255.255 scope global eth0 valid_lft forever preferred_lft forever inet6 fe80::42:acff:fe11:4/64 scope link valid_lft forever preferred_lft forever root@d36cbb25f4ff:/#
vendor/github.com/vishvananda/netlink/link.go
func (macvtap Macvtap) Type() string { return "macvtap" }
// the contents of stderr + a Go error object will be returned. func LaunchCustomQemu(ctx context.Context, path string, params []string, fds []*os.File, attr *syscall.SysProcAttr, logger QMPLog) (string, error) { if logger == nil { logger = qmpNullLogger{} } errStr := "" if path == "" { path = "qemu-system-x86_64" } /* #nosec */ cmd := exec.CommandContext(ctx, path, params...) if len(fds) > 0 { logger.Infof("Adding extra file %v", fds) cmd.ExtraFiles = fds } cmd.SysProcAttr = attr var stderr bytes.Buffer cmd.Stderr = &stderr logger.Infof("launching %s with: %v", path, params) err := cmd.Run() if err != nil { logger.Errorf("Unable to launch %s: %v", path, err) errStr = stderr.String() logger.Errorf("%s", errStr) } return errStr, err }
// ExecuteNetPCIDeviceAdd adds a Net PCI device to a QEMU instance // using the device_add command. devID is the id of the device to add. // Must be valid QMP identifier. netdevID is the id of nic added by previous netdev_add. // queues is the number of queues of a nic. // disableModern indicates if virtio version 1.0 should be replaced by the // former version 0.9, as there is a KVM bug that occurs when using virtio // 1.0 in nested environments. func (q *QMP) ExecuteNetPCIDeviceAdd(ctx context.Context, netdevID, devID, macAddr, addr, bus, romfile string, queues int, disableModern bool) error { args := map[string]interface{}{ "id": devID, "driver": VirtioNetPCI, "romfile": romfile, } if bus != "" { args["bus"] = bus } if addr != "" { args["addr"] = addr } if macAddr != "" { args["mac"] = macAddr } if netdevID != "" { args["netdev"] = netdevID } if disableModern { args["disable-modern"] = disableModern } if queues > 0 { // (2N+2 vectors, N for tx queues, N for rx queues, 1 for config, and one for possible control vq) // -device virtio-net-pci,mq=on,vectors=2N+2... // enable mq in guest by 'ethtool -L eth0 combined $queue_num' // Clearlinux automatically sets up the queues properly // The agent implementation should do this to ensure that it is // always set args["mq"] = "on" args["vectors"] = 2*queues + 2 } return q.executeCommand(ctx, "device_add", args, nil) }
qemu log
func (q *qemu) qmpSetup() error { q.qmpMonitorCh.Lock() defer q.qmpMonitorCh.Unlock() if q.qmpMonitorCh.qmp != nil { return nil } cfg := govmmQemu.QMPConfig{Logger: newQMPLogger()} // Auto-closed by QMPStart(). disconnectCh := make(chan struct{}) qmp, _, err := govmmQemu.QMPStart(q.qmpMonitorCh.ctx, q.qmpMonitorCh.path, cfg, disconnectCh) if err != nil { q.Logger().WithError(err).Error("Failed to connect to QEMU instance") return err } err = qmp.ExecuteQMPCapabilities(q.qmpMonitorCh.ctx) if err != nil { qmp.Shutdown() q.Logger().WithError(err).Error(qmpCapErrMsg) return err } q.qmpMonitorCh.qmp = qmp q.qmpMonitorCh.disconn = disconnectCh return nil }
资源调度 root@ubuntu:/home/ubuntu# ip netns list cnitest-8239ee00-551b-e7ae-13e0-5ef90a69e209 (id: 11) cnitest-05f3b567-6bd0-20ba-d46d-5ec15a5b45aa (id: 10) cnitest-9785e05f-2059-be24-a15f-2532e9c2f98a (id: 9) cnitest-b64a9add-17e3-f0a8-0707-34794d88e0ad (id: 8) cnitest-4404972b-aaed-d970-d9eb-94d88f872123 (id: 7) cnitest-70ddbd3e-be65-f6f6-e957-c131fa4f53c9 (id: 6) cnitest-f32920e0-cdea-3f98-ff4e-9400be0ac9ad (id: 5) net1 cnitest-b790a304-2e67-96a8-392e-b1d5a81214c8 (id: 4) cni-2ee1cfcd-88b0-32cb-377e-44eab39aedab (id: 2) cni-5ac8f964-785c-b80f-c79d-a9938235a3b3 (id: 3) cni-3c0b6c7f-edd4-e3ff-24d3-8f18eac4522a (id: 0) cni-9f34f2b5-d9bf-f889-d889-727c796b03bf (id: 1) 执行docker run -it --runtime=kata-runtime --rm debian /bin/bash 新增一个cnitest-336d3dd8-2913-e023-a3d0-1ac7ef9fed0f (id: 12) root@ubuntu:/home/ubuntu# ip netns list cnitest-336d3dd8-2913-e023-a3d0-1ac7ef9fed0f (id: 12) cnitest-8239ee00-551b-e7ae-13e0-5ef90a69e209 (id: 11) cnitest-05f3b567-6bd0-20ba-d46d-5ec15a5b45aa (id: 10) cnitest-9785e05f-2059-be24-a15f-2532e9c2f98a (id: 9) cnitest-b64a9add-17e3-f0a8-0707-34794d88e0ad (id: 8) cnitest-4404972b-aaed-d970-d9eb-94d88f872123 (id: 7) cnitest-70ddbd3e-be65-f6f6-e957-c131fa4f53c9 (id: 6) cnitest-f32920e0-cdea-3f98-ff4e-9400be0ac9ad (id: 5) net1 cnitest-b790a304-2e67-96a8-392e-b1d5a81214c8 (id: 4) cni-2ee1cfcd-88b0-32cb-377e-44eab39aedab (id: 2) cni-5ac8f964-785c-b80f-c79d-a9938235a3b3 (id: 3) cni-3c0b6c7f-edd4-e3ff-24d3-8f18eac4522a (id: 0) cni-9f34f2b5-d9bf-f889-d889-727c796b03bf (id: 1) root@ubuntu:/home/ubuntu# ip netns exec cnitest-336d3dd8-2913-e023-a3d0-1ac7ef9fed0f bash root@ubuntu:/home/ubuntu# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever 2: tap0_kata: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UNKNOWN group default qlen 1000 link/ether c6:dd:7e:49:09:24 brd ff:ff:ff:ff:ff:ff 461: eth0@if462: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether 02:42:ac:11:00:04 brd ff:ff:ff:ff:ff:ff link-netnsid 0 inet 172.17.0.4/16 brd 172.17.255.255 scope global eth0 valid_lft forever preferred_lft forever root@ubuntu:/home/ubuntu# ========================================================= root@ubuntu:/home/ubuntu# ip netns list cnitest-d4eb6e94-4f75-f2b8-20c3-56cdb6b98803 (id: 13) cnitest-8239ee00-551b-e7ae-13e0-5ef90a69e209 (id: 11) cnitest-05f3b567-6bd0-20ba-d46d-5ec15a5b45aa (id: 10) cnitest-9785e05f-2059-be24-a15f-2532e9c2f98a (id: 9) cnitest-b64a9add-17e3-f0a8-0707-34794d88e0ad (id: 8) cnitest-4404972b-aaed-d970-d9eb-94d88f872123 (id: 7) cnitest-70ddbd3e-be65-f6f6-e957-c131fa4f53c9 (id: 6) cnitest-f32920e0-cdea-3f98-ff4e-9400be0ac9ad (id: 5) net1 cnitest-b790a304-2e67-96a8-392e-b1d5a81214c8 (id: 4) cni-2ee1cfcd-88b0-32cb-377e-44eab39aedab (id: 2) cni-5ac8f964-785c-b80f-c79d-a9938235a3b3 (id: 3) cni-3c0b6c7f-edd4-e3ff-24d3-8f18eac4522a (id: 0) cni-9f34f2b5-d9bf-f889-d889-727c796b03bf (id: 1) root@ubuntu:/home/ubuntu# ip netns exec cnitest-d4eb6e94-4f75-f2b8-20c3-56cdb6b98803 bash root@ubuntu:/home/ubuntu# ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever 2: tap0_kata: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UNKNOWN group default qlen 1000 link/ether 8e:3b:c7:65:28:b9 brd ff:ff:ff:ff:ff:ff 463: eth0@if464: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether 02:42:ac:11:00:04 brd ff:ff:ff:ff:ff:ff link-netnsid 0 inet 172.17.0.4/16 brd 172.17.255.255 scope global eth0 valid_lft forever preferred_lft forever root@ubuntu:/home/ubuntu# ip netns list cnitest-d4eb6e94-4f75-f2b8-20c3-56cdb6b98803 cnitest-8239ee00-551b-e7ae-13e0-5ef90a69e209 cnitest-05f3b567-6bd0-20ba-d46d-5ec15a5b45aa cnitest-9785e05f-2059-be24-a15f-2532e9c2f98a cnitest-b64a9add-17e3-f0a8-0707-34794d88e0ad cnitest-4404972b-aaed-d970-d9eb-94d88f872123 cnitest-70ddbd3e-be65-f6f6-e957-c131fa4f53c9 cnitest-f32920e0-cdea-3f98-ff4e-9400be0ac9ad net1 cnitest-b790a304-2e67-96a8-392e-b1d5a81214c8 cni-2ee1cfcd-88b0-32cb-377e-44eab39aedab cni-5ac8f964-785c-b80f-c79d-a9938235a3b3 cni-3c0b6c7f-edd4-e3ff-24d3-8f18eac4522a cni-9f34f2b5-d9bf-f889-d889-727c796b03bf root@ubuntu:/home/ubuntu# exit exit root@ubuntu:/home/ubuntu# ip a | grep 02:42:ac:11:00:04 root@ubuntu:/home/ubuntu# ip a | grep 8e:3b:c7:65:28:b9 root@ubuntu:/home/ubuntu# ========================================================== root@ubuntu:/home/ubuntu# ip netns list cnitest-26d36f03-aca6-72cf-aa44-815781daf4d8 (id: 12) cnitest-8239ee00-551b-e7ae-13e0-5ef90a69e209 (id: 11) cnitest-05f3b567-6bd0-20ba-d46d-5ec15a5b45aa (id: 10) cnitest-9785e05f-2059-be24-a15f-2532e9c2f98a (id: 9) cnitest-b64a9add-17e3-f0a8-0707-34794d88e0ad (id: 8) cnitest-4404972b-aaed-d970-d9eb-94d88f872123 (id: 7) cnitest-70ddbd3e-be65-f6f6-e957-c131fa4f53c9 (id: 6) cnitest-f32920e0-cdea-3f98-ff4e-9400be0ac9ad (id: 5) net1 cnitest-b790a304-2e67-96a8-392e-b1d5a81214c8 (id: 4) cni-2ee1cfcd-88b0-32cb-377e-44eab39aedab (id: 2) cni-5ac8f964-785c-b80f-c79d-a9938235a3b3 (id: 3) cni-3c0b6c7f-edd4-e3ff-24d3-8f18eac4522a (id: 0) cni-9f34f2b5-d9bf-f889-d889-727c796b03bf (id: 1) root@ubuntu:/home/ubuntu# ip netns exec cnitest-26d36f03-aca6-72cf-aa44-815781daf4d8 ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever 2: tap0_kata: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UNKNOWN group default qlen 1000 link/ether 52:80:79:d2:eb:7a brd ff:ff:ff:ff:ff:ff 465: eth0@if466: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000 link/ether 02:42:ac:11:00:04 brd ff:ff:ff:ff:ff:ff link-netnsid 0 inet 172.17.0.4/16 brd 172.17.255.255 scope global eth0 valid_lft forever preferred_lft forever root@ubuntu:/home/ubuntu# ip a | grep 465 466: vethd1b8694@if465: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master docker0 state UP group default root@ubuntu:/home/ubuntu# 容器退出后,465没有了 root@ubuntu:/home/ubuntu# ip a | grep 465 root@ubuntu:/home/ubuntu# ========================================================== root@ubuntu:/home/ubuntu# ip a | wc -l 84 root@ubuntu:/home/ubuntu# ip a | wc -l 80 root@ubuntu:/home/ubuntu# =========================================================== vendor/github.com/vishvananda/netlink/link_linux.go:674:// Equivalent to: `ip link set $link netns $pid` vendor/github.com/vishvananda/netlink/link_linux.go:681:// Equivalent to: `ip link set $link netns $pid` vendor/github.com/vishvananda/netlink/link_linux.go:703:// Similar to: `ip link set $link netns $ns` vendor/github.com/vishvananda/netlink/link_linux.go:710:// Similar to: `ip link set $link netns $ns` vendor/github.com/vishvananda/netns/netns_linux.go:79:// created by `ip netns add`. =========================================================== ip link add link eth0 name macvtap0 type macvtap ip link set macvtap0 address 1a:46:0b:ca:bc:7b up bash-4.2# cat /sys/class/net/macvtap0/ifindex 2 bash-4.2# cat /sys/class/net/macvtap0/address 1a:46:0b:ca:bc:7b bash-4.2# qemu-system-x86_64 -enable-kvm centos.qcow2 -cdrom CentOS-7-x86_64-Minimal-1810.iso -net nic,model=virtio,macaddr=1a:46:0b:ca:bc:7b -net tap,fd=3 3<>/dev/tap2 -daemonize -monitor telnet:127.0.0.1:5801,server,nowait qemu-system-x86_64: -net tap,fd=3: TUNGETIFF ioctl() failed: Inappropriate ioctl for device TUNSETOFFLOAD ioctl() failed: Inappropriate ioctl for device VNC server running on ::1:5900
Nov 26 15:37:27 ubuntu kata-runtime[36082]: time="2020-11-26T15:37:27.750500481+08:00" level=info msg="Attaching endpoint"
arch=arm64 command=create container=7979de1f27280b9815b6d7bf3f4dc379f37d4ad1891ba7a1eb8088c941d72ae6 endpoint-type=virtual hotplug=false name=kata-runtime pid=36082 source=virtcontainers subsystem=network
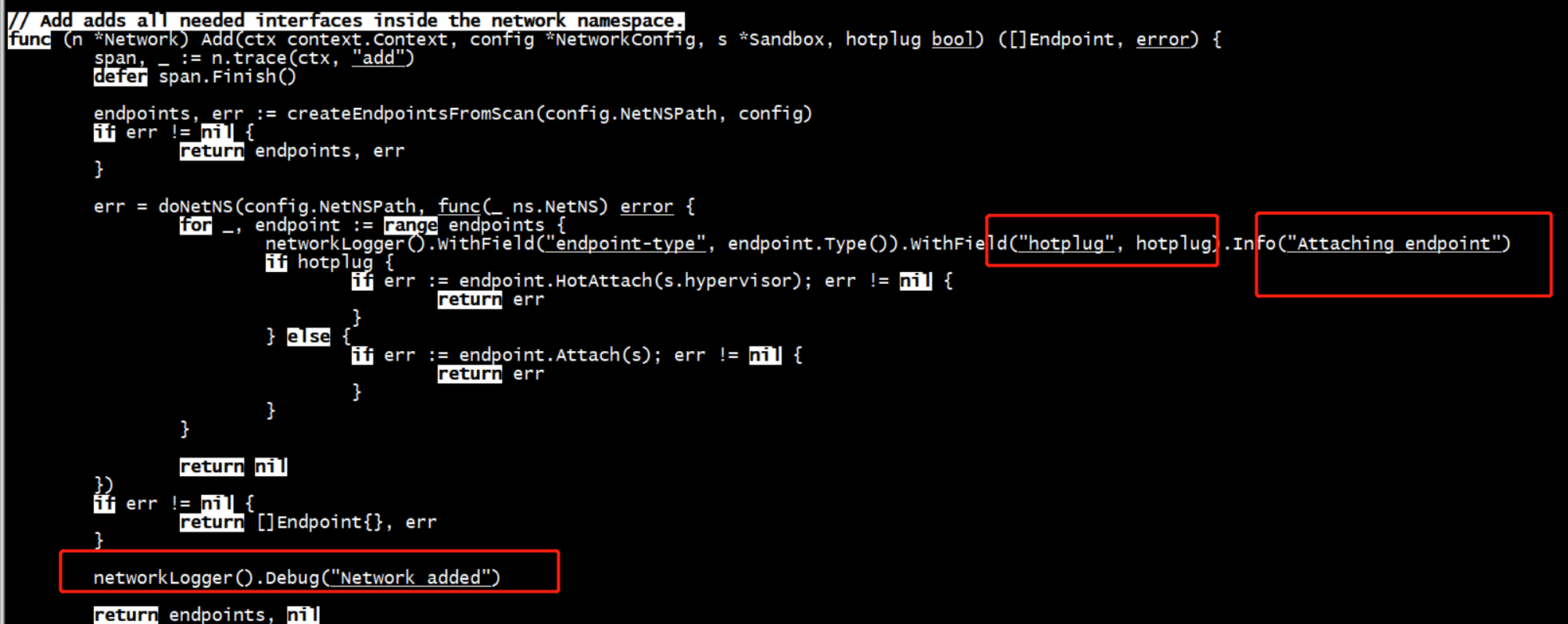
func (n *Network) Add(ctx context.Context, config *NetworkConfig, s *Sandbox, hotplug bool) ([]Endpoint, error) {
tap_endpoint
virtcontainers/tap_endpoint.go:144: tapLink, fds, err := createLink(netHandle, endpoint.TapInterface.TAPIface.Name, &netlink.Tuntap{}, int(numCPUs)) virtcontainers/tuntap_endpoint.go:157: tapLink, _, err := createLink(netHandle, endpoint.TuntapInterface.TAPIface.Name, &netlink.Tuntap{}, int(numCPUs))
attach
// Attach for tap endpoint adds the tap interface to the hypervisor. func (endpoint *TuntapEndpoint) Attach(s *Sandbox) error { h := s.hypervisor if err := xConnectVMNetwork(endpoint, h); err != nil { networkLogger().WithError(err).Error("Error bridging virtual endpoint") return err } return h.addDevice(endpoint, netDev) } // Detach for the tap endpoint tears down the tap func (endpoint *TuntapEndpoint) Detach(netNsCreated bool, netNsPath string) error { if !netNsCreated && netNsPath != "" { return nil } networkLogger().WithField("endpoint-type", TuntapEndpointType).Info("Detaching endpoint") return doNetNS(netNsPath, func(_ ns.NetNS) error { return unTuntapNetwork(endpoint.TuntapInterface.TAPIface.Name) }) }
xConnectVMNetwork
virtcontainers/network.go:410:func xConnectVMNetwork(endpoint Endpoint, h hypervisor) error { virtcontainers/veth_endpoint.go:92: if err := xConnectVMNetwork(endpoint, h); err != nil { virtcontainers/veth_endpoint.go:116: if err := xConnectVMNetwork(endpoint, h); err != nil { virtcontainers/bridgedmacvlan_endpoint.go:89: if err := xConnectVMNetwork(endpoint, h); err != nil { virtcontainers/tuntap_endpoint.go:71: if err := xConnectVMNetwork(endpoint, h); err != nil { virtcontainers/ipvlan_endpoint.go:92: if err := xConnectVMNetwork(endpoint, h); err != nil {
// The endpoint type should dictate how the connection needs to happen. func xConnectVMNetwork(endpoint Endpoint, h hypervisor) error { netPair := endpoint.NetworkPair() queues := 0 caps := h.capabilities() if caps.IsMultiQueueSupported() { queues = int(h.hypervisorConfig().NumVCPUs) } var disableVhostNet bool if rootless.IsRootless() { disableVhostNet = true } else { disableVhostNet = h.hypervisorConfig().DisableVhostNet } if netPair.NetInterworkingModel == NetXConnectDefaultModel { netPair.NetInterworkingModel = DefaultNetInterworkingModel } switch netPair.NetInterworkingModel { case NetXConnectMacVtapModel: return tapNetworkPair(endpoint, queues, disableVhostNet) case NetXConnectTCFilterModel: return setupTCFiltering(endpoint, queues, disableVhostNet) default: return fmt.Errorf("Invalid internetworking model") } }
func setupTCFiltering(endpoint Endpoint, queues int, disableVhostNet bool)

// The endpoint type should dictate how the connection needs to happen. func xConnectVMNetwork(endpoint Endpoint, h hypervisor) error { netPair := endpoint.NetworkPair() queues := 0 caps := h.capabilities() if caps.IsMultiQueueSupported() { queues = int(h.hypervisorConfig().NumVCPUs) } var disableVhostNet bool if rootless.IsRootless() { disableVhostNet = true } else { disableVhostNet = h.hypervisorConfig().DisableVhostNet } if netPair.NetInterworkingModel == NetXConnectDefaultModel { netPair.NetInterworkingModel = DefaultNetInterworkingModel } switch netPair.NetInterworkingModel { case NetXConnectMacVtapModel: return tapNetworkPair(endpoint, queues, disableVhostNet) case NetXConnectTCFilterModel: return setupTCFiltering(endpoint, queues, disableVhostNet) default: return fmt.Errorf("Invalid internetworking model") } }