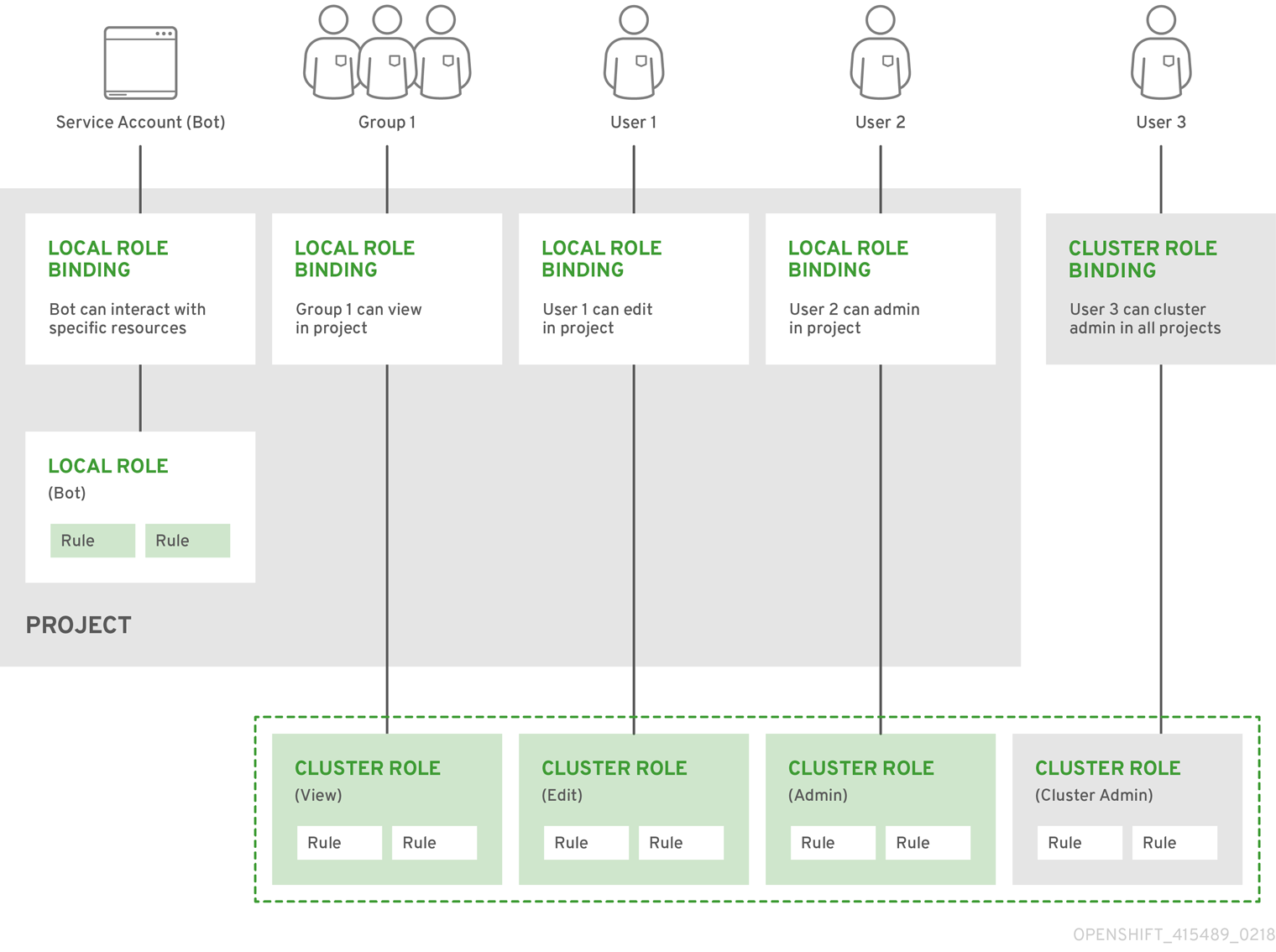
OCP中的权限管理沿用的Kubernetes RBAC机制,授权模式主要取决于下面几个因数
|
针对主要对象的操作权限,比如建立Pod Sets of permitted verbs on a set of objects. For example, whether something can |
|
|
一系列的Rules的集合,用户和组能关联这些Roles Collections of rules. Users and groups can be associated with, or bound to, multiple roles at the same time. |
|
|
用户和组针对角色的关联 Associations between users and/or groups with a role. |
RBAC分成两种,一种是集群范围内的,叫做Cluster RBAC,一种是项目范围内的,叫Local RBAC,官方定义如下
|
Cluster RBAC |
Roles and bindings that are applicable across all projects. Roles that exist cluster-wide are considered cluster roles. Cluster role bindings can only reference cluster roles. |
|
Local RBAC |
Roles and bindings that are scoped to a given project. Roles that exist only in a project are considered local roles. Local role bindings can reference both cluster and local roles. |
而当前的Cluster Role包括如下:
| Default Cluster Role | Description |
|---|---|
|
admin |
A project manager. If used in a local binding, an admin user will have rights to view any resource in the project and modify any resource in the project except for quota. |
|
basic-user |
A user that can get basic information about projects and users. |
|
cluster-admin |
A super-user that can perform any action in any project. When bound to a user with a local binding, they have full control over quota and every action on every resource in the project. |
|
cluster-status |
A user that can get basic cluster status information. |
|
edit |
A user that can modify most objects in a project, but does not have the power to view or modify roles or bindings. |
|
self-provisioner |
A user that can create their own projects. |
|
view |
A user who cannot make any modifications, but can see most objects in a project. They cannot view or modify roles or bindings. |
下面实际操作一下加深理解。
- 添加用户
htpasswd /etc/origin/master/htpasswd eric
htpasswd /etc/origin/master/htpasswd alice
- 查看用户
首先需要以管理员身份登录
[root@master ~]# oc login -u system:admin Logged into "https://master.example.com:8443" as "system:admin" using existing credentials. You have access to the following projects and can switch between them with 'oc project <projectname>': default kube-public kube-service-catalog kube-system logging management-infra myproject openshift openshift-ansible-service-broker openshift-infra openshift-node openshift-template-service-broker openshift-web-console * test Using project "test". [root@master ~]# oc get users NAME UID FULL NAME IDENTITIES admin 7594833f-efd1-11e8-bd01-0800275a35ec htpasswd_auth:admin alice 517c077e-f094-11e8-bc3a-0800275a35ec htpasswd_auth:alice eric 9ff08197-f093-11e8-bc3a-0800275a35ec htpasswd_auth:eric
eric和alice各自建立project,eric创建myproject,alice创建test项目
- 以alice登录后查看rolebinding
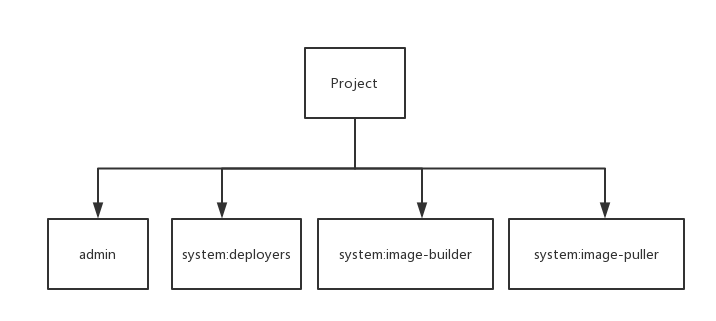
[root@master ~]# oc get rolebinding NAME ROLE USERS GROUPS SERVICE ACCOUNTS SUBJECTS admin /admin alice system:deployers /system:deployer deployer system:image-builders /system:image-builder builder system:image-pullers /system:image-puller system:serviceaccounts:test
也就是说每个新建立的项目包含的本地rolebinding包括
- 查看每个rolebinding具体关联的role和用户
[root@master ~]# oc describe rolebinding.rbac Name: admin Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: admin Subjects: Kind Name Namespace ---- ---- --------- User alice Name: system:deployers Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: system:deployer Subjects: Kind Name Namespace ---- ---- --------- ServiceAccount deployer test Name: system:image-builders Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: system:image-builder Subjects: Kind Name Namespace ---- ---- --------- ServiceAccount builder test Name: system:image-pullers Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: system:image-puller Subjects: Kind Name Namespace ---- ---- --------- Group system:serviceaccounts:test
- 给alice用户授予访问myproject的admin权限
[root@master ~]# oc adm policy add-role-to-user admin alice -n myproject role "admin" added: "alice"
如果只是需要拉取myproject命名空间下的镜像,可以赋予image-puller权限就可以了
[root@master ~]# oc adm policy add-role-to-user system:image-puller alice -n myproject role "system:image-puller" added: "alice"
再度describe一下
[root@master ~]# oc describe rolebinding.rbac -n myproject Name: admin Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: admin Subjects: Kind Name Namespace ---- ---- --------- User eric Name: admin-0 Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: admin Subjects: Kind Name Namespace ---- ---- --------- User alice Name: system:deployers Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: system:deployer Subjects: Kind Name Namespace ---- ---- --------- ServiceAccount deployer myproject Name: system:image-builders Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: system:image-builder Subjects: Kind Name Namespace ---- ---- --------- ServiceAccount builder myproject Name: system:image-puller Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: system:image-puller Subjects: Kind Name Namespace ---- ---- --------- User alice Name: system:image-pullers Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: system:image-puller Subjects: Kind Name Namespace ---- ---- --------- Group system:serviceaccounts:myproject
- 查看所有的clusterrole
[root@master ~]# oc get clusterrole NAME admin asb-access asb-auth basic-user cluster-admin cluster-debugger cluster-reader cluster-status edit hawkular-metrics hawkular-metrics-admin .....
- 查看具体的一个clusterrole能做的内容
[root@master ~]# oc describe clusterrole system:image-builder Name: system:image-builder Created: 37 hours ago Labels: <none> Annotations: openshift.io/description=Grants the right to build, push and pull images from within a project. Used primarily with service accounts for builds. openshift.io/reconcile-protect=false Verbs Non-Resource URLs Resource Names API Groups Resources [get update] [] [] [image.openshift.io ] [imagestreams/layers] [create] [] [] [image.openshift.io ] [imagestreams] [update] [] [] [build.openshift.io ] [builds/details] [get] [] [] [build.openshift.io ] [builds]
所有缺省的ClusterRole都能绑定用户或组到本地项目中。此外可以自己定义本地Role
==============================================================================================
给权限和回收权限
给一个imager:pruner的权限,以及给一个集群管理员的权限
oc adm policy add-cluster-role-to-user system:image-pruner eric
oc adm policy add-cluster-role-to-user cluster-admin eric
查看
[root@master ~]# oc get rolebindings NAME ROLE USERS GROUPS SERVICE ACCOUNTS SUBJECTS admin /admin eric system:deployers /system:deployer deployer system:image-builders /system:image-builder builder system:image-pruner /system:image-pruner eric system:image-pullers /system:image-puller system:serviceaccounts:openshift3
回收
[root@master ~]# oc adm policy remove-role-from-user system:image-pruner eric role "system:image-pruner" removed: "eric"
取消eric的对项目的admin权限,而给只读权限
[root@master ~]# oc adm policy add-role-to-user view eric role "view" added: "eric" [root@master ~]# oc adm policy remove-role-from-user admin eric role "admin" removed: "eric" [root@master ~]# oc get rolebinding NAME ROLE USERS GROUPS SERVICE ACCOUNTS SUBJECTS system:deployers /system:deployer deployer system:image-builders /system:image-builder builder system:image-pullers /system:image-puller system:serviceaccounts:openshift3 view /view eric
可以参考
https://docs.openshift.com/container-platform/3.9/admin_guide/manage_rbac.html