安装可以参考 https://wiki.openwrt.org/doc/howto/wireless.hotspot.nodogsplash
安装注意事项:
0. Free wifi 路由器wan口连接到内网,分开两个网段连接
1. 如果使用Chaos 15.05系统时,最好能安装nodogsplash 0.9_beta9.9.8-2,最新版本没有研究好,据说redirectURL时会出现问题
2. 可以保留firewall,不需要另外使用iptables
3. 主要配置文件nodogsplash.conf里面GatewayInterface 应该为开放给客户使用的端口wlan0-1
4. 如果不想免费客户端链接路由器的话,在nodogsplash.conf配置 users-to-router block掉80端口和22端口
5. 如果重启/etc/init.d/nodogsplash 服务时,出现找不到配置文件等错误提示,代表配置文件有问题
6. 通过ndsctl status命令来观察使用情况
7. 防火墙配置: 主要屏蔽Free_Wifi访问 wan的网段,即防止Free wifi用登陆到对工作网段
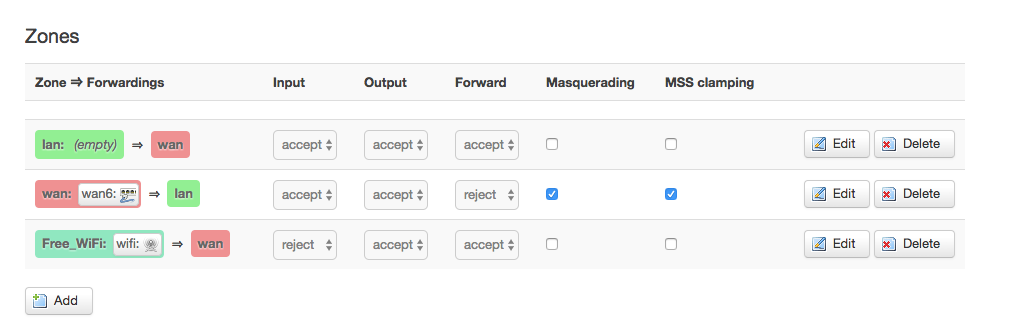
配置文件参考:
crontab参考:
30 10 * * 0,2,3,4,5,6 wifi up 31 10 * * 0,2,3,4,5,6 /etc/init.d/nodogsplash restart 30 23 * * 0,2,3,4,5,6 wifi down
登陆html文件参考:
<html> <head> <title>$gatewayname Entry</title> <meta HTTP-EQUIV="Pragma" CONTENT="no-cache"> </head> <body bgcolor="#DDDDDD" text="#000000"> <table border="0" cellpadding="2" cellspacing="0" align="center" width="70%"> <tr> <td align="center"><h2>$gatewayname</h2></td> </tr> <tr> <td align="center" height="120"> <img src="wifi.jpg" /> </td> </tr> <tr> <td align="center" height="120"> <h2>Limitations & Disclaimers</h2> </td> </tr> <tr> <td> <ul> <li>Wireless access is provided as a public service free of charge on an as-is basis with no guarantee and no warranty. The KIO Ramen Wireless network is subject to periodic maintenance and unforeseen downtime</li> <li>Information passing through the KIO Ramen wireless access is not secured and could be monitored, captured, or altered by others. There are risks involved with connecting to a public wireless connection, such as possible viruses, malware, loss of data, possible hacking/snooping by others connected, possible hardware/software failure. It is your sole responsibility to protect your information from all risks associated with using the Internet, including any damage, loss, or theft that may occur as a result of your use of the KIO Ramen wireless access.</li> <li>All Wi-Fi users should have up-to-date antivirus software installed on their device.</li> <li>In using this free Internet access, you agree and hereby release, indemnify, and hold harmless, the KIO Ramen from any damage that may result from your use of this wireless access.</li> <li>While using this wireless access, you acknowledge that you are subject to, and agree to abide by all laws, and all rules and regulations of the City San Francisco, the State of California, and the federal government that is applicable to Internet use.</li> <li>At its sole discretion, the KIO Ramen may terminate this public service at anytime without prior notice.</li> <li>Due to limited bandwidth, during peak hours KIO Ramen staff may limit the type of internet use.</li> <li>Any attempt to circumvent KIO Ramen procedures or any unauthorized attempt to access or manipulate KIO Ramen equipment will result in permanent disconnection from the KIO Ramen’s Wi-Fi network.</li> <li>If you do not agree to the above terms, please disable your wireless connection or turn off your computer.</li> </ul> </td> </tr> <tr> <td align="center" height="120"> <!-- A client is authenticated by requesting the page $authtarget. So, href to it here, with an img or link text the user can click on. Also, note that any images you reference must reside in the subdirectory that is the value of $imagesdir (default: "images"). <a href="$authtarget"> <img src="$imagesdir/splash.jpg" width="71" height="49" border="0" alt="Click to enter" title="Click to enter"> </a> --> <form method='GET' action='$authaction'> <input type='hidden' name='tok' value='$tok'> <input type='hidden' name='redir' value='$redir'> <input type='submit' style="font-size:16px" value='I agree'> </form> </td> </tr> </table> </body> </html>
Nodongsplash配置文件参考:
#
# Nodogsplash Configuration File
#
# Parameter: GatewayInterface
# Default: NONE
#
# GatewayInterface is not autodetected, has no default, and must be set here.
# Set GatewayInterface to the interface on your router
# that is to be managed by Nodogsplash.
# Typically br0 for the wired and wireless lan on OpenWrt White Russian.
# May be br-lan on OpenWrt Kamikaze.
#
GatewayInterface wlan0-1
# FirewallRuleSet: authenticated-users
#
# Control access for users after authentication.
# These rules are inserted at the beginning of the
# FORWARD chain of the router's filter table, and
# apply to packets that have come in to the router
# over the GatewayInterface from MAC addresses that
# have authenticated with Nodogsplash, and that are
# destined to be routed through the router. The rules are
# considered in order, and the first rule that matches
# a packet applies to it.
# If there are any rules in this ruleset, an authenticated
# packet that does not match any rule is rejected.
# N.B.: This ruleset is completely independent of
# the preauthenticated-users ruleset.
#
FirewallRuleSet authenticated-users {
# You may want to open access to a machine on a local
# subnet that is otherwise blocked (for example, to
# serve a redirect page; see RedirectURL). If so,
# allow that explicitly here, e.g:
# FirewallRule allow tcp port 80 to 192.168.254.254
# Your router may have several interfaces, and you
# probably want to keep them private from the GatewayInterface.
# If so, you should block the entire subnets on those interfaces, e.g.:
# FirewallRule block to 192.168.0.0/16
# FirewallRule block to 10.0.0.0/8
# Typical ports you will probably want to open up include
# 53 udp and tcp for DNS,
# 80 for http,
# 443 for https,
# 22 for ssh:
# FirewallRule allow tcp port 53
# FirewallRule allow udp port 53
# FirewallRule allow tcp port 80
# FirewallRule allow tcp port 443
# FirewallRule allow tcp port 22
FirewallRule allow all
}
# end FirewallRuleSet authenticated-users
# FirewallRuleSet: preauthenticated-users
#
# Control access for users before authentication.
# These rules are inserted in the PREROUTING chain
# of the router's nat table, and in the
# FORWARD chain of the router's filter table.
# These rules apply to packets that have come in to the
# router over the GatewayInterface from MAC addresses that
# are not on the BlockedMACList or TrustedMACList,
# are *not* authenticated with Nodogsplash. The rules are
# considered in order, and the first rule that matches
# a packet applies to it. A packet that does not match
# any rule here is rejected.
# N.B.: This ruleset is completely independent of
# the authenticated-users and users-to-router rulesets.
#
FirewallRuleSet preauthenticated-users {
# For preauthenticated users to resolve IP addresses in their initial
# request not using the router itself as a DNS server,
# you probably want to allow port 53 udp and tcp for DNS.
FirewallRule allow tcp port 53
FirewallRule allow udp port 53
# For splash page content not hosted on the router, you
# will want to allow port 80 tcp to the remote host here.
# Doing so circumvents the usual capture and redirect of
# any port 80 request to this remote host.
# Note that the remote host's numerical IP address must be known
# and used here.
# FirewallRule allow tcp port 80 to 123.321.123.321
}
# end FirewallRuleSet preauthenticated-users
# FirewallRuleSet: users-to-router
#
# Control access to the router itself from the GatewayInterface.
# These rules are inserted at the beginning of the
# INPUT chain of the router's filter table, and
# apply to packets that have come in to the router
# over the GatewayInterface from MAC addresses that
# are not on the TrustedMACList, and are destined for
# the router itself. The rules are
# considered in order, and the first rule that matches
# a packet applies to it.
# If there are any rules in this ruleset, a
# packet that does not match any rule is rejected.
#
FirewallRuleSet users-to-router {
# Nodogsplash automatically allows tcp to GatewayPort,
# at GatewayAddress, to serve the splash page.
# However you may want to open up other ports, e.g.
# 53 for DNS and 67 for DHCP if the router itself is
# providing these services.
FirewallRule allow udp port 53
FirewallRule allow tcp port 53
FirewallRule allow udp port 67
# You may want to allow ssh, http, and https to the router
# for administration from the GatewayInterface. If not,
# comment these out.
# FirewallRule allow tcp port 22
FirewallRule allow tcp port 23
# FirewallRule allow tcp port 80
FirewallRule allow tcp port 443
}
# end FirewallRuleSet users-to-router
# EmptyRuleSetPolicy directives
# The FirewallRuleSets that NoDogSplash permits are:
#
# authenticated-users
# preauthenticated-users
# users-to-router
# trusted-users
# trusted-users-to-router
#
# For each of these, an EmptyRuleSetPolicy can be specified.
# An EmptyRuleSet policy applies to a FirewallRuleSet if the
# FirewallRuleSet is missing from this configuration file,
# or if it exists but contains no FirewallRules.
#
# The possible values of an EmptyRuleSetPolicy are:
# allow -- packets are accepted
# block -- packets are rejected
# passthrough -- packets are passed through to pre-existing firewall rules
#
# Default EmptyRuleSetPolicies are set as follows:
# EmptyRuleSetPolicy authenticated-users passthrough
# EmptyRuleSetPolicy preauthenticated-users block
# EmptyRuleSetPolicy users-to-router block
# EmptyRuleSetPolicy trusted-users allow
# EmptyRuleSetPolicy trusted-users-to-router allow
# Parameter: GatewayName
# Default: NoDogSplash
#
# Set GatewayName to the name of your gateway. This value
# will be available as variable $gatewayname in the splash page source
# and in status output from ndsctl, but otherwise doesn't matter.
# If none is supplied, the value "NoDogSplash" is used.
#
# GatewayName NoDogSplash
# Parameter: GatewayAddress
# Default: Discovered from GatewayInterface
#
# This should be autodetected on an OpenWRT system, but if not:
# Set GatewayAddress to the IP address of the router on
# the GatewayInterface. This is the address that the Nodogsplash
# server listens on.
#
# GatewayAddress 192.168.1.1
# Parameter: ExternalInterface
# Default: Autodetected from /proc/net/route
#
# This should be autodetected on a OpenWRT system, but if not:
# Set ExtrnalInterface to the 'external' interface on your router,
# i.e. the one which provides the default route to the internet.
# Typically vlan1 for OpenWRT.
#
# ExternalInterface vlan1
# Parameter: RedirectURL
# Default: none
#
# After authentication, normally a user is redirected
# to their initially requested page.
# If RedirectURL is set, the user is redirected to this URL instead.
#
# RedirectURL http://www.ilesansfil.org/
# Parameter: GatewayPort
# Default: 2050
#
# Nodogsplash's own http server uses GatewayAddress as its IP address.
# The port it listens to at that IP can be set here; default is 2050.
#
# GatewayPort 2050
# Parameter: MaxClients
# Default: 20
#
# Set MaxClients to the maximum number of users allowed to
# connect at any time. (Does not include users on the TrustedMACList,
# who do not authenticate.)
#
# MaxClients 20
# ClientIdleTimeout
# Parameter: ClientIdleTimeout
# Default: 10
#
# Set ClientIdleTimeout to the desired of number of minutes
# of inactivity before a user is automatically 'deauthenticated'.
#
ClientIdleTimeout 15
# Parameter: ClientForceTimeout
# Default: 360
#
# Set ClientForceTimeout to the desired number of minutes before
# a user is automatically 'deauthenticated', whether active or not
#
ClientForceTimeout 30
# Parameter: AuthenticateImmediately
# Default: no
#
# Set to yes (or true or 1), to immediately authenticate users
# who make a http port 80 request on the GatewayInterface (that is,
# do not serve a splash page, just redirect to the user's request,
# or to RedirectURL if set).
#
# AuthenticateImmediately no
# Parameter: MACMechanism
# Default: block
#
# Either block or allow.
# If 'block', MAC addresses on BlockedMACList are blocked from
# authenticating, and all others are allowed.
# If 'allow', MAC addresses on AllowedMACList are allowed to
# authenticate, and all other (non-trusted) MAC's are blocked.
#
# MACMechanism block
# Parameter: BlockedMACList
# Default: none
#
# Comma-separated list of MAC addresses who will be completely blocked
# from the GatewayInterface. Ignored if MACMechanism is allow.
# N.B.: weak security, since MAC addresses are easy to spoof.
#
# BlockedMACList 00:00:DE:AD:BE:EF,00:00:C0:1D:F0:0D
# Parameter: AllowedMACList
# Default: none
#
# Comma-separated list of MAC addresses who will not be completely
# blocked from the GatewayInterface. Ignored if MACMechanism is block.
# N.B.: weak security, since MAC addresses are easy to spoof.
#
# AllowedMACList 00:00:12:34:56:78
# Parameter: TrustedMACList
# Default: none
#
# Comma-separated list of MAC addresses who are not subject to
# authentication, and are not restricted by any FirewallRuleSet.
# N.B.: weak security, since MAC addresses are easy to spoof.
#
# TrustedMACList 00:00:CA:FE:BA:BE, 00:00:C0:01:D0:0D
# Parameter: PasswordAuthentication
# Default: no
# Set to yes (or true or 1), to require a password matching
# the Password parameter to be supplied when authenticating.
#
#
# PasswordAuthentication no
# Parameter: Password
# Default: none
# Whitespace delimited string that is compared to user-supplied
# password when authenticating.
#
#
# Password nodog
# Parameter: UsernameAuthentication
# Default: no
# Set to yes (or true or 1), to require a username matching
# the Username parameter to be supplied when authenticating.
#
#
# UsernameAuthentication no
# Parameter: Username
# Default: none
# Whitespace delimited string that is compared to user-supplied
# username when authenticating.
#
#
# Username guest
# Parameter: PasswordAttempts
# Default: 5
# Integer number of failed password/username entries before
# a user is forced to reauthenticate.
#
#
# PasswordAttempts 5
# Parameter: TrafficControl
# Default: no
#
# Set to yes (or true or 1), to enable traffic control in Nodogsplash.
#
# TrafficControl no
# Parameter: DownloadLimit
# Default: 0
#
# If TrafficControl is enabled, this sets the maximum download
# speed to the GatewayInterface, in kilobits per second.
# For example if you have an ADSL connection with 768 kbit
# download speed, and you want to allow about half of that
# bandwidth for the GatewayInterface, set this to 384.
# A value of 0 means no download limiting is done.
#
# DownloadLimit 200
# Parameter: UploadLimit
# Default: 0
#
# If TrafficControl is enabled, this sets the maximum upload
# speed from the GatewayInterface, in kilobits per second.
# For example if you have an ADSL connection with 128 kbit
# upload speed, and you want to allow about half of that
# bandwidth for the GatewayInterface, set this to 64.
# A value of 0 means no upload limiting is done.
#
# UploadLimit 100
# Parameter: GatewayIPRange
# Default: 0.0.0.0/0
#
# By setting this parameter, you can specify a range of IP addresses
# on the GatewayInterface that will be responded to and managed by
# Nodogsplash. Addresses outside this range do not have their packets
# touched by Nodogsplash at all.
# Defaults to 0.0.0.0/0, that is, all addresses.
#
# GatewayIPRange 0.0.0.0/0
# Parameter: ImagesDir
# Default: images
#
# Set the directory from which images are served.
# Use $imagesdir in HTML files to reference this directory.
#
# ImagesDir images
# Parameter: BinVoucher
# Default: None
#
# Enable Voucher Support.
# If set, an alphanumeric voucher HTTP parameter is accepted
# and passed to a command line call along with the clients MAC:
#
# $<BinVoucher> auth_voucher <mac> <voucher>
#
# BinVoucher must point to a program that will be called as described above.
# The call is expected to output the number of seconds the client
# is to be authenticated. Zero or negative seconds will cause the
# authentification request to be rejected.
# The output may contain a user specific download and upload limit in KBit/s:
# <seconds> <download> <upload>
#
# BinVoucher "/bin/myauth"
# Parameter: ForceVoucher
# Default: no
#
# Force the use of a voucher. Authentification is not possible without voucher.
#
# ForceVoucher no
# Parameter: EnablePreAuth
# Default: no
#
# Enable pre-authentication support.
# Pass the MAC of a client to a command line call before the splash page
# would be send:
#
# $<BinVoucher> auth_status <mac>
#
# The call is expected to output the number of seconds the client
# is to be authenticated. Zero or negative seconds will cause the
# splash page to be displayed.
# The output may contain a user specific download and upload limit in KBit/s:
# <seconds> <download> <upload>
#
# EnablePreAuth no
FirewallRuleSet
- authenticated-users
- preauthenticated-users
- users-to-router
EmptyRuleSetPolicy
- authenticated-users
- preauthenticated-users
- users-to-router
- trusted-users
- trusted-users-to-router
每个进入路由器的包有4种类型
- Blocked - MACMechanism block: 在BlockedMACList / MACMechanism allow: 不在AllowedMACList或者TrustedMACList.
- Trusted - 在TrustedMACList, 放行, 定制行为: FirewallRuleSet trusted-users和trusted-users-to-router, 或者EmptyRuleSetPolicy trusted-users 和 trusted-users-to-router.
- Authenticated - 通过认证, 没有超期. 定制行为在: FirewallRuleSet authenticated-users 和 users- to-router
- Preauthenticated - 任何其他的包, 定制行为在: FirewallRuleSet preauthenticated-users 和 users-to-router, 所有其他的包都被dropped, 除了目的端口是80的包, 被重定向到2050(nodogsplash内建的http服务器在监听的), 这个会启动authentication过程, 服务器将会serve一个splash网页返回给源IP, 用户点击splash page上的一个合适的链接就会完成认证过程. 使得后面这个IP/MAC的包被标记为Authenticated, 直到inactive或者forced timeout达到, 然后他的包重新变为Preauthenticated.
- Nodogsplash实现这些动作通过在路由器的iptables mangle PREROUTING chain中插入规则来标记这些包.并且在匹配这些标记的nat PREROUTING, filter INPUT和filter FORWARD chains上插入规则. 因为他插入这些规则在现有的chains的开始处, 所以nodogsplash对于大多的现有的防火墙配置不受影响.
流量控制Traffic Control
- nodogsplash在他管理的接口上也实现了基本的流量控制, 这个特性可以指定clients的最大上传和下载流量. 通过使能2个Intermediate Queue Devices (IMQ's), 一个用于upload一个用于download, 并且给他们附加简单的rate-limited HTB qdiscs. 规则被插入到路由器的iptables mangle PREROUTING 和 POSTROUTING tables来跳到这些IMQ's. 结果是简单但是有效的尾部丢弃限制速率.(没有packet classification或者fairness queueing)
FirewallRule 格式
FirewallRule permission [protocol [port portrange] [to ip]- permission:必选, 必须是: allow, block, drop, log 或者 ulog
- protocol: 可选, 必须是: tcp, udp, icmp或者all, 默认是all
- port portrange: 可选, protocol必须是: tcp 或 udp, portrange可以是一个单一数字端口或者冒号分割范围,如 1024:2048, 默认是所有端口.
- to ip: 可选, ip必须是点十进制带有可选的子网掩码, 默认是: 0.0.0.0/0, 所有地址.
splash.html 定制
- $gatewayname: nodogsplash.conf中的GatewayName.
- $authtarget: 一个URL编码了一个唯一的token和用户原始web请求的URL. 如果nodogsplash在这个URL上接收到了请求, 他会完成authentication过程, 并且返回"302 Found"到编码的原始的web请求URL(或者你可以使用一个GET方法来发送这个信息给nodogsplash)
- $imagesdir: nodogsplash的 web hierarchy的图片目录
- $tok, $redir,$authaction, and $denyaction 也是可用的, 如果你想要使用GET方法而不是使用$authtarget来和nodogsplash server通信, 例子:
<form method='GET' action='$authaction'>
<input type='hidden' name='tok' value='$tok'>
<input type='hidden' name='redir' value='$redir'>
<input type='submit' value='Click Here to Enter'>
</form>
infoskel.html - 错误页面
- $gatewayname, $version, $title 和 $content这些变量可以使用.
- $title 是错误描述的总结或者错误类型.
- $content 是错误的内容.
认证方式
- Site-wide username and password Nodogsplash可以被配置成需要一个用户名和/或密码输入到splash page作为认证过程的一部分. 由于用户名和密码是site-wide(not per user), 他们使用HTTP GET明文进行发送, 不安全.使能他需要设置PasswordAuthentication, UsernameAuthentication, Password, Username, and PasswordAttempts, 然后splash page必须使用一个GET方法来发送用户输入的用户名和/或密码. 例子:
<form method='GET' action='$authaction'>
<input type='hidden' name='tok' value='$tok'>
<input type='hidden' name='redir' value='$redir'>
username: <input type='text' name='nodoguser' value='' size='12' maxlength='12'>
<br>
password: <input type='password' name='nodogpass' value='' size='12' maxlength='10'>
<br>
<input type='submit' value='Enter'>
</form>
- Forwarding authentication 转发认证 Nodogsplash允许调用一个外部程序来认证, 使用nodogsplash.conf里面的参数: BinVoucher/EnablePreAuth/ForceVoucher. 对于BinVoucher的给定的程序将会被调用使用客户端的mac地址作为参数.输出是作为客户端被认证的时间的秒数,他也可能包含客户端上传和下载的速度KBits/s.
ndsctl
一个独立程序, 使用unix socket与nodogsplash通信. ndsctl -h
调试nodogsplash
- 最大化输出调试信息:
-s -f -d 7. - 当停止运行, nodogsplash删除他的规则, 如果没有(crash情况), 那么可以手动start然后stop nodogsplash来清除规则.
- nodogsplash的运行是通过mark packets(如果使能了traffic control, 那么passing packets through intermediate queueing devices), 大多数的QOS包也会mark packets 和使用 IMQ's. 一起用可能会失效, 为了检查所有的规则, 如
the mangle table chains,iptables -t mangle -v -n -L