当前环境:
- 阿里云CoreOS
- 所绑定的域名,解析管理也在阿里这儿,在该文档中使用
example.com作为示例。 - Docker 镜像
neilpang/acme.sh:2.8.8https://github.com/acmesh-official/acme.sh - nginx 申请证书并使用
- 使用Docker-Compose
- SSL证书为泛域名证书
实际应用中可以参考下面两篇文章:
- 2. Deploy certs from a container to another container 第二部分
- DNS API 参考这部分
11. Use Aliyun domain API to automatically issue cert acme.shdns模式支持Cloudflare,DNSPod.cn,CloudXNS.com,GoDaddy.com,Amazon Route53,Aliyun,Linode,FreeDNS,DigitalOcean等大概一百多个域名解析提供商,本文使用的是阿里云域名解析,申请SSL的时候会往域名解析力添加一条TXT记录来验证域名所有权。
目的:
- 在阿里云CoreOS操作环境中绑定 Let's Encrypt SSL证书并使用。(不是很清楚使用这种方式能否实现证书自动续费,证书是3个月有效期,也许3个月之后就可以知道了。)
下载所需镜像
个人习惯喜欢先把所需要的镜像给下载下来,不喜欢用latest标签,因为觉得如果新版本有功能更新的话,会让人迷糊。
Docker-Compose的安装略过。
$ sudo docker pull nginx:1.19.6-alpine
$ sudo docker pull neilpang/acme.sh:2.8.8
创建docker-compose.yml文件
version: '3'
services:
runNginx:
image: nginx:1.19.6-alpine
container_name: runNginx
volumes:
- /data/docker_config/nginx/nginx.conf:/etc/nginx/nginx.conf:ro
- /data/docker_config/nginx/ssl:/etc/nginx/ssl
ports:
- 80:80
- 443:443
depends_on:
- runAcmesh
environment:
- NGINX_PORT=80
labels:
- sh.acme.autoload.domain=example.com
runAcmesh:
image: neilpang/acme.sh:2.8.8
container_name: runAcmesh_example.com
command: daemon
volumes:
- /data/docker_config/acme.sh:/acme.sh
- /var/run/docker.sock:/var/run/docker.sock
environment:
- DEPLOY_DOCKER_CONTAINER_LABEL=sh.acme.autoload.domain=example.com
- DEPLOY_DOCKER_CONTAINER_KEY_FILE="/etc/nginx/ssl/example.com/key.pem"
- DEPLOY_DOCKER_CONTAINER_CERT_FILE="/etc/nginx/ssl/example.com/cert.pem"
- DEPLOY_DOCKER_CONTAINER_CA_FILE="/etc/nginx/ssl/example.com/ca.pem"
- DEPLOY_DOCKER_CONTAINER_FULLCHAIN_FILE="/etc/nginx/ssl/example.com/full.pem"
- DEPLOY_DOCKER_CONTAINER_RELOAD_CMD="service nginx force-reload"
修改 /data/docker_config/nginx/nginx.conf 启用 ssl, Configuring HTTPS servers
# HTTPS server
server {
listen 443 ssl;
server_name example.com;
ssl_certificate /etc/nginx/ssl/example.com/cert.pem;
ssl_certificate_key /etc/nginx/ssl/example.com/key.pem;;
location / {
root html;
index index.html index.htm;
}
}
启动 docker-compose
进入dockerr-compose.yml所在的目录启动容器 sudo docker-compose up -d
没猜错的话启动结果应该是nginx启动失败,acme.sh启动成功,启动失败无所谓,部署完SSL证书以后会进行一次重启。
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
64879a113906 nginx:1.19.6-alpine "/docker-entrypoint.…" About an hour ago Exited ... 0.0.0.0:80->80/tcp, 0.0.0.0:443->443/tcp runNginx
bfa2973c990a neilpang/acme.sh:2.8.8 "/entry.sh daemon" About an hour ago Up About an hour runAcmesh_guorenjun.com.cn
申请证书
第一步需要获取你的阿里云 API Key, 既API KEY和API Security,官方推荐使用子账户来申请,但是不确定需要赋值哪个权限,总是提示Invalid Domain,用了Root的API Key一次申请通过,看了一下权限列表好像是这个AliyunDNSFullAccess 管理云解析(DNS)的权限。阿里云APIKEY管理页面在这里:https://ak-console.aliyun.com/#/accesskey
获取API KEY之后,执行如下命令:
sudo docker exec -e Ali_Key="iAihASlUDxxxxxxx" -e Ali_Secret="FaYpsThfLRbQ99UaHWvvibqxxxxxxx" runAcmesh_example.com --issue --dns dns_ali -d *.example.com
Ali_Key和 Ali_Secret 就是获取的阿里云访问权限的KEY, runAcmesh_example.com是已运行的容器名字,也可以用容器ID来代替, *.example.com 要申请的域名,这个是泛域名,如果不想申请泛域名,只想申请 www.example.com 和 example.com 的话,可以指定多个 -d 参数,例如 -d www.example.com -d example.com -d test.example.com 不过好像每次申请的SSL证书有域名大小限制。
如果顺利的话输出内容如下:
[Sat Jan 9 08:20:20 UTC 2021] Using CA: https://acme-v02.api.letsencrypt.org/directory
[Sat Jan 9 08:20:20 UTC 2021] Creating domain key
[Sat Jan 9 08:20:20 UTC 2021] The domain key is here: /acme.sh/*.example.com/*.example.com.key
[Sat Jan 9 08:20:20 UTC 2021] Single domain='*.example.com'
[Sat Jan 9 08:20:20 UTC 2021] Getting domain auth token for each domain
[Sat Jan 9 08:20:27 UTC 2021] Getting webroot for domain='*.example.com'
[Sat Jan 9 08:20:27 UTC 2021] Adding txt value: ToXXnzTdkmwb6Yqn85bl01MzbdrgVCpITb0U7_cB4nI for domain: _acme-challenge.example.com
[Sat Jan 9 08:20:28 UTC 2021] The txt record is added: Success.
[Sat Jan 9 08:20:28 UTC 2021] Let's check each DNS record now. Sleep 20 seconds first.
[Sat Jan 9 08:20:48 UTC 2021] Checking example.com for _acme-challenge.example.com
[Sat Jan 9 08:20:52 UTC 2021] Domain guorenjun.com.cn '_acme-challenge.example.com' success.
[Sat Jan 9 08:20:52 UTC 2021] All success, let's return
[Sat Jan 9 08:20:52 UTC 2021] Verifying: *.example.com
[Sat Jan 9 08:20:57 UTC 2021] Success
[Sat Jan 9 08:20:57 UTC 2021] Removing DNS records.
[Sat Jan 9 08:20:57 UTC 2021] Removing txt: ToXXnzTdkmwb6Yqn85bl01MzbdrgVCpITb0U7_cB4nI for domain: _acme-challenge.example.com
[Sat Jan 9 08:20:59 UTC 2021] Removed: Success
[Sat Jan 9 08:20:59 UTC 2021] Verify finished, start to sign.
[Sat Jan 9 08:20:59 UTC 2021] Lets finalize the order.
[Sat Jan 9 08:20:59 UTC 2021] Le_OrderFinalize='https://acme-v02.api.letsencrypt.org/acme/finalize/108848397/721xxxxxxx'
[Sat Jan 9 08:21:01 UTC 2021] Downloading cert.
[Sat Jan 9 08:21:01 UTC 2021] Le_LinkCert='https://acme-v02.api.letsencrypt.org/acme/cert/0335cdb097496f91f09c53ea7af14xxxxxxx'
[Sat Jan 9 08:21:03 UTC 2021] Cert success.
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
[Sat Jan 9 08:21:03 UTC 2021] Your cert is in /acme.sh/*.example.com/*.example.com.cer
[Sat Jan 9 08:21:03 UTC 2021] Your cert key is in /acme.sh/*.example.com/*.example.com.key
[Sat Jan 9 08:21:03 UTC 2021] The intermediate CA cert is in /acme.sh/*.example.com/ca.cer
[Sat Jan 9 08:21:03 UTC 2021] And the full chain certs is there: /acme.sh/*.example.com/fullchain.cer
在docker-compose.yml中已经将/acme.sh目录link到了/data/docker_config/acme.sh目录,在该目录可以看到申请的一套ssl证书。
部署SSL证书
还差最后一步部署SSL证书,执行如下命令:
$ sudo docker exec runAcmesh_example.com --deploy -d *.example.com --deploy-hook docker
输出如下命令:
[Sat Jan 9 08:22:53 UTC 2021] Container id: 64879a113906f04d0227b8fc26321bc030cd38a2b69d7fe7462c2e7726bxxxxx
[Sat Jan 9 08:22:53 UTC 2021] Copying file from /acme.sh/*.example.com/*.example.com.key to /etc/nginx/ssl/example.com/key.pem
[Sat Jan 9 08:22:54 UTC 2021] Copying file from /acme.sh/*.example.com/*.example.com.cer to /etc/nginx/ssl/example.com/cert.pem
[Sat Jan 9 08:22:54 UTC 2021] Copying file from /acme.sh/*.example.com/ca.cer to /etc/nginx/ssl/example.com/ca.pem
[Sat Jan 9 08:22:55 UTC 2021] Copying file from /acme.sh/*.example.com/fullchain.cer to /etc/nginx/ssl/example.com/full.pem
[Sat Jan 9 08:22:55 UTC 2021] Reloading: service nginx force-reload
[Sat Jan 9 08:22:56 UTC 2021] Success
至此部署完成.
docker-compose.yml中的配置项/data/docker_config/nginx/ssl:/etc/nginx/ssl,猜测部署是把SSL文件移动到nginx容器中,但是容器重启会将文件丢失,所以link到了物理机上面,在执行 docker-compose up 文件是否会自动复制没有进行验证,只是多做了一步link。
不出意外的话,用https协议访问网址应该就没问题了。
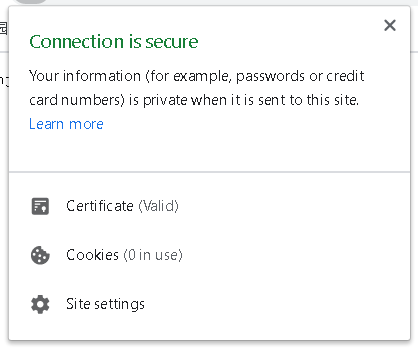
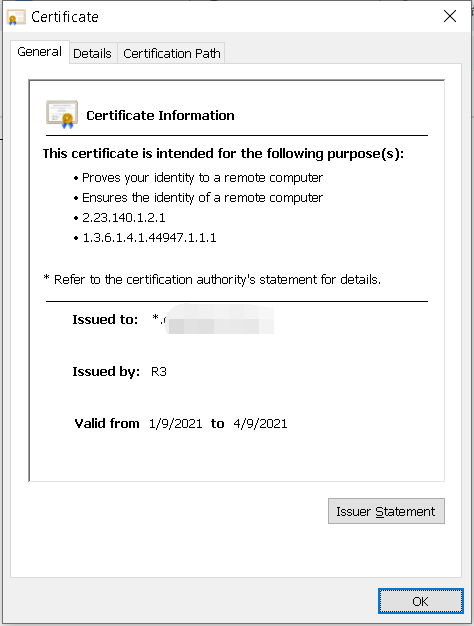
其他不知道有没用的参考: