1.引入依赖
<dependency> <groupId>org.apereo.cas</groupId> <artifactId>cas-server-support-oidc</artifactId> <version>${cas.version}</version> </dependency>
2.生成jwks
官方提供的用于生产JWK文件工具:https://mkjwk.org/
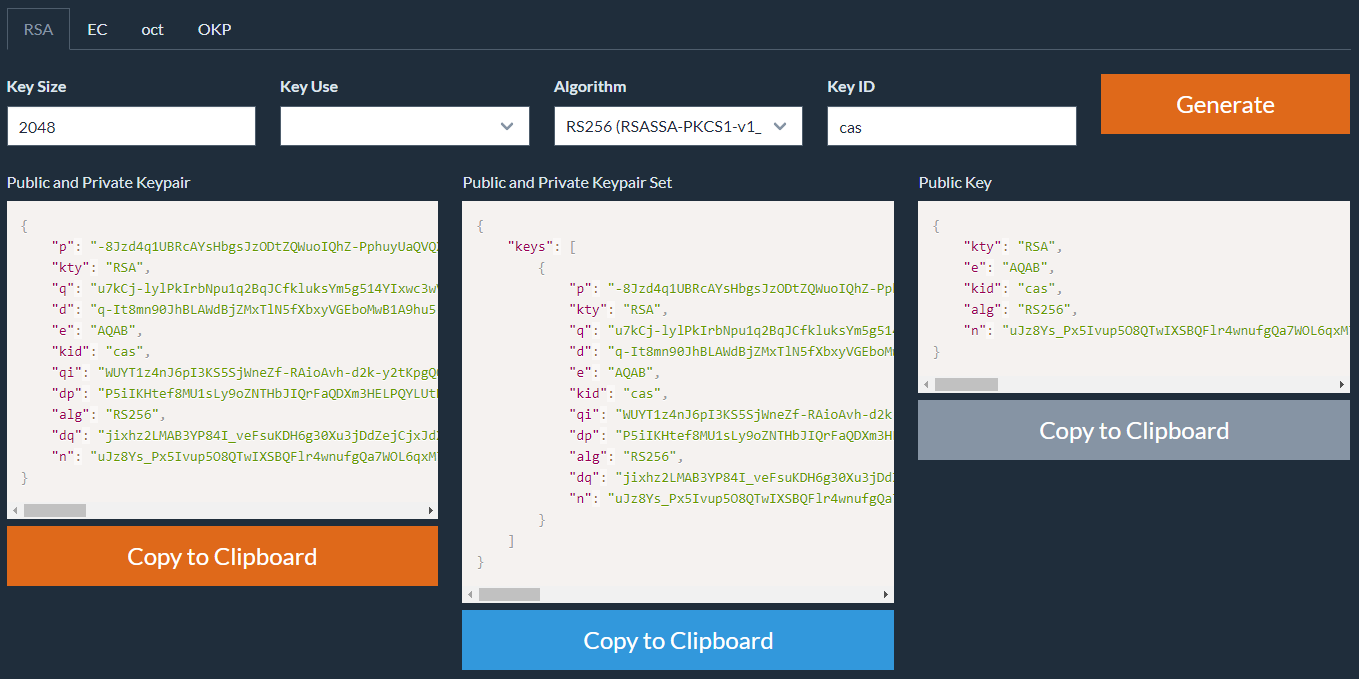
复制出来如下:
{ "keys": [ { "p": "-8Jzd4q1UBRcAYsHbgsJzODtZQWuoIQhZ-PphuyUaQVQXTF466FZjeKkvlGkf3H-TgxlQxgb5S0rfbNKxlR3NO4xdGwtuv8hvzI1FJFmCA2Ap78u0-9UCvmpmiJ--SREF6r50_-kXOg_RIvEmH_mEVjHWMN7k4ajwL5jnWr1R0M", "kty": "RSA", "q": "u7kCj-lylPkIrbNpu1q2BqJCfkluksYm5g514YIxwc3wVVWF6SSTdnpLHvckVjzS8-w9gtnC0kcaKpE8bhQpetu5gf-1QGYIty03Q4my6qca6KosW3yUIfSjOpTKETwJOjby0Se1F9axr11_tP1A_OBZHfV_DDnH5xp7bBAagdk", "d": "q-It8mn90JhBLAWdBjZMxTlN5fXbxyVGEboMwB1A9hu5-08JyVRGPPTUe-6kVqSjPMGRDraXNw54PiixE-qLEK80lA_0CWbD00vdRFPelQU0A84koUazGwwy7rnl5ARjqJmQkUBgn6BnwXyvhX1ENKui4jCixFG5oWO2H1HT5LAzzI0z5XVhvngdF6hfMBXdIsUQtkFCnjbnLziQxdcOpmYXbqTgclUWdO--8IZ-PkaHlX7JhJ3BhVJH4bdautCaI5yytc4MBqjQHGCcExMIsXSrJmLwocLqTq1jK05cz1P5Ukkd9xvkCDrSv6osS7SUxP1ZS7fy0VLxsViPvbL34Q", "e": "AQAB", "kid": "cas", "qi": "WUYT1z4nJ6pI3KS5SjWneZf-RAioAvh-d2k-y2tKpgQOSQX_E-n8YqAxVBZrbXRt5mcM4Tr39E65jmQQKkIbxylOyzh0yffnSjLpsi1vZa1ZoTtO2ae2hlk9NvCHjKi0xd4K-A_v93VUZERIV_A2ZeMMfw7u0waLvgJCWn90DmU", "dp": "P5iIKHtef8MU1sLy9oZNTHbJIQrFaQDXm3HELPQYLUtNWK1FmWghwiitavIetp7qGXciIUe2zDaT1OX0jpMJpdJBpeIpzyHhuXWKWQ69km0uwbEWuCytszQL9saeAnt5w-zJvRbHwzxbtwoDeG5ehKVDfhWrYsHRHcA6U6qQGRc", "alg": "RS256", "dq": "jixhz2LMAB3YP84I_veFsuKDH6g30Xu3jDdZejCjxJdXNRnvsJKeCHY4nLwqzhGE5259a7PHRIDLRX_315r3i3AMQHPM73gXk7vwBfutAOEMlTgFHkjs3Aau9TgpDgJ9LpTdNCExm1tj-WADz6ya4qp7dCAxV64PQ22gGkjb-ok", "n": "uJz8Ys_Px5Ivup5O8QTwIXSBQFlr4wnufgQa7WOL6qxM7KEpWAWArj4u4Aj_Clmj48r-VNTJRctz7IDZNgtsmd3FKNMENaWVhvvzFCbHSghYT44vzy21Ct0GwA5RTLppkACkgiGOEUXedfqVay5eAPS2V-bZD8B9EnDKETOGj0qPjYXKCwOVa-Ik-gLu4XqBU1nbfF3OWl_SY-sPC6JU3rwT0twFh5zRynCfjZiwyFq3yfVcgoKrFQAPLKtfJQTUFsYx2S6iXrd79S4I5NADR5s4_ZDzT8MA-i4x4j6-zCVhrw1DCgFwiLsUF7TPAMBz63xWcEjuR5bwxjX2r6Aqyw" } ] }
在static下新建keystore.jwks文件,将以上内容复制进去。
3.修改application.properties
## # OIDC # #签名文件路径 cas.authn.oidc.jwksFile=classpath:/static/keystore.jwks #签发端地址 cas.authn.oidc.issuer=${cas.server.name}/oidc/ #-------------------开启动态注册客户端------------------ cas.authn.oidc.dynamicClientRegistrationMode=OPEN #-------------------自定义字段------------------ cas.authn.oidc.userDefinedScopes.hbtvprofiles=id,name,mobile,email,avatar
4.在service下新建OIDC-1002.json
{ "@class" : "org.apereo.cas.services.OidcRegisteredService", "clientId": "abcd", "clientSecret": "xyz", "serviceId" : "^(https|http|imaps)://app1.cas.com.*", "name": "ODICService", "id": 1002, "scopes" : [ "java.util.HashSet", [ "profile", "email", "address", "phone", "offline_access", "displayName", "eduPerson" ] ] }
5.OIDC所有节点信息
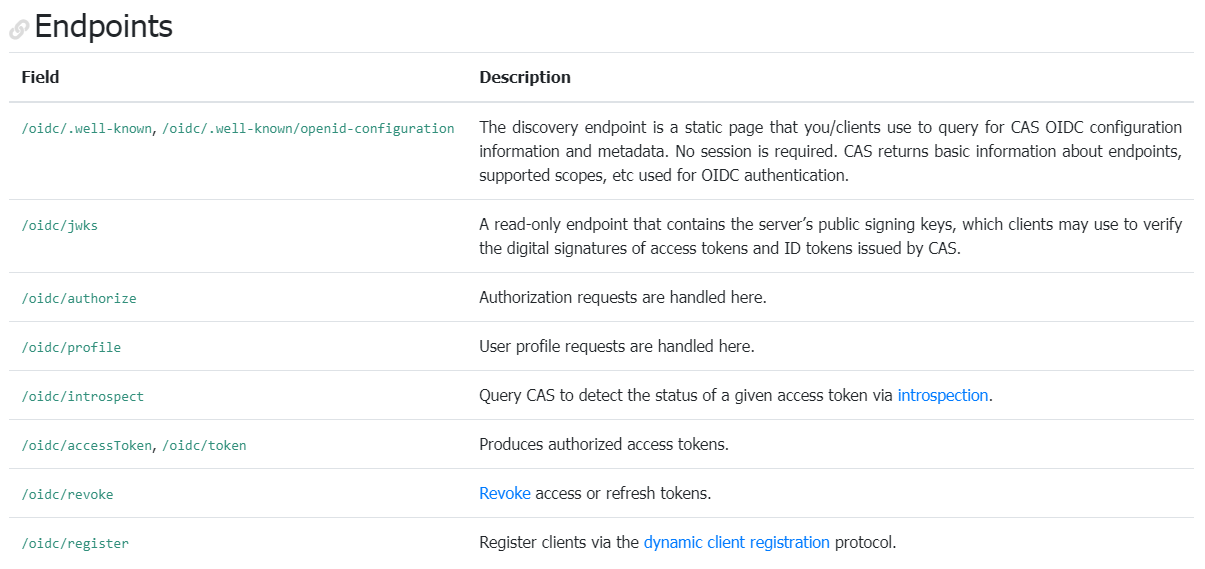
6.测试
请求:https://server.cas.com:8443/cas/oidc/.well-known,可以如下信息:
{ "issuer":"https://server.cas.com:8443/cas/oidc/", "scopes_supported":[ "openid", "profile", "email", "address", "phone", "offline_access" ], "response_types_supported":[ "code", "token", "id_token token" ], "subject_types_supported":[ "public", "pairwise" ], "claim_types_supported":[ "normal" ], "claims_supported":[ "sub", "name", "preferred_username", "family_name", "given_name", "middle_name", "given_name", "profile", "picture", "nickname", "website", "zoneinfo", "locale", "updated_at", "birthdate", "email", "email_verified", "phone_number", "phone_number_verified", "address", "gender" ], "grant_types_supported":[ "authorization_code", "password", "client_credentials", "refresh_token" ], "id_token_signing_alg_values_supported":[ "none", "RS256" ], "introspection_endpoint_auth_methods_supported":[ "client_secret_basic" ], "jwks_uri":"https://server.cas.com:8443/cas/oidc/jwks", "token_endpoint":"https://server.cas.com:8443/cas/oidc/accessToken", "authorization_endpoint":"https://server.cas.com:8443/cas/oidc/authorize", "userinfo_endpoint":"https://server.cas.com:8443/cas/oidc/profile", "registration_endpoint":"https://server.cas.com:8443/cas/oidc/register", "end_session_endpoint":"https://server.cas.com:8443/cas/logout", "introspection_endpoint":"https://server.cas.com:8443/cas/oidc/introspect", "revocation_endpoint":"https://server.cas.com:8443/cas/oidc/revoke" }
从response_types_supported,可知相较于OAuth模式,OIDC多了一种id_token。
6.1.id_token模式
1.请求以下地址获取id_token:
https://server.cas.com:8443/cas/oidc/authorize?response_type=id_token token&scope=openid&client_id=abcd&redirect_uri=http://app1.cas.com
response_type:获取的响应类型,id_token token,中间有空格
返回如下:
http://app1.cas.com/#access_token=AT-2-C3bFdo7yBqgR0-kfQZn2GTT54BDE-k8I&token_type=bearer&expires_in=28800&refresh_token=RT-2-XRmagsTk9HsVfty-uOo-ffT-mM0bwuWH&id_token=eyJhbGciOiJSUzI1NiIsImtpZCI6ImNhcyJ9.eyJqdGkiOiJUR1QtMS14V1pYUlgwNEpUazdWT3BVQlpGajk2MFBSeGJPT2VpVVRDLWhnSzg1cUdxZm13T3lDLXNHVTV2R3hSRlFYWE1OUnlNYW5nZWwtUEMiLCJpc3MiOiJodHRwczovL3NlcnZlci5jYXMuY29tOjg0NDMvY2FzL29pZGMvIiwiYXVkIjoiYWJjZCIsImV4cCI6MTU5MDQzNTA3NSwiaWF0IjoxNTkwNDA2Mjc1LCJuYmYiOjE1OTA0MDU5NzUsInN1YiI6ImFkbWluIiwiYW1yIjpbIlJlbWVtYmVyTWVVc2VybmFtZVBhc3N3b3JkQ2FwdGNoYUF1dGhlbnRpY2F0aW9uSGFuZGxlciJdLCJzdGF0ZSI6IiIsIm5vbmNlIjoiIiwiYXRfaGFzaCI6IjZ0bkgyejk5SUQ4ZkVIWmhnSHI5aFEiLCJwcmVmZXJyZWRfdXNlcm5hbWUiOiJhZG1pbiJ9.brHP9rswVSNFWLorJnAlGqkU7xrPa9CxR255d8VKJjJMqfjRcDxVKjEGQgztSR-upX2PNFqLG7PZMi1mWbZ86NV_4f3wQ9ywQiB59wE4Qe5W_v0kgEz5wF9gi9oWLExKI9sj2EPeU7L-AKVPz-5oRGl20Vs8_bJOqJaPnBVz1jojTsdBgPW4EcEiKv8tU6FA7KXuC_61kXVCCBj8vCLDIOWZETep8KFN_3tLfJ5CcmzC3MioG7Jmg60YhstsS9W2HZV_faxQFV44HgxnuWV-G4wp4_bhs6GorJqCQCNKjE2r1ZFC6bm3jRHQvRWvDDIoyk79HBrQW-noKk5NA8N_wg
整理如下:
access_token:AT-2-C3bFdo7yBqgR0-kfQZn2GTT54BDE-k8I
refresh_token:RT-2-XRmagsTk9HsVfty-uOo-ffT-mM0bwuWH
id_token:eyJhbGciOiJSUzI1NiIsImtpZCI6ImNhcyJ9.eyJqdGkiOiJUR1QtMS14V1pYUlgwNEpUazdWT3BVQlpGajk2MFBSeGJPT2VpVVRDLWhnSzg1cUdxZm13T3lDLXNHVTV2R3hSRlFYWE1OUnlNYW5nZWwtUEMiLCJpc3MiOiJodHRwczovL3NlcnZlci5jYXMuY29tOjg0NDMvY2FzL29pZGMvIiwiYXVkIjoiYWJjZCIsImV4cCI6MTU5MDQzNTA3NSwiaWF0IjoxNTkwNDA2Mjc1LCJuYmYiOjE1OTA0MDU5NzUsInN1YiI6ImFkbWluIiwiYW1yIjpbIlJlbWVtYmVyTWVVc2VybmFtZVBhc3N3b3JkQ2FwdGNoYUF1dGhlbnRpY2F0aW9uSGFuZGxlciJdLCJzdGF0ZSI6IiIsIm5vbmNlIjoiIiwiYXRfaGFzaCI6IjZ0bkgyejk5SUQ4ZkVIWmhnSHI5aFEiLCJwcmVmZXJyZWRfdXNlcm5hbWUiOiJhZG1pbiJ9.brHP9rswVSNFWLorJnAlGqkU7xrPa9CxR255d8VKJjJMqfjRcDxVKjEGQgztSR-upX2PNFqLG7PZMi1mWbZ86NV_4f3wQ9ywQiB59wE4Qe5W_v0kgEz5wF9gi9oWLExKI9sj2EPeU7L-AKVPz-5oRGl20Vs8_bJOqJaPnBVz1jojTsdBgPW4EcEiKv8tU6FA7KXuC_61kXVCCBj8vCLDIOWZETep8KFN_3tLfJ5CcmzC3MioG7Jmg60YhstsS9W2HZV_faxQFV44HgxnuWV-G4wp4_bhs6GorJqCQCNKjE2r1ZFC6bm3jRHQvRWvDDIoyk79HBrQW-noKk5NA8N_wg
2.根据accessToken获取用户信息,请求如下:
https://server.cas.com:8443/cas/oidc/profile?access_token=AT-2-C3bFdo7yBqgR0-kfQZn2GTT54BDE-k8I
得到响应如下:
{ "sub" : "admin", "auth_time" : 1590406275, "attributes" : { "credentialType" : "RememberMeUsernamePasswordCaptchaCredential" }, "id" : "admin" }
参考如下:
https://apereo.github.io/cas/5.2.x/installation/OIDC-Authentication.html
https://www.jianshu.com/p/be7cc032a4e9
https://blog.csdn.net/BecauseSy/article/details/80223125
https://www.cnblogs.com/linianhui/p/openid-connect-core.html
https://www.cnblogs.com/linianhui/p/openid-connect-extension.html