1, background info
5 stages in CPU pipeline: IF, ID, EX, MM, WB
IF – Instruction Fetch
ID – Instruction Decode
EX – Execute
MM – Memory
WB – Write Back
2, what is data hazard and how does it happen
Data hazards occur when instructions that exhibit data dependency modify data in different stages of a pipeline.
For example, we write a register and then read it. The write and read operations are dependent; they are related by the same register.
In a pipeline, if read happens before the write can finish, it’s very likely that it would not read back a correct value.
In this case, data hazard happens.
It’s not difficult to imagine that any 2 operations involving write may cause data hazard.
We can categorize data hazard into 3 kinds:
(1) read after write (RAW);
(2) write after write (WAW);
(3) write after read (WAR);
3, how to prevent data hazard
(1) pipeline bubbling
That is, stall the pipeline until hazard is resolved.
add r1, r2, r3
add r4, r1, r5
Cycles----->
________________________ Instructions
|_IF_|_ID_|_EX_|_MM_|_WB_|______________ add r1, r2, r3
|_IF_|_x_x_x_x_|_ID_|_EX_|_MM_|_WB_| add r4, r1, r5
stall cycles
Usually, NOP operationg is inserted during stall time.
As instructions are fetched, control logic determines whether a hazard could/will occur. If this is true, then the control logic insert NOPs into the pipeline.
If the number of NOPs equals the number of stages in the pipeline, the processor has been cleared of all instructions and can proceed free from hazards.
(2) out-of-order execution
This would be introduced heavily later.
(3) operand forwarding/bypass
See below examle.
Instruction 0: Register 1 = 6Instruction 1: Register 1 = 3Instruction 2: Register 2 = Register 1 + 7 = 10
Instruction 2 would need to use Register 1. If Instruction 2 is executed before Instruction 1 is finished, it may get a wrong result.
However, we can see that:
a) the output of Instruction 1 (which is 3) can be used by subsequent instructions before the value 3 is committed to/stored in Register 1.
b) there is no wait to commit/store the output of Instruction 1 in Register 1 (in this example, the output is 3) before making that output available to the subsequent instruction (in this case, Instruction 2).
So it can be done that:
Instruction 2 uses the correct (the more recent) value of Register 1: the commit/store was made immediately and not pipelined.
This is forwarding/bypass.
4, how does forwarding/bypss work
With forwarding enabled, the Instruction Decode/Execution (ID/EX) stage of the pipeline now has two inputs: the value read from the register specified (in this example, the value 6 from Register 1), and the new value of Register 1 (in this example, this value is 3) which is sent from the next stage Instruction Execute/Memory Access(EX/MM). Added control logic is used to determine which input to use.
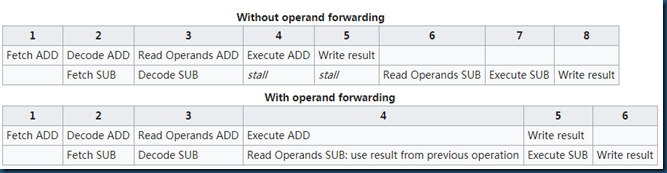
A forwarding vs. no forwarding example as followed:
ADD A B C #A=B+C SUB D C A #D=C-A